Exploiting MS15-061 Microsoft Windows Kernel Use-After-Free (Win32k!Xxxsetclasslong)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

ENDPOINT MANAGEMENT 1 Information Systems Managers
STAFF SYMPOSIUM SERIES INFORMATION TECHNOLOGY TRACK FACILITATORS Carl Brooks System Manager ‐ Detroit, MI Chapter 13 Standing Trustee – Tammy L. Terry Debbie Smith System Manager – Robinsonville, NJ Chapter 13 Standing Trustee – Al Russo Scot Turner System Manager –Las Vegas, NV Chapter 13 Standing Trustee – Rick Yarnall Tom O’Hern Program Manager, ICF International, Baltimore, MD STACS ‐ Standing Trustee Alliance for Computer Security STAFF SYMPOSIUM ‐ IT TRACK 5/11/2017 SESSION 4 ‐ ENDPOINT MANAGEMENT 1 Information Systems Managers Windows 10 Debbie Smith System Manager Regional Staff Symposium ‐ IT Track May 11 and 12, 2017 Las Vegas, NV STAFF SYMPOSIUM ‐ IT TRACK 5/11/2017 SESSION 4 ‐ ENDPOINT MANAGEMENT 2 Windows lifecycle fact sheet End of support refers to the date when Microsoft no longer provides automatic fixes, updates, or online technical assistance. This is the time to make sure you have the latest available update or service pack installed. Without Microsoft support, you will no longer receive security updates that can help protect your PC from harmful viruses, spyware, and other malicious software that can steal your personal information. Client operating systems Latest update End of mainstream End of extended or service pack support support Windows XP Service Pack 3April 14, 2009 April 8, 2014 Windows Vista Service Pack 2April 10, 2012 April 11, 2017 Windows 7* Service Pack 1 January 13, 2015 January 14, 2020 Windows 8 Windows 8.1 January 9, 2018 January 10, 2023 Windows 10, July 2015 N/A October 13, 2020 October 14, 2025 * Support for Windows 7 RTM without service packs ended on April 9, 2013. -

What Are Kernel-Mode Rootkits?
www.it-ebooks.info Hacking Exposed™ Malware & Rootkits Reviews “Accessible but not dumbed-down, this latest addition to the Hacking Exposed series is a stellar example of why this series remains one of the best-selling security franchises out there. System administrators and Average Joe computer users alike need to come to grips with the sophistication and stealth of modern malware, and this book calmly and clearly explains the threat.” —Brian Krebs, Reporter for The Washington Post and author of the Security Fix Blog “A harrowing guide to where the bad guys hide, and how you can find them.” —Dan Kaminsky, Director of Penetration Testing, IOActive, Inc. “The authors tackle malware, a deep and diverse issue in computer security, with common terms and relevant examples. Malware is a cold deadly tool in hacking; the authors address it openly, showing its capabilities with direct technical insight. The result is a good read that moves quickly, filling in the gaps even for the knowledgeable reader.” —Christopher Jordan, VP, Threat Intelligence, McAfee; Principal Investigator to DHS Botnet Research “Remember the end-of-semester review sessions where the instructor would go over everything from the whole term in just enough detail so you would understand all the key points, but also leave you with enough references to dig deeper where you wanted? Hacking Exposed Malware & Rootkits resembles this! A top-notch reference for novices and security professionals alike, this book provides just enough detail to explain the topics being presented, but not too much to dissuade those new to security.” —LTC Ron Dodge, U.S. -

