Block Ciphers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

COS433/Math 473: Cryptography Mark Zhandry Princeton University Spring 2017 Cryptography Is Everywhere a Long & Rich History
COS433/Math 473: Cryptography Mark Zhandry Princeton University Spring 2017 Cryptography Is Everywhere A Long & Rich History Examples: • ~50 B.C. – Caesar Cipher • 1587 – Babington Plot • WWI – Zimmermann Telegram • WWII – Enigma • 1976/77 – Public Key Cryptography • 1990’s – Widespread adoption on the Internet Increasingly Important COS 433 Practice Theory Inherent to the study of crypto • Working knowledge of fundamentals is crucial • Cannot discern security by experimentation • Proofs, reductions, probability are necessary COS 433 What you should expect to learn: • Foundations and principles of modern cryptography • Core building blocks • Applications Bonus: • Debunking some Hollywood crypto • Better understanding of crypto news COS 433 What you will not learn: • Hacking • Crypto implementations • How to design secure systems • Viruses, worms, buffer overflows, etc Administrivia Course Information Instructor: Mark Zhandry (mzhandry@p) TA: Fermi Ma (fermima1@g) Lectures: MW 1:30-2:50pm Webpage: cs.princeton.edu/~mzhandry/2017-Spring-COS433/ Office Hours: please fill out Doodle poll Piazza piaZZa.com/princeton/spring2017/cos433mat473_s2017 Main channel of communication • Course announcements • Discuss homework problems with other students • Find study groups • Ask content questions to instructors, other students Prerequisites • Ability to read and write mathematical proofs • Familiarity with algorithms, analyZing running time, proving correctness, O notation • Basic probability (random variables, expectation) Helpful: • Familiarity with NP-Completeness, reductions • Basic number theory (modular arithmetic, etc) Reading No required text Computer Science/Mathematics Chapman & Hall/CRC If you want a text to follow along with: Second CRYPTOGRAPHY AND NETWORK SECURITY Cryptography is ubiquitous and plays a key role in ensuring data secrecy and Edition integrity as well as in securing computer systems more broadly. -

The Mathemathics of Secrets.Pdf
THE MATHEMATICS OF SECRETS THE MATHEMATICS OF SECRETS CRYPTOGRAPHY FROM CAESAR CIPHERS TO DIGITAL ENCRYPTION JOSHUA HOLDEN PRINCETON UNIVERSITY PRESS PRINCETON AND OXFORD Copyright c 2017 by Princeton University Press Published by Princeton University Press, 41 William Street, Princeton, New Jersey 08540 In the United Kingdom: Princeton University Press, 6 Oxford Street, Woodstock, Oxfordshire OX20 1TR press.princeton.edu Jacket image courtesy of Shutterstock; design by Lorraine Betz Doneker All Rights Reserved Library of Congress Cataloging-in-Publication Data Names: Holden, Joshua, 1970– author. Title: The mathematics of secrets : cryptography from Caesar ciphers to digital encryption / Joshua Holden. Description: Princeton : Princeton University Press, [2017] | Includes bibliographical references and index. Identifiers: LCCN 2016014840 | ISBN 9780691141756 (hardcover : alk. paper) Subjects: LCSH: Cryptography—Mathematics. | Ciphers. | Computer security. Classification: LCC Z103 .H664 2017 | DDC 005.8/2—dc23 LC record available at https://lccn.loc.gov/2016014840 British Library Cataloging-in-Publication Data is available This book has been composed in Linux Libertine Printed on acid-free paper. ∞ Printed in the United States of America 13579108642 To Lana and Richard for their love and support CONTENTS Preface xi Acknowledgments xiii Introduction to Ciphers and Substitution 1 1.1 Alice and Bob and Carl and Julius: Terminology and Caesar Cipher 1 1.2 The Key to the Matter: Generalizing the Caesar Cipher 4 1.3 Multiplicative Ciphers 6 -

