Curriculum Vitae
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Shanlu › About › Cv › CV Shanlu.Pdf Shan Lu
Shan Lu University of Chicago, Dept. of Computer Science Phone: +1-773-702-3184 5730 S. Ellis Ave., Rm 343 E-mail: [email protected] Chicago, IL 60637 USA Homepage: http://people.cs.uchicago.edu/~shanlu RESEARCH INTERESTS Tool support for improving the correctness and efficiency of large scale software systems EMPLOYMENT 2019 – present Professor, Dept. of Computer Science, University of Chicago 2014 – 2019 Associate Professor, Dept. of Computer Sciences, University of Chicago 2009 – 2014 Assistant Professor, Dept. of Computer Sciences, University of Wisconsin – Madison EDUCATION 2008 University of Illinois at Urbana-Champaign, Urbana, IL Ph.D. in Computer Science Thesis: Understanding, Detecting, and Exposing Concurrency Bugs (Advisor: Prof. Yuanyuan Zhou) 2003 University of Science & Technology of China, Hefei, China B.S. in Computer Science HONORS AND AWARDS 2019 ACM Distinguished Member Among 62 members world-wide recognized for outstanding contributions to the computing field 2015 Google Faculty Research Award 2014 Alfred P. Sloan Research Fellow Among 126 “early-career scholars (who) represent the most promising scientific researchers working today” 2013 Distinguished Alumni Educator Award Among 3 awardees selected by Department of Computer Science, University of Illinois 2010 NSF Career Award 2021 Honorable Mention Award @ CHI for paper [C71] (CHI 2021) 2019 Best Paper Award @ SOSP for paper [C62] (SOSP 2019) 2019 ACM SIGSOFT Distinguished Paper Award @ ICSE for paper [C58] (ICSE 2019) 2017 Google Scholar Classic Paper Award for -
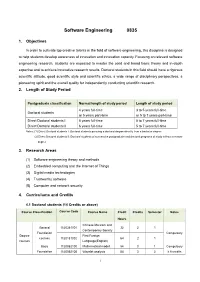
Software Engineering 0835
Software Engineering 0835 1. Objectives In order to cultivate top creative talents in the field of software engineering, this discipline is designed to help students develop awareness of innovation and innovation capacity. Focusing on relevant software engineering research, students are expected to master the solid and broad basic theory and in-depth expertise and to achieve innovative research results. Doctoral students in this field should have a rigorous scientific attitude, good scientific style and scientific ethics, a wide range of disciplinary perspectives, a pioneering spirit and the overall quality for independently conducting scientific research. 2. Length of Study Period Postgraduate classification Normal length of study period Length of study period 4 years full-time 3 to 5 years full-time Doctoral students or 5 years part-time or 5 to 7 years part-time Direct Doctoral students I 5 years full-time 5 to 7 years full-time Direct Doctoral students II 6 years full-time 5 to 7 years full-time Notes: (1) Direct Doctoral students I: Doctoral students pursuing a doctoral degree directly from a bachelor degree (2) Direct Doctoral students II: Doctoral students of successive postgraduate and doctoral programs of study without a master degree 3. Research Areas (1) Software engineering theory and methods (2) Embedded computing and the Internet of Things (3) Digital media technologies (4) Trustworthy software (5) Computer and network security 4. Curriculums and Credits 4.1 Doctoral students (14 Credits or above) Course Classification Course -
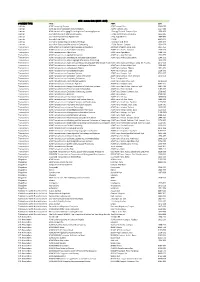
A ACM Transactions on Trans. 1553 TITLE ABBR ISSN ACM Computing Surveys ACM Comput. Surv. 0360‐0300 ACM Journal
ACM - zoznam titulov (2016 - 2019) CONTENT TYPE TITLE ABBR ISSN Journals ACM Computing Surveys ACM Comput. Surv. 0360‐0300 Journals ACM Journal of Computer Documentation ACM J. Comput. Doc. 1527‐6805 Journals ACM Journal on Emerging Technologies in Computing Systems J. Emerg. Technol. Comput. Syst. 1550‐4832 Journals Journal of Data and Information Quality J. Data and Information Quality 1936‐1955 Journals Journal of Experimental Algorithmics J. Exp. Algorithmics 1084‐6654 Journals Journal of the ACM J. ACM 0004‐5411 Journals Journal on Computing and Cultural Heritage J. Comput. Cult. Herit. 1556‐4673 Journals Journal on Educational Resources in Computing J. Educ. Resour. Comput. 1531‐4278 Transactions ACM Letters on Programming Languages and Systems ACM Lett. Program. Lang. Syst. 1057‐4514 Transactions ACM Transactions on Accessible Computing ACM Trans. Access. Comput. 