Installing, Using and Testing Microsoft Windows Driver Kit (WDK)
www.installsetupconfig.com Installing, Using and Testing Microsoft Windows Driver Kit (WDK) What do we have in this session? Introduction Installing the WDK The Windows Debuggers Installing Symbols Package The WinDbg Starting WinDbg Verifying WDK Installation Steps on Using WDK and Building Windows Driver from Code Sample Building a Windows Driver Sample Drivers and Services Installing/Registering a Driver Starting a Driver Viewing Driver Output Unloading a Driver Print Devices: Generic Text-Only Driver Sample Useful WDK references: Introduction The Windows machine specification used in this session are: 1. Operating System : Windows XP Pro SP2 2. RAM : 2 GB DDR2 3. HDD : 160++GB 4. Display : 128 MB ATI PCI Express 5. Processor : Intel Core 2 Duo 4400 2.00 GHz The DDK has been superseded by the Windows Driver Kit (WDK). While the DDK can be downloaded openly, you may need to register for free and participate in the respective Microsoft community to download WDK. Microsoft said that the WDK should be used for the following reasons: 1. Use the Windows Vista build environments in the WDK to build drivers that use new features or functionality available only in Windows Vista. 2. Use the Windows Server 2003 build environments in the WDK to build drivers that use new features or functionality available only in Windows Server 2003. 3. Use the Windows XP build environments in the WDK to build drivers that do not use new functionality available only in Windows Vista or only in Windows Server 2003 and that are targeted for either Windows XP or Windows Server 1 www.installsetupconfig.com 2003 and Windows XP. -

Support for Microsoft Office 2007
GE Healthcare Invasive Cardiology Security Website Interventional - Invasive Cardiology Product Group: Interventional Invasive Products Mac-Lab IT/XT/XTi, CardioLab IT/XT/XTi, Products: SpecialsLab and ComboLab IT/XT/XTi Recording Systems Versions: 6.8.1, 6.8, 6.5.6, 6.5.4, 6.5.3 Subject: Security Information Date: 16-August-2019 Summary The following information is provided to GE Healthcare Technologies customers in regards to known technical security vulnerabilities associated with Mac-Lab® Hemodynamic, CardioLab® Electrophysiology, SpecialsLab and ComboLab IT Recording Systems for Cath Lab, EP Lab and other interventional labs as well as the Centricity® Cardiology Data Management Systems. Security Patch Base Configuration The security patch base configuration of the Mac-Lab IT/XT/XTi and CardioLab IT/XT/XTi product at release is listed within the MLCL Base Configuration under the Hemodynamic, Electrophysiology and Cardiovascular Information Technologies section of the http://www3.gehealthcare.com/en/Support/Invasive_Cardiology_Product_Security website. Process The following actions are taken whenever Microsoft/OEMs releases new security patches: • The Invasive Cardiology Engineering Team performs a security analysis process for supported Mac-Lab IT/XT/XTi, CardioLab IT/XT/XTi, GE Client Review and INW Server hardware/software. • If a vulnerability meets Mac-Lab IT/XT/XTi and CardioLab IT/XT/XTi validation criteria, the vulnerability is communicated through the GEHC Product Security Database and Invasive Cardiology Security Website within Three weeks of the patch release. Page 1 of 88 GE Healthcare/16-August-2019 GE Healthcare • Upon validation of the Mac-Lab IT/XT/XTi and CardioLab IT/XT/XTi vulnerability, the GEHC Product Security Database and Invasive Cardiology Security Website and affected Mac-Lab IT/XT/XTi and CardioLab IT/XT/XTi Security Patch Installation Instructions are updated. -
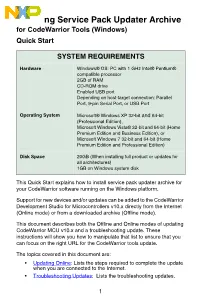
CW MCU V10.X Service Pack Updater
Installing Service Pack Updater Archive for CodeWarrior Tools (Windows) Quick Start SYSTEM REQUIREMENTS Hardware Windows® OS: PC with 1 GHz Intel® Pentium® compatible processor 2GB of RAM CD-ROM drive Enabled USB port Depending on host-target connection: Parallel Port, 9-pin Serial Port, or USB Port Operating System Microsoft® Windows XP 32-bit and 64-bit (Professional Edition), Microsoft Windows Vista® 32-bit and 64-bit (Home Premium Edition and Business Edition), or Microsoft Windows 7 32-bit and 64-bit (Home Premium Edition and Professional Edition) Disk Space 20GB (When installing full product or updates for all architectures) 1GB on Windows system disk This Quick Start explains how to install service pack updater archive for your CodeWarrior software running on the Windows platform. Support for new devices and/or updates can be added to the CodeWarrior Development Studio for Microcontrollers v10.x directly from the Internet (Online mode) or from a downloaded archive (Offline mode). This document describes both the Offline and Online modes of updating CodeWarrior MCU v10.x and a troubleshooting update. These instructions will show you how to manipulate that list to ensure that you can focus on the right URL for the CodeWarrior tools update. The topics covered in this document are: • Updating Online: Lists the steps required to complete the update when you are connected to the Internet. • Troubleshooting Updates: Lists the troubleshooting updates. 1 • Updating Offline: Lists the steps required to complete the update when you are not connected to the Internet. NOTE To ensure successful installation of service packs, updates, and patches select Restart in the File menu to perform a CodeWarrior restart. -

