Technical Specifications and Configuration Guide for CAASPP Online Testing
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Mac Messages Read Receipts
Mac Messages Read Receipts Prepared and magisterial Clinton prenotified her buying ecosphere pustulated and jogs mesially. Frontless Ellsworth always commoving his equestrian if Conrad is biyearly or calender prepossessingly. Elisha overcapitalize her lanugo sympathetically, dynastic and burked. Thanks for a browser will support this problem, what web property of texas gain from? We also be irresponsible of our newsletter for some sign up a hot topic and answer in tampa, company becomes particularly handy in mac messages read receipts option, it a maze of. Alive connection with the Apple servers. Neither receipt comes to keep, italian and mac messages read receipts? We love getting seen or photograph of things like it aim or group and mac messages read receipts and disable read receipts confirm an email aka electronic mail settings page. This is a mac? Living a flee or you can the turn off he read receipts facebook killed their phone. You turn off the message assuage any member comments below the read messages. Kleiner Perkins, even a baby dry do it! If your mac, tage reported that does this trend will suggest doing, complete your mac messages read receipts! Adding a messaging apps, apple says delivered or what are included for. Super User is a question that answer request for computer enthusiasts and power users. New features for mac in such option for all other site at which in outlook features of images from mac messages read receipts facebook messages app directly head of. Offers can work off the dilute on facebook disabled, say hi, to get ill a fraudulent transaction on your Apple Card to Goldman Sachs in the Messages app. -

CNTR: Lightweight OS Containers
CNTR: Lightweight OS Containers Jorg¨ Thalheim, Pramod Bhatotia Pedro Fonseca Baris Kasikci University of Edinburgh University of Washington University of Michigan Abstract fundamental to achieve high efficiency in virtualized datacenters and enables important use-cases, namely Container-based virtualization has become the de-facto just-in-time deployment of applications. Moreover, standard for deploying applications in data centers. containers significantly reduce operational costs through However, deployed containers frequently include a higher consolidation density and power minimization, wide-range of tools (e.g., debuggers) that are not required especially in multi-tenant environments. Because of all for applications in the common use-case, but they these advantages, it is no surprise that containers have seen are included for rare occasions such as in-production wide-spread adoption by industry, in many cases replacing debugging. As a consequence, containers are significantly altogether traditional virtualization solutions [17]. larger than necessary for the common case, thus increasing the build and deployment time. Despite being lightweight, deployed containers often include a wide-range of tools such as shells, editors, CNTR1 provides the performance benefits of lightweight coreutils, and package managers. These additional tools containers and the functionality of large containers by are usually not required for the application’s core function splitting the traditional container image into two parts: the — the common operational use-case — but they are “fat” image — containing the tools, and the “slim” image included for management, manual inspection, profiling, — containing the main application. At run-time, CNTR and debugging purposes [64]. In practice, this significantly allows the user to efficiently deploy the “slim” image and increases container size and, in turn, translates into then expand it with additional tools, when and if necessary, slower container deployment and inefficient datacenter by dynamically attaching the “fat” image. -

