SECURE ALGORITHMS Minding Your MAC Algorithms?
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Software Performance of Authenticated-Encryption Modes 1
An earlier version of this paper appears at Fast Software Encryption 2011 (FSE 2011). The Software Performance of Authenticated-Encryption Modes Ted Krovetz∗ Phillip Rogawayy March 21, 2011 Abstract We study the software performance of authenticated-encryption modes CCM, GCM, and OCB. Across a variety of platforms, we find OCB to be substantially faster than either alternative. For example, on an Intel i5 (\Clarkdale") processor, good implementations of CCM, GCM, and OCB encrypt at around 4.2 cpb, 3.7 cpb, and 1.5 cpb, while CTR mode requires about 1.3 cpb. Still we find room for algorithmic improvements to OCB, showing how to trim one blockcipher call (most of the time, assuming a counter-based nonce) and reduce latency. Our findings contrast with those of McGrew and Viega (2004), who claimed similar performance for GCM and OCB. Key words: authenticated encryption, cryptographic standards, encryption speed, modes of operation, CCM, GCM, OCB. 1 Introduction Background. Over the past few years, considerable effort has been spent constructing schemes for authenticated encryption (AE). One reason is recognition of the fact that a scheme that delivers both privacy and authenticity may be more efficient than the straightforward amalgamation of separate privacy and authenticity techniques. A second reason is the realization that an AE scheme is less likely to be incorrectly used than an encryption scheme designed for privacy alone. While other possibilities exist, it is natural to build AE schemes from blockciphers, employing some mode of operation. There are two approaches. In a composed (\two-pass") AE scheme one conjoins essentially separate privacy and authenticity modes. -

Two Practical and Provably Secure Block Ciphers: BEAR and LION
Two Practical and Provably Secure Block Ciphers: BEAR and LION Ross Anderson 1 and Eh Biham 2 Cambridge University, England; emall rja14~cl.cmn.ar .uk 2 Technion, Haifa, Israel; email biham~cs .teclmion.ac.il Abstract. In this paper we suggest two new provably secure block ci- phers, called BEAR and LION. They both have large block sizes, and are based on the Luby-Rackoff construction. Their underlying components are a hash function and a stream cipher, and they are provably secure in the sense that attacks which find their keys would yield attacks on one or both of the underlying components. They also have the potential to be much faster than existing block ciphers in many applications. 1 Introduction There are a number of ways in which cryptographic primitives can be trans- formed by composition, such as output feedback mode which transforms a block cipher into a stream cipher, and feedforward mode which transforms it into a hash function [P]. A number of these reductions are provable, in the sense that certain kinds of attack on the composite function would yield an attack on the underlying primitive; a recent example is the proof that the ANSI message au- thentication code is as secure as the underlying block cipher [BKR]. One construction which has been missing so far is a means of building a block cipher out of a stream cipher. In this paper, we show provably secure ways to construct a block cipher from a stream cipher and a hash function. Given that ways of constructing keyed hash functions from stream ciphers already exist [LRW] [K], this enables block ciphers to be constructed from stream ciphers. -

Patent-Free Authenticated-Encryption As Fast As OCB
Patent-Free Authenticated-Encryption As Fast As OCB Ted Krovetz Computer Science Department California State University Sacramento, California, 95819 USA [email protected] Abstract—This paper presents an efficient authenticated encryp- VHASH hash family [4]. The resulting authenticated encryp- tion construction based on a universal hash function and block tion scheme peaks at 12.8 cpb, while OCB peaks at 13.9 cpb in cipher. Encryption is achieved via counter-mode while authenti- our experiments. The paper closes with a performance com- cation uses the Wegman-Carter paradigm. A single block-cipher parison of several well-known authenticated encryption algo- key is used for both operations. The construction is instantiated rithms [6]. using the hash functions of UMAC and VMAC, resulting in authenticated encryption with peak performance about ten per- cent slower than encryption alone. II. SECURITY DEFINITIONS We adopt the notions of security from [7], and summarize Keywords- Authenticated encryption, block-cipher mode-of- them less formally here. An authenticated encryption with as- operation, AEAD, UMAC, VMAC. sociated data (AEAD) scheme is a triple S = (K,E,D), where K is a set of keys, and E and D are encryption and decryption I. INTRODUCTION functions. Encryption occurs by computing E(k,n,h,p,f), which Traditionally when one wanted to both encrypt and authen- returns (c,t), for key k, nonce n, header h, plaintext m and ticate communications, one would encrypt the message under footer f. Ciphertext c is the encryption of p, and tag t authenti- one key and authenticate the resulting ciphertext under a sepa- cates h, c and f. -