Two Practical and Provably Secure Block Ciphers: BEAR and LION
Two Practical and Provably Secure Block Ciphers: BEAR and LION Ross Anderson 1 and Eh Biham 2 Cambridge University, England; emall rja14~cl.cmn.ar .uk 2 Technion, Haifa, Israel; email biham~cs .teclmion.ac.il Abstract. In this paper we suggest two new provably secure block ci- phers, called BEAR and LION. They both have large block sizes, and are based on the Luby-Rackoff construction. Their underlying components are a hash function and a stream cipher, and they are provably secure in the sense that attacks which find their keys would yield attacks on one or both of the underlying components. They also have the potential to be much faster than existing block ciphers in many applications. 1 Introduction There are a number of ways in which cryptographic primitives can be trans- formed by composition, such as output feedback mode which transforms a block cipher into a stream cipher, and feedforward mode which transforms it into a hash function [P]. A number of these reductions are provable, in the sense that certain kinds of attack on the composite function would yield an attack on the underlying primitive; a recent example is the proof that the ANSI message au- thentication code is as secure as the underlying block cipher [BKR]. One construction which has been missing so far is a means of building a block cipher out of a stream cipher. In this paper, we show provably secure ways to construct a block cipher from a stream cipher and a hash function. Given that ways of constructing keyed hash functions from stream ciphers already exist [LRW] [K], this enables block ciphers to be constructed from stream ciphers. -

An Investigation Into Mathematical Cryptography with Applications
Project Report BSc (Hons) Mathematics An Investigation into Mathematical Cryptography with Applications Samuel Worton 1 CONTENTS Page: 1. Summary 3 2. Introduction to Cryptography 4 3. A History of Cryptography 6 4. Introduction to Modular Arithmetic 12 5. Caesar Cipher 16 6. Affine Cipher 17 7. Vigenère Cipher 19 8. Autokey Cipher 21 9. One-Time Pad 22 10. Pohlig-Hellman Encryption 24 11. RSA Encryption 27 12. MATLAB 30 13. Conclusion 35 14. Glossary 36 15. References 38 2 1. SUMMARY AND ACKNOWLEDGEMENTS In this report, I will explore the history of cryptography, looking at the origins of cryptosystems in the BC years all the way through to the current RSA cryptosystem which governs the digital era we live in. I will explain the mathematics behind cryptography and cryptanalysis, which is largely based around number theory and in particular, modular arithmetic. I will relate this to several famous, important and relevant cryptosystems, and finally I will use the MATLAB program to write codes for a few of these cryptosystems. I would like to thank Mr. Kuldeep Singh for his feedback and advice during all stages of my report, as well as enthusiasm towards the subject. I would also like to thank Mr. Laurence Taylor for generously giving his time to help me in understanding and producing the MATLAB coding used towards the end of this investigation. Throughout this report I have been aided by the book ‘Elementary Number Theory’ by Mr. David M. Burton, amongst others, which was highly useful in refreshing my number theory knowledge and introducing me to the concepts of cryptography; also Mr. -

Identifying Open Research Problems in Cryptography by Surveying Cryptographic Functions and Operations 1
International Journal of Grid and Distributed Computing Vol. 10, No. 11 (2017), pp.79-98 http://dx.doi.org/10.14257/ijgdc.2017.10.11.08 Identifying Open Research Problems in Cryptography by Surveying Cryptographic Functions and Operations 1 Rahul Saha1, G. Geetha2, Gulshan Kumar3 and Hye-Jim Kim4 1,3School of Computer Science and Engineering, Lovely Professional University, Punjab, India 2Division of Research and Development, Lovely Professional University, Punjab, India 4Business Administration Research Institute, Sungshin W. University, 2 Bomun-ro 34da gil, Seongbuk-gu, Seoul, Republic of Korea Abstract Cryptography has always been a core component of security domain. Different security services such as confidentiality, integrity, availability, authentication, non-repudiation and access control, are provided by a number of cryptographic algorithms including block ciphers, stream ciphers and hash functions. Though the algorithms are public and cryptographic strength depends on the usage of the keys, the ciphertext analysis using different functions and operations used in the algorithms can lead to the path of revealing a key completely or partially. It is hard to find any survey till date which identifies different operations and functions used in cryptography. In this paper, we have categorized our survey of cryptographic functions and operations in the algorithms in three categories: block ciphers, stream ciphers and cryptanalysis attacks which are executable in different parts of the algorithms. This survey will help the budding researchers in the society of crypto for identifying different operations and functions in cryptographic algorithms. Keywords: cryptography; block; stream; cipher; plaintext; ciphertext; functions; research problems 1. Introduction Cryptography [1] in the previous time was analogous to encryption where the main task was to convert the readable message to an unreadable format. -

