FCRC 2011 June 4 - 11, San Jose, CA TIMELINE SCHEDULE
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Phillip B. Gibbons Curriculum Vitae
Phillip B. Gibbons Curriculum Vitae [email protected] http://cs.cmu.edu/~gibbons/ July 2020 Research Interests Research areas include big data, parallel computing, databases, cloud computing, sensor networks, distributed systems, and computer architecture. My publications span theory and systems, across a broad range of computer science and engineering (e.g., conference papers in APoCS, ATC, ESA, EuroSys, HPCA, ICML, IPDPS, ISCA, MICRO, NeurIPS, NSDI, OSDI, PACT, SoCC, SODA, SOSP, SPAA and VLDB since 2015). Education • University of California at Berkeley, Berkeley, California, 1984{1989. Ph.D. in Computer Science. Dissertation advisor: Richard M. Karp. • Dartmouth College, Hanover, New Hampshire, 1979{1983. B.A. in Mathematics. Graduated summa cum laude and Phi Beta Kappa. Professional Experience • Carnegie Mellon University, Pittsburgh, Pennsylvania. Professor, Computer Science Department, 2015{present. Professor, Electrical and Computer Engineering Department, 2015{present. Principal Investigator (PI or co-PI) for the following research projects: { Prescriptive Memory: Razing the semantic wall between applications and computer systems with heterogeneous compute and memories. { Asymmetric Memory: Write-efficient algorithms and systems, for settings (such as emerging non- volatile memories) where writes are significantly more costly than reads. { Big Learning Systems: Mapping out and exploring the space of large-scale machine learning from a systems' perspective. Recent focus on geo-distributed learning over non-IID data. Adjunct Professor, Computer Science Department, 2003{2015. Adjunct Associate Professor, Computer Science Department, 2000{2003. Visiting Professor, Computer Science Department, 2000. • Intel Labs Pittsburgh, Pittsburgh, Pennsylvania. Principal Research Scientist, 2001{2015. Principal Investigator for the Intel Science and Technology Center for Cloud Computing { A $11.5M research partnership with Carnegie Mellon, Georgia Tech, Princeton, UC Berkeley, and U. -

Polynomial Transformations of Tschirnhaus, Bring and Jerrard
ACM SIGSAM Bulletin, Vol 37, No. 3, September 2003 Polynomial Transformations of Tschirnhaus, Bring and Jerrard Victor S. Adamchik Department of Computer Science, Carnegie Mellon University, Pittsburgh, PA, USA [email protected] David J. Jeffrey Department of Applied Mathematics, The University of Western Ontario, London, Ontario, Canada [email protected] Abstract Tschirnhaus gave transformations for the elimination of some of the intermediate terms in a polynomial. His transformations were developed further by Bring and Jerrard, and here we describe all these transformations in modern notation. We also discuss their possible utility for polynomial solving, particularly with respect to the Mathematica poster on the solution of the quintic. 1 Introduction A recent issue of the BULLETIN contained a translation of the 1683 paper by Tschirnhaus [10], in which he proposed a method for solving a polynomial equation Pn(x) of degree n by transforming it into a polynomial Qn(y) which has a simpler form (meaning that it has fewer terms). Specifically, he extended the idea (which he attributed to Decartes) in which a polynomial of degree n is reduced or depressed (lovely word!) by removing its term in degree n ¡ 1. Tschirnhaus’s transformation is a polynomial substitution y = Tk(x), in which the degree of the transformation k < n can be selected. Tschirnhaus demonstrated the utility of his transformation by apparently solving the cubic equation in a way different from Cardano. Although Tschirnhaus’s work is described in modern books [9], later works by Bring [2, 3] and Jerrard [7, 6] have been largely forgotten. Here, we present the transformations in modern notation and make some comments on their utility. -