Symmetric Key Cryptography PQCRYPTO Summer School on Post-Quantum Cryptography 2017
Symmetric Key Cryptography PQCRYPTO Summer School on Post-Quantum Cryptography 2017 Stefan Kölbl June 20th, 2017 DTU Compute, Technical University of Denmark Introduction to Symmetric Key Cryptography Symmetric Key Cryptography What can we do? • Encryption • Authentication (MAC) • Hashing • Random Number Generation • Digital Signature Schemes • Key Exchange 1 Authentication Authentication Message Authentication Code (MAC) Key Message MAC Tag • Produces a tag • Provide both authenticity and integrity • It should be hard to forge a valid tag. • Similar to hash but has a key • Similar to digital signature but same key 2 Authentication MAC Algorithm • Block Cipher Based (CBC-MAC) • Hash-based (HMAC, Sponge) • Universal Hashing (UMAC, Poly1305) 3 Authentication CBC-MAC M1 M2 Mi 0 EK EK EK T 4 Authentication Hash-based: • H(k jj m) • Okay with Sponge, fails with MD construction. • H(m jj k) • Collision on H allows to construct Tag collision. • HMAC: H(k ⊕ c1kj H(k ⊕ c2jjm)) 5 Authentication Universal Hashing (UMAC, Poly1305, …) • We need a universal hash function family H. • Parties share a secret member of H and key k. • Attacker does not know which one was chosen. Definition A set H of hash functions h : U ! N is universal iff 8x; y 2 U: 1 Pr (h(x) = h(y)) ≤ h2H jNj when h is chosen uniformly at random. 6 Authenticated Encryption In practice we always want Authenticated Encryption • Encryption does not protect against malicious alterations. • WEP [TWP07] • Plaintext recovery OpenSSH [APW09] • Recover TLS cookies [DR11] Problem Lot of things can go wrong when combining encryption and authentication. Note: This can allow to recover plaintext, forge messages.. -

Identifying Open Research Problems in Cryptography by Surveying Cryptographic Functions and Operations 1
International Journal of Grid and Distributed Computing Vol. 10, No. 11 (2017), pp.79-98 http://dx.doi.org/10.14257/ijgdc.2017.10.11.08 Identifying Open Research Problems in Cryptography by Surveying Cryptographic Functions and Operations 1 Rahul Saha1, G. Geetha2, Gulshan Kumar3 and Hye-Jim Kim4 1,3School of Computer Science and Engineering, Lovely Professional University, Punjab, India 2Division of Research and Development, Lovely Professional University, Punjab, India 4Business Administration Research Institute, Sungshin W. University, 2 Bomun-ro 34da gil, Seongbuk-gu, Seoul, Republic of Korea Abstract Cryptography has always been a core component of security domain. Different security services such as confidentiality, integrity, availability, authentication, non-repudiation and access control, are provided by a number of cryptographic algorithms including block ciphers, stream ciphers and hash functions. Though the algorithms are public and cryptographic strength depends on the usage of the keys, the ciphertext analysis using different functions and operations used in the algorithms can lead to the path of revealing a key completely or partially. It is hard to find any survey till date which identifies different operations and functions used in cryptography. In this paper, we have categorized our survey of cryptographic functions and operations in the algorithms in three categories: block ciphers, stream ciphers and cryptanalysis attacks which are executable in different parts of the algorithms. This survey will help the budding researchers in the society of crypto for identifying different operations and functions in cryptographic algorithms. Keywords: cryptography; block; stream; cipher; plaintext; ciphertext; functions; research problems 1. Introduction Cryptography [1] in the previous time was analogous to encryption where the main task was to convert the readable message to an unreadable format. -