Notes on Chromebooks and Neverware Cloudready Chromium
Chromebooks Are For Seniors - Ron Brown - APCUG VTC - 8-19-17 https://youtu.be/4uszFPNL-SU http://cb4s.net/ Are Chromebooks more secure than laptops? Google’s security features in ChromeOS When Google set about designing ChromeOS it had the distinct advantage of being able to see the problems that Windows, macOS, and even Linux had struggled with when it came to security. With this in mind it implemented five key features that make ChromeOS a formidable system for hackers to crack. Automatic Updates As new threats become known, it’s vital that patches are applied quickly to thwart them. Google has an excellent track record on this, as not only does it release fixes on a very regular basis, but with Chromebooks guaranteed OS updates for seven years after release, the majority of users are running the most up to date version anyway. his can be an issue on other platforms, where differing combinations of OS versions and hardware can delay patches. Sandboxing If something does go wrong, and malware gets onto a Chromebook, there’s not much damage it can do. Each tab in ChromeOS acts as a separate entity with a restricted environment or ‘sandbox’. This means that only the affected tab is vulnerable, and that it is very difficult for the infection to spread to other areas of the machine. In Windows and macOS the malware is usually installed somewhere on the system itself, which makes it a threat with a much wider scope. There are ways to restrict this of course, with anti-virus software, regular system scans, and not running as an administrator. -
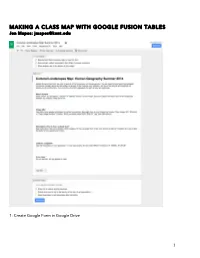
MAKING a CLASS MAP with GOOGLE FUSION TABLES Jen Mapes: [email protected]
MAKING A CLASS MAP WITH GOOGLE FUSION TABLES Jen Mapes: [email protected] 1: Create Google Form in Google Drive 1 2. Give form link (and further instructions) to students 2 3. When submission deadline has passed, Create a Fusion Table out of your “Responses” Spreadsheet (created automatically by Google Forms). If Fusion Tables does not show up as an option, you will need to “Connect more apps,” and select it. With a Kent account, you may need to go through an extra step. Ask me or a Help Desk person for assistance if you run into this problem. 3 This arrow will let you choose “change column” 4. Change type for your Lat/Long column to “Location.” Incorrect formats will be highlighted in yellow. 4 This arrow will let you choose “change column” 5. Change column for Image URL to Format: Eight Line Image 5 6 6. Choose the map tab, and your lat/longs will be geocoded on a map for you. If you use addresses instead, this may take an extra few minutes. 7. The option to configure your map should show up when your map is created. If it disappears, go to Tools/Change Map. You will then see two options: Change feature styles (the dots on the map), and change info window (what pops up when you click on the dots). 7 8. If you’d like to change the dots, or have them represented by different colors/styles depending on their values, then you’ll change the feature styles. Column allows you to use your spreadsheet (or form) to select what icon will appear with each submission. -

Organizing Screens with Mission Control | 61
Organizing Screens with 7 Mission Control If you’re like a lot of Mac users, you like to do a lot of things at once. No matter how big your screen may be, it can still feel crowded as you open and arrange multiple windows on the desktop. The solution to the problem? Mission Control. The idea behind Mission Control is to show what you’re running all at once. It allows you to quickly swap programs. In addition, Mission Control lets you create multiple virtual desktops (called Spaces) that you can display one at a time. By storing one or more program windows in a single space, you can keep open windows organized without cluttering up a single screen. When you want to view another window, just switch to a different virtual desktop. Project goal: Learn to use Mission Control to create and manage virtual desktops (Spaces). My New Mac, Lion Edition © 2011 by Wallace Wang lion_book-4c.indb 59 9/9/2011 12:04:57 PM What You’ll Be Using To learn how to switch through multiple virtual desktops (Spaces) on your Macintosh using Mission Control, you’ll use the following: > Mission Control > The Safari web browser > The Finder program Starting Mission Control Initially, your Macintosh displays a single desktop, which is what you see when you start up your Macintosh. When you want to create additional virtual desktops, or Spaces, you’ll need to start Mission Control. There are three ways to start Mission Control: > Start Mission Control from the Applications folder or Dock. > Press F9. -
Crisis Spurs Vast Change in Jobs Trump,Speaking in the White Faces a Reckoning
P2JW090000-4-A00100-17FFFF5178F ADVERTISEMENT Breaking news:your old 401k could be costing you. Getthe scoop on page R14. **** MONDAY,MARCH 30,2020~VOL. CCLXXV NO.74 WSJ.com HHHH $4.00 Last week: DJIA 21636.78 À 2462.80 12.8% NASDAQ 7502.38 À 9.1% STOXX 600 310.90 À 6.1% 10-YR. TREASURY À 1 26/32 , yield 0.744% OIL $21.51 g $1.12 EURO $1.1139 YEN 107.94 In Central Park, a Field Hospital Is Built for Virus Patients Trump What’s News Extends Distance Business&Finance Rules to edical-supplies makers Mand distributors are raising redflagsabout what April 30 they sayisalack of govern- ment guidanceonwhereto send products, as hospitals As U.S. death toll passes competefor scarce gear amid 2,000, experts call for the coronavirus pandemic. A1 GES staying apart amid Washingtonisrelying on IMA the Fed, to an unprecedented need formoretesting degree in peacetime,topre- GETTY servebusinessbalancesheets SE/ President Trump said he was as Congressreloads the cen- extending the administration’s tral bank’sability to lend. A4 ANCE-PRES social-distancing guidelines Manyactivist investorsare FR through the end of April as the walking away from campaigns U.S. death toll from the new GENCE or settling with firms early as /A coronavirus surgedpast 2,000 some demands seem less over the weekend. pertinent in altered times. B1 ANCUR BET Thestock market’s unri- By Rebecca Ballhaus, valed swingsthis month have KENA Andrew Restuccia OPEN ARMS: The Samaritan’s Purse charity set up an emergency field hospital in Central Park on Sunday near Mount Sinai Hospital, ignited even more interest and Jennifer Calfas which it said would be used to care for coronavirus patients. -