SIGOPS Annual Report 2011
SIGOPS Annual Report 2011 Fiscal Year July 2010-June 2011 Submitted by Doug Terry, SIGOPS Chair Overview SIGOPS is a vibrant community of people with interests in “operating systems” in the broadest sense, including topics such as distributed computing, storage systems, security, concurrency, middleware, mobility, virtualization, networking, cloud computing, datacenter software, and Internet services. We sponsor a number of top conferences, provide travel grants to students, present yearly awards, disseminate information to members electronically, and collaborate with other SIGs on important programs for computing professionals. Notable activities from the past year include: Elections were held for new officers, and Jeanna Matthews was elected as the new SIGOPS Chair, George Candea as Vice Chair, and Dilma da Silva as Treasurer. They will serve two-year terms from July 1, 2011 through June 30, 2013. The past officers (Doug Terry as Chair, Frank Bellosa as Vice Chair and Jeanna Matthews as Treasurer) completed their 4 years of service on June 30. Planning for the next ACM Symposium on Operating Systems (SOSP), which is scheduled for October 2011 in Cascais, Portugal, has been largely completed by Ted Wobber, the General Chair, and Peter Druschel, the Program Chair. The Second ACM Symposium on Cloud Computing (SOCC), which is co-sponsored between SIGOPS and SIGMOD, is being co-located with SOSP in Portugal. The first SIGOPS Asia-Pacific Workshop on Systems (APSys) was held on August 30, 2010 in New Delhi, India, immediately before the SIGCOMM 2010 conference. And the second instance of this workshop is being held in Shanghai, China, in July 2011. ACM released the first version of the Cloud Computing Tech Pack, which was produced by Doug Terry, the SIGOPS Chair. -

Curriculum Vitae
Massachusetts Institute of Technology School of Engineering Faculty Personnel Record Date: April 1, 2020 Full Name: Charles E. Leiserson Department: Electrical Engineering and Computer Science 1. Date of Birth November 10, 1953 2. Citizenship U.S.A. 3. Education School Degree Date Yale University B. S. (cum laude) May 1975 Carnegie-Mellon University Ph.D. Dec. 1981 4. Title of Thesis for Most Advanced Degree Area-Efficient VLSI Computation 5. Principal Fields of Interest Analysis of algorithms Caching Compilers and runtime systems Computer chess Computer-aided design Computer network architecture Digital hardware and computing machinery Distance education and interaction Fast artificial intelligence Leadership skills for engineering and science faculty Multicore computing Parallel algorithms, architectures, and languages Parallel and distributed computing Performance engineering Scalable computing systems Software performance engineering Supercomputing Theoretical computer science MIT School of Engineering Faculty Personnel Record — Charles E. Leiserson 2 6. Non-MIT Experience Position Date Founder, Chairman of the Board, and Chief Technology Officer, Cilk Arts, 2006 – 2009 Burlington, Massachusetts Director of System Architecture, Akamai Technologies, Cambridge, 1999 – 2001 Massachusetts Shaw Visiting Professor, National University of Singapore, Republic of 1995 – 1996 Singapore Network Architect for Connection Machine Model CM-5 Supercomputer, 1989 – 1990 Thinking Machines Programmer, Computervision Corporation, Bedford, Massachusetts 1975 -

SIGLOG: Special Interest Group on Logic and Computation a Proposal
SIGLOG: Special Interest Group on Logic and Computation A Proposal Natarajan Shankar Computer Science Laboratory SRI International Menlo Park, CA Mar 21, 2014 SIGLOG: Executive Summary Logic is, and will continue to be, a central topic in computing. ACM has a core constituency with an interest in Logic and Computation (L&C), witnessed by 1 The many Turing Awards for work centrally in L&C 2 The ACM journal Transactions on Computational Logic 3 Several long-running conferences like LICS, CADE, CAV, ICLP, RTA, CSL, TACAS, and MFPS, and super-conferences like FLoC and ETAPS SIGLOG explores the connections between logic and computing covering theory, semantics, analysis, and synthesis. SIGLOG delivers value to its membership through the coordination of conferences, journals, newsletters, awards, and educational programs. SIGLOG enjoys significant synergies with several existing SIGs. Natarajan Shankar SIGLOG 2/9 Logic and Computation: Early Foundations Logicians like Alonzo Church, Kurt G¨odel, Alan Turing, John von Neumann, and Stephen Kleene have played a pioneering role in laying the foundation of computing. In the last 65 years, logic has become the calculus of computing underpinning the foundations of many diverse sub-fields. Natarajan Shankar SIGLOG 3/9 Logic and Computation: Turing Awardees Turing awardees for logic-related work include John McCarthy, Edsger Dijkstra, Dana Scott Michael Rabin, Tony Hoare Steve Cook, Robin Milner Amir Pnueli, Ed Clarke Allen Emerson Joseph Sifakis Leslie Lamport Natarajan Shankar SIGLOG 4/9 Interaction between SIGLOG and other SIGs Logic interacts in a significant way with AI (SIGAI), theory of computation (SIGACT), databases (SIGMOD) and knowledge bases (SIGKDD), programming languages (SIGPLAN), software engineering (SIGSOFT), computational biology (SIGBio), symbolic computing (SIGSAM), semantic web (SIGWEB), and hardware design (SIGDA and SIGARCH). -