1936‐7228 Transactions ACM Transactions on Algorithms ACM Trans. Algorithms 1549‐6325 Transactions ACM Transactions on Applied Perception ACM Trans. Appl. Percept. 1544‐3558 Transactions ACM Transactions on Architecture and Code Optimization ACM Trans. Archit. Code Optim. 1544‐3566 Transactions ACM Transactions on Asian Language Information Processing 1530‐0226 Transactions ACM Transactions on Asian and Low‐Resource Language Information Proce ACM Trans. Asian Low‐Resour. Lang. Inf. Process. 2375‐4699 Transactions ACM Transactions on Autonomous and Adaptive Systems ACM Trans. Auton. Adapt. Syst. 1556‐4665 Transactions ACM Transactions on Computation Theory ACM Trans. Comput. Theory 1942‐3454 Transactions ACM Transactions on Computational Logic ACM Trans. Comput. Logic 1529‐3785 Transactions ACM Transactions on Computer Systems ACM Trans. Comput. Syst. 0734‐2071 Transactions ACM Transactions on Computer‐Human Interaction ACM Trans. -

Thomas E. Anderson
Thomas E. Anderson November 2015 Personal Born in Orlando, Florida, August 28, 1961. Work Address: Home Address: 646 Allen Center 1201 18th Ave. E. Department of Computer Science and Engineering Seattle, WA 98112 University of Washington (206) 568{0230 Seattle, WA 98112 (206) 543-9348 [email protected] Research Operating systems, cloud computing, computer networks, computer security, local and Interests wide area distributed systems, high performance computer and router architectures, and education software, with a focus on the construction of robust, secure, and efficient computer systems. Education Ph.D. in Computer Science, 1991, University of Washington. Dissertation Title: Operating System Support for High Performance Multiprocessing, supervised by Profs. E.D. Lazowska and H.M. Levy. M.S. in Computer Science, 1989, University of Washington. A.B. cum laude in Philosophy, 1983, Harvard University. Professional Department of Computer Science and Engineering, University of Washington. Experience Warren Francis and Wilma Kolm Bradley Chair of Computer Science and Engineering, 2009 { present. Visiting Professor, Eidgenossische Technische Hoschschule Zurich (ETHZ), 2009. Department of Computer Science and Engineering, University of Washington. Professor, 2001 { 2009. Department of Computer Science and Engineering, University of Washington. Associate Professor, 1997 { 2001. Founder and Interim CEO/CTO, Asta Networks, 2000 - 2001 (on leave from UW). Computer Science Division, University of California, Berkeley. Associate Professor, 1996 { 1997. Computer Science Division, University of California, Berkeley. Assistant Professor, 1991 { 1996. Digital Equipment Corporation Systems Research Center. Research Intern, Fall, 1990. Thomas E. Anderson - 2 - November 2015 Awards USENIX Lifetime Achievement Award, 2014. USENIX Software Tools User Group Award (for PlanetLab), 2014. IEEE Koji Kobayashi Computers and Communications Award, 2012. -
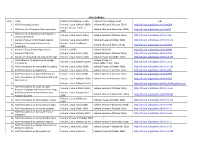
ACM JOURNALS S.No. TITLE PUBLICATION RANGE :STARTS PUBLICATION RANGE: LATEST URL 1. ACM Computing Surveys Volume 1 Issue 1
ACM JOURNALS S.No. TITLE PUBLICATION RANGE :STARTS PUBLICATION RANGE: LATEST URL 1. ACM Computing Surveys Volume 1 Issue 1 (March 1969) Volume 49 Issue 3 (October 2016) http://dl.acm.org/citation.cfm?id=J204 Volume 24 Issue 1 (Feb. 1, 2. ACM Journal of Computer Documentation Volume 26 Issue 4 (November 2002) http://dl.acm.org/citation.cfm?id=J24 2000) ACM Journal on Emerging Technologies in 3. Volume 1 Issue 1 (April 2005) Volume 13 Issue 2 (October 2016) http://dl.acm.org/citation.cfm?id=J967 Computing Systems 4. Journal of Data and Information Quality Volume 1 Issue 1 (June 2009) Volume 8 Issue 1 (October 2016) http://dl.acm.org/citation.cfm?id=J1191 Journal on Educational Resources in Volume 1 Issue 1es (March 5. Volume 16 Issue 2 (March 2016) http://dl.acm.org/citation.cfm?id=J814 Computing 2001) 6. Journal of Experimental Algorithmics Volume 1 (1996) Volume 21 (2016) http://dl.acm.org/citation.cfm?id=J430 7. Journal of the ACM Volume 1 Issue 1 (Jan. 1954) Volume 63 Issue 4 (October 2016) http://dl.acm.org/citation.cfm?id=J401 8. Journal on Computing and Cultural Heritage Volume 1 Issue 1 (June 2008) Volume 9 Issue 3 (October 2016) http://dl.acm.org/citation.cfm?id=J1157 ACM Letters on Programming Languages Volume 2 Issue 1-4 9. Volume 1 Issue 1 (March 1992) http://dl.acm.org/citation.cfm?id=J513 and Systems (March–Dec. 1993) 10. ACM Transactions on Accessible Computing Volume 1 Issue 1 (May 2008) Volume 9 Issue 1 (October 2016) http://dl.acm.org/citation.cfm?id=J1156 11. -

