BT to Honour Computer Pioneer Tommy Flowers, MBE
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

To What Extent Did British Advancements in Cryptanalysis During World War II Influence the Development of Computer Technology?
Portland State University PDXScholar Young Historians Conference Young Historians Conference 2016 Apr 28th, 9:00 AM - 10:15 AM To What Extent Did British Advancements in Cryptanalysis During World War II Influence the Development of Computer Technology? Hayley A. LeBlanc Sunset High School Follow this and additional works at: https://pdxscholar.library.pdx.edu/younghistorians Part of the European History Commons, and the History of Science, Technology, and Medicine Commons Let us know how access to this document benefits ou.y LeBlanc, Hayley A., "To What Extent Did British Advancements in Cryptanalysis During World War II Influence the Development of Computer Technology?" (2016). Young Historians Conference. 1. https://pdxscholar.library.pdx.edu/younghistorians/2016/oralpres/1 This Event is brought to you for free and open access. It has been accepted for inclusion in Young Historians Conference by an authorized administrator of PDXScholar. Please contact us if we can make this document more accessible: [email protected]. To what extent did British advancements in cryptanalysis during World War 2 influence the development of computer technology? Hayley LeBlanc 1936 words 1 Table of Contents Section A: Plan of Investigation…………………………………………………………………..3 Section B: Summary of Evidence………………………………………………………………....4 Section C: Evaluation of Sources…………………………………………………………………6 Section D: Analysis………………………………………………………………………………..7 Section E: Conclusion……………………………………………………………………………10 Section F: List of Sources………………………………………………………………………..11 Appendix A: Explanation of the Enigma Machine……………………………………….……...13 Appendix B: Glossary of Cryptology Terms.…………………………………………………....16 2 Section A: Plan of Investigation This investigation will focus on the advancements made in the field of computing by British codebreakers working on German ciphers during World War 2 (19391945). -

Theeccentric Engineer by Justin Pollard
106 TIME OUT COLUMNIST The name of Tommy Flowers deserves to be as well known as the computing industry giants who profited from his wartime efforts. TheEccentric Engineer by Justin Pollard PEOPLE Competition purpose machine, it was the first electronic computer. THE FORGOTTEN What are these Bletchley The device set to work on Park Wrens thinking as they Tunny intercepts. It also gained ENGINEER OF work on Colossus? The best a new name, thought up by BLETCHLEY PARK caption emailed to the members of the Women’s [email protected] by Royal Naval who operated the 23 March wins a pair of one-tonne, room-sized behemoth books from Haynes. – Colossus. A 2,400-valve version entered service four days before D-Day, providing crucial decrypts of Tunny messages in the lead-up to the invasion. It’s said system offering five trillion that Eisenhower had a Tunny times more combinations decrypt, courtesy of Colossus, than the 157 trillion offered in his hand as he gave the order by Enigma. The possibility to launch Operation Overlord. of getting bombes to crunch By the end of the war there that many permutations fast were ten Colossus machines at enough for the intelligence to Bletchley. After the surrender of have any value seemed remote. Germany, eight of them were The man charged with solving destroyed and the other two this conundrum was Max secretly moved to the peacetime Newman, whose ‘Hut F’ team was government intelligence centre, assigned the task of cracking the GCHQ, where one remained in ‘Tunny’ intercepts known to operation until 1960. -

How I Learned to Stop Worrying and Love the Bombe: Machine Research and Development and Bletchley Park
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by CURVE/open How I learned to stop worrying and love the Bombe: Machine Research and Development and Bletchley Park Smith, C Author post-print (accepted) deposited by Coventry University’s Repository Original citation & hyperlink: Smith, C 2014, 'How I learned to stop worrying and love the Bombe: Machine Research and Development and Bletchley Park' History of Science, vol 52, no. 2, pp. 200-222 https://dx.doi.org/10.1177/0073275314529861 DOI 10.1177/0073275314529861 ISSN 0073-2753 ESSN 1753-8564 Publisher: Sage Publications Copyright © and Moral Rights are retained by the author(s) and/ or other copyright owners. A copy can be downloaded for personal non-commercial research or study, without prior permission or charge. This item cannot be reproduced or quoted extensively from without first obtaining permission in writing from the copyright holder(s). The content must not be changed in any way or sold commercially in any format or medium without the formal permission of the copyright holders. This document is the author’s post-print version, incorporating any revisions agreed during the peer-review process. Some differences between the published version and this version may remain and you are advised to consult the published version if you wish to cite from it. Mechanising the Information War – Machine Research and Development and Bletchley Park Christopher Smith Abstract The Bombe machine was a key device in the cryptanalysis of the ciphers created by the machine system widely employed by the Axis powers during the Second World War – Enigma. -

