(SP1) for Windows 7 and Windows Server 2008 R2 by Mark Mizrahi
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

ENDPOINT MANAGEMENT 1 Information Systems Managers
STAFF SYMPOSIUM SERIES INFORMATION TECHNOLOGY TRACK FACILITATORS Carl Brooks System Manager ‐ Detroit, MI Chapter 13 Standing Trustee – Tammy L. Terry Debbie Smith System Manager – Robinsonville, NJ Chapter 13 Standing Trustee – Al Russo Scot Turner System Manager –Las Vegas, NV Chapter 13 Standing Trustee – Rick Yarnall Tom O’Hern Program Manager, ICF International, Baltimore, MD STACS ‐ Standing Trustee Alliance for Computer Security STAFF SYMPOSIUM ‐ IT TRACK 5/11/2017 SESSION 4 ‐ ENDPOINT MANAGEMENT 1 Information Systems Managers Windows 10 Debbie Smith System Manager Regional Staff Symposium ‐ IT Track May 11 and 12, 2017 Las Vegas, NV STAFF SYMPOSIUM ‐ IT TRACK 5/11/2017 SESSION 4 ‐ ENDPOINT MANAGEMENT 2 Windows lifecycle fact sheet End of support refers to the date when Microsoft no longer provides automatic fixes, updates, or online technical assistance. This is the time to make sure you have the latest available update or service pack installed. Without Microsoft support, you will no longer receive security updates that can help protect your PC from harmful viruses, spyware, and other malicious software that can steal your personal information. Client operating systems Latest update End of mainstream End of extended or service pack support support Windows XP Service Pack 3April 14, 2009 April 8, 2014 Windows Vista Service Pack 2April 10, 2012 April 11, 2017 Windows 7* Service Pack 1 January 13, 2015 January 14, 2020 Windows 8 Windows 8.1 January 9, 2018 January 10, 2023 Windows 10, July 2015 N/A October 13, 2020 October 14, 2025 * Support for Windows 7 RTM without service packs ended on April 9, 2013. -

Analysis of Microsoft “Patch Tuesday”
Report 2015 Microsoft Vulnerabilities Study: Mitigating risk by removing user privileges Analysis of Microsoft “Patch Tuesday” Security Bulletins from 2015 highlights that 85% of Critical Microsoft vulnerabilities would be mitigated by removing admin rights across an enterprise, with a 52% increase in the total volume of vulnerabilities compared to 2014. avecto.com Report Contents Introduction 2 Methodology 2 Key findings 3 Vulnerability Categories 4 Microsoft Windows vulnerabilites 5 Internet Explorer 6 Microsoft Office 7 Windows Servers 8 Additional Microsoft services 9 Conclusion 9 About Avecto 11 Appendix 12 avecto.com 1 Report Introduction Compiled by Avecto, this report analyzes the data from security bulletins issued by Microsoft throughout 2015. Microsoft bulletins are typically issued on the second Tuesday of each month, a date commonly referred to as “Patch Tuesday”, and contain fixes for vulnerabilities affecting Microsoft products that have been discovered since the last bulletin’s release. Network administrators, Security Managers and IT Professionals then respond to the update as quickly as they are able, ensuring the patches are rolled out across their systems to protect against the known vulnerabilities. In 2015, it was widely reported that Microsoft’s Patch Tuesday approach would change for all Windows 10 devices, with an approach of patches being released as soon as they are available. This effectively increases response time by as much as a month, cutting down the time between a vulnerability being discovered (Zero Day) and the patch being rolled and applied. The 2015 Microsoft Vulnerabilities Report is the third iteration of Avecto’s research. In 2014, the same report found a total of 240 vulnerabilities with a Critical rating. -
August 11, 2020
August 11, 2020 Adobe Are you bored sitting at home in Covid Quarantine? We 19 1 1 0 1 have a little excitement for you this month with two zero Bulletin Critical Important User Targeted day releases from Microsoft. These vulnerabilities impact all New Bulletins Windows Operating System versions going back to Windows Apple 18 1 1 0 1 7 and Server 2008, and also Internet Explorer 11 across all Bulletin Critical Important User Targeted supported OSs. This release also includes the resolution of Critical Windows Print Spooler Elevation of Privilege vulnerability Microsoft (CVE-2020-1337) that made recent headlines. Adobe 16 17 16 1 14 Acrobat, Reader and Apple iCloud also have critical updates Bulletins Critical Important User Targeted User Targeted resolving 26 and 20 CVEs respectively. Privilege Management CVE Vendor Ivanti Threat User Mitigates Bulletins Count Impact Severity Priority Risk Notes Targeted Impact Adobe APSB20-48 Code Execution Critical Acrobat and Reader 26 1 Apple ICLOUD-200811 Code Execution Critical iCloud for Windows 11.3 20 1 MS20-08-IE Microsoft Remote Code Exploited: Internet Explorer 9 Critical 3 Execution 1 CVE-2020-1380 and 11 MS20-08-MR2K8-ESU Exploited and Remote Code Server 2008 and Critical Disclosed: 33 Execution 1 IE 9 - Extended Security CVE-2020-1464 MS20-08-MR2K8R2- Exploited: CVE-2020-1380 ESU Remote Code Critical Exploited and Server 2008 R2 + 56 Execution 1 Disclosed: IE - Extended Security CVE-2020-1464 Exploited: MS20-08-MR7-ESU CVE-2020-1380 Remote Code Windows 7 + IE - Critical Exploited and 56 -