© in This Web Service Cambridge University Press
Cambridge University Press 978-1-107-03903-2 - Modern Computer Algebra: Third Edition Joachim Von Zur Gathen and Jürgen Gerhard Index More information Index A page number is underlined (for example: 667) when it represents the definition or the main source of information about the index entry. For several key words that appear frequently only ranges of pages or the most important occurrences are indexed. AAECC ......................................... 21 analytic number theory . 508, 523, 532, 533, 652 Abbott,John .............................. 465, 734 AnalyticalEngine ............................... 312 Abel,NielsHenrik .............................. 373 Andrews, George Eyre . 644, 697, 729, 735 Abeliangroup ................................... 704 QueenAnne .................................... 219 Abramov, Serge˘ı Aleksandrovich (Abramov annihilating polynomial ......................... 341 SergeiAleksandroviq) 7, 641, 671, 675, annihilator, Ann( ) .............................. 343 734, 735 annusconfusionis· ................................ 83 Abramson, Michael . 738 Antoniou,Andreas ........................ 353, 735 Achilles ......................................... 162 Antoniszoon, Adrian (Metius) .................... 82 ACM . see Association for Computing Machinery Aoki,Kazumaro .......................... 542, 751 active attack . 580 Apéry, Roger . 671, 684, 697, 761 Adam,Charles .................................. 729 number ....................................... 684 Adams,DouglasNoël ..................... 729, 796 Apollonius of -

Curriculum Vitae Bradley E. Richards December 2010
Curriculum Vitae Bradley E. Richards December 2010 Office: Home: Department of Mathematics and Computer Science 13446 108th Ave SW University of Puget Sound Vashon, WA 98070 1500 N. Warner St. (206) 567-5308 Tacoma, WA 98416 (206) 234-3560 (cell) (253) 879{3579 (253) 879{3352 (fax) [email protected] Degrees Ph.D. in Computer Science, August 1996 and M.S. in Computer Science, May 1992 University of Wisconsin, Madison, WI Advisor: James R. Larus Thesis: \Memory Systems for Parallel Programming" M.Sc. in Computer Science, April 1990 University of Victoria, Victoria B.C., Canada Advisor: Maarten van Emden Thesis: \Contributions to Functional Programming in Logic" B.A. Degrees, magna cum laude, in Computer Science and Physics, May 1988 Gustavus Adolphus College, St. Peter, MN Advisor: Karl Knight Positions Held University of Puget Sound, Tacoma, Washington Professor (7/2010{present) Associate Professor (7/2005{6/2010) Vassar College, Poughkeepsie, New York Associate Professor, tenured (6/2004{8/2005) Assistant Professor (9/1997{6/2004) Visiting Assistant Professor (9/1996{8/1997) University of Wisconsin, Madison, Wisconsin Graduate Research Assistant (6/1993{8/1996) Graduate Teaching Assistant (9/1990{5/1993) University of Victoria, Victoria, B.C., Canada Graduate Research Assistant (9/1988{4/1990) Graduate Teaching Assistant (9/1988{4/1990) Grants and Awards Co-PI, NSF Computing Research Infrastructure (CRI) grant #0734761, titled \Workshop for investigating the issues involved in implementing a data repository for empirical CS education data." Total grant amount $19,070, awarded 7/2007. With PI Kathryn Sanders, Associate Professor of Mathematics and Computer Science, Rhode Island College. -