Ece Connections
ECE2019/2020 CONNECTIONS BUILDING THE NEW COMPUTER USING REVOLUTIONARY NEW ARCHITECTURES Page 16 ECE CONNECTIONS DIRECTOR’S REFLECTIONS: ALYSSA APSEL Wishna Robyn s I write this, our Cornell scaling alone isn’t the answer to more community is adapting powerful and more efficient computers. to the rapidly evolving We can build chips with upwards of four conditions resulting from billion transistors in a square centimeter the COVID-19 pandemic. (such as Apple’s A11 chip), but when My heart is heavy with attempting to make devices any smaller the distress, uncertainty and anxiety this the electrical properties become difficult to Abrings for so many of us, and in particular control. Pushing them faster also bumps seniors who were looking forward to their up against thermal issues as the predicted last semesters at Cornell. temperatures on-chip become comparable I recognize that these are difficult to that of a rocket nozzle. times and many uncertainties remain, Does that mean the end of innovation very nature of computation by building but I sincerely believe that by working in electronics? No, it’s just the beginning. memory devices, algorithms, circuits, and together as a community, we will achieve Instead of investing in manufacturing devices that directly integrate computation the best possible results for the health and that matches the pace of Moore’s law, even at the cellular level. The work well-being of all of Cornell. Although we major manufacturers have realized highlighted in this issue is exciting in that are distant from each other, our work in that it is cost effective to pursue other it breaks the traditional separation between ECE continues. -

FCRC 2011 June 4 - 11, San Jose, CA TIMELINE SCHEDULE
FCRC 2011 June 4 - 11, San Jose, CA TIMELINE SCHEDULE Sponsored by Corporate Support Provided by Gold Silver CONFERENCE/WORKSHOP/EVENT ACRONYMS & DATES Dates Full Name Dates Full Name 3DAPAS 8 A Workshop on Dynamic Distrib. Data-Intensive Applications, Programming Abstractions, & Systs (HPDC) IWQoS 6--7 Int. Workshop on Quality of Service (ACM SIGMETRICS and IEEE Communications Society) A4MMC 4 Applications fo Multi and Many Core Processors: Analysis, Implementation, and Performance (ISCA) LSAP 8 P Workshop on Large-Scale System and Application Performance (HPDC) AdAuct 5 Ad Auction Workshop (EC) MAMA 8 Workshop on Mathematical Performance Modeling and Analysis (METRICS) AMAS-BT 4 P Workship on Architectural and Microarchitectural Support for Binary Translation (ISCA) METRICS 7--11 ACM SIGMETRICS International Conference on Measurement and Modeling of Computer Systems BMD 5 Workshop on Bayesian Mechanism Design (EC) MoBS 5 A Workshop on Modeling, Benchmarking, and Simulation (ISCA) CARD 5 P Workshop on Computer Architecture Research Directions (ISCA) MRA 8 Int. Workshop on MapReduce and its Applications (HPDC) CBP 4 P JILP Workshop on Computer Architecture Competitions: Championship Branch Prediction (ISCA) MSPC 5 Memory Systems Performance and Correctness (PLDI) Complex 8--10 IEEE Conference on Computational Complexity (IEEE TCMFC) NDCA 5 A New Directions in Computer Architecture (ISCA) CRA-W 4--5 CRA-W Career Mentoring Workshop NetEcon 6 Workshop on the Economics of Networks, Systems, and Computation (EC) DIDC 8 P Int. Workshop on Data-Intensive Distributed Computing (HPDC) PLAS 5 Programming Languages and Analysis for Security Workshop (PLDI) EAMA 4 Workshop on Emerging Applications and Manycore Architectures (ISCA) PLDI 4--8 ACM SIGPLAN Conference on Programming Language Design and Implementation EC 5--9 ACM Conference on Electronic Commerce (ACM SIGECOM) PODC 6--8 ACM SIGACT-SIGOPT Symp. -

March 2, 2020 Remzi Arpaci-Dusseau Professor And
