Microsoft Service Pack & Security Bulletin Support
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

ENDPOINT MANAGEMENT 1 Information Systems Managers
STAFF SYMPOSIUM SERIES INFORMATION TECHNOLOGY TRACK FACILITATORS Carl Brooks System Manager ‐ Detroit, MI Chapter 13 Standing Trustee – Tammy L. Terry Debbie Smith System Manager – Robinsonville, NJ Chapter 13 Standing Trustee – Al Russo Scot Turner System Manager –Las Vegas, NV Chapter 13 Standing Trustee – Rick Yarnall Tom O’Hern Program Manager, ICF International, Baltimore, MD STACS ‐ Standing Trustee Alliance for Computer Security STAFF SYMPOSIUM ‐ IT TRACK 5/11/2017 SESSION 4 ‐ ENDPOINT MANAGEMENT 1 Information Systems Managers Windows 10 Debbie Smith System Manager Regional Staff Symposium ‐ IT Track May 11 and 12, 2017 Las Vegas, NV STAFF SYMPOSIUM ‐ IT TRACK 5/11/2017 SESSION 4 ‐ ENDPOINT MANAGEMENT 2 Windows lifecycle fact sheet End of support refers to the date when Microsoft no longer provides automatic fixes, updates, or online technical assistance. This is the time to make sure you have the latest available update or service pack installed. Without Microsoft support, you will no longer receive security updates that can help protect your PC from harmful viruses, spyware, and other malicious software that can steal your personal information. Client operating systems Latest update End of mainstream End of extended or service pack support support Windows XP Service Pack 3April 14, 2009 April 8, 2014 Windows Vista Service Pack 2April 10, 2012 April 11, 2017 Windows 7* Service Pack 1 January 13, 2015 January 14, 2020 Windows 8 Windows 8.1 January 9, 2018 January 10, 2023 Windows 10, July 2015 N/A October 13, 2020 October 14, 2025 * Support for Windows 7 RTM without service packs ended on April 9, 2013. -

Windows 7 Operating Guide
Welcome to Windows 7 1 1 You told us what you wanted. We listened. This Windows® 7 Product Guide highlights the new and improved features that will help deliver the one thing you said you wanted the most: Your PC, simplified. 3 3 Contents INTRODUCTION TO WINDOWS 7 6 DESIGNING WINDOWS 7 8 Market Trends that Inspired Windows 7 9 WINDOWS 7 EDITIONS 10 Windows 7 Starter 11 Windows 7 Home Basic 11 Windows 7 Home Premium 12 Windows 7 Professional 12 Windows 7 Enterprise / Windows 7 Ultimate 13 Windows Anytime Upgrade 14 Microsoft Desktop Optimization Pack 14 Windows 7 Editions Comparison 15 GETTING STARTED WITH WINDOWS 7 16 Upgrading a PC to Windows 7 16 WHAT’S NEW IN WINDOWS 7 20 Top Features for You 20 Top Features for IT Professionals 22 Application and Device Compatibility 23 WINDOWS 7 FOR YOU 24 WINDOWS 7 FOR YOU: SIMPLIFIES EVERYDAY TASKS 28 Simple to Navigate 28 Easier to Find Things 35 Easy to Browse the Web 38 Easy to Connect PCs and Manage Devices 41 Easy to Communicate and Share 47 WINDOWS 7 FOR YOU: WORKS THE WAY YOU WANT 50 Speed, Reliability, and Responsiveness 50 More Secure 55 Compatible with You 62 Better Troubleshooting and Problem Solving 66 WINDOWS 7 FOR YOU: MAKES NEW THINGS POSSIBLE 70 Media the Way You Want It 70 Work Anywhere 81 New Ways to Engage 84 INTRODUCTION TO WINDOWS 7 6 WINDOWS 7 FOR IT PROFESSIONALS 88 DESIGNING WINDOWS 7 8 WINDOWS 7 FOR IT PROFESSIONALS: Market Trends that Inspired Windows 7 9 MAKE PEOPLE PRODUCTIVE ANYWHERE 92 WINDOWS 7 EDITIONS 10 Remove Barriers to Information 92 Windows 7 Starter 11 Access -

