Phylogenetic Systematics Using POY Final Final.Book
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Phylogenetic Trees and Cladograms Are Graphical Representations (Models) of Evolutionary History That Can Be Tested
AP Biology Lab/Cladograms and Phylogenetic Trees Name _______________________________ Relationship to the AP Biology Curriculum Framework Big Idea 1: The process of evolution drives the diversity and unity of life. Essential knowledge 1.B.2: Phylogenetic trees and cladograms are graphical representations (models) of evolutionary history that can be tested. Learning Objectives: LO 1.17 The student is able to pose scientific questions about a group of organisms whose relatedness is described by a phylogenetic tree or cladogram in order to (1) identify shared characteristics, (2) make inferences about the evolutionary history of the group, and (3) identify character data that could extend or improve the phylogenetic tree. LO 1.18 The student is able to evaluate evidence provided by a data set in conjunction with a phylogenetic tree or a simple cladogram to determine evolutionary history and speciation. LO 1.19 The student is able create a phylogenetic tree or simple cladogram that correctly represents evolutionary history and speciation from a provided data set. [Introduction] Cladistics is the study of evolutionary classification. Cladograms show evolutionary relationships among organisms. Comparative morphology investigates characteristics for homology and analogy to determine which organisms share a recent common ancestor. A cladogram will begin by grouping organisms based on a characteristics displayed by ALL the members of the group. Subsequently, the larger group will contain increasingly smaller groups that share the traits of the groups before them. However, they also exhibit distinct changes as the new species evolve. Further, molecular evidence from genes which rarely mutate can provide molecular clocks that tell us how long ago organisms diverged, unlocking the secrets of organisms that may have similar convergent morphology but do not share a recent common ancestor. -

An Introduction to Phylogenetic Analysis
This article reprinted from: Kosinski, R.J. 2006. An introduction to phylogenetic analysis. Pages 57-106, in Tested Studies for Laboratory Teaching, Volume 27 (M.A. O'Donnell, Editor). Proceedings of the 27th Workshop/Conference of the Association for Biology Laboratory Education (ABLE), 383 pages. Compilation copyright © 2006 by the Association for Biology Laboratory Education (ABLE) ISBN 1-890444-09-X All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written permission of the copyright owner. Use solely at one’s own institution with no intent for profit is excluded from the preceding copyright restriction, unless otherwise noted on the copyright notice of the individual chapter in this volume. Proper credit to this publication must be included in your laboratory outline for each use; a sample citation is given above. Upon obtaining permission or with the “sole use at one’s own institution” exclusion, ABLE strongly encourages individuals to use the exercises in this proceedings volume in their teaching program. Although the laboratory exercises in this proceedings volume have been tested and due consideration has been given to safety, individuals performing these exercises must assume all responsibilities for risk. The Association for Biology Laboratory Education (ABLE) disclaims any liability with regards to safety in connection with the use of the exercises in this volume. The focus of ABLE is to improve the undergraduate biology laboratory experience by promoting the development and dissemination of interesting, innovative, and reliable laboratory exercises. -

A Phylogenetic Analysis of the Basal Ornithischia (Reptilia, Dinosauria)
A PHYLOGENETIC ANALYSIS OF THE BASAL ORNITHISCHIA (REPTILIA, DINOSAURIA) Marc Richard Spencer A Thesis Submitted to the Graduate College of Bowling Green State University in partial fulfillment of the requirements of the degree of MASTER OF SCIENCE December 2007 Committee: Margaret M. Yacobucci, Advisor Don C. Steinker Daniel M. Pavuk © 2007 Marc Richard Spencer All Rights Reserved iii ABSTRACT Margaret M. Yacobucci, Advisor The placement of Lesothosaurus diagnosticus and the Heterodontosauridae within the Ornithischia has been problematic. Historically, Lesothosaurus has been regarded as a basal ornithischian dinosaur, the sister taxon to the Genasauria. Recent phylogenetic analyses, however, have placed Lesothosaurus as a more derived ornithischian within the Genasauria. The Fabrosauridae, of which Lesothosaurus was considered a member, has never been phylogenetically corroborated and has been considered a paraphyletic assemblage. Prior to recent phylogenetic analyses, the problematic Heterodontosauridae was placed within the Ornithopoda as the sister taxon to the Euornithopoda. The heterodontosaurids have also been considered as the basal member of the Cerapoda (Ornithopoda + Marginocephalia), the sister taxon to the Marginocephalia, and as the sister taxon to the Genasauria. To reevaluate the placement of these taxa, along with other basal ornithischians and more derived subclades, a phylogenetic analysis of 19 taxonomic units, including two outgroup taxa, was performed. Analysis of 97 characters and their associated character states culled, modified, and/or rescored from published literature based on published descriptions, produced four most parsimonious trees. Consistency and retention indices were calculated and a bootstrap analysis was performed to determine the relative support for the resultant phylogeny. The Ornithischia was recovered with Pisanosaurus as its basalmost member. -

