Poirel CL D 2013.Pdf (3.645Mb)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Computational Approach for Defining a Signature of Β-Cell Golgi Stress in Diabetes Mellitus
Page 1 of 781 Diabetes A Computational Approach for Defining a Signature of β-Cell Golgi Stress in Diabetes Mellitus Robert N. Bone1,6,7, Olufunmilola Oyebamiji2, Sayali Talware2, Sharmila Selvaraj2, Preethi Krishnan3,6, Farooq Syed1,6,7, Huanmei Wu2, Carmella Evans-Molina 1,3,4,5,6,7,8* Departments of 1Pediatrics, 3Medicine, 4Anatomy, Cell Biology & Physiology, 5Biochemistry & Molecular Biology, the 6Center for Diabetes & Metabolic Diseases, and the 7Herman B. Wells Center for Pediatric Research, Indiana University School of Medicine, Indianapolis, IN 46202; 2Department of BioHealth Informatics, Indiana University-Purdue University Indianapolis, Indianapolis, IN, 46202; 8Roudebush VA Medical Center, Indianapolis, IN 46202. *Corresponding Author(s): Carmella Evans-Molina, MD, PhD ([email protected]) Indiana University School of Medicine, 635 Barnhill Drive, MS 2031A, Indianapolis, IN 46202, Telephone: (317) 274-4145, Fax (317) 274-4107 Running Title: Golgi Stress Response in Diabetes Word Count: 4358 Number of Figures: 6 Keywords: Golgi apparatus stress, Islets, β cell, Type 1 diabetes, Type 2 diabetes 1 Diabetes Publish Ahead of Print, published online August 20, 2020 Diabetes Page 2 of 781 ABSTRACT The Golgi apparatus (GA) is an important site of insulin processing and granule maturation, but whether GA organelle dysfunction and GA stress are present in the diabetic β-cell has not been tested. We utilized an informatics-based approach to develop a transcriptional signature of β-cell GA stress using existing RNA sequencing and microarray datasets generated using human islets from donors with diabetes and islets where type 1(T1D) and type 2 diabetes (T2D) had been modeled ex vivo. To narrow our results to GA-specific genes, we applied a filter set of 1,030 genes accepted as GA associated. -

Transcriptome Sequencing and Genome-Wide Association Analyses Reveal Lysosomal Function and Actin Cytoskeleton Remodeling in Schizophrenia and Bipolar Disorder
Molecular Psychiatry (2015) 20, 563–572 © 2015 Macmillan Publishers Limited All rights reserved 1359-4184/15 www.nature.com/mp ORIGINAL ARTICLE Transcriptome sequencing and genome-wide association analyses reveal lysosomal function and actin cytoskeleton remodeling in schizophrenia and bipolar disorder Z Zhao1,6,JXu2,6, J Chen3,6, S Kim4, M Reimers3, S-A Bacanu3,HYu1, C Liu5, J Sun1, Q Wang1, P Jia1,FXu2, Y Zhang2, KS Kendler3, Z Peng2 and X Chen3 Schizophrenia (SCZ) and bipolar disorder (BPD) are severe mental disorders with high heritability. Clinicians have long noticed the similarities of clinic symptoms between these disorders. In recent years, accumulating evidence indicates some shared genetic liabilities. However, what is shared remains elusive. In this study, we conducted whole transcriptome analysis of post-mortem brain tissues (cingulate cortex) from SCZ, BPD and control subjects, and identified differentially expressed genes in these disorders. We found 105 and 153 genes differentially expressed in SCZ and BPD, respectively. By comparing the t-test scores, we found that many of the genes differentially expressed in SCZ and BPD are concordant in their expression level (q ⩽ 0.01, 53 genes; q ⩽ 0.05, 213 genes; q ⩽ 0.1, 885 genes). Using genome-wide association data from the Psychiatric Genomics Consortium, we found that these differentially and concordantly expressed genes were enriched in association signals for both SCZ (Po10 − 7) and BPD (P = 0.029). To our knowledge, this is the first time that a substantially large number of genes show concordant expression and association for both SCZ and BPD. Pathway analyses of these genes indicated that they are involved in the lysosome, Fc gamma receptor-mediated phagocytosis, regulation of actin cytoskeleton pathways, along with several cancer pathways. -