March 2, 2020 Remzi Arpaci-Dusseau Professor and Department Chair UW-Madison Computer Sciences With CC to Lance Potter for Department Files Dear Remzi: I write to formally request emeritus status upon my retirement from the University of Wisconsin-Madison this summer with my last day on the payroll being August 16, 2020. I started at Wisconsin on January 1, 1988. I believe that my 100000.1two years (32.5ten years) have been to both UW’s and my benefit. I feel blessed by my time at this great university. When I started, the following were non-existent or in niche use: world-wide web, laptops, broadband, and smartphones. Universities had no general email, course web pages, or social media presence. Companies like Amazon, Facebook, and Google could not exist. It has been a privilege to witness and modestly contribute to the last three decades of change by advancing computer hardware as the platform for information technology wizardry. On the next page to explain my research, I include the press release from my 2019 ACM - IEEE CS Eckert-Mauchly Award for seminal contributions to the fields of cache memories, memory consistency models, transactional memory, and simulation. It is the highest award in computer architecture and hardware and represents a lifetime of achievement. Note that “memory” refers to computer memory. On the final two pages, I summarize some of my UW accomplishments in the third person. Sincerely, Mark D. Hill John P. Morgridge Professor Gene M. Amdahl Professor of Computer Sciences Professor of Electrical and Computer Engineering (by courtesy) Chair of Computing Community Consortium (CCC) ACM Fellow & Fellow of the IEEE Eckert-Mauchly Award, 2019 CV: http://www.cs.wisc.edu/~markhill/markhill_cv.pdf Prof. -

PERMDNN: Efficient Compressed DNN Architecture with Permuted
PERMDNN: Efficient Compressed DNN Architecture with Permuted Diagonal Matrices Chunhua Deng∗+ Siyu Liao∗+ Yi Xie+ City University of New York City University of New York City University of New York [email protected] [email protected] [email protected] Keshab K. Parhi Xuehai Qian Bo Yuan+ University of Minnesota, Twin Cities University of Southern California City University of New York [email protected] [email protected] [email protected] Abstract—Deep neural network (DNN) has emerged as the demand intelligence, such as speech recognition [3], object most important and popular artificial intelligent (AI) technique. recognition [4], natural language processing [5] etc. The growth of model size poses a key energy efficiency challenge The extraordinary performance of DNNs with respect to for the underlying computing platform. Thus, model compression becomes a crucial problem. However, the current approaches are high accuracy is mainly attributed to their very large model limited by various drawbacks. Specifically, network sparsification sizes [6]–[8]. As indicated in a number of theoretical anal- approach suffers from irregularity, heuristic nature and large ysis [9] [10] and empirical simulations [11]–[13], scaling indexing overhead. On the other hand, the recent structured up the model sizes can improve the overall learning and matrix-based approach (i.e., CIRCNN) is limited by the rela- representation capability of the DNN models, leading to higher tively complex arithmetic computation (i.e., FFT), less flexible compression ratio, and its inability to fully utilize input sparsity. classification/predication accuracy than the smaller models. To address these drawbacks, this paper proposes PERMDNN, Motivated by these encouraging findings, the state-of-the-art a novel approach to generate and execute hardware-friendly DNNs continue to scale up with the purpose of tackling more structured sparse DNN models using permuted diagonal ma- complicated tasks with higher accuracy. -

ASPLOS XX Twentieth International Conference on Architectural Support for Programming Languages and Operating Systems
ASPLOS XX Twentieth International Conference on Architectural Support for Programming Languages and Operating Systems March 14–18, 2015 Istanbul, Turkey Sponsored by: ACM SIGARCH ACM SIGOPS ACM SIGPLAN In co-operation with: ACM SIGBED With Support from: Bilkent University, NSF, VMware, Intel, Google, ARM, Oracle, Microsoft Research, Facebook, IBM Research, and HP Labs The Association for Computing Machinery 2 Penn Plaza, Suite 701 New York, New York 10121-0701 Copyright © 2015 by the Association for Computing Machinery, Inc. (ACM). Permission to make digital or hard copies of portions of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. Copyright for components of this work owned by others than ACM must be honored. Abstracting with credit is permitted. To copy otherwise, to republish, to post on servers or to redistribute to lists, requires prior specific permission and/or a fee. Request permission to republish from: [email protected] or Fax +1 (212) 869-0481. For other copying of articles that carry a code at the bottom of the first or last page, copying is permitted provided that the per-copy fee indicated in the code is paid through www.copyright.com. Notice to Past Authors of ACM-Published Articles ACM intends to create a complete electronic archive of all articles and/or other material previously published by ACM. If you have written a work that has been previously published by ACM in any journal or conference proceedings prior to 1978, or any SIG Newsletter at any time, and you do NOT want this work to appear in the ACM Digital Library, please inform [email protected], stating the title of the work, the author(s), and where and when published. -

