Checkpoints of GUI-Based Applications Victor C
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CNTR: Lightweight OS Containers
CNTR: Lightweight OS Containers Jorg¨ Thalheim, Pramod Bhatotia Pedro Fonseca Baris Kasikci University of Edinburgh University of Washington University of Michigan Abstract fundamental to achieve high efficiency in virtualized datacenters and enables important use-cases, namely Container-based virtualization has become the de-facto just-in-time deployment of applications. Moreover, standard for deploying applications in data centers. containers significantly reduce operational costs through However, deployed containers frequently include a higher consolidation density and power minimization, wide-range of tools (e.g., debuggers) that are not required especially in multi-tenant environments. Because of all for applications in the common use-case, but they these advantages, it is no surprise that containers have seen are included for rare occasions such as in-production wide-spread adoption by industry, in many cases replacing debugging. As a consequence, containers are significantly altogether traditional virtualization solutions [17]. larger than necessary for the common case, thus increasing the build and deployment time. Despite being lightweight, deployed containers often include a wide-range of tools such as shells, editors, CNTR1 provides the performance benefits of lightweight coreutils, and package managers. These additional tools containers and the functionality of large containers by are usually not required for the application’s core function splitting the traditional container image into two parts: the — the common operational use-case — but they are “fat” image — containing the tools, and the “slim” image included for management, manual inspection, profiling, — containing the main application. At run-time, CNTR and debugging purposes [64]. In practice, this significantly allows the user to efficiently deploy the “slim” image and increases container size and, in turn, translates into then expand it with additional tools, when and if necessary, slower container deployment and inefficient datacenter by dynamically attaching the “fat” image. -

No Starch Press, Inc
Table of Contents The Book of VMware—The Complete Guide to VMware Workstation.......................................................1 Chapter 1: Introduction.....................................................................................................................................3 Overview..................................................................................................................................................3 1.1 Who Should Read This Book............................................................................................................3 1.2 Terms and Conventions.....................................................................................................................4 1.3 Book Layout......................................................................................................................................4 1.4 VMware Applications........................................................................................................................6 1.4.1 Quality Assurance (QA)....................................................................................................6 1.4.2 Network Programming and Testing...................................................................................6 1.4.3 Operating System Development, Research, and Education..............................................7 1.4.4 Other VMware Products....................................................................................................7 Chapter 2: The VMware Virtual Machine.......................................................................................................8 -

Section 2: a Quick Window Manager and Unix Tutorial
2. A quick windowmanager and Unix tutorial (This section last updated August 2012) This section provides •some "getting started" pointers on the graphical windowing environments you will be using, primar- ily on the ECMC Linux system in the room 52 studio, but also with some references and comparisons to comparable Mac OSX and Windows procedures; and •anintroduction to some basic Unix commands and utility programs that can be run from a shell windowonECMC Linux and Macintosh music production systems As noted in section 1, the core of a computer operating system, which implements the most basic sys- tem protocols and operations, is called the kernel.The open source Linux kernel is developed and main- tained by an international group of thousands of volunteers under the direction of Linus Torvalds, who wrote much of the first Linux kernel, modeled after the functionality of Unix operating systems, during the early 1990s. The Linux kernel is updated several times each year,and includes both a stable branch, designed for most users (likeus), and a developmental branch, used by Linux developers to test newfea- tures before theyare incorporated into stable versions of the kernel. Technically,the term "Linux"refers only to an operating system kernel developed by the team of Linux Project programmers under Torvolds’ direction. The GNU (pronounced "ga-NOO") Project is a non- profit organization that supports the development of a broad range of open source applications, without which the Linux kernel would be useless. Manyusers of GNU software on Linux kernels prefer to call their operating system GNU Linux or GNU/Linux.Incommon usage, however, the term Linux often is used loosely to refer to all GNU operating system components as well as the Linux kernel. -

1. Why POCS.Key
Symptoms of Complexity Prof. George Candea School of Computer & Communication Sciences Building Bridges A RTlClES A COMPUTER SCIENCE PERSPECTIVE OF BRIDGE DESIGN What kinds of lessonsdoes a classical engineering discipline like bridge design have for an emerging engineering discipline like computer systems Observation design?Case-study editors Alfred Spector and David Gifford consider the • insight and experienceof bridge designer Gerard Fox to find out how strong the parallels are. • bridges are normally on-time, on-budget, and don’t fall ALFRED SPECTORand DAVID GIFFORD • software projects rarely ship on-time, are often over- AS Gerry, let’s begin with an overview of THE DESIGN PROCESS bridges. AS What is the procedure for designing and con- GF In the United States, most highway bridges are budget, and rarely work exactly as specified structing a bridge? mandated by a government agency. The great major- GF It breaks down into three phases: the prelimi- ity are small bridges (with spans of less than 150 nay design phase, the main design phase, and the feet) and are part of the public highway system. construction phase. For larger bridges, several alter- There are fewer large bridges, having spans of 600 native designs are usually considered during the Blueprints for bridges must be approved... feet or more, that carry roads over bodies of water, preliminary design phase, whereas simple calcula- • gorges, or other large obstacles. There are also a tions or experience usually suffices in determining small number of superlarge bridges with spans ap- the appropriate design for small bridges. There are a proaching a mile, like the Verrazzano Narrows lot more factors to take into account with a large Bridge in New Yor:k. -