Reducing the Impact of Dos Attacks on Endpoint IP Security
Reducing the Impact of DoS Attacks on Endpoint IP Security Joseph D. Touch and Yi-Hua Edward Yang USC/ISI [email protected] / [email protected] 1 Abstract some attack traffic. These results also indicate that this technique becomes more effective as the algorithm IP security is designed to protect hosts from attack, becomes more computationally intensive, and suggest but can itself provide a way to overwhelm the that such hierarchical intra-packet defenses are needed resources of a host. One such denial of service (DoS) to avoid IPsec being itself an opportunity for attack. attack involves sending incorrectly signed packets to a host, which then consumes substantial CPU resources 2. Background to reject unwanted traffic. This paper quantifies the impact of such attacks and explores preliminary ways Performance has been a significant issue for to reduce that impact. Measurements of the impact of Internet security since its inception and affects the DoS attack traffic on PC hosts indicate that a single IPsec suite both at the IKE (session establishment) and attacker can reduce throughput by 50%. This impact IPsec (packets in a session) level [10][11]. This paper can be reduced to 20% by layering low-effort nonce focuses on the IPsec level, i.e., protection for validation on IPsec’s CPU-intensive cryptographic established sessions. Previous performance analysis of algorithms, but the choice of algorithm does not have HMAC-MD5 (Hashed-MAC, where MAC means as large an effect. This work suggests that effective keyed Message Authentication Code), HMAC-SHA1, DoS resistance requires a hierarchical defense using and 3DES showed that the cost of the cryptographic both nonces and strong cryptography at the endpoints, algorithms dwarfs other IPsec overheads [6] [7] [15]. -

Implementation of Hash Function for Cryptography (Rsa Security)
International Journal For Technological Research In Engineering Volume 4, Issue 6, February-2017 ISSN (Online): 2347 - 4718 IMPLEMENTATION OF HASH FUNCTION FOR CRYPTOGRAPHY (RSA SECURITY) Syed Fateh Reza1, Mr. Prasun Das2 1M.Tech. (ECE), 2Assistant Professor (ECE), Bitm,Bolpur ABSTRACT: In this thesis, a new method for expected to have a unique hash code and it should be implementing cryptographic hash functions is proposed. generally difficult for an attacker to find two messages with This method seeks to improve the speed of the hash the same hash code. function particularly when a large set of messages with Mathematically, a hash function (H) is defined as follows: similar blocks such as documents with common Headers H: {0, 1}* → {0, 1}n are to be hashed. The method utilizes the peculiar run-time In this notation, {0, 1}* refers to the set of binary elements configurability Feature of FPGA. Essentially, when a block of any length including the empty string while {0, 1}n refers of message that is commonly hashed is identified, the hash to the set of binary elements of length n. Thus, the hash value is stored in memory so that in subsequent occurrences function maps a set of binary elements of arbitrary length to of The message block, the hash value does not need to be a set of binary elements of fixed length. Similarly, the recomputed; rather it is Simply retrieved from memory, thus properties of a hash function are defined as follows: giving a significant increase in speed. The System is self- x {0, 1}*; y {0,1}n learning and able to dynamically build on its knowledge of Pre-image resistance: given y= H(x), it should be difficult to frequently Occurring message blocks without intervention find x. -