Adaptive Android Kernel Live Patching
Adaptive Android Kernel Live Patching Yue Chen Yulong Zhang Zhi Wang Liangzhao Xia Florida State University Baidu X-Lab Florida State University Baidu X-Lab Chenfu Bao Tao Wei Baidu X-Lab Baidu X-Lab Abstract apps contain sensitive personal data, such as bank ac- counts, mobile payments, private messages, and social Android kernel vulnerabilities pose a serious threat to network data. Even TrustZone, widely used as the se- user security and privacy. They allow attackers to take cure keystore and digital rights management in Android, full control over victim devices, install malicious and un- is under serious threat since the compromised kernel en- wanted apps, and maintain persistent control. Unfortu- ables the attacker to inject malicious payloads into Trust- nately, most Android devices are never timely updated Zone [42, 43]. Therefore, Android kernel vulnerabilities to protect their users from kernel exploits. Recent An- pose a serious threat to user privacy and security. droid malware even has built-in kernel exploits to take Tremendous efforts have been put into finding (and ex- advantage of this large window of vulnerability. An ef- ploiting) Android kernel vulnerabilities by both white- fective solution to this problem must be adaptable to lots hat and black-hat researchers, as evidenced by the sig- of (out-of-date) devices, quickly deployable, and secure nificant increase of kernel vulnerabilities disclosed in from misuse. However, the fragmented Android ecosys- Android Security Bulletin [3] in recent years. In ad- tem makes this a complex and challenging task. dition, many kernel vulnerabilities/exploits are publicly To address that, we systematically studied 1;139 An- available but never reported to Google or the vendors, droid kernels and all the recent critical Android ker- let alone patched (e.g., exploits in Android rooting nel vulnerabilities. -

Introduction to Windows 7
[Not for Circulation] Introduction to Windows 7 This document provides a basic overview of the new and enhanced features of Windows 7 as well as instructions for how to request an upgrade. Windows 7 at UIS Windows 7 is Microsoft’s latest operating system. Beginning in the fall of 2010, UIS will upgrade all classroom and lab PCs to Windows 7. Any new PC that is ordered will automatically come installed with Windows 7. To request an upgrade, contact the Technology Support Center (TSC) at 217/206-6000 or [email protected]. The TSC will evaluate your machine to see if it’s capable of running Windows 7. (Your computer needs a dual core processor and at least 2 GB of RAM.) Please note that University licensing does NOT cover distribution of Windows 7 for personally owned computers. However, it is available for a discounted price via the WebStore at http://webstore.illinois.edu. What to Consider Before Upgrading There is no direct upgrade path from Windows XP to Windows 7. Therefore, the TSC will take your computer, save your files, and install Windows 7 on a clean hard drive. Please budget a couple days for this process. In some cases, you may have older devices that will not work with Windows 7. While many vendors are providing and will continue to provide drivers for their hardware, in some cases, printers, scanners, and other devices that are more than 5 years old may have issues running on Windows 7. To check the compatibility of your devices with Windows 7, visit the Microsoft Windows 7 Compatibility Center at http://www.microsoft.com/windows/compatibility/windows-7/en-us/default.aspx. -
Performing a Windows 7 Upgrade from Windows Vista
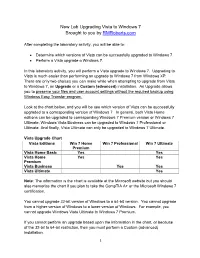
New Lab Upgrading Vista to Windows 7 Brought to you by RMRoberts.com After completing the laboratory activity, you will be able to: Determine which versions of Vista can be successfully upgraded to Windows 7. Perform a Vista upgrade o Windows 7. In this laboratory activity, you will perform a Vista upgrade to Windows 7. Upgrading to Vista is much easier than performing an upgrade to Windows 7 from Windows XP. There are only two choices you can make while when attempting to upgrade from Vista to Windows 7, an Upgrade or a Custom (advanced) installation. An Upgrade allows you to preserve your files and user account settings without the required backup using Windows Easy Transfer program. Look at the chart below, and you will be see which version of Vista can be successfully upgraded to a corresponding version of Windows 7. In general, both Vista Home editions can be upgraded to corresponding Windows 7 Premium version or Windows 7 Ultimate. Windows Vista Business can be upgraded to Windows 7 Professional or Ultimate. And finally, Vista Ultimate can only be upgraded to Windows 7 Ultimate. Vista Upgrade Chart Vista Editions Win 7 Home Win 7 Professional Win 7 Ultimate Premium Vista Home Basic Yes Yes Vista Home Yes Yes Premium Vista Business Yes Yes Vista Ultimate Yes Note: The information is the chart is available at the Microsoft website but you should also memorize the chart if you plan to take the CompTIA A+ or the Microsoft Windows 7 certification. You cannot upgrade 32-bit version of Windows to a 64-bit version. -
Intel® HD Graphics 5300 12 4.4 2.0 Yes Yes
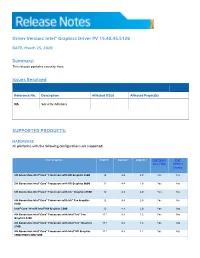
Driver Version: Intel® Graphics Driver PV 15.40.45.5126 DATE: March 25, 2020 Summary: This release contains security fixes. Issues Resolved Reference No. Description Affected OS(s) Affected Project(s) NA Security Advisory SUPPORTED PRODUCTS: HARDWARE All platforms with the following configurations are supported: Intel® Graphics1 DirectX*2 OpenGL* OpenCL* Intel® Quick Intel® Sync Video Wireless Display 5th Generation Intel® Core™ Processors with HD Graphics 5500 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with HD Graphics 6000 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with Iris™ Graphics 6100 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with Iris™ Pro Graphics 12 4.4 2.0 Yes Yes 6200 Intel® Core™ M with Intel® HD Graphics 5300 12 4.4 2.0 Yes Yes 4th Generation Intel® Core™ Processors with Intel® Iris™ Pro 11.1 4.3 1.2 Yes Yes Graphics 5200 4th Generation Intel® Core™ Processors with Intel® Iris™ Graphics 11.1 4.3 1.2 Yes Yes 5100 4th Generation Intel® Core™ Processors with Intel® HD Graphics 11.1 4.3 1.2 Yes Yes 5000/4600/4400/4200 Intel® Pentium® and Celeron® Processors with Intel® HD Graphics 11.1 4.3 1.2 Yes Yes based on 4th and 5th Generation Intel® Core™ Pentium®, Celeron®, and Atom™ processors based on Braswell and 12 4.3 2.0 Yes Yes CherryTrail. SOFTWARE On 4th Generation Intel Core processors and related Pentium/Celeron: • Microsoft Windows 10® 64-bit, 32-bit* *32-bit support is limited to particular SKU’s. -

