The Key-Dependent Message Security of Key-Alternating Feistel Ciphers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Two Practical and Provably Secure Block Ciphers: BEAR and LION
Two Practical and Provably Secure Block Ciphers: BEAR and LION Ross Anderson 1 and Eh Biham 2 Cambridge University, England; emall rja14~cl.cmn.ar .uk 2 Technion, Haifa, Israel; email biham~cs .teclmion.ac.il Abstract. In this paper we suggest two new provably secure block ci- phers, called BEAR and LION. They both have large block sizes, and are based on the Luby-Rackoff construction. Their underlying components are a hash function and a stream cipher, and they are provably secure in the sense that attacks which find their keys would yield attacks on one or both of the underlying components. They also have the potential to be much faster than existing block ciphers in many applications. 1 Introduction There are a number of ways in which cryptographic primitives can be trans- formed by composition, such as output feedback mode which transforms a block cipher into a stream cipher, and feedforward mode which transforms it into a hash function [P]. A number of these reductions are provable, in the sense that certain kinds of attack on the composite function would yield an attack on the underlying primitive; a recent example is the proof that the ANSI message au- thentication code is as secure as the underlying block cipher [BKR]. One construction which has been missing so far is a means of building a block cipher out of a stream cipher. In this paper, we show provably secure ways to construct a block cipher from a stream cipher and a hash function. Given that ways of constructing keyed hash functions from stream ciphers already exist [LRW] [K], this enables block ciphers to be constructed from stream ciphers. -

Identifying Open Research Problems in Cryptography by Surveying Cryptographic Functions and Operations 1
International Journal of Grid and Distributed Computing Vol. 10, No. 11 (2017), pp.79-98 http://dx.doi.org/10.14257/ijgdc.2017.10.11.08 Identifying Open Research Problems in Cryptography by Surveying Cryptographic Functions and Operations 1 Rahul Saha1, G. Geetha2, Gulshan Kumar3 and Hye-Jim Kim4 1,3School of Computer Science and Engineering, Lovely Professional University, Punjab, India 2Division of Research and Development, Lovely Professional University, Punjab, India 4Business Administration Research Institute, Sungshin W. University, 2 Bomun-ro 34da gil, Seongbuk-gu, Seoul, Republic of Korea Abstract Cryptography has always been a core component of security domain. Different security services such as confidentiality, integrity, availability, authentication, non-repudiation and access control, are provided by a number of cryptographic algorithms including block ciphers, stream ciphers and hash functions. Though the algorithms are public and cryptographic strength depends on the usage of the keys, the ciphertext analysis using different functions and operations used in the algorithms can lead to the path of revealing a key completely or partially. It is hard to find any survey till date which identifies different operations and functions used in cryptography. In this paper, we have categorized our survey of cryptographic functions and operations in the algorithms in three categories: block ciphers, stream ciphers and cryptanalysis attacks which are executable in different parts of the algorithms. This survey will help the budding researchers in the society of crypto for identifying different operations and functions in cryptographic algorithms. Keywords: cryptography; block; stream; cipher; plaintext; ciphertext; functions; research problems 1. Introduction Cryptography [1] in the previous time was analogous to encryption where the main task was to convert the readable message to an unreadable format. -

All-Or-Nothing Encryption and the Package Transform