War Machines: Women's Computing Work and the Underpinnings of the Data-Driven State, 1930-1946
Programmed Inequality How Britain Discarded Women Technologists and Lost Its Edge in Computing Marie Hicks HD 6135 H53 2017 The Library Mt. St. Vincent Univ. Halifax, N.S. B3M 2J6 The MIT Press Cambridge, Massachusetts London, England 1 War Machines: Women's Computing Work and the Underpinnings of the Data-Driven State, 1930-1946 In recent years, the restoration of Bletchley Park has attracted worldwide attention. The country estate in Milton Keynes, United Kingdom, was the site of the most important codebreaking operations of World War II and home to the first digital, electronic, programmable computer: the Colossus. The British-designed and manufactured Colossus computers, of which there were ten in all by war's end, were critical to the conduct of Allied wartime operations. Unlike their better-known U.S. counter part, the ENIAC, the Colossus computers were actually deployed during the war, actively changing its outcome. Kept secret for decades, the full import of the developments at Bletchley has only recently become widely known.1 Yet while popular culture has begun to recognize the importance of Bletchley's wartime operations, misunderstandings persist about the nature of the information work performed there. The 2014 blockbuster The Imitation Game, for instance, cleaves the Colossus computers from the narrative entirely in favor of building a "great man" narrative for a single codebreaker.2 Hidden within the story of Bletchley is a less popular narrative that cannot leverage the appeal of a lone genius and his accomplishments. Thousands of women worked at Bletchley during the war-most in tech nical roles.3 Although it is generally accepted that the striking and wide ranging roles of the mostly women workers within Bletchley Park give lie to stereotypes about computing as a traditionally masculine field, the contributions of these women have not been analyzed as constitutive of larger trends in the history of computing. -

On How a Kenya Policeman Ended up – Working in the Research and Development Division of a Supercomputer Manufacturer in America
On How a Kenya Policeman Ended Up – Working in the Research and Development Division of a Supercomputer Manufacturer in America Jitze Couperus When the Belgian Congo was granted independence in 1960, the country deteriorated into chaos within the first few days. Secessionist factions and inter-tribal warfare resulted in wide-spread anarchy, looting and bloodshed. It was this event that also triggered my leaving school early and even before I had sat for my final exams (for a “Higher School Certificate” or what were also known as “A Levels”). The Prince of Wales School was a boarding school for about 600 boys, and the dormitories were needed to house the stream of refugees from the Congo. I was a “senior” who had spent some years in the Combined Cadet Force while at school – referred to as the CCF in that context but probably more familiar to American readers as the equivalent of ROTC. While other boys were sent home, I was asked to stay on at school to help liaise with the Belgian refugees (I spoke Dutch) and help organize some of the inevitable chaos arranging for food, clothing and sanitation as the stream of refugees threatened to swamp our resources. However, once the situation at the school was under control, it was decided that my talents could be better used closer to the real action. Accordingly I was “called up” into the Kenya Regiment and then rapidly seconded (i.e. transferred) to the 4th Battalion Kings African Rifles in Uganda to help them deal with the ever growing refugee problem. -

BT Smart Hub: Marketing Claims Substantiation
BT Smart Hub: Marketing claims substantiation July 2016 BT Smart Hub marketing claims substantiation – July 2016 Contents 1.1 Introduction 3 1.2 How is the most powerful wi-fi tested? 4 Routers tested 4 What do we measure? 5 How do we test? 5 Devices used in the test 6 Where were the tests completed? 6 Sagemcom floor plan 6 BT floor plan 7 Live customer homes 7 1.3 Test set-up 8 1.4 Results 9 BT test house 2.4 GHz 9 BT test house 5 GHz 14 Sagemcom test house 2.4 GHz 17 Sagemcom test house 5 GHz 20 10 real homes 21 1.5 Conclusion 23 Appendix 1 - Test home floor plans 24 Appendix 2 - Coverage testing with Interference 34 Appendix 3 - TalkTalk Wi-Fi Hub 37 2 BT Smart Hub marketing claims substantiation – July 2016 1.1 Introduction The BT Smart Hub provides the UK’s most powerful wi-fi signal. The following report presents extensive in-home and lab wi-fi testing of the BT Smart Hub compared to all major UK broadband providers. At any distance from the router, the BT Smart Hub will always provide the most powerful wi-fi signal. The tests were based on the IEEE802.11T method, to • The tests capture speeds for normal user tasks. provide robust and repeatable data, taking into account • Turntables were used to ensure the routers did not previous Advertising Standards Authority (ASA) rulings and exhibit directionality and to ensure a fair test. guidance on wi-fi performance claims: • Hundreds of data-points were captured to ensure • The tests were carried out on 2.4 GHz and 5 GHz to results were repeatable and reliable. -