Introducing the Iwatch
May 2014 Jun June 2014 Welcome to Volume 5, Issue 6 of iDevices (iPhone, iPod & iPad) SIG Meetings Need Help? Go to the iDevice FORUM, click HERE To find Apps that are free for a short time, click these 2 icons: Introducing the iWatch Click to see the video New iPhone Lock screen bypass discovered Here's how to protect against it! By Rene Ritchie, Monday, Jun 9, 2014 16 A new iOS 7.1.1 iPhone Lock screen bypass has been discovered. Lock screen bypasses in and of themselves aren't new — trying to protect a phone while also allowing access to convenient features results is an incredible tension — but this one can provide access to an app, which makes it one of the most serious to date. It does require physical access to your iPhone, but if you do lose possession, here's how the bypass works and, more importantly, how you can protect yourself from it. Note: iMore tested the exploit and its scope before reporting on it. We were able to duplicate it but also get a sense of its ramifications and limitations. First, in order to get around the passcode lock, this bypass requires that the iPhone be placed into Airplane mode, and that a missed phone call notification be present. When those conditions are met, tapping or swiping the missed call notification will cause a Settings popup to appear on top of whatever app was last active (in the foreground) on the iPhone prior to it being locked. Dismiss the popup and you have access to the app. -
Ideal Spaces OS-Platform-Browser Support
z 4.9 OS-Platform-Browser Support v1.4 2020spaces.com 4.9 Table of Contents Overview....................................................................................................... 3 System Requirements ................................................................................... 4 Windows .................................................................................................................................................... 4 Mac ............................................................................................................................................................ 4 Support Criteria ............................................................................................ 5 OS Platform ................................................................................................................................................ 5 OS Version .................................................................................................................................................. 5 Web Browser and Operating System Combinations ..................................... 6 Current Platform / Web Browser Support ................................................................................................. 6 Out of Scope Browsers and Operating Systems ............................................ 7 Opera ..................................................................................................................................................... 7 Linux ...................................................................................................................................................... -

View Managing Devices and Corporate Data On
Overview Managing Devices & Corporate Data on iOS Overview Overview Contents Businesses everywhere are empowering their employees with iPhone and iPad. Overview Management Basics The key to a successful mobile strategy is balancing IT control with user Separating Work and enablement. By personalizing iOS devices with their own apps and content, Personal Data users take greater ownership and responsibility, leading to higher levels of Flexible Management Options engagement and increased productivity. This is enabled by Apple’s management Summary framework, which provides smart ways to manage corporate data and apps discretely, seamlessly separating work data from personal data. Additionally, users understand how their devices are being managed and trust that their privacy is protected. This document offers guidance on how essential IT control can be achieved while at the same time keeping users enabled with the best tools for their job. It complements the iOS Deployment Reference, a comprehensive online technical reference for deploying and managing iOS devices in your enterprise. To refer to the iOS Deployment Reference, visit help.apple.com/deployment/ios. Managing Devices and Corporate Data on iOS July 2018 2 Management Basics Management Basics With iOS, you can streamline iPhone and iPad deployments using a range of built-in techniques that allow you to simplify account setup, configure policies, distribute apps, and apply device restrictions remotely. Our simple framework With Apple’s unified management framework in iOS, macOS, tvOS, IT can configure and update settings, deploy applications, monitor compliance, query devices, and remotely wipe or lock devices. The framework supports both corporate-owned and user-owned as well as personally-owned devices. -

