Universitatis Scientiarum Budapestinensis De Rolando Eötvös Nominatae Sectio Computatorica
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Bi-Unitary Multiperfect Numbers, I
Notes on Number Theory and Discrete Mathematics Print ISSN 1310–5132, Online ISSN 2367–8275 Vol. 26, 2020, No. 1, 93–171 DOI: 10.7546/nntdm.2020.26.1.93-171 Bi-unitary multiperfect numbers, I Pentti Haukkanen1 and Varanasi Sitaramaiah2 1 Faculty of Information Technology and Communication Sciences, FI-33014 Tampere University, Finland e-mail: [email protected] 2 1/194e, Poola Subbaiah Street, Taluk Office Road, Markapur Prakasam District, Andhra Pradesh, 523316 India e-mail: [email protected] Dedicated to the memory of Prof. D. Suryanarayana Received: 19 December 2019 Revised: 21 January 2020 Accepted: 5 March 2020 Abstract: A divisor d of a positive integer n is called a unitary divisor if gcd(d; n=d) = 1; and d is called a bi-unitary divisor of n if the greatest common unitary divisor of d and n=d is unity. The concept of a bi-unitary divisor is due to D. Surynarayana [12]. Let σ∗∗(n) denote the sum of the bi-unitary divisors of n: A positive integer n is called a bi-unitary perfect number if σ∗∗(n) = 2n. This concept was introduced by C. R. Wall in 1972 [15], and he proved that there are only three bi-unitary perfect numbers, namely 6, 60 and 90. In 1987, Peter Hagis [6] introduced the notion of bi-unitary multi k-perfect numbers as solu- tions n of the equation σ∗∗(n) = kn. A bi-unitary multi 3-perfect number is called a bi-unitary triperfect number. A bi-unitary multiperfect number means a bi-unitary multi k-perfect number with k ≥ 3: Hagis [6] proved that there are no odd bi-unitary multiperfect numbers. -

On the Largest Odd Component of a Unitary Perfect Number*
ON THE LARGEST ODD COMPONENT OF A UNITARY PERFECT NUMBER* CHARLES R. WALL Trident Technical College, Charleston, SC 28411 (Submitted September 1985) 1. INTRODUCTION A divisor d of an integer n is a unitary divisor if gcd (d9 n/d) = 1. If d is a unitary divisor of n we write d\\n9 a natural extension of the customary notation for the case in which d is a prime power. Let o * (n) denote the sum of the unitary divisors of n: o*(n) = £ d. d\\n Then o* is a multiplicative function and G*(pe)= 1 + p e for p prime and e > 0. We say that an integer N is unitary perfect if o* (N) = 2#. In 1966, Sub- baro and Warren [2] found the first four unitary perfect numbers: 6 = 2 * 3 ; 60 = 223 - 5 ; 90 = 2 * 325; 87,360 = 263 • 5 • 7 • 13. In 1969s I announced [3] the discovery of another such number, 146,361,936,186,458,562,560,000 = 2183 • 5^7 • 11 • 13 • 19 • 37 • 79 • 109 * 157 • 313, which I later proved [4] to be the fifth unitary perfect number. No other uni- tary perfect numbers are known. Throughout what follows, let N = 2am (with m odd) be unitary perfect and suppose that K is the largest odd component (i.e., prime power unitary divisor) of N. In this paper we outline a proof that, except for the five known unitary perfect numbers, K > 2 2. TECHNIQUES In light of the fact that 0*(pe) = 1 + pe for p prime, the problem of find- ing a unitary perfect number is equivalent to that of expressing 2 as a product of fractions, with each numerator being 1 more than its denominator, and with the denominators being powers of distinct primes. -

Types of Integer Harmonic Numbers (Ii)
Bulletin of the Transilvania University of Bra¸sov • Vol 9(58), No. 1 - 2016 Series III: Mathematics, Informatics, Physics, 67-82 TYPES OF INTEGER HARMONIC NUMBERS (II) Adelina MANEA1 and Nicu¸sorMINCULETE2 Abstract In the first part of this paper we obtained several bi-unitary harmonic numbers which are higher than 109, using the Mersenne prime numbers. In this paper we investigate bi-unitary harmonic numbers of some particular forms: 2k · n, pqt2, p2q2t, with different primes p, q, t and a squarefree inte- ger n. 2010 Mathematics Subject Classification: 11A25. Key words: harmonic numbers, bi-unitary harmonic numbers. 1 Introduction The harmonic numbers introduced by O. Ore in [8] were named in this way by C. Pomerance in [11]. They are defined as positive integers for which the harmonic mean of their divisors is an integer. O. Ore linked the perfect numbers with the harmonic numbers, showing that every perfect number is harmonic. A list of the harmonic numbers less than 2 · 109 is given by G. L. Cohen in [1], finding a total of 130 of harmonic numbers, and G. L. Cohen and R. M. Sorli in [2] have continued to this list up to 1010. The notion of harmonic numbers is extended to unitary harmonic numbers by K. Nageswara Rao in [7] and then to bi-unitary harmonic numbers by J. S´andor in [12]. Our paper is inspired by [12], where J. S´andorpresented a table containing all the 211 bi-unitary harmonic numbers up to 109. We extend the J. S´andors's study, looking for other bi-unitary harmonic numbers, greater than 109. -