All-or-Nothing Encryption and the Package Transform Ronald L. Rivest MIT Laboratory for Computer Science 545 Technology Square, Cambridge, Mass. 02139 rivest@theory, ics.mit, edu Abstract. We present a new mode of encryption for block ciphers, which we call all-or-nothing encryption. This mode has the interesting defining property that one must decrypt the entire ciphertext before one can de- termine even one message block. This means that brute-force searches against all-or-nothing encryption are slowed down by a factor equal to the number of blocks in the ciphertext. We give a specific way of im- plementing all-or-nothing encryption using a "package transform" as a pre-processing step to an ordinary encryption mode. A package trans- form followed by ordinary codebook encryption also has the interest- ing property that it is very efficiently implemented in parallel. All-or- nothing encryption can also provide protection against chosen-plaintext and related-message attacks. 1 Introduction One way in which a cryptosystem may be attacked is by brute-force search: an adversary tries decrypting an intercepted ciphertext with all possible keys until the plaintext "makes sense" or until it matches a known target plaintext. Our primary motivation is to devise means to make brute-force search more difficult, by appropriately pre-processing a message before encrypting it. In this paper, we assume that the cipher under discussion is a block cipher with fixed-length input/output blocks, although our remarks generalize to other kinds of ciphers. An "encryption mode" is used to extend the encryption function to arbitrary length messages (see, for example, Schneier [9] and Biham [3]). -

Building Provably Secure Block Ciphers from Cryptographic Hash Functions
International Journal of Computer Applications (0975 - 8887) Volume 176 - No.16, April 2020 Building Provably Secure Block Ciphers from Cryptographic Hash Functions Charles F. de Barros Department of Computer Science Federal University of Sao˜ Joao˜ del Rei Minas Gerais, Brazil ABSTRACT The former must satisfy certain criteria, such as confusion and diffusion, while the latter should have properties like collision This paper presents a proposal for the construction of provably resistance. It can be said that these primitives are inherently secure block ciphers based on cryptographic hash functions. different, mainly because block ciphers are reversible (it is always The core idea consists of using a hash function to generate possible to decrypt an encrypted message, given the proper key), pseudorandom strings to be combined with the message blocks. while hash functions are, by design, irreversible. Each one of these strings depend on the previous ciphertext block Nevertheless, there is a certain similarity in the way block ciphers (or the initialization vector, in the case of the first message block), and hash functions are built. In fact, both are based on iterations: the secret key k and a block key derived from k. One of the block ciphers consist of iterations of a round function, while hash main features of the proposed construction is that it allows keys of algorithms are built upon iterations of a compression function. As arbitrary length, since the key itself is never directly combined with a matter of fact, it is possible to build hash functions from block the message. Furthermore, even if an adversary manages to guess ciphers, due to the fact that block ciphers are natural compression all of the block keys, he can’t efficiently retrieve the master secret functions, which makes them suitable to be used at the core of key or the message, provided that the underlying hash function the so-called Merkle-Damgard˚ [1] construction for cryptographic is cryptographically secure. -
Taxophrase: Exploring Knowledge Base Via Joint Learning of Taxonomy and Topical Phrases
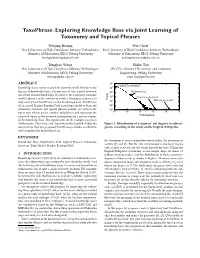
TaxoPhrase: Exploring Knowledge Base via Joint Learning of Taxonomy and Topical Phrases Weijing Huang Wei Chen∗ Key Laboratory of High Confidence Software Technologies Key Laboratory of High Confidence Software Technologies (Ministry of Education), EECS, Peking University (Ministry of Education), EECS, Peking University [email protected] [email protected] Tengjiao Wang Shibo Tao Key Laboratory of High Confidence Software Technologies SPCCTA, School of Electronics and Computer (Ministry of Education), EECS, Peking University Engineering, Peking University [email protected] [email protected] ABSTRACT 106 Politics_of_Morelos Knowledge bases restore many facts about the world. But due to the 105 big size of knowledge bases, it is not easy to take a quick overview 104 Mathematics onto their restored knowledge. In favor of the taxonomy structure 3 10 Musicians_by_band and the phrases in the content of entities, this paper proposes an Freq 2 Albums_by_artist exploratory tool TaxoPhrase on the knowledge base. TaxoPhrase 10 (1) is a novel Markov Random Field based topic model to learn the 101 taxonomy structure and topical phrases