CARBOPLATIN and PACLITAXEL a Dissertation SUBMITTED
PHARMACOGENOMICS OF CHEMOTHERAPEUTIC AGENTS: CARBOPLATIN AND PACLITAXEL A Dissertation SUBMITTED TO THE FACULTY OF UNIVERSITY OF MINNESOTA BY Taraswi Mitra Ghosh IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF DOCTOR OF PHILOSOPHY Dr. Jatinder K. Lamba May 2017 © Taraswi Mitra Ghosh, 2017 ACKNOWLEDGEMENTS At this special moment when I have reached the concluding stages of my Doctoral research and am ready to embark upon another voyage in my scientific career, I would like to take the opportunity to acknowledge the contributions of the people who have shaped up my life and career. First and foremost, I would like to thank Almighty God for giving me the strength to overcome all the challenges, for giving me the motivation to learn and to acquire knowledge. I would like to thank Dr. Jatinder Lamba, my adviser. I have learned a lot from her and am extremely thankful to her. She has helped me develop my scientific temper and inquisitive thinking. I would like to express my sincere gratitude towards my committee members. Dr. Mark Kirstein, my committee chair, has been a constant support. He has helped me develop my concepts in Pharmacokinetics. His insightful questions during our discussions have encouraged me to think deep and broaden my knowledge base. Dr. Angela Birnbaum, my committee member and DGS, has always been a strong support. Working with her was a very nice and cherishable experience for me. She has provided me the confidence to undertake independent projects- an experience which I am sure will be helpful in my future as a Scientist. I would like to thank Dr. -

Supplementary Figure Legends
1 Supplementary Figure legends 2 Supplementary Figure 1. 3 Experimental workflow. 4 5 Supplementary Figure 2. 6 IRF9 binding to promoters. 7 a) Verification of mIRF9 antibody by site-directed ChIP. IFNβ-stimulated binding of IRF9 to 8 the ISRE sequences of Mx2 was analyzed using BMDMs of WT and Irf9−/− (IRF9-/-) mice. 9 Cells were treated with 250 IU/ml of IFNβ for 1.5h. Data represent mean and SEM values of 10 three independent experiments. P-values were calculated using the paired ratio t-test (*P ≤ 11 0.05; **P ≤ 0.01, ***P ≤ 0.001). 12 b) Browser tracks showing complexes assigned as STAT-IRF9 in IFNγ treated wild type 13 BMDMs. Input, STAT2, IRF9 (scale 0-200). STAT1 (scale 0-150). 14 15 Supplementary Figure 3. 16 Experimental system for BioID. 17 a) Kinetics of STAT1, STAT2 and IRF9 synthesis in Raw 264.7 macrophages and wild type 18 BMDMs treated with 250 IU/ml as indicated. Whole-cell extracts were tested in western blot 19 for STAT1 phosphorylation at Y701 and of STAT2 at Y689 as well as total STAT1, STAT2, 20 IRF9 and GAPDH levels. The blots are representative of three independent experiments. b) 21 Irf9-/- mouse embryonic fibroblasts (MEFs) were transiently transfected with the indicated 22 expression vectors, including constitutively active IRF7-M15. One day after transfection, 23 RNA was isolated and Mx2 expression determined by qPCR. c) Myc-BirA*-IRF9 transgenic 24 Raw 264.7 were treated with increasing amounts of doxycycline (dox) (0,2µg/ml, 0,4µg/ml, 25 0,6µg/ml, 0,8µg/ml, 1mg/ml) and 50µM biotin. -

Supplementary Material Sumoylation Regulates the Chromatin