Digital Vision Network 5000 Series BCM Motherboard BIOS Upgrade
Digital Vision Network 5000 Series BCM™ Motherboard BIOS Upgrade Instructions October, 2011 24-10129-128 Rev. – Copyright 2011 Johnson Controls, Inc. All Rights Reserved (805) 522-5555 www.johnsoncontrols.com No part of this document may be reproduced without the prior permission of Johnson Controls, Inc. Cardkey P2000, BadgeMaster, and Metasys are trademarks of Johnson Controls, Inc. All other company and product names are trademarks or registered trademarks of their respective owners. These instructions are supplemental. Some times they are supplemental to other manufacturer’s documentation. Never discard other manufacturer’s documentation. Publications from Johnson Controls, Inc. are not intended to duplicate nor replace other manufacturer’s documentation. Due to continuous development of our products, the information in this document is subject to change without notice. Johnson Controls, Inc. shall not be liable for errors contained herein or for incidental or consequential damages in connection with furnishing or use of this material. Contents of this publication may be preliminary and/or may be changed at any time without any obligation to notify anyone of such revision or change, and shall not be regarded as a warranty. If this document is translated from the original English version by Johnson Controls, Inc., all reasonable endeavors will be used to ensure the accuracy of translation. Johnson Controls, Inc. shall not be liable for any translation errors contained herein or for incidental or consequential damages in connection -

Guide to Enterprise Patch Management Technologies
NIST Special Publication 800-40 Revision 3 Guide to Enterprise Patch Management Technologies Murugiah Souppaya Karen Scarfone C O M P U T E R S E C U R I T Y NIST Special Publication 800-40 Revision 3 Guide to Enterprise Patch Management Technologies Murugiah Souppaya Computer Security Division Information Technology Laboratory Karen Scarfone Scarfone Cybersecurity Clifton, VA July 2013 U.S. Department of Commerce Penny Pritzker, Secretary National Institute of Standards and Technology Patrick D. Gallagher, Under Secretary of Commerce for Standards and Technology and Director Authority This publication has been developed by NIST to further its statutory responsibilities under the Federal Information Security Management Act (FISMA), Public Law (P.L.) 107-347. NIST is responsible for developing information security standards and guidelines, including minimum requirements for Federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate Federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130, Section 8b(3), Securing Agency Information Systems, as analyzed in Circular A- 130, Appendix IV: Analysis of Key Sections. Supplemental information is provided in Circular A-130, Appendix III, Security of Federal Automated Information Resources. Nothing in this publication should be taken to contradict the standards and guidelines made mandatory and binding on Federal agencies by the Secretary of Commerce under statutory authority. Nor should these guidelines be interpreted as altering or superseding the existing authorities of the Secretary of Commerce, Director of the OMB, or any other Federal official. -