All-Or-Nothing Encryption and the Package Transform
All-or-Nothing Encryption and the Package Transform Ronald L. Rivest MIT Laboratory for Computer Science 545 Technology Square, Cambridge, Mass. 02139 rivest@theory, ics.mit, edu Abstract. We present a new mode of encryption for block ciphers, which we call all-or-nothing encryption. This mode has the interesting defining property that one must decrypt the entire ciphertext before one can de- termine even one message block. This means that brute-force searches against all-or-nothing encryption are slowed down by a factor equal to the number of blocks in the ciphertext. We give a specific way of im- plementing all-or-nothing encryption using a "package transform" as a pre-processing step to an ordinary encryption mode. A package trans- form followed by ordinary codebook encryption also has the interest- ing property that it is very efficiently implemented in parallel. All-or- nothing encryption can also provide protection against chosen-plaintext and related-message attacks. 1 Introduction One way in which a cryptosystem may be attacked is by brute-force search: an adversary tries decrypting an intercepted ciphertext with all possible keys until the plaintext "makes sense" or until it matches a known target plaintext. Our primary motivation is to devise means to make brute-force search more difficult, by appropriately pre-processing a message before encrypting it. In this paper, we assume that the cipher under discussion is a block cipher with fixed-length input/output blocks, although our remarks generalize to other kinds of ciphers. An "encryption mode" is used to extend the encryption function to arbitrary length messages (see, for example, Schneier [9] and Biham [3]). -

The Key-Dependent Message Security of Key-Alternating Feistel Ciphers
The Key-Dependent Message Security of Key-Alternating Feistel Ciphers Pooya Farshim1, Louiza Khati2, Yannick Seurin2, and Damien Vergnaud3 1 University of York, Department of Computer Science, York, United Kingdom 2 ANSSI, Paris, France 3 Sorbonne Université, LIP6, Paris, France and Institut Universitaire de France Abstract. Key-Alternating Feistel (KAF) ciphers are a popular variant of Feistel ciphers whereby the round functions are defined as x 7→ F(ki ⊕x), where ki are the round keys and F is a public random function. Most Feistel ciphers, such as DES, indeed have such a structure. However, the security of this construction has only been studied in the classical CPA/CCA models. We provide the first security analysis of KAF ciphers in the key-dependent message (KDM) attack model, where plaintexts can be related to the private key. This model is motivated by cryptographic schemes used within application scenarios such as full-disk encryption or anonymous credential systems. We show that the four-round KAF cipher, with a single function F reused across the rounds, provides KDM security for a non-trivial set of KDM functions. To do so, we develop a generic proof methodology, based on the H-coefficient technique, that can ease the analysis of other block ciphers in such strong models of security. 1 Introduction The notion of key-dependent message (KDM) security for block ciphers was intro- duced by Black, Rogaway, and Shrimpton [5]. It guarantees strong confidentiality of communicated ciphertexts, i.e., the infeasibility of learning anything about plaintexts from the ciphertexts, even if an adversary has access to encryptions of messages that may depend on the secret key. -