Supplementary material SUMOylation Regulates the Chromatin Occupancy and Anti-Proliferative Gene Programs of Glucocorticoid Receptor Ville Paakinaho, Sanna Kaikkonen, Harri Makkonen, Vladimir Benes, and Jorma J. Palvimo A FRT wtGR GR3KR clone wt-1 wt-2 wt-3 3KR-1 3KR-2 3KR-3 - - - - - - - dex + + + + + + + kDa a-GR - 100 a-GAPDH - 35 A549 + - - HEK293-wtGR - + - - - HEK293-GR3KR + kDa a-GR - 100 a-GAPDH - 35 B wtGR GR3KR 43°C - - + + - - + + dex - + - + - + - + kDa - 170 a-GR - 130 - 100 a-GAPDH - 35 - 170 a-SUMO-1 - 130 R - 100 G - a : P I a-SUMO-2/3 - 170 - 130 - 100 Figure S1. Expression and SUMOylation of GR in stable isogenic HEK293 cells. (A) Upper panel, immunoblot analysis of three HEK293 cell clones expressing either wtGR (wt-1-3) or GR3KR (3KR-1-3). The clones and background HEK293 (FRT) cells were exposed to vehicle or dex for 17 h, and cell samples were immunoblotting with anti-GR (Santa Cruz, sc-1003) and anti- GAPDH (Santa Cruz, sc-25778) antibodies. Lower panel, comparison of the GR level in A549 cells (from ATCC) with that of the selected clones from isogenic HEK293 cells (wt-3 and 3KR-3) by immunoblotting. (B) To analyse GR SUMOylation, wtGR- and GR3KR-expressing cells were grown with of without dex for 2 h and exposed for 30 min to 43°C. Immunoprecipitation (IP) with anti- GR antibody and immunoblotting with anti-SUMO-1 (Invitrogen, 33-2400) or anti-SUMO-2/3 (MBL M114-3) antibody were performed essentially as described (Rytinki et al. 2011, Methods Mol. Biol.). A total dex- sensitivity induced for dex expression ADARB1 -

Microrna Modulate Alveolar Epithelial Response to Cyclic Stretch
University of Pennsylvania ScholarlyCommons Departmental Papers (BE) Department of Bioengineering 2012 MicroRNA Modulate Alveolar Epithelial Response to Cyclic Stretch Nadir Yehya University of Pennsylvania, [email protected] Adi Yerrapureddy University of Pennsylvania John Tobias University of Pennsylvania, [email protected] Susan S. Margulies University of Pennsylvania, [email protected] Follow this and additional works at: https://repository.upenn.edu/be_papers Part of the Biomedical Engineering and Bioengineering Commons Recommended Citation Yehya, N., Yerrapureddy, A., Tobias, J., & Margulies, S. S. (2012). MicroRNA Modulate Alveolar Epithelial Response to Cyclic Stretch. BMC Genomics, 13 (154), http://dx.doi.org/10.1186/1471-2164-13-154 This paper is posted at ScholarlyCommons. https://repository.upenn.edu/be_papers/205 For more information, please contact [email protected]. MicroRNA Modulate Alveolar Epithelial Response to Cyclic Stretch Abstract Background MicroRNAs (miRNAs) are post-transcriptional regulators of gene expression implicated in multiple cellular processes. Cyclic stretch of alveoli is characteristic of mechanical ventilation, and is postulated to be partly responsible for the lung injury and inflammation in entilatv or-induced lung injury. We propose that miRNAs may regulate some of the stretch response, and therefore hypothesized that miRNAs would be differentially expressed between cyclically stretched and unstretched rat alveolar epithelial cells (RAECs). Results RAECs were isolated and cultured to express type I epithelial characteristics. They were then equibiaxially stretched to 25% change in surface area at 15 cycles/minute for 1 hour or 6 hours, or served as unstretched controls, and miRNAs were extracted. Expression profiling of the miRNAs with at least 1.5-fold change over controls revealed 42 miRNAs were regulated (34 up and 8 down) with stretch. -

Target Gene Gene Description Validation Diana Miranda