Installing Microsoft Windows Driver Development Kit (DDK) for Microsoft Windows Server 2003 Service Pack 1 (SP1) on Windows XP Pro SP2
www.tenouk.com Installing Microsoft Windows Driver Development Kit (DDK) for Microsoft Windows Server 2003 Service Pack 1 (SP1) on Windows XP Pro SP2 This step-by-step document also contains how-to install the Debugging Tools for Windows and Symbols Package. Machine specification used in this scenario. 1. Operating System : Windows Xp Pro SP2 2. RAM : 2 GB DDR2 3. HDD : 160++G 4. Display : 128 MB ATI PCI Express 5. Processor : Intel Core 2 Duo 4400 2.00 GHz Installing the DDK First of all we need to download the ISO from Microsoft or you can buy the CD as well. The current version is Windows Server 2003 SP1 that covers Windows 2000, Windows XP and Windows 2003 Server family. This DDK has been superseded by the Windows Driver Kit (WDK). We will try to install the WDK later. While the DDK can be downloaded openly, you need to register for free and participate in the respective Microsoft community to download WDK. Microsoft said that the WDK should be used for the following reasons: 1. Use the Windows Vista build environments in the WDK to build drivers that use new features or functionality available only in Windows Vista. 2. Use the Windows Server 2003 build environments in the WDK to build drivers that use new features or functionality available only in Windows Server 2003. 3. Use the Windows XP build environments in the WDK to build drivers that do not use new functionality available only in Windows Vista or only in Windows Server 2003 and that are targeted for either Windows XP or Windows Server 2003 and Windows XP. -

GAO-04-706 Information Security: Continued Action Needed To
United States General Accounting Office GAO Report to Congressional Requesters June 2004 INFORMATION SECURITY Continued Action Needed to Improve Software Patch Management a GAO-04-706 June 2004 INFORMATION SECURITY Continued Actions Needed to Improve Highlights of GAO-04-706, a report to Software Patch Management congressional requesters Flaws in software code can Based on agency-reported data, agencies generally are implementing introduce vulnerabilities that may important common practices for effective patch management, such as be exploited to cause significant performing systems inventories and providing information security training. damage to federal information However, they are not consistently performing others, such as risk systems. Such risks continue to assessments and testing all patches before deployment. Additional grow with the increasing speed, sophistication, and volume of information on key aspects of agencies’ patch management practices—such reported attacks, as well as the as their documentation of patch management policies and procedures and decreasing period of the time from the frequency with which systems are monitored to ensure that patches are vulnerability announcement to installed—could provide OMB, Congress, and agencies themselves with attempted exploits. The process of consistent data that could better enable an assessment of the effectiveness applying software patches to fix of an agency’s patch management processes. flaws, referred to as patch management, is a critical process Several automated tools and services are available to assist agencies in to help secure systems from performing patch management. These tools and services typically include a attacks. wide range of functionality, including methods to inventory computers, identify relevant patches and workarounds, test patches, and report network The Chairmen of the House Committee on Government Reform status information to various levels of management. -