A Study of .Perfect Numbers and Unitary Perfect
CORE Metadata, citation and similar papers at core.ac.uk Provided by SHAREOK repository A STUDY OF .PERFECT NUMBERS AND UNITARY PERFECT NUMBERS By EDWARD LEE DUBOWSKY /I Bachelor of Science Northwest Missouri State College Maryville, Missouri: 1951 Master of Science Kansas State University Manhattan, Kansas 1954 Submitted to the Faculty of the Graduate College of the Oklahoma State University in partial fulfillment of .the requirements fqr the Degree of DOCTOR OF EDUCATION May, 1972 ,r . I \_J.(,e, .u,,1,; /q7Q D 0 &'ISs ~::>-~ OKLAHOMA STATE UNIVERSITY LIBRARY AUG 10 1973 A STUDY OF PERFECT NUMBERS ·AND UNITARY PERFECT NUMBERS Thesis Approved: OQ LL . ACKNOWLEDGEMENTS I wish to express my sincere gratitude to .Dr. Gerald K. Goff, .who suggested. this topic, for his guidance and invaluable assistance in the preparation of this dissertation. Special thanks.go to the members of. my advisory committee: 0 Dr. John Jewett, Dr. Craig Wood, Dr. Robert Alciatore, and Dr. Vernon Troxel. I wish to thank. Dr. Jeanne Agnew for the excellent training in number theory. that -made possible this .study. I wish tc;, thank Cynthia Wise for her excellent _job in typing this dissertation •. Finally, I wish to express gratitude to my wife, Juanita, .and my children, Sondra and David, for their encouragement and sacrifice made during this study. TABLE OF CONTENTS Chapter Page I. HISTORY AND INTRODUCTION. 1 II. EVEN PERFECT NUMBERS 4 Basic Theorems • • • • • • • • . 8 Some Congruence Relations ••• , , 12 Geometric Numbers ••.••• , , , , • , • . 16 Harmonic ,Mean of the Divisors •. ~ ••• , ••• I: 19 Other Properties •••• 21 Binary Notation. • •••• , ••• , •• , 23 III, ODD PERFECT NUMBERS . " . 27 Basic Structure • , , •• , , , . -