jointly; (2) extracts the 0 10 0 1 2 3 4 5 topics over subcategories, entities, and phrases, and represents the 10 10 10 10 10 10 extracted topics as the overview information for a given category Outdegree in the knowledge base. The experiments on the example categories Mathematics, Chemistry, and Argentina in the English Wikipedia Figure 1: Distribution of categories’ out degrees to subcate- demonstrate that our proposed TaxoPhrase provides an effective gories, according to the study on the English Wikipedia. tool to explore the knowledge base. KEYWORDS the taxonomy, it seems straightforward to utilize the taxonomy to Knowledge Base, Exploratory Tool, Topical Phrases, Taxonomy answer Q1 and Q2. -

Statistical Cryptanalysis of Block Ciphers
STATISTICAL CRYPTANALYSIS OF BLOCK CIPHERS THÈSE NO 3179 (2005) PRÉSENTÉE À LA FACULTÉ INFORMATIQUE ET COMMUNICATIONS Institut de systèmes de communication SECTION DES SYSTÈMES DE COMMUNICATION ÉCOLE POLYTECHNIQUE FÉDÉRALE DE LAUSANNE POUR L'OBTENTION DU GRADE DE DOCTEUR ÈS SCIENCES PAR Pascal JUNOD ingénieur informaticien dilpômé EPF de nationalité suisse et originaire de Sainte-Croix (VD) acceptée sur proposition du jury: Prof. S. Vaudenay, directeur de thèse Prof. J. Massey, rapporteur Prof. W. Meier, rapporteur Prof. S. Morgenthaler, rapporteur Prof. J. Stern, rapporteur Lausanne, EPFL 2005 to Mimi and Chlo´e Acknowledgments First of all, I would like to warmly thank my supervisor, Prof. Serge Vaude- nay, for having given to me such a wonderful opportunity to perform research in a friendly environment, and for having been the perfect supervisor that every PhD would dream of. I am also very grateful to the president of the jury, Prof. Emre Telatar, and to the reviewers Prof. em. James L. Massey, Prof. Jacques Stern, Prof. Willi Meier, and Prof. Stephan Morgenthaler for having accepted to be part of the jury and for having invested such a lot of time for reviewing this thesis. I would like to express my gratitude to all my (former and current) col- leagues at LASEC for their support and for their friendship: Gildas Avoine, Thomas Baign`eres, Nenad Buncic, Brice Canvel, Martine Corval, Matthieu Finiasz, Yi Lu, Jean Monnerat, Philippe Oechslin, and John Pliam. With- out them, the EPFL (and the crypto) would not be so fun! Without their support, trust and encouragement, the last part of this thesis, FOX, would certainly not be born: I owe to MediaCrypt AG, espe- cially to Ralf Kastmann and Richard Straub many, many, many hours of interesting work. -

Research Problems in Block Cipher Cryptanalysis: an Experimental Analysis Amandeep, G
International Journal of Innovative Technology and Exploring Engineering (IJITEE) ISSN: 2278-3075, Volume-8 Issue-8S3, June 2019 Research Problems in Block Cipher Cryptanalysis: An Experimental Analysis Amandeep, G. Geetha Abstract: Cryptography has always been a very concerning Organization of this paper is as follows. Section 2 lists the issue in research related to digital security. The dynamic need of Block ciphers in a chronological order in a table having six applications and keeping online transactions secure have been columns stating name of the algorithm, year of publication, giving pathways to the need of developing different its cryptographic strategies. Though a number of cryptographic structure, block size, key size, and the cryptanalysis done on algorithms have been introduced till now, but each of these algorithms has its own disadvantages or weaknesses which are that particular cipher. This table becomes the basis of the identified by the process of cryptanalysis. This paper presents a analysis done in Section 3 and tabulates the information as to survey of different block ciphers and the results of attempts to which structure has been cryptanalyzed more, thereby identify their weakness. Depending upon the literature review, establishing a trend of structures analyzed Section 4 some open research problems are being presented which the identifies the open research problems based on the analysis cryptologists can depend on to work for bettering cyber security. done in Section 3. Section 5 of the paper, presents the conclusion of this study. Index Terms: block ciphers, cryptanalysis, attacks, SPN, Feistel. II. RELATED WORK I. INTRODUCTION This paper surveys 69 block ciphers and presents, in Cryptography is the science which deals with Table I, a summarized report as per the attacks concerned. -

SECURE ALGORITHMS Minding Your MAC Algorithms?