Neuroworks/Sleepworks Microsoft Windows Update Guide
Neuroworks/Sleepworks Microsoft Windows Update Guide Author: Savio Silva Document #: DCMX-038621 Date: 04-January-2021 Revision: ZO Change Order: DCO#45854 Revision History: Refer to Appendix A I certify that, in my capacity as the project manager, I believe to the best of my knowledge that all system components are compatible as stated in this document. Approval(s) is required as per QMS-005321 Change Control Board Matrix. XLTEK Confidential Page 1 of 7 Document Template ID: DCMX-000000, Rev 3, DCO# 2445 Neuroworks/Sleepworks Microsoft Windows Update Guide Table of Contents 1. Introduction ........................................................................................................................................................... 3 1.1. Glossary ........................................................................................................................................................ 3 1.2. Related Documents and Bibliography .......................................................................................................... 3 2. Microsoft Windows Update Compatibility ............................................................................................................ 3 2.1. Windows XP and Windows Server 2003 R2 ................................................................................................. 3 2.2. Windows 7 Professional, Service Pack 1 ...................................................................................................... 3 2.3. Windows 7 Ultimate, Service Pack 1 ........................................................................................................... -
Windows 10 Service Pack Downloads Determining What Service Pack I Have Installed in Windows
windows 10 service pack downloads Determining what service pack I have installed in Windows. To see the Service Pack that's installed for Windows on your computer, follow the steps below. Viewing system properties. My Computer, found on the Windows desktop or in the Start menu. Select Properties in the popup menu. In the System Properties window, under the General tab, the version of Windows is displayed, and the currently-installed Windows Service Pack. The picture below is an example of what this screen may look like in Microsoft Windows 7. In this example, Service Pack 1 is currently installed. Your system information may look different, for example: Alternate method. Click Start . In the Search text box, type winver and press Enter . Running this command gives you a window similar to the example below, which as shown, contains the full version information including Service Pack. In Windows 10, you can type winver in the Search text box on the Windows taskbar, located next to Start . List of all Service Pack 1 (SP1) updates for Microsoft Office 2013 and related desktop products. This article lists all the Microsoft Office 2013 Service Pack 1 (SP1) desktop updates, and describes how to obtain them. Resolution. You can obtain the SP1 updates by using one of the following methods. Note If you have the Click-to-Run version of Office installed, you will be prompted to update automatically to the SP1 version. You do not have to install an update by using one of the methods in the "Resolution" section. Those apply only to a Windows Installer-based (MSI) installation. -

Microsoft Products Nearing End of Support for 2020
Microsoft Products Nearing End of Support for 2020 Products governed by the Modern Policy nearing end of support The following products (governed by the Modern Policy) have announced the end of support for 2020. There will be no new security updates, non-security updates, free or paid assisted support options or online technical content updates. Products Moving to End of Support (Modern Policy) End of Support Date System Center Data Protection Manager, version 1807 System Center Operations Manager, version 1807 System Center Orchestrator, version 1807 January 24, 2020 System Center Service Manager, version 1807 System Center Virtual Machine Manager, version 1807 Azure Container Service January 31, 2020 Windows 10, version 1709 (Enterprise, Education, IoT Enterprise) Windows 10, version 1809 (Home, Pro, Pro for Workstation, IoT Core) April 14, 2020 Windows Server version 1809 (Datacenter Core, Standard Core) Windows 10, version 1803 (Enterprise, Education, IoT Enterprise) November 10, 2020 InMage/ASR Scout December 31, 2020 pg. 1 Microsoft Products Nearing End of Support for 2020 Products governed by the Fixed Policy nearing end of support The following products (governed by the Fixed Policy) have announced the end of support in 2020. There will be no new security updates, non-security updates, free or paid assisted support options or online technical content updates. End of Support Products Moving to End of Support (Fixed Policy) Date Exchange Server 2010 (all editions) Microsoft Dynamics NAV 2009 R2 Microsoft Expression Blend 3 Microsoft Expression Design 3 Microsoft Expression Encoder 3 Microsoft Expression Studio 3 Microsoft Expression Web 3 January 14, 2020 Microsoft Hyper-V Server 2008 Microsoft Hyper-V Server 2008 R2 Windows 7 Windows Embedded Handheld 6.5 Windows Server 2008 R2 Windows Server 2008 Windows Server Update Services 3.0 April 14, 2020 Forefront Unified Access Gateway 2010 Microsoft Forefront Threat Management Gateway 2010 Enterprise Microsoft HPC Pack 2008 R2 pg. -