Integer Sequences
UHX6PF65ITVK Book > Integer sequences Integer sequences Filesize: 5.04 MB Reviews A very wonderful book with lucid and perfect answers. It is probably the most incredible book i have study. Its been designed in an exceptionally simple way and is particularly just after i finished reading through this publication by which in fact transformed me, alter the way in my opinion. (Macey Schneider) DISCLAIMER | DMCA 4VUBA9SJ1UP6 PDF > Integer sequences INTEGER SEQUENCES Reference Series Books LLC Dez 2011, 2011. Taschenbuch. Book Condition: Neu. 247x192x7 mm. This item is printed on demand - Print on Demand Neuware - Source: Wikipedia. Pages: 141. Chapters: Prime number, Factorial, Binomial coeicient, Perfect number, Carmichael number, Integer sequence, Mersenne prime, Bernoulli number, Euler numbers, Fermat number, Square-free integer, Amicable number, Stirling number, Partition, Lah number, Super-Poulet number, Arithmetic progression, Derangement, Composite number, On-Line Encyclopedia of Integer Sequences, Catalan number, Pell number, Power of two, Sylvester's sequence, Regular number, Polite number, Ménage problem, Greedy algorithm for Egyptian fractions, Practical number, Bell number, Dedekind number, Hofstadter sequence, Beatty sequence, Hyperperfect number, Elliptic divisibility sequence, Powerful number, Znám's problem, Eulerian number, Singly and doubly even, Highly composite number, Strict weak ordering, Calkin Wilf tree, Lucas sequence, Padovan sequence, Triangular number, Squared triangular number, Figurate number, Cube, Square triangular -
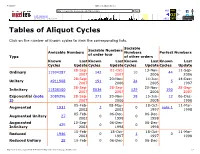
Tables of Aliquot Cycles
5/29/2017 Tables of Aliquot Cycles http://amicable.homepage.dk/tables.htm Go FEB MAY JUN f ❎ 117 captures 02 ⍰ ▾ About 28 May 2002 ‑ 2 May 2014 2012 2014 2015 this capture Tables of Aliquot Cycles Click on the number of known cycles to view the corresponding lists. Sociable Sociable Numbers Amicable Numbers Numbers Perfect Numbers of order four Type of other orders Known Last Known Last Known Last Known Last Cycles Update Cycles Update Cycles Update Cycles Update 28Sep 01Oct 13Nov 11Sep Ordinary 11994387 142 10 44 2007 2007 2006 2006 28Sep 20Nov 14Jun 14Dec Unitary 4911908 191 24 5 2007 2006 2005 1997 28Sep 28Sep 20Nov 28Sep Infinitary 11538100 5034 129 190 2007 2007 2006 2007 Exponential (note 3089296 28Sep 371 20Nov 38 15Jun 12 06Dec 2) 2007 2006 2005 1998 05Feb 08May 18Oct 11Mar Augmented 1931 2 0 note 1 2002 2003 1997 1998 05Feb 06Dec 06Dec Augmented Unitary 27 0 0 2002 1998 1998 Augmented 10Sep 06Dec 06Dec 425 0 0 Infinitary 2003 1998 1998 15Feb 18Oct 18Oct 11Mar Reduced 1946 0 1 0 2003 1997 1997 1998 Reduced Unitary 28 15Feb 0 06Dec 0 06Dec http://web.archive.org/web/20140502102524/http://amicable.homepage.dk/tables.htm 1/3 5/29/2017 Tables of Aliquot Cycles http://amicable.homepage.dk/tables.htm2003 1998 Go 1998 FEB MAY JUN f ❎ 117 captures 10Sep 06Dec 06Dec 02 ⍰ Reduced Infinitary 427 0 0 ▾ About 28 May 2002 ‑ 2 May 2014 2003 1998 1998 2012 2014 2015 this capture Note 1: All powers of 2 are augmented perfect numbers; no other augmented perfect numbers are known. -

Numbers 1 to 100
Numbers 1 to 100 PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Tue, 30 Nov 2010 02:36:24 UTC Contents Articles −1 (number) 1 0 (number) 3 1 (number) 12 2 (number) 17 3 (number) 23 4 (number) 32 5 (number) 42 6 (number) 50 7 (number) 58 8 (number) 73 9 (number) 77 10 (number) 82 11 (number) 88 12 (number) 94 13 (number) 102 14 (number) 107 15 (number) 111 16 (number) 114 17 (number) 118 18 (number) 124 19 (number) 127 20 (number) 132 21 (number) 136 22 (number) 140 23 (number) 144 24 (number) 148 25 (number) 152 26 (number) 155 27 (number) 158 28 (number) 162 29 (number) 165 30 (number) 168 31 (number) 172 32 (number) 175 33 (number) 179 34 (number) 182 35 (number) 185 36 (number) 188 37 (number) 191 38 (number) 193 39 (number) 196 40 (number) 199 41 (number) 204 42 (number) 207 43 (number) 214 44 (number) 217 45 (number) 220 46 (number) 222 47 (number) 225 48 (number) 229 49 (number) 232 50 (number) 235 51 (number) 238 52 (number) 241 53 (number) 243 54 (number) 246 55 (number) 248 56 (number) 251 57 (number) 255 58 (number) 258 59 (number) 260 60 (number) 263 61 (number) 267 62 (number) 270 63 (number) 272 64 (number) 274 66 (number) 277 67 (number) 280 68 (number) 282 69 (number) 284 70 (number) 286 71 (number) 289 72 (number) 292 73 (number) 296 74 (number) 298 75 (number) 301 77 (number) 302 78 (number) 305 79 (number) 307 80 (number) 309 81 (number) 311 82 (number) 313 83 (number) 315 84 (number) 318 85 (number) 320 86 (number) 323 87 (number) 326 88 (number) -