Interpreting Cladograms Notes
Interpreting Cladograms Notes INTERPRETING CLADOGRAMS BIG IDEA: PHYLOGENIES DEPICT ANCESTOR AND DESCENDENT RELATIONSHIPS AMONG ORGANISMS BASED ON HOMOLOGY THESE EVOLUTIONARY RELATIONSHIPS ARE REPRESENTED BY DIAGRAMS CALLED CLADOGRAMS (BRANCHING DIAGRAMS THAT ORGANIZE RELATIONSHIPS) What is a Cladogram ● A diagram which shows ● Is not an evolutionary ___________ among tree, ___________show organisms. how ancestors are related ● Lines branching off other to descendants or how lines. The lines can be much they have changed traced back to where they branch off. These branching off points represent a hypothetical ancestor. Parts of a Cladogram Reading Cladograms ● Read like a family tree: show ________of shared ancestry between lineages. • When an ancestral lineage______: speciation is indicated due to the “arrival” of some new trait. Each lineage has unique ____to itself alone and traits that are shared with other lineages. each lineage has _______that are unique to that lineage and ancestors that are shared with other lineages — common ancestors. Quick Question #1 ●What is a_________? ● A group that includes a common ancestor and all the descendants (living and extinct) of that ancestor. Reading Cladogram: Identifying Clades ● Using a cladogram, it is easy to tell if a group of lineages forms a clade. ● Imagine clipping a single branch off the phylogeny ● all of the organisms on that pruned branch make up a clade Quick Question #2 ● Looking at the image to the right: ● Is the green box a clade? ● The blue? ● The pink? ● The orange? Reading Cladograms: Clades ● Clades are nested within one another ● they form a nested hierarchy. ● A clade may include many thousands of species or just a few. -

Conceptual Issues in Phylogeny, Taxonomy, and Nomenclature
Contributions to Zoology, 66 (1) 3-41 (1996) SPB Academic Publishing bv, Amsterdam Conceptual issues in phylogeny, taxonomy, and nomenclature Alexandr P. Rasnitsyn Paleontological Institute, Russian Academy ofSciences, Profsoyuznaya Street 123, J17647 Moscow, Russia Keywords: Phylogeny, taxonomy, phenetics, cladistics, phylistics, principles of nomenclature, type concept, paleoentomology, Xyelidae (Vespida) Abstract On compare les trois approches taxonomiques principales développées jusqu’à présent, à savoir la phénétique, la cladis- tique et la phylistique (= systématique évolutionnaire). Ce Phylogenetic hypotheses are designed and tested (usually in dernier terme s’applique à une approche qui essaie de manière implicit form) on the basis ofa set ofpresumptions, that is, of à les traits fondamentaux de la taxonomic statements explicite représenter describing a certain order of things in nature. These traditionnelle en de leur et particulier son usage preuves ayant statements are to be accepted as such, no matter whatever source en même temps dans la similitude et dans les relations de evidence for them exists, but only in the absence ofreasonably parenté des taxons en question. L’approche phylistique pré- sound evidence pleading against them. A set ofthe most current sente certains avantages dans la recherche de réponses aux phylogenetic presumptions is discussed, and a factual example problèmes fondamentaux de la taxonomie. ofa practical realization of the approach is presented. L’auteur considère la nomenclature A is made of the three -