Summer/Fall 2015 Newsletter
INCREASING THE SUCCESS & PARTICIPATION OF WOMEN IN COMPUTING RESEARCH CRA-WomenSummer/Fall 2015 Edition NEWSLETTER This Issue: P2 Interview with Dilma Da Silva Highlight on Alum P5 Attend the Inaugural Virtual Undergraduate Sarah Ita Levitan Town Hall! Sarah Ita Levitan is a 3rd year PhD student in the Department of Computer Science at Columbia University. She is a member P7 Nomination Opportunities of the Spoken Language Processing group directed by Dr. Julia Hirschberg. Her research involves identifying spoken cues to deception and examining cultural and gender differences in P8 Alum News communicating and perceiving lies. She received her bachelor’s degree in computer science from Brooklyn College (CUNY). Before her P11-13 Awards senior year, she participated in the Distributed Research Experience for Undergraduates (DREU), studying acoustic and prosodic P14 News of Affiliated Groups entrainment in Supreme Court oral arguments. Sarah Ita is currently funded through an NSF-GRFP fellowship and is an IGERT fellow. continued on page 6 P14 Upcoming Events and Deadlines Natalie Enright Jerger wins Editors: Carla Ellis, Duke University Borg Early Career Award Amanda Stent, Yahoo Labs CRA-Women proudly announces Natalie Enright Jerger as this year’s BECA winner. Natalie is an associate professor in the Department of Electrical and Computer Engineering at the University of Toronto. Her research interests include multi- and many-core computer architectures, on-chip networks, cache coherence protocols, memory systems and approximate computing. Natalie is passionate about mentoring students and is deeply committed to increasing the participation of women in computer science and engineering. Natalie’s contributions to research have been recognized with several awards including the Ontario Ministry of Research and Innovation Early Researcher Award (2012), the Ontario Professional Engineers Young Engineer Medal (2014) and an Alfred P. -

Computing Research Association Annual Report FY 2013-2014
FY 2013-2014 ANNUAL REPORT Computing Research Association Annual Report FY 2013-2014 UNITING INDUSTRY, ACADEMIA AND GOVERNMENT TO ADVANCE COMPUTING RESEARCH AND CHANGE THE WORLD 1 FY 2013-2014 ANNUAL REPORT TaBLE OF CONTENTS Message From the Board Chair 3 Financial Statement 6 Highlights by Mission Area Leadership 7 Policy 11 Talent Development 13 CRA Members 24 Board of Directors 28 Staff 29 Committees and Joint Activities 30 OUR MISSION The mission of the Computing Research Association (CRA) is to enhance innovation by joining with industry, government and academia to strengthen research and advanced education in computing. CRA executes this mission by leading the computing research community, informing policymakers and the public, and facilitating the development of strong, diverse talent in the field. Founded in 1972, CRA’s membership includes more than 200 North American organizations active in computing research: academic departments of computer science and computer engineering, laboratories and centers (industry, government, and academia), and affiliated professional societies (AAAI, ACM, CACS/AIC, IEEE Computer Society, SIAM, and USENIX). Computing Research Association 1828 L St, NW, Suite 800 Washington, DC 20036 P: 202-234-2111 F: 202-667-1066 E: [email protected] W: www.cra.org 2 FY 2013-2014 ANNUAL REPORT MESSAGE FROM THE BOARD CHAIR I am delighted to report that 2013-14 was another very successful year for CRA’s efforts to strengthen research and advanced education in computing -- we have made substantial progress in our programs while ending the year on a positive financial note. The following report gives an excellent overview of CRA’s initiatives and activities in our three mission areas of leadership, talent development and policy during FY 2013-14.