Alan Turing, Computing, Bletchley, and Mathematics, Wellington Public
Alan Turing, Computing, Bletchley, and Mathematics Rod Downey Victoria University Wellington New Zealand Downey's research is supported by the Marsden Fund, and this material also by the Newton Institute. Wellington, February 2015 Turing I Turing has become a larger than life figure following the movie \The Imitation Game". I which followed Andrew Hodges book \Alan Turing : The Enigma", I which followed the release of classified documents about WWII. I I will try to comment on aspects of Turing's work mentioned in the movie. I I will give extensive references if you want to follow this up, including the excellent Horizon documentary. I Posted to my web site. Type \rod downey" into google. Turing Award I The equivalent of the \Nobel Prize" in computer science is the ACM Turing Award. I It is for life work in computer science and worth about $1M. I Why? This award was made up (1966) was well before Bletchley became public knowledge. I (Aside) Prof. D. Ritchie (Codebreaker)-from \Station X, Pt 3" Alan Turing was one of the figures of the century. || There were great men at Bletchley Park, but in the long hall of history Turing's name will be remembered as Number One in terms of consequences for mankind. Logic I Aristotle and other early Greeks then \modern" re-invention: Leibnitz (early 18th C), Boole, Frege, etc. I We want a way to represent arguments, language, processes etc by formal symbols and manipulate them like we do numbers to determine, e.g. validity of argument. I Simplest modern formal system propositional logic. -

BT Group Plc Annual Report 2020 BT Group Plc Annual Report 2020 Strategic Report 1
BT Group plc Group BT Annual Report 2020 Beyond Limits BT Group plc Annual Report 2020 BT Group plc Annual Report 2020 Strategic report 1 New BT Halo. ... of new products and services Contents Combining the We launched BT Halo, We’re best of 4G, 5G our best ever converged Strategic report connectivity package. and fibre. ... of flexible TV A message from our Chairman 2 A message from our Chief Executive 4 packages About BT 6 investing Our range of new flexible TV Executive Committee 8 packages aims to disrupt the Customers and markets 10 UK’s pay TV market and keep Regulatory update 12 pace with the rising tide of in the streamers. Our business model 14 Our strategy 16 Strategic progress 18 ... of next generation Our stakeholders 24 future... fibre broadband Culture and colleagues 30 We expect to invest around Introducing the Colleague Board 32 £12bn to connect 20m Section 172 statement 34 premises by mid-to-late-20s Non-financial information statement 35 if the conditions are right. Digital impact and sustainability 36 Our key performance indicators 40 Our performance as a sustainable and responsible business 42 ... of our Group performance 43 A letter from the Chair of Openreach 51 best-in-class How we manage risk 52 network ... to keep us all Our principal risks and uncertainties 53 5G makes a measurable connected Viability statement 64 difference to everyday During the pandemic, experiences and opens we’re helping those who up even more exciting need us the most. Corporate governance report 65 new experiences. Financial statements 117 .. -

Martlesham Heath Area Specific Guidance June 2001
Supplementary Planning Guidance 12.8 Hi-Tech Cluster: Martlesham Heath Area Specific Guidance June 2001 Following the reforms to the Planning system through the enactment of the Planning and Compulsory Purchase Act 2004 all Supplementary Planning Guidance’s can only be kept for a maximum of three years. It is the District Council’s intention to review each Supplementary Planning Guidance in this time and reproduce these publications as Supplementary Planning Documents which will support the policies to be found in the Local Development Framework which is to replace the existing Suffolk Coastal Local Plan First Alteration, February 2001. Some Supplementary Planning Guidance dates back to the early 1990’s and may no longer be appropriate as the site or issue may have been resolved so these documents will be phased out of the production and will not support the Local Development Framework. Those to be kept will be reviewed and republished in accordance with new guidelines for public consultation. A list of those to be kept can be found in the Suffolk Coastal Local Development Scheme December 2004. Please be aware when reading this guidance that some of the Government organisations referred to no longer exist or do so under a different name. For example MAFF (Ministry for Agriculture, Fisheries and Food) is no longer in operation but all responsibilities and duties are now dealt with by DEFRA (Department for the Environment, Food and Rural Affairs). Another example may be the DETR (Department of Environment, Transport and Regions) whose responsibilities are now dealt with in part by the DCLG (Department of Communities & Local Government). -