Phylogenetic Analysis
Phylogenetic Analysis Aristotle • Through classification, one might discover the essence and purpose of species. Nelson & Platnick (1981) Systematics and Biogeography Carl Linnaeus • Swedish botanist (1700s) • Listed all known species • Developed scheme of classification to discover the plan of the Creator 1 Linnaeus’ Main Contributions 1) Hierarchical classification scheme Kingdom: Phylum: Class: Order: Family: Genus: Species 2) Binomial nomenclature Before Linnaeus physalis amno ramosissime ramis angulosis glabris foliis dentoserratis After Linnaeus Physalis angulata (aka Cutleaf groundcherry) 3) Originated the practice of using the ♂ - (shield and arrow) Mars and ♀ - (hand mirror) Venus glyphs as the symbol for male and female. Charles Darwin • Species evolved from common ancestors. • Concept of closely related species being more recently diverged from a common ancestor. Therefore taxonomy might actually represent phylogeny! The phylogeny and classification of life a proposed by Haeckel (1866). 2 Trees - Rooted and Unrooted 3 Trees - Rooted and Unrooted ABCDEFGHIJ A BCDEH I J F G ROOT ROOT D E ROOT A F B H J G C I 4 Monophyletic: A group composed of a collection of organisms, including the most recent common ancestor of all those organisms and all the descendants of that most recent common ancestor. A monophyletic taxon is also called a clade. Paraphyletic: A group composed of a collection of organisms, including the most recent common ancestor of all those organisms. Unlike a monophyletic group, a paraphyletic group does not include all the descendants of the most recent common ancestor. Polyphyletic: A group composed of a collection of organisms in which the most recent common ancestor of all the included organisms is not included, usually because the common ancestor lacks the characteristics of the group. -
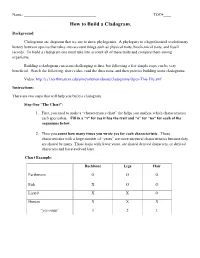
How to Build a Cladogram
Name: _____________________________________ TOC#____ How to Build a Cladogram. Background: Cladograms are diagrams that we use to show phylogenies. A phylogeny is a hypothesized evolutionary history between species that takes into account things such as physical traits, biochemical traits, and fossil records. To build a cladogram one must take into account all of these traits and compare them among organisms. Building a cladogram can seem challenging at first, but following a few simple steps can be very beneficial. Watch the following, short video, read the directions, and then practice building some cladograms. Video: http://ccl.northwestern.edu/simevolution/obonu/cladograms/Open-This-File.swf Instructions: There are two steps that will help you build a cladogram. Step One “The Chart”: 1. First, you need to make a “characteristics chart” the helps you analyze which characteristics each specieshas. Fill in a “x” for yes it has the trait and “o” for “no” for each of the organisms below. 2. Then you count how many times you wrote yes for each characteristic. Those characteristics with a large number of “yeses” are more ancestral characteristics because they are shared by many. Those traits with fewer yeses, are shared derived characters, or derived characters and have evolved later. Chart Example: Backbone Legs Hair Earthworm O O O Fish X O O Lizard X X O Human X X X “yes count” 3 2 1 Step Two “The Venn Diagram”: This step will help you to learn to build Cladograms, but once you figure it out, you may not always need to do this step. -