Supplemental Table S1. Mmu-miR-183-5p in silico predicted targets. TARGET GENE GENE DESCRIPTION VALIDATION DIANA MIRANDA MIRBRIDGE PICTAR PITA RNA22 TARGETSCAN TOTAL_HIT AP3M1 adaptor-related protein complex 3, mu 1 subunit V V V V V V V 7 BTG1 B-cell translocation gene 1, anti-proliferative V V V V V V V 7 CLCN3 chloride channel, voltage-sensitive 3 V V V V V V V 7 CTDSPL CTD (carboxy-terminal domain, RNA polymerase II, polypeptide A) small phosphatase-like V V V V V V V 7 DUSP10 dual specificity phosphatase 10 V V V V V V V 7 MAP3K4 mitogen-activated protein kinase kinase kinase 4 V V V V V V V 7 PDCD4 programmed cell death 4 (neoplastic transformation inhibitor) V V V V V V V 7 PPP2R5C protein phosphatase 2, regulatory subunit B', gamma V V V V V V V 7 PTPN4 protein tyrosine phosphatase, non-receptor type 4 (megakaryocyte) V V V V V V V 7 EZR ezrin V V V V V V 6 FOXO1 forkhead box O1 V V V V V V 6 ANKRD13C ankyrin repeat domain 13C V V V V V V 6 ARHGAP6 Rho GTPase activating protein 6 V V V V V V 6 BACH2 BTB and CNC homology 1, basic leucine zipper transcription factor 2 V V V V V V 6 BNIP3L BCL2/adenovirus E1B 19kDa interacting protein 3-like V V V V V V 6 BRMS1L breast cancer metastasis-suppressor 1-like V V V V V V 6 CDK5R1 cyclin-dependent kinase 5, regulatory subunit 1 (p35) V V V V V V 6 CTDSP1 CTD (carboxy-terminal domain, RNA polymerase II, polypeptide A) small phosphatase 1 V V V V V V 6 DCX doublecortin V V V V V V 6 ENAH enabled homolog (Drosophila) V V V V V V 6 EPHA4 EPH receptor A4 V V V V V V 6 FOXP1 forkhead box P1 V -

Integrated Transcriptomic, Phenotypic, and Functional Study Reveals Tissue-Specific Immune Properties of Mesenchymal Stromal
Integrated Transcriptomic, Phenotypic, and Functional Study Reveals Tissue-Specific Immune Properties of Mesenchymal Stromal Cells Cédric Ménard, Joelle Dulong, David Roulois, Benjamin Hebraud, Léa Verdière, Céline Pangault, Vonick Sibut, Isabelle Bezier, Nadège Bescher, Céline Monvoisin, et al. To cite this version: Cédric Ménard, Joelle Dulong, David Roulois, Benjamin Hebraud, Léa Verdière, et al.. Inte- grated Transcriptomic, Phenotypic, and Functional Study Reveals Tissue-Specific Immune Prop- erties of Mesenchymal Stromal Cells. STEM CELLS, AlphaMed Press, 2020, 38 (1), pp.146-159. 10.1002/stem.3077. hal-02282131 HAL Id: hal-02282131 https://hal-univ-rennes1.archives-ouvertes.fr/hal-02282131 Submitted on 10 Sep 2019 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Stem Cells Integrated transcriptomic, phenotypic, and functional study reveals tissue-specific immune properties of mesenchymal stromal cells Journal: Stem Cells Manuscript ID Draft Wiley - Manuscript Type: Original Research Date Submitted by Forthe Peer Review n/a Author: Complete -

TFIIE Alpha (GTF2E1) (NM 005513) Human Recombinant Protein Product Data
OriGene Technologies, Inc. 9620 Medical Center Drive, Ste 200 Rockville, MD 20850, US Phone: +1-888-267-4436 [email protected] EU: [email protected] CN: [email protected] Product datasheet for TP318763 TFIIE alpha (GTF2E1) (NM_005513) Human Recombinant Protein Product data: Product Type: Recombinant Proteins Description: Recombinant protein of human general transcription factor IIE, polypeptide 1, alpha 56kDa (GTF2E1) Species: Human Expression Host: HEK293T Tag: C-Myc/DDK Predicted MW: 49.3 kDa Concentration: >50 ug/mL as determined by microplate BCA method Purity: > 80% as determined by SDS-PAGE and Coomassie blue staining Buffer: 25 mM Tris.HCl, pH 7.3, 100 mM glycine, 10% glycerol Preparation: Recombinant protein was captured through anti-DDK affinity column followed by conventional chromatography steps. Storage: Store at -80°C. Stability: Stable for 12 months from the date of receipt of the product under proper storage and handling conditions. Avoid repeated freeze-thaw cycles. RefSeq: NP_005504 Locus ID: 2960 UniProt ID: P29083 RefSeq Size: 2969 Cytogenetics: 3q13.33 RefSeq ORF: 1317 Synonyms: FE; TF2E1; TFIIE-A Summary: Recruits TFIIH to the initiation complex and stimulates the RNA polymerase II C-terminal domain kinase and DNA-dependent ATPase activities of TFIIH. Both TFIIH and TFIIE are required for promoter clearance by RNA polymerase.[UniProtKB/Swiss-Prot Function] Protein Families: Transcription Factors Protein Pathways: Basal transcription factors This product is to be used for laboratory only. Not for diagnostic or therapeutic use. View online » ©2021 OriGene Technologies, Inc., 9620 Medical Center Drive, Ste 200, Rockville, MD 20850, US 1 / 2 TFIIE alpha (GTF2E1) (NM_005513) Human Recombinant Protein – TP318763 Product images: Coomassie blue staining of purified GTF2E1 protein (Cat# TP318763). -
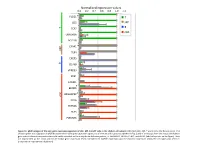
Normalized Expression Values *
Normalized expression values 0.0 0.2 0.4 0.6 0.8 1.0 1.2 PLCG1 * T CD5 MP T B TCF7 cDC UBASH3A BCL11B C5AR1 * MP TLR4 CXCR5 B CD79B VPREB3 XCR1 CADM1 BEND5 * ARGHAP22 * cDC CIITA ZBTB46 FLT3 PLEKHA5 Figure S1. qPCR analysis of the core gene expression signature of cDC, MP, B and T cells in the chicken cell suBsets. RNA from cDC, MP, T and B cells of 2 disUnct pools of 4 chicken spleen was subjected to qPCR detecUon of the core gene expression signatures of immune cell subsets established in Fig. 3 and of transcripts from the mouse and human gene subset selected compendia that could not be detected on the array due to defecUve probes, i.e. ARGHAP22, BEND5, C5AR1, and PLCG1 (labeled by a star on the figure). Data are represented as the mean and SD of relave gene expression levels normalized to GAPDH expression and the maximal expression across the cell types was set to 1 (independent experimental duplicates). B cell T cell cDC Monocyte/MP Chicken Human Mouse Figure S2. Unsupervised hierarchical clustering of orthologous immune response genes across chicken, human and mouse reveals globally conserved clusters of lymphoïd- specific and myeloïd- specific genes. Heatmap of cross-normalized expression profiles for immune response genes present on all three species arrays and regulated at least 2 folds across all cell suBsets, including chicken B cells (c_B), T cells (c_CD3), MP (c_MP) and cDC (c_cDC), human B cells (h_B), T cells (h_CD4_T and h_CD8_T), monocyte-derived MP (h_MoMP), peripheral blood mononucleated cell-derived MP (h_PBMC_MP), non-classical monocytes (h_non- classical_MO), classical monocytes (h_classical_MO), BDCA3+ cDC (h_BDCA3), BDCA1+ cDC (h_BDCA1), murine B cells (m_B), T cells (m_CD4_T and m_CD8_T), peritoneal cavity MP (m_PC_MPII-480HI), lung MP (m_LU_MP), non-classical monocytes (m_non-classical_MO), classical monocytes (m_classical_MO), splenic CD8α+ cDC (m_SP_DC1), suBcutaneous lymph node CD8α+ cDC (m_LN_DC1), splenic CD11B+ cDC (m_SP_DC2), suBcutaneous lymph node CD11B+ cDC (m_LN_DC2). -

Content Based Search in Gene Expression Databases and a Meta-Analysis of Host Responses to Infection