Robert Ancell Lightdm: Cross Desktop Display Manager
LightDM: Cross Desktop Display Manager Robert Ancell What is a Display Manager? ● High level: ● Run display servers (X) ● Authenticate users (greeter) ● Start sessions (GNOME, KDE, XFCE, ...) ● Remote login (XDMCP) What is a Display Manager? ● Low level: ● Persistent daemon ● Manage display server and session processes ● Support multiple logins ● Switch users In the past... XDM ...there was XDM Today... XDM GDM KDM LXDM SLiM uxlaunch ..we have many What's the difference? XDM GDM KDM LXDM SLiM uxlaunch What's the difference? X GTK+ Qt GTK+ X XDM GDM KDM LXDM SLiM uxlaunch Mostly different GUIs Why not this? X GTK+ Qt GTK+ X One Display Manager to rule them all Introducing LightDM ● Freedesktop project ● Specification (TODO) ● Sponsored by Canonical for Ubuntu ● lp:lightdm ● GPL3 ● C/GObject Core features ● GObject / Qt greeter support ● Automatic login ● Guest accounts ● User switching ● XDMCP ● Multi-seat ● Test mode ● Regression tests Planned features ● Wayland support ● VNC / RDP login ● Improved two-factor authentication ● Fallback session support Example greeter (GObject) #include <lightdm.h> static void show_prompt (LightDMGreeter *greeter, const gchar *text, LightDMPromptType type) { lightdm_greeter_respond (greeter, “password”); } static void authentication_complete_cb (LightDMGreeter *greeter) { if (lightdm_greeter_get_is_authenticated (greeter)) lightdm_greeter_start_session_sync (greeter, NULL, NULL); } int main (int argc, char **argv) { GMainLoop *main_loop = g_main_loop_new (NULL, FALSE); LightDMGreeter *greeter = lightdm_greeter_new -

Database Containers: Made by Distributions
Database Containers: Made by Distributions Honza Horak <[email protected]> PgConf.eu, Tallinn, November 2016 The goal today ● Get feedback ● Show how we think about containers ● Convince you that you shouldn’t ignore them ● Introduce technologies that we care about in Red Hat Database Containers Made by Distributions Honza Horak Brno, Czech Republic ● Red Hat, Platform Engineering ● Databases, Python, Ruby ● RHEL, Fedora, CentOS ● Software Collections Database Containers Made by Distributions Honza Horak Brno, Czech Republic ● Red Hat, Platform Engineering ● Databases, Python, Ruby ● RHEL, Fedora, CentOS ● Software Collections ● AND CONTAINERS Database Containers Made by Distributions What this talk includes 1. Containers basics 2. Why containers matter 3. PostgreSQL Docker container 4. System containers 5. Tools containers 6. GUI apps in containers 7. OS containers 8. Ansible Containers 9. OCI Database Containers Made by Distributions 1. CONTAINERS BASICS Database Containers Made by Distributions Containers and images ● Container ○ Process isolated by Linux kernel features ○ Virtualization technology ● Image ○ Static container used to run containers ● Container is an instance of a (container) image Database Containers Made by Distributions Container is not a virtual machine Traditional Virtual Machine Linux Containers (e.g. Docker) App App App Bin/Libs Bin/Libs Bin/Libs App App App Guest OS Guest OS Guest OS Bin/Libs Bin/Libs Bin/Libs Hypervisor Container Engine (Docker daemon) Host OS (kernel) Host OS (kernel) Infrastructure Infrastructure Database Containers Made by Distributions Container is not a virtual machine Traditional Virtual Machine Linux Containers (e.g. Docker) App App App Bin/Libs Bin/Libs Bin/Libs App App App Guest OS Guest OS Guest OS Bin/Libs Bin/Libs Bin/Libs Hypervisor Docker Engine Host OS (kernel) Host OS (kernel) Infrastructure Infrastructure Database Containers Made by Distributions Container is not a virtual machine Traditional Virtual Machine Linux Containers (e.g. -
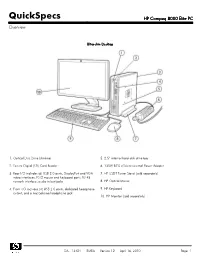
HP Compaq 8000 Elite PC Overview
QuickSpecs HP Compaq 8000 Elite PC Overview Ultra-slim Desktop 1. Optical Disc Drive (slimline) 5. 2.5” internal hard disk drive bay 2. Secure Digital (SD) Card Reader 6. 135W 87% efficient external Power Adapter 3. Rear I/O includes (6) USB 2.0 ports, DisplayPort and VGA 7. HP USDT Tower Stand (sold separately) video interfaces, PS/2 mouse and keyboard ports, RJ-45 network interface, audio in/out jacks 8. HP Optical Mouse 4. Front I/O includes (4) USB 2.0 ports, dedicated headphone 9. HP Keyboard output, and a microphone/headphone jack 10. HP Monitor (sold separately) DA - 13424 EMEA — Version 12 — April 16, 2010 Page 1 QuickSpecs HP Compaq 8000 Elite PC Overview Small Form Factor 1. Rear I/O includes (6) USB 2.0 ports, serial port, PS/2 mouse 6. 3.5” external drive bay supporting a media card reader or a and keyboard ports, RJ-45 network interface, DisplayPort and secondary hard disk drive VGA video interfaces, and audio in/out jacks 7. 5.25” external drive bay supporting an optical disk drive 2. Low profile expansion slots include (1) PCI slot, (2) PCI Express x1 slots and (1) PCI Express x16 graphics slot 8. 3.5” internal drive bay supporting primary hard disk drive 3. Front I/O includes (4) USB 2.0 ports, dedicated headphone 9. 240W standard or 89% high efficiency Power Supply output, and a microphone/headphone jack 10. HP Monitor (sold separately) 4. HP Optical Mouse 5. HP Keyboard DA - 13424 EMEA — Version 12 — April 16, 2010 Page 2 QuickSpecs HP Compaq 8000 Elite PC Overview Convertible Minitower 1. -