SECURE ALGORITHMS Abstract In spite of the advantages of digital signa- tures, MAC algorithms are still widely used to authenticate data; common uses include authorization of financial transactions, mo- bile communications (GSM and 3GPP), and authentication of Internet communications with SSL/TLS and IPsec. While some MAC algorithms are part of ‘legacy’ implementa- tions, the success of MAC algorithms is mainly due to their much lower computa- tional and storage costs (compared to digital signatures). This article describes a list of common pitfalls that the authors have en- countered when evaluating MAC algorithms deployed in commercial applications and pro- vides some recommendations for practitio- ners. Minding Your Introduction MAC Algorithms? MAC algorithms compute a short string as a complex function of a message and a secret key. In a communications setting, the sender will ap- Helena Handschuh pend the MAC value to the message (see also Gemplus, France Figure 1). The recipient shares a secret key with the sender. On receipt of the message, he recom- putes the MAC value using the shared key and Bart Preneel verifies that it is the same as the MAC value sent K.U.Leuven, Belgium along with the message. If the MAC value is cor- rect, he can be convinced that the message origi- nated from the particular sender and that it has not been tampered with during the transmis- sion. Indeed, if an opponent modifies the mes- sage, the MAC value will no longer be correct. Moreover, the opponent does not know the se- cret key, so he is not able to predict how the MAC value should be modified. -

Statistical Cryptanalysis of Block Ciphers
Statistical Cryptanalysis of Block Ciphers THESE` N◦ 3179 (2004) PRESENT´ EE´ A` LA FACULTE´ INFORMATIQUE & COMMUNICATIONS Institut de syst`emes de communication SECTION DES SYSTEMES` DE COMMUNICATION ECOLE´ POLYTECHNIQUE FED´ ERALE´ DE LAUSANNE POUR L'OBTENTION DU GRADE DE DOCTEUR ES` SCIENCES PAR Pascal JUNOD ing´enieur informaticien diplom´e EPF de nationalit´e suisse et originaire de Sainte-Croix (VD) accept´ee sur proposition du jury: Prof. Emre Telatar (EPFL), pr´esident du jury Prof. Serge Vaudenay (EPFL), directeur de th`ese Prof. Jacques Stern (ENS Paris, France), rapporteur Prof. em. James L. Massey (ETHZ & Lund University, Su`ede), rapporteur Prof. Willi Meier (FH Aargau), rapporteur Prof. Stephan Morgenthaler (EPFL), rapporteur Lausanne, EPFL 2005 to Mimi and Chlo´e Acknowledgments First of all, I would like to warmly thank my supervisor, Prof. Serge Vaude- nay, for having given to me such a wonderful opportunity to perform research in a friendly environment, and for having been the perfect supervisor that every PhD would dream of. I am also very grateful to the president of the jury, Prof. Emre Telatar, and to the reviewers Prof. em. James L. Massey, Prof. Jacques Stern, Prof. Willi Meier, and Prof. Stephan Morgenthaler for having accepted to be part of the jury and for having invested such a lot of time for reviewing this thesis. I would like to express my gratitude to all my (former and current) col- leagues at LASEC for their support and for their friendship: Gildas Avoine, Thomas Baign`eres, Nenad Buncic, Brice Canvel, Martine Corval, Matthieu Finiasz, Yi Lu, Jean Monnerat, Philippe Oechslin, and John Pliam. -

Block Ciphers
This is a Chapter from the Handbook of Applied Cryptography, by A. Menezes, P. van Oorschot, and S. Vanstone, CRC Press, 1996. For further information, see www.cacr.math.uwaterloo.ca/hac CRC Press has granted the following specific permissions for the electronic version of this book: Permission is granted to retrieve, print and store a single copy of this chapter for personal use. This permission does not extend to binding multiple chapters of the book, photocopying or producing copies for other than personal use of the person creating the copy, or making electronic copies available for retrieval by others without prior permission in writing from CRC Press. Except where over-ridden by the specific permission above, the standard copyright notice from CRC Press applies to this electronic version: Neither this book nor any part may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, microfilming, and recording, or by any information storage or retrieval system, without prior permission in