Microsoft Patch Tuesday March 2019
Microsoft Patch Tuesday March 2019 Dear Constituents, Microsoft has released its monthly roll-up of security patches known as Second Patch Tuesday. This means it's time to get those security updates installed. The March 2019 software updates addresses a total of 64 security vulnerabilities in its Windows operating systems and other products, 17 of which are rated critical, 45 important, one moderate and one low in severity. Included in this month's update are fixes for two vulnerabilities that are known to be actively exploited in the wild. Security updates for two actively exploited vulnerabilities Google stated that a vulnerability in Chrome and in Windows 7 was being chained together and actively exploited in the wild. While this vulnerability was mitigated by security features of Windows 10, Google warned that Windows 7 users were at risk. This vulnerability, has been fixed as part of this month's Patch Tuesday. Finally, Microsoft also fixed two bugs that are reported to be publicly disclosed. The first is a Windows denial of service vulnerability and a vulnerability in the NuGet Package Manager. What to do Users and system administrators are strongly recommended to update to the latest security patches to protect your computer from security risks. Reference Microsoft Security Update- https://portal.msrc.microsoft.com/en-us/security-guidance Please for more information you can contact us: Tonga National CERT Ministry of MEIDECC Nuku'alofa Tel: 2378 (CERT) email: [email protected] web: www.cert.gov.to 1 Disclaimer Notice: The information in this notice is intended solely for public knowledge and awareness, and not intending to harm, fright or disturb any person(s), legal entity or the receiver of this information. -