Android 10 OS Update Instruction for Family of Products on SDM660
Android 10 OS Update Instruction for Family of Products on SDM660 1 Contents 1. A/B (Seamless) OS Update implementation on SDM660 devices ................................................................................................... 2 2. How AB system is different to Non-AB system ............................................................................................................................... 3 3. Android AB Mode for OS Update .................................................................................................................................................... 4 4. Recovery Mode for OS Update ........................................................................................................................................................ 4 5. Reset Packages and special recovery packages ................................................................................................................................ 4 6. OS Upgrade and Downgrade ............................................................................................................................................................ 5 7. OS Upgrade and Downgrade via EMMs .......................................................................................................................................... 6 8. AB Streaming Update ....................................................................................................................................................................... 7 9. User Notification for Full OTA package -

Students,Faculty & Staff Guide for Windows 7
iM Students,Faculty & Staff Guide for Windows 7 Prepared by Information Technology Division Lehman College, CUNY March 22, 2014 This document was originally prepared by Dickinson College. It was modified and adapted for use at Lehman College with the permission of Dickinson College. Introduction to Windows 7 Table of Contents Windows 7 Taskbar ...................................................................................................................................... 2 Show Desktop ............................................................................................................................................... 2 Start Menu..................................................................................................................................................... 3 Pin ................................................................................................................................................................. 4 Jump Lists ..................................................................................................................................................... 4 Snap .............................................................................................................................................................. 5 Windows Search ........................................................................................................................................... 6 Library (the new My Documents area & more) ........................................................................................... -

Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability
Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Hernan Ochoa Agustin Azubel [email protected] [email protected] Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Presentation goals: ‣ Describe the vulnerability in detail ‣ Explain & demonstrate exploitation • Three different exploitation methods ‣ Clear up misconceptions ‣ Determine vulnerability scope, severity and impact ‣ Share Conclusions BlackHat USA 2010 Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Vulnerability Information ‣ Flaws in Windows’ implementation of NTLM - attackers can access SMB service as authorized user - leads to read/write access to files, SMB shared resources in general and remote code execution ‣ Published February 2010 ‣ CVE-2010-0231, BID 38085 ‣ Advisory with Exploit Code: • http://www.hexale.org/advisories/OCHOA-2010-0209.txt ‣ Addressed by MS10-012 BlackHat USA 2010 Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Why talk about this vulnerability? ‣ Major 14-year old vulnerability affecting Windows Authentication Mechanism! - Basically, all Windows versions were affected (NT4, 2000, XP, 2003, Vista, 2008, 7) - Windows NT 4 released in ∼1996 - Windows NT 3.1 released in ∼1993 (∼17 years ago) - All this time, we assumed it was working correctly.. but it wasn’t... - Flew under the radar... BlackHat USA 2010 Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Why talk about this vulnerability? ‣ Interesting vulnerability, not your common buffer overflow - Issues in the Pseudo-Random Number Generator (PRNG) - Challenge-response protocol implementation issues - Replay attacks - Attack to predict challenges is interesting BlackHat USA 2010 Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Why talk about this vulnerability? ‣ There’s a lesson to be learned.. -

Patch My PC Microsoft Intune Setup Guide Document Versions
Patch My PC Microsoft Intune Setup Guide Document Versions: Date Version Description February 07, 2020 1.0 Initial Release March 03, 2020 1.1 User Interface Update August 18, 2020 1.2 Intune Update Feature September 24, 2020 1.3 Grammar and App Registration permission cleanup January 22, 2021 1.4 Update App Registration Permissions February 1, 2021 1.5 Clarified WSUS RSAT prerequisite March 4, 2021 1.6 Updated App Registration permission requirement for GroupMember.Read.All March 17, 2021 1.7 Updated text for Group.Read.All API permission March 26, 2021 1.8 Updated screenshot for new Application Manager Utility location Patch My PC – Publishing Service Setup Guide (Microsoft Intune) 1 System Requirements: • Microsoft .NET Framework 4.5 • Supported Operating Systems o Windows Server 2008 o Windows Server 2012 o Windows Server 2016 o Windows Server 2019 o Windows 10 (x64) – Microsoft Intune only Prerequisites: • WSUS Remote Server Administration Tools (RSAT) to be installed Download the latest MSI installer of the publishing service using the following URL: https://patchmypc.com/publishing- service-download Start the installation by double- clicking the downloaded MSI. Note: Depending on user account control settings, you may need to run an elevated command prompt and launch the MSI from the command prompt. Click Next in the Welcome Wizard Click Next in the Installation Folder Dialog Optionally, you can change the installation folder by clicking Browse… Click Install on the Ready to Install dialog. Note: if user-account control is enabled, you will receive a prompt “Do you want to allow this app to make changes to your device?” Click Yes on this prompt to allow installation Patch My PC – Publishing Service Setup Guide (Microsoft Intune) 2 If you are configuring the product for Intune Win32 application publishing only, you can check Enable Microsoft Intune standalone mode When this option is enabled, prerequisite checks related to WSUS and Configuration Manager are skipped.