Building Provably Secure Block Ciphers from Cryptographic Hash Functions
International Journal of Computer Applications (0975 - 8887) Volume 176 - No.16, April 2020 Building Provably Secure Block Ciphers from Cryptographic Hash Functions Charles F. de Barros Department of Computer Science Federal University of Sao˜ Joao˜ del Rei Minas Gerais, Brazil ABSTRACT The former must satisfy certain criteria, such as confusion and diffusion, while the latter should have properties like collision This paper presents a proposal for the construction of provably resistance. It can be said that these primitives are inherently secure block ciphers based on cryptographic hash functions. different, mainly because block ciphers are reversible (it is always The core idea consists of using a hash function to generate possible to decrypt an encrypted message, given the proper key), pseudorandom strings to be combined with the message blocks. while hash functions are, by design, irreversible. Each one of these strings depend on the previous ciphertext block Nevertheless, there is a certain similarity in the way block ciphers (or the initialization vector, in the case of the first message block), and hash functions are built. In fact, both are based on iterations: the secret key k and a block key derived from k. One of the block ciphers consist of iterations of a round function, while hash main features of the proposed construction is that it allows keys of algorithms are built upon iterations of a compression function. As arbitrary length, since the key itself is never directly combined with a matter of fact, it is possible to build hash functions from block the message. Furthermore, even if an adversary manages to guess ciphers, due to the fact that block ciphers are natural compression all of the block keys, he can’t efficiently retrieve the master secret functions, which makes them suitable to be used at the core of key or the message, provided that the underlying hash function the so-called Merkle-Damgard˚ [1] construction for cryptographic is cryptographically secure. -
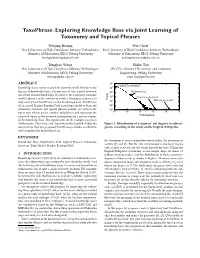
Taxophrase: Exploring Knowledge Base Via Joint Learning of Taxonomy and Topical Phrases
TaxoPhrase: Exploring Knowledge Base via Joint Learning of Taxonomy and Topical Phrases Weijing Huang Wei Chen∗ Key Laboratory of High Confidence Software Technologies Key Laboratory of High Confidence Software Technologies (Ministry of Education), EECS, Peking University (Ministry of Education), EECS, Peking University [email protected] [email protected] Tengjiao Wang Shibo Tao Key Laboratory of High Confidence Software Technologies SPCCTA, School of Electronics and Computer (Ministry of Education), EECS, Peking University Engineering, Peking University [email protected] [email protected] ABSTRACT 106 Politics_of_Morelos Knowledge bases restore many facts about the world. But due to the 105 big size of knowledge bases, it is not easy to take a quick overview 104 Mathematics onto their restored knowledge. In favor of the taxonomy structure 3 10 Musicians_by_band and the phrases in the content of entities, this paper proposes an Freq 2 Albums_by_artist exploratory tool TaxoPhrase on the knowledge base. TaxoPhrase 10 (1) is a novel Markov Random Field based topic model to learn the 101 taxonomy structure and topical phrases jointly; (2) extracts the 0 10 0 1 2 3 4 5 topics over subcategories, entities, and phrases, and represents the 10 10 10 10 10 10 extracted topics as the overview information for a given category Outdegree in the knowledge base. The experiments on the example categories Mathematics, Chemistry, and Argentina in the English Wikipedia Figure 1: Distribution of categories’ out degrees to subcate- demonstrate that our proposed TaxoPhrase provides an effective gories, according to the study on the English Wikipedia. tool to explore the knowledge base. KEYWORDS the taxonomy, it seems straightforward to utilize the taxonomy to Knowledge Base, Exploratory Tool, Topical Phrases, Taxonomy answer Q1 and Q2. -

Authenticated Ciphers D. J. Bernstein University of Illinois at Chicago
Authenticated ciphers D. J. Bernstein University of Illinois at Chicago Joint work with: Tanja Lange Technische Universiteit Eindhoven Advertisement: SHARCS 2012 (Special-Purpose Hardware for Attacking Cryptographic Systems) is right before FSE+SHA-3. 2012.01.23 deadline to submit extended abstracts. 2012.sharcs.org Multiple-year SHA-3 competition has produced a natural focus for security analysis and performance analysis. Community shares an interest in selecting best hash as SHA-3. Intensive analysis of candidates: hash conferences, hash workshops, active SHA-3 mailing list, etc. Would have been harder to absorb same work spread over more conferences, more time. Focus improves community's understanding and confidence. This is a familiar pattern. June 1998: AES block-cipher submissions from 50 people ) community focus. April 2005: eSTREAM stream- cipher submissions from 100 people ) community focus. October 2008: SHA-3 hash- function submissions from 200 people ) community focus. This is a familiar pattern. June 1998: AES block-cipher submissions from 50 people ) community focus. April 2005: eSTREAM stream- cipher submissions from 100 people ) community focus. October 2008: SHA-3 hash- function submissions from 200 people ) community focus. NESSIE was much less focused and ended up in more trouble: e.g., only two MAC submissions. The next community focus What's next after block ciphers, stream ciphers, hash functions? Proposal: authenticated ciphers. Basic security goal: two users start with a shared secret key; then want to protect messages against espionage and forgery. The usual competition: maximize security subject to performance constraints; i.e.: maximize performance subject to security constraints. \Isn't authenticated encryption done already?" \Isn't authenticated encryption done already?" FSE 2011 Krovetz{Rogaway cite EtM, RPC, IAPM, XCBC, OCB1, TAE, CCM, CWC, GCM, EAX, OCB2, CCFB, CHM, SIV, CIP, HBS, BTM; and propose OCB3.