Windows Updates and Major Builds
WINDOWS UPDATES AND MAJOR BUILDS Updates install automatically, and you can’t pick and choose Another big change with Window 10 is that there will be automatic updates, so there’s less chance of you missing an important security update or bug fix. In addition, all Windows 10 systems will be on the same page at all times, whether it’s on a computer, a tablet, or a smart phone. Visit the Windows Update interface (type windows update in the search box) and you’ll find a single button — Check for updates. Click this button and Windows will check for available updates. If it finds any, it will automatically download and install them. Windows will also check for updates in the background and automatically download and install them the moment that they are released by Microsoft. Unlike on previous versions of Windows, there’s no way to select individual updates you want to download. All updates — from security updates and Windows Defender definition updates to optional updates and driver updates — will be installed automatically. The only option you can control is to select the “Advanced options” link and uncheck Give me updates for other Microsoft products when I update Windows. This will allow you to disable updates for Microsoft Office and other Microsoft programs. In Windows 10, Microsoft is committed to rolling out both security updates and feature updates. Most of the installed Modern applications will also automatically update themselves via the Windows Store. Microsoft is thinking of Windows 10 as the last version of Windows, so instead of a Windows 11 or Windows 10.1, we should see future updates and interface changes appear on an ongoing basis. -
PATCH TUESDAY April 11, 2017
PATCH TUESDAY April 11, 2017 19 Microsoft Given last month’s torrential patch downpour, 13 12 1 12 April Patch Tuesday was bound to make a quieter Bulletins Critical Important User Targeted New Bulletins entrance—but that doesn’t mean that it sprinkled. Adobe Anything but, in fact. The list includes swan song 14 5 1 1 2 security updates for one Windows OS and the Bulletins Critical Important User Targeted first of many for another. And speaking of Vista: User Targeted patch away, then deal with the aging software you Oracle can no longer patch. This month’s IIS 6.0 Zero Day 2 1 1 0 0 underlines the need for continued vigilance. Bulletin Critical Important User Targeted Zero Day Privilege Management CVE Vendor Shavlik Threat User Mitigates Bulletins Count Impact Severity Priority Risk Notes Targeted Impact MS17-IE-04 Remote Code Public Disclosure Microsoft Critical Internet Explorer 3 Execution 1 (CVE-2017-0210) Exploited (CVE-2017-0210) MS17-OFF-04 Remote Code Public Disclosure Critical Microsoft Office 8 Execution 1 (CVE-2017-0199) Exploited (CVE-2017-0199) MS17-W10-04 Remote Code Public Disclosure Critical Windows 10, 25 Execution 1 (CVE-2017-0203) Server 2016 MS17-SO7-04 Remote Code Critical Windows 7, Server 26 Execution 1 2008 R2 MS17-SO8-04 Remote Code Critical Server 2012 26 Execution 1 MS17-SO81-04 Remote Code Critical Windows 8.1, 26 Execution 1 Server 2012 R2 MS17-MR7-04 Remote Code Critical Windows 7, 26 Execution 1 Server 2008 R2 MS17-MR8-04 Remote Code Critical Server 2012 26 Execution 1 MS17-MR81-04 Remote Code Critical -

Make Technology Great Again
Make Technology Great Again Michał „rysiek” Woźniak [email protected] Everything is Broken – Quinn Norton https://medium.com/message/everything-is-broken-81e5f33a24e1 "Malicious Word Doc Uses ActiveX To Infect" https://www.vmray.com/blog/malicious-word-doc-uses-activex-infect/ "Word Malware: OLE Exploited in Zero-Day Attack" https://www.vadesecure.com/en/word-doc-malware/ "Dynamic Data Exchange was frst introduced in 1987 with the release of Windows 2.0” https://en.wikipedia.org/wiki/Dynamic_Data_Exchange "As part of the December 2017 Patch Tuesday, Microsoft has shipped an Ofce update that disables the DDE feature in Word applications, after several malware campaigns have abused this feature to install malware.” https://www.bleepingcomputer.com/news/microsoft/microsoft-disables-dde-feature-in-word- to-prevent-further-malware-attacks/ "Dynamic Data Exchange was frst introduced in 1987 with the release of Windows 2.0” https://en.wikipedia.org/wiki/Dynamic_Data_Exchange "As part of the December 2017 Patch Tuesday, Microsoft has shipped an Ofce update that disables the DDE feature in Word applications, after several malware campaigns have abused this feature to install malware.” https://www.bleepingcomputer.com/news/microsoft/microsoft-disables-dde-feature-in-word- to-prevent-further-malware-attacks/ "Microsoft Ofce macro malware targets Macs" https://blog.malwarebytes.com/cybercrime/2017/02/microsoft-ofce-macro- malware-targets-macs/ "Beware PowerSniff Malware uses Word macros and PowerShell scripts" https://www.grahamcluley.com/beware-powersnif-malware/ -