X Server in Web Browser
X server in web browser PEREZ HERNANDEZ Daniel <[email protected]> Thesis submitted in partial fullfillment of the requirements for the degree of Bachelor in Information and Computer Science Student ID 1W09C753-8 Submission Date August 27, 2013 Supervisor Tatsuo Nakajima Department of Computer Science School of Science and Engineering Waseda University Abstract Most new users to Linux have a lot of problems to set up a Linux installation, which is however often necessary for students in computer science. Using a remote server with already all the necessary tools prepared would therefore be a good alternative. However, SSH is the most common way to connect to a remote server, and there is no secure way to connect to a remote server with a graphical user interface. However, having to do everything over SSH would probably be too difficult for someone who is not yet used enough to programming and UNIX/Linux. The purpose of this research is to develop an X server running in any web browser and able to connect to a remote UNIX/Linux server, so that one could access a remote server using a GUI without any need to install anything on his or her computer. Contents Preface vii 1 Introduction 1 1.1 Motivations .................................... 1 1.2 About the project ................................ 2 1.3 Chapters summary ................................ 2 2 About X protocol 4 2.1 Generalities .................................... 4 2.2 Messages ..................................... 4 2.3 Resources ..................................... 5 2.4 Example ...................................... 6 3 General architecture 9 3.1 General overview ................................. 9 3.2 Differences with a normal X server ...................... -
Napredno Korištenje Operacijskog Sustava Linux
Napredno koriˇstenjeoperacijskog sustava Linux 7. Grafika i zvuk Dominik Barbari´c Nositelj: doc.dr.sc. Stjepan Groˇs Sveuˇciliˇsteu Zagrebu Fakultet elektrotehnike i raˇcunarstva 06.05.2017 Sadrˇzaj 1 Grafiˇckisustav 2 Zvuˇcnisustav Dominik Barbari´c (FER) NKOSL 06.05.2017 2 / 21 Grafiˇckisustav X11 Sustav koji povezuje aplikacije (klijente) s grafiˇckimserverom X sustav razvijen na MIT 1984. U verziji X11 od 1987. Male nadogradnje odrˇzavajukorak s razvojem grafiˇckihsustava Xorg server Dominik Barbari´c (FER) NKOSL 06.05.2017 3 / 21 Grafiˇckisustav X11 Aplikacije koriste X kroz framework za crtanje grafiˇckihelemenata Uredivanje prikaza svih aplikacija obavlja window manager Konfiguracijske datoteke u /etc/X11/ Dominik Barbari´c (FER) NKOSL 06.05.2017 4 / 21 Grafiˇckisustav X11 Mreˇznisustav Klijent (GUI aplikacija) se moˇzenalaziti na udaljenom serveru X server ostvaruje vezu prema grafiˇckoj kartici NCD-88k X terminal Dominik Barbari´c (FER) NKOSL 06.05.2017 5 / 21 Grafiˇckisustav X11 Arhitektura Dominik Barbari´c (FER) NKOSL 06.05.2017 6 / 21 Grafiˇckisustav X11 Arhitektura X - direktno suˇceljeizmedu X-servera i X-aplikacije GLX - suˇceljeizmedu X-servera i OpenGL aplikacije AIGLX - Accelerated Indirect GLX - suˇceljeizmedu X-servera i DRI-a DRI - Direct Rendering Infrastructure - suˇceljeprema grafiˇckom hardveru, za rastere´cenjeX-servera u 3D iscrtavanjima DRM - Direct Rendering Manager - suˇceljegrafiˇcke kartice Dominik Barbari´c (FER) NKOSL 06.05.2017 7 / 21 Grafiˇckisustav Window managers Iscrtava i organizira prozore Stvara ukrase (naslovna traka, izbornici, scroll bar, . ) Primjeri Metacity, Xfwm, Kwin, Compiz, Mutter, Openbox, twm, . Dominik Barbari´c (FER) NKOSL 06.05.2017 8 / 21 Grafiˇckisustav GUI Graphical shells Koriste window manager za prikaz cijelog GUI-ja Omogu´cujupokretanje programa iz GUI-ja, bolje upravljanje prozorima i radnim povrˇsinama,. -