writing from the publisher. The consent of CRC Press does not extend to copying for general distribution, for promotion, for creating new works, or for resale. Specific permission must be obtained in writing from CRC Press for such copying. c 1997 by CRC Press, Inc. Chapter 7 Block Ciphers Contents in Brief 7.1 Introduction and overview :::::::::::::::::::::223 7.2 Background and general concepts :::::::::::::::::224 7.3 Classical ciphers and historical development ::::::::::::237 7.4 DES :::::::::::::::::::::::::::::::::250 7.5 FEAL ::::::::::::::::::::::::::::::::259 7.6 IDEA ::::::::::::::::::::::::::::::::263 7.7 SAFER, RC5, and other block ciphers :::::::::::::::266 7.8 Notes and further references ::::::::::::::::::::271 7.1 Introduction and overview Symmetric-key block ciphers are the most prominent and important elements in many cryp- tographic systems. -
7.4.2 DES Algorithm DES Is a Feistel Cipher Which Processes Plaintext Blocks of N =64Bits, Producing 64-Bit Ciphertext Blocks (Figure 7.8)
252 Ch. 7 Block Ciphers 7.4.2 DES algorithm DES is a Feistel cipher which processes plaintext blocks of n =64bits, producing 64-bit ciphertext blocks (Figure 7.8). The effective size of the secret key K is k =56bits; more precisely, the input key K is speci®ed as a 64-bit key, 8 bits of which (bits 8; 16;::: ;64) may be used as parity bits. The 256 keys implement (at most) 256 of the 264! possible bijec- tions on 64-bit blocks. A widely held belief is that the parity bits were introduced to reduce the effective key size from 64 to 56 bits, to intentionally reduce the cost of exhaustive key search by a factor of 256. K K plaintext P 56 56 ciphertext C K 64key 64 −1 PCDESC DES P Figure 7.8: DES input-output. Full details of DES are given in Algorithm 7.82 and Figures 7.9 and 7.10. An overview follows. Encryption proceeds in 16 stages or rounds. From the input key K, sixteen 48-bit subkeys Ki are generated, one for each round. Within each round, 8 ®xed, carefully selected 6-to-4 bit substitution mappings (S-boxes) Si, collectively denoted S, are used. The 64-bit plaintext is divided into 32-bit halves L0 and R0. Each round is functionally equivalent, taking 32-bit inputs Li−1 and Ri−1 from the previous round and producing 32-bit outputs Li and Ri for 1 ≤ i ≤ 16, as follows: Li = Ri−1; (7.4) Ri = Li−1 ⊕ f(Ri−1;Ki); where f(Ri−1;Ki)=P (S(E(Ri−1) ⊕ Ki))(7.5) Here E is a ®xed expansion permutation mapping Ri−1 from 32 to 48 bits (all bits are used once; some are used twice). -
Py (Roo): a Fast and Secure Stream Cipher
University of Wollongong Research Online Faculty of Engineering and Information Faculty of Informatics - Papers (Archive) Sciences 24-5-2005 Py (Roo): A Fast and Secure Stream Cipher E. Biham Computer Science Department, Technion, Israel Jennifer Seberry University of Wollongong, [email protected] Follow this and additional works at: https://ro.uow.edu.au/infopapers Part of the Physical Sciences and Mathematics Commons Recommended Citation Biham, E. and Seberry, Jennifer: Py (Roo): A Fast and Secure Stream Cipher 2005. https://ro.uow.edu.au/infopapers/274 Research Online is the open access institutional repository for the University of Wollongong. For further information contact the UOW Library: [email protected] Py (Roo): A Fast and Secure Stream Cipher Abstract Py (pronounced Roo, a shorthand for Kangaroo) is a new stream cipher designed especially for the Ecrypt stream cipher contest. It is based on a new kind of primitive, which we call Rolling Arrays. It also uses various other ideas from many types of ciphers, including variable rotations and permutations. In some sense, this design is a kind of a new type of rotor machine, which is specially designed with operations that are very efficient in software. The allowed stream size is 2(to the power 64) bytes in each stream (or 2 (to the power 40) in the smaller version Py6). The security claims of the cipher are that no key recovery attacks can be performed with complexity smaller than that of exhaustive search, and distinguishing attacks are also impractical with a similar complexity. The speed of the cipher is impressively fast, as it is more than 2.5 times faster than RC4 on a Pentium III (with less than 2.9 cycles/byte when implemented with the API of NESSIE and tested with the NESSIE software).