Preface (PDF 321KB)
iii Preface Mark with serene impartiality The strife of things, and yet be comforted, Knowing that by the chain causality All separate existences are wed Oscar Wilde, “Humanitad” This Festschrift is dedicated to Maciej Koutny on the occasion of his 60th birthday. As Maciej’s colleagues are undoubtedly aware, causality (with Petri nets used as the harness) is a prominent unifying topic of Maciej’s research, and it was selected as the topic of this Fest- schrift. It turns out that causality is a very complicated phenomenon. E.g. this book is ‘caused’ by Maciej’s 60th birthday – even though its creation had preceded this remarkable occasion. This constitutes an instance of reverse temporal causality, whose formal modelling would un- doubtedly require Petri nets with inhibitor arcs, contextual loops, and step semantics, not to mention the heavy mathematical artillery that Maciej uses so fluently. It is left to the reader to complete this formal model. (I didn’t get research funding for this.) Attendees of Petri Nets 2018 (Bratislava) on the way to the conference banquet. Maciej is on the left, holding the conference banner. Photo credit: Juraj Mazari. Apparently, the number 60 has some special significance, which I could not comprehend (being only 42, i.e. having accomplished only 70%). Hence, I have commissioned a personal research project to discover the secrets of 60, using the computational resources at my dis- posal. The experiment was conducted on a PC with a 64-bit Intel Core i7-6700K 4.00GHz CPU with 4 cores (hyperthreaded) and 64Gb RAM. “60” was entered into Wikipedia’s search box, and the results were carefully analysed. -

Perfect Diameter of Ali Pi
PhasePhaseAliAli 33 PerfectPerfect DiameterDiameter ofof AliAli PiPi www.ali-pi.com 66 -- FirstFirst PerfectPerfect NumberNumber inin MathematicsMathematics 66 AliAli NumberNumber –– 66 isis thethe firstfirst andand thethe smallestsmallest ‘Perfect‘Perfect Number’Number’ inin mathematics.mathematics. www.ali-pi.com NumberNumber 66 –– aa PerfectPerfect NumberNumber inin thethe eyeseyes ofof GreekGreek MathematiciansMathematicians Number – 6 is a Perfect Number in the eyes of Greek Mathematicians because 6 equals the sum of its divisors that are smaller than itself. Such a number is neither 5 nor 7 nor 10, but 6 for theAliAli reason: 66 == 11 ++ 22 ++ 33 66 == 11 xx 22 xx 33 66 ==www.ali 66-pi.com 33 xx 33 MagicMagic SquareSquare ofof 66 33 11 22 1 2 3 1 AliAli2 3 22 33 11 All rows, columns and diagonals add to 6 1 + 2 + 3 = 6 www.ali-pi.com NumberNumber –– 66 isis thethe 1st1st andand SmallestSmallest PerfectPerfect Number.Number. Number – 6 is the 1st Unitary Perfect Number. Number – 6 is the multiply perfect Number. Number – 6 is a hyperAliAli-perfect number. Number – 6 is the semi-perfect Number. Number – 6 is a primitive semi-perfect or primitive pseudo-perfect Number. Number – 6 is the One and Only Number in Mathematics which is ‘Perfect’ in all aspects and dimensions www.ali-pi.com Number – 6 Cardinal 6 ( six ) Ordinal 6th (sixth) Numeral system Senary Factorization 2.3 Divisors 1,2,3,6 Roman numeral VI Roman numeral (Unicode)AliAli , Japanese numeral prefixes hexa-/hex- (from Greek) sexa-/sex- (from Latin) Binary 110 Octal 6 DuDuodecimalodecimal 6 Hexadecimal 6 (Vav) ו Hebrew www.ali-pi.com SignificanceSignificance ofof NumberNumber –– 66 1. -

UNITARY HARMONIC NUMBERS (3) //*(«) = Nd*(N)/A*(N) = U 2P?Ap? +
PROCEEDINGS OF THE AMERICAN MATHEMATICAL SOCIETY Volume 51, Number 1, August 1975 UNITARY HARMONICNUMBERS PETER HAGIS, JR. AND GRAHAM LORD ABSTRACT. If d (n) and cr (n) denote the number and sum, respec- tively, of the unitary divisors of the natural number n then the harmonic mean of the unitary divisors of n is given by H (n) = nd (n)/cr (n). Here we investigate the properties of H (ra), and, in particular, study those num- bers n for which H (n) is an integer. 1. Introduction. Let d{n) and o(n) denote, respectively, the number and sum of the positive divisors of the natural number n. Ore [6] showed that the harmonic mean of the positive divisors of n is given by H{n) = nd{n)/a{n), and several papers (see [l], [5J> [6], L7]) have been devoted to the study of H{n). In particular the set of numbers S for which H(n) is an integer has attracted the attention of number theorists, since the set of per- fect numbers is a subset of 5, The elements of S are called harmonic num- bers by Pomerance [7j. This paper is devoted to a study of the unitary analogue of H(n). We recall that the positive integer d is said to be a uni- tary divisor of n if d\n and {d, n/d) = 1. It is easy to verify that if the canonical prime decomposition of n is given by al «2 .ak (1) » = PlPl'-'Pk and d (n) and o {n) denote the number and sum, respectively, of the uni- tary divisors of n then (2) d*(n) = 2k; o*{n) = (p"1 + l){pa22 +!)■■■ {p¡k + 1). -