Microsoft Update Testing
Microsoft Update Testing Microsoft provides the Windows Update Service that distributes bug fixes in the form of patches. Normally, Microsoft release patches via Windows Update every second Tuesday of each month and this has unofficially become known as 'Patch Tuesday'. To assure end users they can install Microsoft patches without adversely affecting existing installations of ClearSCADA, a set of regression tests are run on selected operating systems with released versions of ClearSCADA. Date: 11-06-2015 Operating Systems • Windows 7 SP1 (x64) • Windows Server 2008 R2 (x64) • Windows Server 2012 R2 • Windows 8.1 ClearSCADA 2010 R3.2 (72.5373), ClearSCADA 2013 R1.2 (73.4955), ClearSCADA 2013 R2.1 (RC Build 74.5213), ClearSCADA 2014 R1 (75.5387) and ClearSCADA 2015 R1 (76.5640) Installed Patches/Updates on Windows 7 (x64) Security Update for Windows 7, Windows Server 2008 R2, Windows Server 2008, and Windows Vista (KB3063858) https://support.microsoft.com/kb/3063858 Security Update for Windows 7, Windows Server 2008 R2, Windows Server 2008, and Windows Vista (KB3059317) https://support.microsoft.com/kb/3059317 Cumulative Security Update for Internet Explorer (KB3058515) https://support.microsoft.com/kb/3058515 Security Update for Windows 7, Windows Server 2008 R2, Windows Server 2008, Windows Vista, Windows Server 2003, and Windows XP Embedded (KB3057839) https://support.microsoft.com/kb/3057839 Security Update for Windows 7, Windows Server 2008 R2, Windows Server 2008, Windows Vista, Windows Server 2003, and Windows XP Embedded (KB3033890) -

What Are Kernel-Mode Rootkits?
www.it-ebooks.info Hacking Exposed™ Malware & Rootkits Reviews “Accessible but not dumbed-down, this latest addition to the Hacking Exposed series is a stellar example of why this series remains one of the best-selling security franchises out there. System administrators and Average Joe computer users alike need to come to grips with the sophistication and stealth of modern malware, and this book calmly and clearly explains the threat.” —Brian Krebs, Reporter for The Washington Post and author of the Security Fix Blog “A harrowing guide to where the bad guys hide, and how you can find them.” —Dan Kaminsky, Director of Penetration Testing, IOActive, Inc. “The authors tackle malware, a deep and diverse issue in computer security, with common terms and relevant examples. Malware is a cold deadly tool in hacking; the authors address it openly, showing its capabilities with direct technical insight. The result is a good read that moves quickly, filling in the gaps even for the knowledgeable reader.” —Christopher Jordan, VP, Threat Intelligence, McAfee; Principal Investigator to DHS Botnet Research “Remember the end-of-semester review sessions where the instructor would go over everything from the whole term in just enough detail so you would understand all the key points, but also leave you with enough references to dig deeper where you wanted? Hacking Exposed Malware & Rootkits resembles this! A top-notch reference for novices and security professionals alike, this book provides just enough detail to explain the topics being presented, but not too much to dissuade those new to security.” —LTC Ron Dodge, U.S. -

Installing, Using and Testing Microsoft Windows Driver Kit (WDK)
www.installsetupconfig.com Installing, Using and Testing Microsoft Windows Driver Kit (WDK) What do we have in this session? Introduction Installing the WDK The Windows Debuggers Installing Symbols Package The WinDbg Starting WinDbg Verifying WDK Installation Steps on Using WDK and Building Windows Driver from Code Sample Building a Windows Driver Sample Drivers and Services Installing/Registering a Driver Starting a Driver Viewing Driver Output Unloading a Driver Print Devices: Generic Text-Only Driver Sample Useful WDK references: Introduction The Windows machine specification used in this session are: 1. Operating System : Windows XP Pro SP2 2. RAM : 2 GB DDR2 3. HDD : 160++GB 4. Display : 128 MB ATI PCI Express 5. Processor : Intel Core 2 Duo 4400 2.00 GHz The DDK has been superseded by the Windows Driver Kit (WDK). While the DDK can be downloaded openly, you may need to register for free and participate in the respective Microsoft community to download WDK. Microsoft said that the WDK should be used for the following reasons: 1. Use the Windows Vista build environments in the WDK to build drivers that use new features or functionality available only in Windows Vista. 2. Use the Windows Server 2003 build environments in the WDK to build drivers that use new features or functionality available only in Windows Server 2003. 3. Use the Windows XP build environments in the WDK to build drivers that do not use new functionality available only in Windows Vista or only in Windows Server 2003 and that are targeted for either Windows XP or Windows Server 1 www.installsetupconfig.com 2003 and Windows XP. -