Network Security
Cristina Nita-Rotaru CS6740: Network security Additional material: Cryptography 1: Terminology and classic ciphers Readings for this lecture Required readings: } Cryptography on Wikipedia Interesting reading } The Code Book by Simon Singh 3 Cryptography The science of secrets… } Cryptography: the study of mathematical techniques related to aspects of providing information security services (create) } Cryptanalysis: the study of mathematical techniques for attempting to defeat information security services (break) } Cryptology: the study of cryptography and cryptanalysis (both) 4 Cryptography Basic terminology in cryptography } cryptography } plaintexts } cryptanalysis } ciphertexts } cryptology } keys } encryption } decryption plaintext ciphertext plaintext Encryption Decryption Key_Encryption Key_Decryption 5 Cryptography Cryptographic protocols } Protocols that } Enable parties } Achieve objectives (goals) } Overcome adversaries (attacks) } Need to understand } Who are the parties and the context in which they act } What are the goals of the protocols } What are the capabilities of adversaries 6 Cryptography Cryptographic protocols: Parties } The good guys } The bad guys Alice Carl Bob Eve Introduction of Alice and Bob Check out wikipedia for a longer attributed to the original RSA paper. list of malicious crypto players. 7 Cryptography Cryptographic protocols: Objectives/Goals } Most basic problem: } Ensure security of communication over an insecure medium } Basic security goals: } Confidentiality (secrecy, confidentiality) } Only the -

All-Or-Nothing Encryption and the Package Transform
All-or-Nothing Encryption and the Package Transform Ronald L. Rivest MIT Laboratory for Computer Science 545 Technology Square, Cambridge, Mass. 02139 rivest@theory, ics.mit, edu Abstract. We present a new mode of encryption for block ciphers, which we call all-or-nothing encryption. This mode has the interesting defining property that one must decrypt the entire ciphertext before one can de- termine even one message block. This means that brute-force searches against all-or-nothing encryption are slowed down by a factor equal to the number of blocks in the ciphertext. We give a specific way of im- plementing all-or-nothing encryption using a "package transform" as a pre-processing step to an ordinary encryption mode. A package trans- form followed by ordinary codebook encryption also has the interest- ing property that it is very efficiently implemented in parallel. All-or- nothing encryption can also provide protection against chosen-plaintext and related-message attacks. 1 Introduction One way in which a cryptosystem may be attacked is by brute-force search: an adversary tries decrypting an intercepted ciphertext with all possible keys until the plaintext "makes sense" or until it matches a known target plaintext. Our primary motivation is to devise means to make brute-force search more difficult, by appropriately pre-processing a message before encrypting it. In this paper, we assume that the cipher under discussion is a block cipher with fixed-length input/output blocks, although our remarks generalize to other kinds of ciphers. An "encryption mode" is used to extend the encryption function to arbitrary length messages (see, for example, Schneier [9] and Biham [3]). -

Cryptanalysis of Selected Block Ciphers
Downloaded from orbit.dtu.dk on: Sep 24, 2021 Cryptanalysis of Selected Block Ciphers Alkhzaimi, Hoda A. Publication date: 2016 Document Version Publisher's PDF, also known as Version of record Link back to DTU Orbit Citation (APA): Alkhzaimi, H. A. (2016). Cryptanalysis of Selected Block Ciphers. Technical University of Denmark. DTU Compute PHD-2015 No. 360 General rights Copyright and moral rights for the publications made accessible in the public portal are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognise and abide by the legal requirements associated with these rights. Users may download and print one copy of any publication from the public portal for the purpose of private study or research. You may not further distribute the material or use it for any profit-making activity or commercial gain You may freely distribute the URL identifying the publication in the public portal If you believe that this document breaches copyright please contact us providing details, and we will remove access to the work immediately and investigate your claim. Cryptanalysis of Selected Block Ciphers Dissertation Submitted in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy at the Department of Mathematics and Computer Science-COMPUTE in The Technical University of Denmark by Hoda A.Alkhzaimi December 2014 To my Sanctuary in life Bladi, Baba Zayed and My family with love Title of Thesis Cryptanalysis of Selected Block Ciphers PhD Project Supervisor Professor Lars R. Knudsen(DTU Compute, Denmark) PhD Student Hoda A.Alkhzaimi Assessment Committee Associate Professor Christian Rechberger (DTU Compute, Denmark) Professor Thomas Johansson (Lund University, Sweden) Professor Bart Preneel (Katholieke Universiteit Leuven, Belgium) Abstract The focus of this dissertation is to present cryptanalytic results on selected block ci- phers. -