Introduction to Phylogenetics Workshop on Molecular Evolution 2018 Marine Biological Lab, Woods Hole, MA
Introduction to Phylogenetics Workshop on Molecular Evolution 2018 Marine Biological Lab, Woods Hole, MA. USA Mark T. Holder University of Kansas Outline 1. phylogenetics is crucial for comparative biology 2. tree terminology 3. why phylogenetics is difficult 4. parsimony 5. distance-based methods 6. theoretical basis of multiple sequence alignment Part #1: phylogenetics is crucial for biology Species Habitat Photoprotection 1 terrestrial xanthophyll 2 terrestrial xanthophyll 3 terrestrial xanthophyll 4 terrestrial xanthophyll 5 terrestrial xanthophyll 6 aquatic none 7 aquatic none 8 aquatic none 9 aquatic none 10 aquatic none slides by Paul Lewis Phylogeny reveals the events that generate the pattern 1 pair of changes. 5 pairs of changes. Coincidence? Much more convincing Many evolutionary questions require a phylogeny Determining whether a trait tends to be lost more often than • gained, or vice versa Estimating divergence times (Tracy Heath Sunday + next • Saturday) Distinguishing homology from analogy • Inferring parts of a gene under strong positive selection (Joe • Bielawski and Belinda Chang next Monday) Part 2: Tree terminology A B C D E terminal node (or leaf, degree 1) interior node (or vertex, degree 3+) split (bipartition) also written AB|CDE or portrayed **--- branch (edge) root node of tree (de gree 2) Monophyletic groups (\clades"): the basis of phylogenetic classification black state = a synapomorphy white state = a plesiomorphy Paraphyletic Polyphyletic grey state is an autapomorphy (images from Wikipedia) Branch rotation does not matter ACEBFDDAFBEC Rooted vs unrooted trees ingroup: the focal taxa outgroup: the taxa that are more distantly related. Assuming that the ingroup is monophyletic with respect to the outgroup can root a tree. -

Phylogenetic Systematics As the Basis of Comparative Biology
SMITHSONIAN CONTRIBUTIONS TO BOTANY NUMBER 73 Phylogenetic Systematics as the Basis of Comparative Biology KA. Funk and Daniel R. Brooks SMITHSONIAN INSTITUTION PRESS Washington, D.C. 1990 ABSTRACT Funk, V.A. and Daniel R. Brooks. Phylogenetic Systematics as the Basis of Comparative Biology. Smithsonian Contributions to Botany, number 73, 45 pages, 102 figures, 12 tables, 199O.-Evolution is the unifying concept of biology. The study of evolution can be approached from a within-lineage (microevolution) or among-lineage (macroevolution) perspective. Phylogenetic systematics (cladistics) is the appropriate basis for all among-liieage studies in comparative biology. Phylogenetic systematics enhances studies in comparative biology in many ways. In the study of developmental constraints, the use of such phylogenies allows for the investigation of the possibility that ontogenetic changes (heterochrony) alone may be sufficient to explain the perceived magnitude of phenotypic change. Speciation via hybridization can be suggested, based on the character patterns of phylogenies. Phylogenetic systematics allows one to examine the potential of historical explanations for biogeographic patterns as well as modes of speciation. The historical components of coevolution, along with ecological and behavioral diversification, can be compared to the explanations of adaptation and natural selection. Because of the explanatory capabilities of phylogenetic systematics, studies in comparative biology that are not based on such phylogenies fail to reach their potential. OFFICIAL PUBLICATION DATE is handstamped in a limited number of initial copies and is recorded in the Institution's annual report, Srnithonhn Year. SERIES COVER DESIGN: Leaf clearing from the katsura tree Cercidiphyllumjaponicum Siebold and Zuccarini. Library of Cmgrcss Cataloging-in-PublicationDiaa Funk, V.A (Vicki A.), 1947- PhylogmttiC ryrtcmaticsas tk basis of canpamtive biology / V.A. -

Taxonomy and Classification Goals: Un Ders Tan D Traditi Onal and Hi Erarchi Cal Cl Assifi Cati Ons of Biodiversity, and What Information Classifications May Contain
Taxonomy and classification Goals: Un ders tan d tra ditional and hi erarchi cal cl assifi cati ons of biodiversity, and what information classifications may contain. Readings: 1. Chapter 1. Figure 1-1 from Pough et al. Taxonomy and classification (cont ’d) Some new words This is a cladogram. Each branching that are very poiiint is a nod dEhbhe. Each branch, starti ng important: at the node, is a clade. 9 Cladogram 9 Clade 9 Synapomorphy (Shared, derived character) 9 Monophyly; monophyletic 9 PhlParaphyly; parap hlihyletic 9 Polyphyly; polyphyletic Definitions of cladogram on the Web: A dichotomous phylogenetic tree that branches repeatedly, suggesting the classification of molecules or org anisms based on the time sequence in which evolutionary branches arise. xray.bmc.uu.se/~kenth/bioinfo/glossary.html A tree that depicts inferred historical branching relationships among entities. Unless otherwise stated, the depicted branch lengt hs in a cl ad ogram are arbi trary; onl y th e b ranchi ng ord er is significant. See phylogram. www.bcu.ubc.ca/~otto/EvolDisc/Glossary.html TAKE-HOME MESSAGE: Cladograms tell us about the his tory of the re lati onshi ps of organi sms. K ey word : Hi st ory. Historically, classification of organisms was mainlyypg a bookkeeping task. For this monumental job, Carrolus Linnaeus invented the s ystem of binomial nomenclature that we are all familiar with. (Did you know that his name was Carol Linne? He liidhilatinized his own name th e way h e named speci i!)es!) Merely giving species names and arranging them according to similar groups was acceptable while we thought species were static entities . -