Content Based Search in Gene Expression Databases and a Meta-analysis of Host Responses to Infection A Thesis Submitted to the Faculty of Drexel University by Francis X. Bell in partial fulfillment of the requirements for the degree of Doctor of Philosophy November 2015 c Copyright 2015 Francis X. Bell. All Rights Reserved. ii Acknowledgments I would like to acknowledge and thank my advisor, Dr. Ahmet Sacan. Without his advice, support, and patience I would not have been able to accomplish all that I have. I would also like to thank my committee members and the Biomed Faculty that have guided me. I would like to give a special thanks for the members of the bioinformatics lab, in particular the members of the Sacan lab: Rehman Qureshi, Daisy Heng Yang, April Chunyu Zhao, and Yiqian Zhou. Thank you for creating a pleasant and friendly environment in the lab. I give the members of my family my sincerest gratitude for all that they have done for me. I cannot begin to repay my parents for their sacrifices. I am eternally grateful for everything they have done. The support of my sisters and their encouragement gave me the strength to persevere to the end. iii Table of Contents LIST OF TABLES.......................................................................... vii LIST OF FIGURES ........................................................................ xiv ABSTRACT ................................................................................ xvii 1. A BRIEF INTRODUCTION TO GENE EXPRESSION............................. 1 1.1 Central Dogma of Molecular Biology........................................... 1 1.1.1 Basic Transfers .......................................................... 1 1.1.2 Uncommon Transfers ................................................... 3 1.2 Gene Expression ................................................................. 4 1.2.1 Estimating Gene Expression ............................................ 4 1.2.2 DNA Microarrays ...................................................... -

Internal Checkpoint Regulates T Cell Neoantigen Reactivity and Susceptibility to PD1 Blockade
bioRxiv preprint doi: https://doi.org/10.1101/2020.09.24.306571; this version posted September 25, 2020. The copyright holder for this preprint (which was not certified by peer review) is the author/funder. All rights reserved. No reuse allowed without permission. Internal checkpoint regulates T cell neoantigen reactivity and susceptibility to PD1 blockade Douglas C. Palmer1*§, Beau R. Webber2,3,4*§, Yogin Patel1, Matthew J. Johnson2,3,4, Christine M. Kariya1, Walker S. Lahr2,3,4, Maria R. Parkhurst1, Jared J Gartner1, Todd D Prickett1, Frank J. Lowery1, Rigel J. Kishton1, Devikala Gurusamy1, Zulmarie Franco1, Suman K. Vodnala1, Miechaleen D. Diers2,3,4, Natalie K. Wolf2,3,4, Nicholas J. Slipek2,3,4, David H. McKenna5, Darin Sumstad6, Lydia Viney7, Tom Henley7, Tilmann Bürckstümmer7, Oliver Baker7, Ying Hu8, Chunhua Yan8, Daoud Meerzaman8, Kartik Padhan9, Winnie Lo1, Parisa Malekzadeh1, Li Jia1, Drew C. Deniger1, Shashank J. Patel1, Paul F. Robbins1, R. Scott McIvor1,10, Modassir Choudhry7, Steven A. Rosenberg1*§, Branden S. Moriarity2,3,4*§, Nicholas P. Restifo1*§ 1Surgery Branch, National Cancer Institute (NCI), National Institutes of Health, Bethesda, Maryland, USA. 2Department of Pediatrics, University of Minnesota, Minneapolis, MN, USA. 3Masonic Cancer Center, University of Minnesota, Minneapolis, MN, USA. 4Center for Genome Engineering, University of Minnesota, Minneapolis, MN, USA. 5Department of Laboratory Medicine and Pathology, University of Minnesota, Minneapolis, Minnesota, USA. 6Molecular and Cellular Therapeutics, University of Minnesota, Saint Paul, Minnesota, USA. 7Intima Bioscience, Inc. New York, NY, USA. 8The Center for Biomedical Informatics and Information Technology (CBIIT), National Institutes of Health, Bethesda, Maryland, USA, 9National Institute of Allergy and Infectious Disease (NIAID), National Institutes of Health, Bethesda, Maryland, USA.