Cryptology: an Historical Introduction DRAFT
Cryptology: An Historical Introduction DRAFT Jim Sauerberg February 5, 2013 2 Copyright 2013 All rights reserved Jim Sauerberg Saint Mary's College Contents List of Figures 8 1 Caesar Ciphers 9 1.1 Saint Cyr Slide . 12 1.2 Running Down the Alphabet . 14 1.3 Frequency Analysis . 15 1.4 Linquist's Method . 20 1.5 Summary . 22 1.6 Topics and Techniques . 22 1.7 Exercises . 23 2 Cryptologic Terms 29 3 The Introduction of Numbers 31 3.1 The Remainder Operator . 33 3.2 Modular Arithmetic . 38 3.3 Decimation Ciphers . 40 3.4 Deciphering Decimation Ciphers . 42 3.5 Multiplication vs. Addition . 44 3.6 Koblitz's Kid-RSA and Public Key Codes . 44 3.7 Summary . 48 3.8 Topics and Techniques . 48 3.9 Exercises . 49 4 The Euclidean Algorithm 55 4.1 Linear Ciphers . 55 4.2 GCD's and the Euclidean Algorithm . 56 4.3 Multiplicative Inverses . 59 4.4 Deciphering Decimation and Linear Ciphers . 63 4.5 Breaking Decimation and Linear Ciphers . 65 4.6 Summary . 67 4.7 Topics and Techniques . 67 4.8 Exercises . 68 3 4 CONTENTS 5 Monoalphabetic Ciphers 71 5.1 Keyword Ciphers . 72 5.2 Keyword Mixed Ciphers . 73 5.3 Keyword Transposed Ciphers . 74 5.4 Interrupted Keyword Ciphers . 75 5.5 Frequency Counts and Exhaustion . 76 5.6 Basic Letter Characteristics . 77 5.7 Aristocrats . 78 5.8 Summary . 80 5.9 Topics and Techniques . 81 5.10 Exercises . 81 6 Decrypting Monoalphabetic Ciphers 89 6.1 Letter Interactions . 90 6.2 Decrypting Monoalphabetic Ciphers . -

The Key-Dependent Message Security of Key-Alternating Feistel Ciphers
The Key-Dependent Message Security of Key-Alternating Feistel Ciphers Pooya Farshim1, Louiza Khati2, Yannick Seurin2, and Damien Vergnaud3 1 University of York, Department of Computer Science, York, United Kingdom 2 ANSSI, Paris, France 3 Sorbonne Université, LIP6, Paris, France and Institut Universitaire de France Abstract. Key-Alternating Feistel (KAF) ciphers are a popular variant of Feistel ciphers whereby the round functions are defined as x 7→ F(ki ⊕x), where ki are the round keys and F is a public random function. Most Feistel ciphers, such as DES, indeed have such a structure. However, the security of this construction has only been studied in the classical CPA/CCA models. We provide the first security analysis of KAF ciphers in the key-dependent message (KDM) attack model, where plaintexts can be related to the private key. This model is motivated by cryptographic schemes used within application scenarios such as full-disk encryption or anonymous credential systems. We show that the four-round KAF cipher, with a single function F reused across the rounds, provides KDM security for a non-trivial set of KDM functions. To do so, we develop a generic proof methodology, based on the H-coefficient technique, that can ease the analysis of other block ciphers in such strong models of security. 1 Introduction The notion of key-dependent message (KDM) security for block ciphers was intro- duced by Black, Rogaway, and Shrimpton [5]. It guarantees strong confidentiality of communicated ciphertexts, i.e., the infeasibility of learning anything about plaintexts from the ciphertexts, even if an adversary has access to encryptions of messages that may depend on the secret key. -