Support for Microsoft Office 2007
GE Healthcare Invasive Cardiology Security Website Interventional - Invasive Cardiology Product Group: Interventional Invasive Products Mac-Lab IT/XT/XTi, CardioLab IT/XT/XTi, Products: SpecialsLab and ComboLab IT/XT/XTi Recording Systems Versions: 6.8.1, 6.8, 6.5.6, 6.5.4, 6.5.3 Subject: Security Information Date: 16-August-2019 Summary The following information is provided to GE Healthcare Technologies customers in regards to known technical security vulnerabilities associated with Mac-Lab® Hemodynamic, CardioLab® Electrophysiology, SpecialsLab and ComboLab IT Recording Systems for Cath Lab, EP Lab and other interventional labs as well as the Centricity® Cardiology Data Management Systems. Security Patch Base Configuration The security patch base configuration of the Mac-Lab IT/XT/XTi and CardioLab IT/XT/XTi product at release is listed within the MLCL Base Configuration under the Hemodynamic, Electrophysiology and Cardiovascular Information Technologies section of the http://www3.gehealthcare.com/en/Support/Invasive_Cardiology_Product_Security website. Process The following actions are taken whenever Microsoft/OEMs releases new security patches: • The Invasive Cardiology Engineering Team performs a security analysis process for supported Mac-Lab IT/XT/XTi, CardioLab IT/XT/XTi, GE Client Review and INW Server hardware/software. • If a vulnerability meets Mac-Lab IT/XT/XTi and CardioLab IT/XT/XTi validation criteria, the vulnerability is communicated through the GEHC Product Security Database and Invasive Cardiology Security Website within Three weeks of the patch release. Page 1 of 88 GE Healthcare/16-August-2019 GE Healthcare • Upon validation of the Mac-Lab IT/XT/XTi and CardioLab IT/XT/XTi vulnerability, the GEHC Product Security Database and Invasive Cardiology Security Website and affected Mac-Lab IT/XT/XTi and CardioLab IT/XT/XTi Security Patch Installation Instructions are updated. -
CW MCU V10.X Service Pack Updater
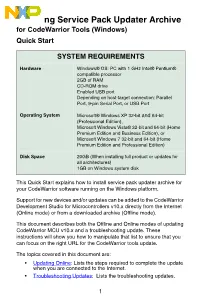
Installing Service Pack Updater Archive for CodeWarrior Tools (Windows) Quick Start SYSTEM REQUIREMENTS Hardware Windows® OS: PC with 1 GHz Intel® Pentium® compatible processor 2GB of RAM CD-ROM drive Enabled USB port Depending on host-target connection: Parallel Port, 9-pin Serial Port, or USB Port Operating System Microsoft® Windows XP 32-bit and 64-bit (Professional Edition), Microsoft Windows Vista® 32-bit and 64-bit (Home Premium Edition and Business Edition), or Microsoft Windows 7 32-bit and 64-bit (Home Premium Edition and Professional Edition) Disk Space 20GB (When installing full product or updates for all architectures) 1GB on Windows system disk This Quick Start explains how to install service pack updater archive for your CodeWarrior software running on the Windows platform. Support for new devices and/or updates can be added to the CodeWarrior Development Studio for Microcontrollers v10.x directly from the Internet (Online mode) or from a downloaded archive (Offline mode). This document describes both the Offline and Online modes of updating CodeWarrior MCU v10.x and a troubleshooting update. These instructions will show you how to manipulate that list to ensure that you can focus on the right URL for the CodeWarrior tools update. The topics covered in this document are: • Updating Online: Lists the steps required to complete the update when you are connected to the Internet. • Troubleshooting Updates: Lists the troubleshooting updates. 1 • Updating Offline: Lists the steps required to complete the update when you are not connected to the Internet. NOTE To ensure successful installation of service packs, updates, and patches select Restart in the File menu to perform a CodeWarrior restart.