Data Exploration in Phylogenetic Inference: Scientific, Heuristic, Or Neither
Cladistics Cladistics 19 (2003) 379–418 www.elsevier.com/locate/yclad Data exploration in phylogenetic inference: scientific, heuristic, or neither Taran Granta,b,* and Arnold G. Klugec,* a Division of Vertebrate Zoology, Herpetology, American Museum of Natural History, New York, NY 10024, USA b Department of Ecology, Evolution, and Environmental Biology, Columbia University, New York, NY 10027, USA c Museum of Zoology, University of Michigan, Ann Arbor, MI 48109, USA Accepted 16 June 2003 Abstract The methods of data exploration have become the centerpiece of phylogenetic inference, but without the scientific importance of those methods having been identified. We examine in some detail the procedures and justifications of WheelerÕs sensitivity analysis and relative rate comparison (saturation analysis). In addition, we review methods designed to explore evidential decisiveness, clade stability, transformation series additivity, methodological concordance, sensitivity to prior probabilities (Bayesian analysis), skewness, computer-intensive tests, long-branch attraction, model assumptions (likelihood ratio test), sensitivity to amount of data, polymorphism, clade concordance index, character compatibility, partitioned analysis, spectral analysis, relative apparent syna- pomorphy analysis, and congruence with a ‘‘known’’ phylogeny. In our review, we consider a method to be scientific if it performs empirical tests, i.e., if it applies empirical data that could potentially refute the hypothesis of interest. Methods that do not perform tests, and therefore are not scientific, may nonetheless be heuristic in the scientific enterprise if they point to more weakly or am- biguously corroborated hypotheses, such propositions being more easily refuted than those that have been more severely tested and are more strongly corroborated. Based on common usage, data exploration in phylogenetics is accomplished by any method that performs sensitivity or quality analysis. -

Geo 302D: Age of Dinosaurs LAB 4: Systematics
Geo 302D: Age of Dinosaurs LAB 4: Systematics Systematics is the comparative study of biological diversity, with the intent of determining the relationships between organisms. Humankind has always tried to find ways of organizing the creatures that surround us into categories or classes. Linnaeus was the first to utilize a working system of hierarchical classification, in 1758. It is his classification scheme which most of you are familiar with, as it is still taught in its basic form in grade schools. The system is based upon the organization of life forms into groups based upon their overall similarity. In this course we use phylogenetic systematics, also called cladistics. This technique is used by most professional biologists, zoologists, and paleontologists. In this system, organisms are grouped together on the basis of shared ancestry. A result of using this system is that the ranks (e.g. Kingdom, Phylum, Class, Order, etc.) which many of you were forced to learn in previous science classes are impractical and do not necessarily reflect evolutionary relationships between organisms. Therefore, they are not used in cladistic methodology. Cladograms Cladistics uses branching diagrams called cladograms (or trees) to visually display the hypothesized relationships between taxa (a taxon is any unit of biological diversity; taxa is the plural form of the word). Look at the cladogram below. Relative time runs vertically. A, B, C, and D represent different taxa. They are out at the terminal tips of branches on the tree, so they are called terminal taxa. The points on the tree where branches meet are called nodes. A node represents the point of divergence between evolutionary lineages.