Notices of the American Mathematical Society
OF THE AMERICAN MATHEMATICAL SOCIETY Edited by Everett Pitcher and Gordon L. Walker CONTENTS MEETINGS Calendar of Meetings ................ 578 Program for the june Meeting in Corvallis, Oregon 579 Abstracts for the Meeting: Pages 611-617 PRELIMINARY ANNOUNCEMENTS OF MEETINGS 583 NEWS ITEMS AND ANNOUNCEMENTS . 582, 589 MATHEMATICAL OFFPRINT SERVICE 590 LETTERS TO THE EDITOR . 592 SPECIAL MEETINGS INFORMATION CENTER 595 MEMORANDA TO MEMBERS . 600 Policy on Recruitment PERSONAL ITEMS 601 NEW AMS PUBLICATIONS .. 605 ABSTRACTS OF CONTRIBUTED PAPERS 608 ERRATA TO ABSTRACTS ........• 617 ABSTRACTS PRESENTED TO THE SOCIETY 618 INDEX TO ADVERTISERS. 687 RESERVATION FORM •.. 688 MEETINGS Calendar of Meetings NOTE: This Calendar lists all of the meetings which have been approved by the Council up to the date at which this issue of the cJ{oticti) was sent to press. The summer and annual meetings are joint meetings of the Mathematical Association of America and the American Mathematical Society. The meeting dates which fall rather far in the future are subject to change. This is particularly true of the meetings to which no numbers have yet been assigned. Meet· Deadline ing Date Place for No. Abstracts• 687 August 30-September 3, 1171 University Park, Pennsylvania July 7, I 'n I (76th Summer Meeting) 688 October 30, 1971 Cambridge, Massachusetts Sept. 9, 1971 689 November 19-20, I971 Auburn, Alabama Oct. 4, 1971 690 November 27, 1971 Milwaukee, Wisconsin Oct. 4, 1971 691 January 17-21, 1972 Las Vegas, Nevada Nov. 4, 1971 (78th Annual Meeting) March 29-April 1, 1972 St. Louis, Missouri August 28-September 1, 1972 Hanover, New Hampshire (77th Summer Meeting) January 25-29, 1973 Dallas, Texas (79:h Annual Meeting) August 20-24, 1973 Missoula, Montana (78th Summer Meeting) January 13-19, 1974 San Francisco, California (80th Annual Meeting) January 23-27, 1975 Washington, D.C. -

Some Results on Generalized Multiplicative Perfect Numbers
Some Results on Generalized Multiplicative Perfect Numbers Alexandre Laugier Lyc´eeprofessionnel Tristan Corbi`ere 16 rue de Kerveguen - BP 17149 29671 Morlaix cedex France [email protected] Manjil P. Saikia1 Fakult¨atf¨urMathematik Universit¨atWien Oskar-Morgenstern-Platz 1 1090 Wien Austria [email protected] Abstract In this article, we define k-multiplicatively e-perfect numbers and k-multiplicatively e-superperfect numbers and prove some results on them. We also characterize the k- ∗ T0T -perfect numbers defined by Das and Saikia (2013). 1 Introduction A natural number n is said to be perfect (A000396) if the sum of all aliqout divisors of n is equal to n. Or equivalently, σ(n) = 2n, where σ(k) is the sum of the divisors of k. It is a well known result of Euler-Euclid that the form of even perfect numbers is n = 2kp, where p = 2k+1 − 1 is a Mersenne prime and k ≥ 1. Till date, no odd perfect number is known, and it is believed that none exists. Moreover n is said to be super-perfect if σ(σ(n)) = 2n. It was proved by Suryanarayana-Kanold [3,7] that the general form of such super-perfect numbers are n = 2k, where 2k+1 − 1 is a prime and k ≥ 1. No odd super-perfect numbers are known till date. Unless, otherwise mentioned all n considered in this paper will be a natural number. We also denote by 1; n , the set f1; 2; : : : ; ng. J K 1Corresponding author 1 Let T (n) denote the product of all the divisors of n.A multiplicatively perfect (A007422) number is a number n such that T (n) = n2 and n is called a multiplicatively super-perfect if T (T (n)) = n2.