Intro to Windows Debugger (Windbg) for .NET Developers and Concepts in C# Vijay Rodrigues (Vijayrod) Last Updated: 2011-11-30 I
Intro to Windows Debugger (WinDBG) for .NET Developers And Concepts in C# Vijay Rodrigues (VijayRod) Last Updated: 2011-11-30 I’ve written this content as part of driving .Net Academy. Most of content has been written at home in my spare time with a real slow internet connection. Due to its very nature of publicly available symbols, .Net and its debugging information is publicly available on the internet. Hence this content can be freely redistributed for non-commercial use. A lot of acknowledgements to Ranjan Bhattacharjee for this idea, to Xavier S Raj for valuable mentorship and for the logo, and to Rishi Maini for his guidance whenever required. We’ve also discussed this with multiple resources and got ideas from them. They’ve made a difference - Kane Conway, Satya Madhuri Krovvidi, Dhiraj H N, Durai Murugan, Varun Dhawan, Balmukund Lakhani, Anmol Bhasin, Tejas Shah, Ajith Krishnan, Shasank Prasad, Chandresh Hegde. If you have any new inputs or suggestion that will help this effort please let me know. Table of Contents Section i: Getting Started 1. To give a start 2. Introduction and Concepts 3. Learning - videos (and books) 4. Learning - Advantages of C# over VB.NET and vice versa 5. Practical guide to .Net debugging 6. Useful websites Section ii: Introduction 7. Introduction 8. Intro to WinDBG for .NET Developers - part II 9. Intro to WinDBG for .NET Developers - part III (Examining code and stacks) 10. Intro to WinDBG for .NET Developers - part IV (Examining code and stacks contd.) 11. Intro to WinDBG for .NET Developers - part V (still more on Examining code and stacks) 12. -

Microsoft Service Pack & Security Bulletin Support
Microsoft Service Pack & Security Bulletin Support ReadMe Revision History Date Revised Changes Made October 21, 2020 October 2020 Microsoft Security Update Contents What’s New? . 1 Microsoft Security Bulletins . 2 Current Microsoft Security Bulletin Status . 2 Enabling Windows Updates on Avid Systems . 6 Using a Microsoft WSUS Server for distributing Windows Updates. 7 Historical List of Microsoft Security Bulletin Exceptions . 7 What’s New? For October security bulletins, see “Current Microsoft Security Bulletin Status” on page 2. For additional information on system security, see the following link on the Avid Knowledge Base: http://avid.force.com/pkb/articles/en_US/Troubleshooting/en239659. Microsoft Security Bulletins Microsoft Security Bulletins Install Windows Security Patches and Service Packs. To download patches, run Windows Update. By default Avid supports all Windows Service Packs and security patches (sometimes referred to as “hot fixes”) which apply to the environments in which Avid products are deployed. We refer to them as Windows Updates in this document. Customers can schedule the download and installation of Windows Updates whenever they are available and make sense in their production environment. Avid tests the updates within several days of their availability. However, customers do not have to wait for the testing to be complete before installing the updates. Our current testing methodology is to utilize Windows Update on a representative sample of Avid products upon notification of new Security Bulletin availability by Microsoft. These systems are updated and observed while under test. Once the test period has completed (approx. 5 days), support for the latest release of Security Bulletins is announced. Avid encourages customers to do their own independent research and to review Microsoft’s c Security Update Release Notes before installing any update to your operating system.