Colossus and the Origins of Programmability
Colossus and the Origins of Programmability Draft for discussion at the 2016 SIGCIS Workshop. Do not quote or cite without permission of the authors. Thomas Haigh ([email protected]) and Mark Priestley ([email protected]) This is an initial draft of some material from our ongoing project to explore the history of Tommy Flowers, the ways in which Colossus was used and configured, and its place in the history of information technology. This work is sponsored by Mrs. L.D. Rope’s Second Charitable Trust. The current draft is very preliminary, so please do not quote, cite, or distribute without our permission. If names and references are confusing to you our apologies! Fortunately the basics of Colossus and Bletchley Park are well covered in Wikipedia. Colossus was a codebreaking device built by the British General Post Office at the end of 1943, under the direction of career telecommunications engineer Tommy Flowers. It entered use at Bletchley Park in 1944 to speed the work of codebreakers targeting what was then codenamed “fish,” a family of Lorenz teleprinter codes used for high level German military communication. Colossus was not a one‐off machine, like most early electronic computers, but the prototype for a family of ten “colossi,” in which later models incorporated some significant improvements. The machines were used by the Newmanry, a group under mathematician Max Newman, where ingenious codebreaking users discovered new applications for them which, in turn, shaped the provision of additional controls and capabilities in the later models. Unlike ENIAC, which began in modest secrecy but soon graced the front page of the New York Times, Colossus was highly classified and remained unknown to the public until the 1970s. -
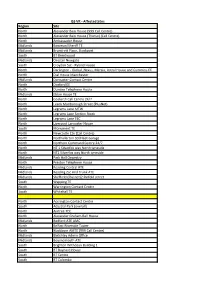
LTB 342.2019 Attachment 1
ISS VR - Affected Sites Region Site North Alexander Bain House (999 Call Centre) North Alexander Bain House (Thurso) (Call Centre) North Ambassador House Midlands Bowman/Sheriff TE Midlands Brundrett Place, Stockport South BT Brentwood Midlands Chester Newgate South Croydon Ssc - Ryland House North Darlington - Global ,Nexus, Mercia, Astral House and Cummins EE North Dial House Manchester Midlands Doncaster Contact Centre North Doxford EE North Dundee Telephone House Midlands Eldon House TE North Gosforth Call Centre 24/7 North Leeds Marlborough Street (PlusNet) North Legrams Lane MTW North Legrams Lane Section Stock North Legrams Lane TEC North Liverpool Lancaster House South Monument TE North Newcastle Cte (Call Centre) North Northallerton SD/Fleet Garage North Northern Command Centre 24/7 North NT 1 Silverfox way North tyneside North NT2 Silverfox way North tyneside Midlands Park Hall Oswestry North Preston Telephone House Midlands Reading Central ATE Midlands Reading Zsc And Trunk ATE Midlands Sheffield (Plusnet)2 Pinfold street South Wapping TE North Warrington Contact Centre South Whitehall TE North Accrington Contact Centre South Adastral Park (overall) North Aintree TEC North Alexander Graham Bell House Midlands Bedford ATE AMC North Belfast Riverside Tower North Blackburn AMTE (999 Call Centre) Midlands Bletchley Admin Office Midlands Bournemouth ATE South Brighton Withdean Building 1 South BT Baynard House South BT Centre South BT Colombo South BT Mill House South BT Tower South Canterbury Becket House South Crawley New TEC -

Inventing the Communications Revolution in Post-War Britain
Information and Control: Inventing the Communications Revolution in Post-War Britain Jacob William Ward UCL PhD History of Science and Technology 1 I, Jacob William Ward, confirm that the work presented in this thesis is my own. Where information has been derived from other sources, I confirm that this has been indicated in the thesis. 2 Abstract This thesis undertakes the first history of the post-war British telephone system, and addresses it through the lens of both actors’ and analysts’ emphases on the importance of ‘information’ and ‘control’. I explore both through a range of chapters on organisational history, laboratories, telephone exchanges, transmission technologies, futurology, transatlantic communications, and privatisation. The ideal of an ‘information network’ or an ‘information age’ is present to varying extents in all these chapters, as are deployments of different forms of control. The most pervasive, and controversial, form of control throughout this history is computer control, but I show that other forms of control, including environmental, spatial, and temporal, are all also important. I make three arguments: first, that the technological characteristics of the telephone system meant that its liberalisation and privatisation were much more ambiguous for competition and monopoly than expected; second, that information has been more important to the telephone system as an ideal to strive for, rather than the telephone system’s contribution to creating an apparent information age; third, that control is a more useful concept than information for analysing the history of the telephone system, but more work is needed to study the discursive significance of ‘control’ itself. 3 Acknowledgements There are many people to whom I owe thanks for making this thesis possible, and here I can only name some of them.