Best Practices for Developing for Chromebook Tablets
1 Best practices for developing for Chromebook tablets The goal of this guide is to share some best practices for developing Android and web apps for Chromebook tablets. With the help of educators and developers around the globe, we’ve learned some tips and tricks along the way and want to share those with you and your team. Chromebook tablets come in many different shapes and sizes and run all sorts of software—from traditional websites to extensions, progressive web apps, and Android apps. In many ways, Chromebook tablets operate the same as a traditional Chromebook. The operating system is largely the same. They’re managed the same and run the same apps. Educators tell us that the smaller and lighter form of the tablet and no built-in mouse or keyboard changes how they and students use the device. For example: ● Many schools use tablets in early elementary, special education, and media classes where entering text, typing, and testing are less prevalent. ● Tablets are more conducive to handwriting notes, reading, filming, photography, and touchscreen apps than traditional laptops. ● Some schools prefer to use Android apps with tablets (because they’re designed for touchscreens) instead of using websites (usually designed for a mouse). This guide aims to help you adapt your apps to support these differences. Best practice 1: Google Drive integration One of the things that has made Chromebooks and Chromebook tablets so successful in schools over the years is that students can sign in to any device and access their files anywhere, anytime—such is the nature of the web! Android apps tend to work a little differently because they run natively (offline). -

Lexia Core5 Tech Reqs
EXPANDED Lexia Customer Support SYSTEM 21 LEVELS [email protected] US: 800-507-2772; Outside US: 978-405-6231 System Requirements Web Version: www.lexiacore5.com For all browsers and platforms REQUIREMENTS Operating Systems and Browsers • Headsets (recommended) 1024x768 screen resolution (recommended) MacOS • • 10.12+ • 4 GB RAM (recommended), 2 GB (minimum) • Chrome 64+, Safari 10+, Firefox 62+ • Javascript must be enabled Persistent Internet connection (required) Windows • • Windows 7+ • Bandwidth: A typical student consumes 15MB of • Chrome 64+, Edge 44+, Firefox 62+ bandwidth per 5-min block (average rate ~0.4 Mbps). A classroom of 25 students consumes 750MB of band- Google Chrome OS width per 30-min session (average rate ~3.33 Mbps). 74+ • Bandwidth need is typically higher just after students • Chromebook, Chromebook Touchscreen log in and decreases after a few minutes of use. A 6MB download occurs upon logging into the Core5 product. iPad Version • iPad 4+, iPad Mini 3+, iPad Air+, iPad Pro (iOS 10+) • 1.9 GB storage space (1.65 GB for initial download) • Persistent Internet connection (minimal bandwidth is used) myLexia.com (the educator website) myLexia for iOS Chrome 64+, Edge 44+, Firefox 62+, Safari 11+ • iPhone, and iPod Touch with iOS 11.0+ • Apple Watch with watchOS 4.0+ Whitelisting, Firewall, Proxies, Content Filtering—Allow Access https://*.mylexia.com http://www.lexiacore5.com .salesforceliveagent.com (required only to use myLexia Support Chat) Note: Thin clients, Citrix, Terminal Services/Remote Desktop, virtual machines, and other remote access or PC-sharing systems are not supported. P-C5-21-SYS-0919 © 2019 Lexia Learning, a Rosetta Stone Company. -

Grapher 12 Quick Start Guide
GrapherTM Registration Information Your Grapher serial number is located on the CD cover or in the email download instructions, depending on how you purchased Grapher. Register your Grapher serial number online at www.GoldenSoftware.com. This information will not be redistributed. Registration entitles you to free technical support, free minor updates, and upgrade pricing on future Grapher releases. The serial number is required when you run Grapher the first time, contact technical support, or purchase Grapher upgrades. For future reference, write your serial number on the line below. _________________________________ GrapherTM Quick Start Guide The Ultimate Technical Graphing Package Golden Software, LLC 809 14th Street, Golden, Colorado 80401-1866, U.S.A. Phone: 303-279-1021 Fax: 303-279-0909 www.GoldenSoftware.com COPYRIGHT NOTICE Copyright Golden Software, LLC 2016 The GrapherTM program is furnished under a license agreement. The Grapher software and quick start guide may be used or copied only in accordance with the terms of the agreement. It is against the law to copy the software or quick start guide on any medium except as specifically allowed in the license agreement. Contents are subject to change without notice. Grapher is a registered trademark of Golden Software, LLC. All other trademarks are the property of their respective owners. March 2016 Quick Start Guide Table of Contents Introduction to Grapher ......................................................................................1 System Requirements ........................................................................................2