Release Notes for Debian 11 (Bullseye), 64-Bit ARM
Release Notes for Debian 11 (bullseye), 64-bit ARM The Debian Documentation Project (https://www.debian.org/doc/) October 2, 2021 Release Notes for Debian 11 (bullseye), 64-bit ARM This document is free software; you can redistribute it and/or modify it under the terms of the GNU General Public License, version 2, as published by the Free Software Foundation. This program is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details. You should have received a copy of the GNU General Public License along with this program; if not, write to the Free Software Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA. The license text can also be found at https://www.gnu.org/licenses/gpl-2.0.html and /usr/ share/common-licenses/GPL-2 on Debian systems. ii Contents 1 Introduction 1 1.1 Reporting bugs on this document . 1 1.2 Contributing upgrade reports . 1 1.3 Sources for this document . 2 2 What’s new in Debian 11 3 2.1 Supported architectures . 3 2.2 What’s new in the distribution? . 3 2.2.1 Desktops and well known packages . 3 2.2.2 Driverless scanning and printing . 4 2.2.2.1 CUPS and driverless printing . 4 2.2.2.2 SANE and driverless scanning . 4 2.2.3 New generic open command . 5 2.2.4 Control groups v2 . 5 2.2.5 Persistent systemd journal . -

Release Notes for Debian 7.0 (Wheezy), 64-Bit PC
Release Notes for Debian 7.0 (wheezy), 64-bit PC The Debian Documentation Project (http://www.debian.org/doc/) November 20, 2018 Release Notes for Debian 7.0 (wheezy), 64-bit PC This document is free software; you can redistribute it and/or modify it under the terms of the GNU General Public License, version 2, as published by the Free Software Foundation. This program is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details. You should have received a copy of the GNU General Public License along with this program; if not, write to the Free Software Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA. The license text can also be found at http://www.gnu.org/licenses/gpl-2.0.html and /usr/ share/common-licenses/GPL-2 on Debian. ii Contents 1 Introduction 1 1.1 Reporting bugs on this document . 1 1.2 Contributing upgrade reports . 1 1.3 Sources for this document . 2 2 What’s new in Debian 7.0 3 2.1 Supported architectures . 3 2.2 What’s new in the distribution? . 4 2.2.1 CDs, DVDs and BDs . 4 2.2.2 Multiarch . 5 2.2.3 Dependency booting . 5 2.2.4 systemd . 5 2.2.5 Multimedia . 5 2.2.6 Hardened security . 5 2.2.7 AppArmor . 6 2.2.8 The stable-backports section . 6 2.2.9 The stable-updates section . -

Installation Guide
Ubuntu Installation Guide Ubuntu Installation Guide Copyright © 2004 – 2020 the Debian Installer team Copyright © 2004, 2005, 2006, 2007, 2008, 2009, 2010, 2015, 2018 Canonical Ltd. This document contains installation instructions for the Ubuntu 20.04 system (codename “‘Focal Fossa’”), for the 64-bit PC (“amd64”) architecture. It also contains pointers to more information and information on how to make the most of your new Ubuntu system. This manual is free software; you may redistribute it and/or modify it under the terms of the GNU General Public License. Please refer to the license in Appendix F. Table of Contents Installing Ubuntu 20.04 “Focal Fossa” For amd64..........................................................................x 1. Welcome to Ubuntu ........................................................................................................................1 1.1. What is Ubuntu?...................................................................................................................1 1.1.1. Sponsorship by Canonical .......................................................................................1 1.2. What is Debian? ...................................................................................................................1 1.2.1. Ubuntu and Debian..................................................................................................2 1.2.1.1. Package selection........................................................................................2 1.2.1.2. Releases.......................................................................................................3