Building Provably Secure Block Ciphers from Cryptographic Hash Functions
International Journal of Computer Applications (0975 - 8887) Volume 176 - No.16, April 2020 Building Provably Secure Block Ciphers from Cryptographic Hash Functions Charles F. de Barros Department of Computer Science Federal University of Sao˜ Joao˜ del Rei Minas Gerais, Brazil ABSTRACT The former must satisfy certain criteria, such as confusion and diffusion, while the latter should have properties like collision This paper presents a proposal for the construction of provably resistance. It can be said that these primitives are inherently secure block ciphers based on cryptographic hash functions. different, mainly because block ciphers are reversible (it is always The core idea consists of using a hash function to generate possible to decrypt an encrypted message, given the proper key), pseudorandom strings to be combined with the message blocks. while hash functions are, by design, irreversible. Each one of these strings depend on the previous ciphertext block Nevertheless, there is a certain similarity in the way block ciphers (or the initialization vector, in the case of the first message block), and hash functions are built. In fact, both are based on iterations: the secret key k and a block key derived from k. One of the block ciphers consist of iterations of a round function, while hash main features of the proposed construction is that it allows keys of algorithms are built upon iterations of a compression function. As arbitrary length, since the key itself is never directly combined with a matter of fact, it is possible to build hash functions from block the message. Furthermore, even if an adversary manages to guess ciphers, due to the fact that block ciphers are natural compression all of the block keys, he can’t efficiently retrieve the master secret functions, which makes them suitable to be used at the core of key or the message, provided that the underlying hash function the so-called Merkle-Damgard˚ [1] construction for cryptographic is cryptographically secure. -
Taxophrase: Exploring Knowledge Base Via Joint Learning of Taxonomy and Topical Phrases
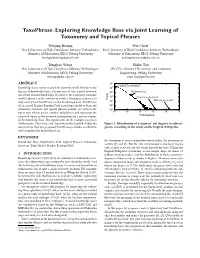
TaxoPhrase: Exploring Knowledge Base via Joint Learning of Taxonomy and Topical Phrases Weijing Huang Wei Chen∗ Key Laboratory of High Confidence Software Technologies Key Laboratory of High Confidence Software Technologies (Ministry of Education), EECS, Peking University (Ministry of Education), EECS, Peking University [email protected] [email protected] Tengjiao Wang Shibo Tao Key Laboratory of High Confidence Software Technologies SPCCTA, School of Electronics and Computer (Ministry of Education), EECS, Peking University Engineering, Peking University [email protected] [email protected] ABSTRACT 106 Politics_of_Morelos Knowledge bases restore many facts about the world. But due to the 105 big size of knowledge bases, it is not easy to take a quick overview 104 Mathematics onto their restored knowledge. In favor of the taxonomy structure 3 10 Musicians_by_band and the phrases in the content of entities, this paper proposes an Freq 2 Albums_by_artist exploratory tool TaxoPhrase on the knowledge base. TaxoPhrase 10 (1) is a novel Markov Random Field based topic model to learn the 101 taxonomy structure and topical phrases jointly; (2) extracts the 0 10 0 1 2 3 4 5 topics over subcategories, entities, and phrases, and represents the 10 10 10 10 10 10 extracted topics as the overview information for a given category Outdegree in the knowledge base. The experiments on the example categories Mathematics, Chemistry, and Argentina in the English Wikipedia Figure 1: Distribution of categories’ out degrees to subcate- demonstrate that our proposed TaxoPhrase provides an effective gories, according to the study on the English Wikipedia. tool to explore the knowledge base. KEYWORDS the taxonomy, it seems straightforward to utilize the taxonomy to Knowledge Base, Exploratory Tool, Topical Phrases, Taxonomy answer Q1 and Q2.