Shanlu › About › Cv › CV Shanlu.Pdf Shan Lu
Shan Lu University of Chicago, Dept. of Computer Science Phone: +1-773-702-3184 5730 S. Ellis Ave., Rm 343 E-mail: [email protected] Chicago, IL 60637 USA Homepage: http://people.cs.uchicago.edu/~shanlu RESEARCH INTERESTS Tool support for improving the correctness and efficiency of large scale software systems EMPLOYMENT 2019 – present Professor, Dept. of Computer Science, University of Chicago 2014 – 2019 Associate Professor, Dept. of Computer Sciences, University of Chicago 2009 – 2014 Assistant Professor, Dept. of Computer Sciences, University of Wisconsin – Madison EDUCATION 2008 University of Illinois at Urbana-Champaign, Urbana, IL Ph.D. in Computer Science Thesis: Understanding, Detecting, and Exposing Concurrency Bugs (Advisor: Prof. Yuanyuan Zhou) 2003 University of Science & Technology of China, Hefei, China B.S. in Computer Science HONORS AND AWARDS 2019 ACM Distinguished Member Among 62 members world-wide recognized for outstanding contributions to the computing field 2015 Google Faculty Research Award 2014 Alfred P. Sloan Research Fellow Among 126 “early-career scholars (who) represent the most promising scientific researchers working today” 2013 Distinguished Alumni Educator Award Among 3 awardees selected by Department of Computer Science, University of Illinois 2010 NSF Career Award 2021 Honorable Mention Award @ CHI for paper [C71] (CHI 2021) 2019 Best Paper Award @ SOSP for paper [C62] (SOSP 2019) 2019 ACM SIGSOFT Distinguished Paper Award @ ICSE for paper [C58] (ICSE 2019) 2017 Google Scholar Classic Paper Award for -
Software Engineering 0835
Software Engineering 0835 1. Objectives In order to cultivate top creative talents in the field of software engineering, this discipline is designed to help students develop awareness of innovation and innovation capacity. Focusing on relevant software engineering research, students are expected to master the solid and broad basic theory and in-depth expertise and to achieve innovative research results. Doctoral students in this field should have a rigorous scientific attitude, good scientific style and scientific ethics, a wide range of disciplinary perspectives, a pioneering spirit and the overall quality for independently conducting scientific research. 2. Length of Study Period Postgraduate classification Normal length of study period Length of study period 4 years full-time 3 to 5 years full-time Doctoral students or 5 years part-time or 5 to 7 years part-time Direct Doctoral students I 5 years full-time 5 to 7 years full-time Direct Doctoral students II 6 years full-time 5 to 7 years full-time Notes: (1) Direct Doctoral students I: Doctoral students pursuing a doctoral degree directly from a bachelor degree (2) Direct Doctoral students II: Doctoral students of successive postgraduate and doctoral programs of study without a master degree 3. Research Areas (1) Software engineering theory and methods (2) Embedded computing and the Internet of Things (3) Digital media technologies (4) Trustworthy software (5) Computer and network security 4. Curriculums and Credits 4.1 Doctoral students (14 Credits or above) Course Classification Course -

Curriculum Vitae
Vita Benjamin G. Zorn June 2021 Partner Researcher Research in Software Engineering (RiSE) Group URL: http://aka.ms/zorn Microsoft Research, Redmond Lab Telephone: (425) 703-6290, Cell: on-request Microsoft Corporation Fax: (425) 936-7329 One Microsoft Way, Redmond WA 98052 Email: [email protected], [email protected] Research Interests Programming language design and implementation, program runtime systems and memory management, performance evaluation, compilers, error recovery, software fault tolerance, security, malware detection, software development, computer architecture Education • Ph.D. (Computer Science) December 1989, University of California, Berkeley. Thesis: Comparative Performance Evaluation of Garbage Collection Algorithms. Advisor: Paul N. Hilfinger. • M.S. (Computer Science) 1984, University of California, Berkeley. Master's Thesis: Experiences with Ada Code Generation. Advisor: Paul N. Hilfinger. • B.S. (Mathematics/Computer Science) summa cum laude 1982. Rensselaer Polytechnic Institute. Professional Experience • May 2019 – present. Partner Researcher, Research in Software Engineering (RiSE) group, Microsoft Research, Redmond Lab. • January 2012 – May 2019, Research Manager and Principal Researcher, Research in Software Engineering (RiSE) group, Microsoft Research, Redmond. I co-managed the Research in Software Engineering (RiSE) group, a group of almost 30 researchers and developers working on programming languages and software engineering research. • January 2006 – 2012, Principal Researcher, Microsoft Research, Redmond. • August 1998 – January 2006, Senior Researcher, Microsoft Research. • June 1999 – present, Adjoint Associate Professor, University of Colorado at Boulder. • August 1996 – Junes 1999, Associate Professor, University of Colorado at Boulder. • January 1990 – July 1996, Assistant Professor, University of Colorado at Boulder. • May 1983 – December 1989, Research Assistant, University of California at Berkeley. • December 1985 – December 1989, Course Instructor, Franz Incorporated. -
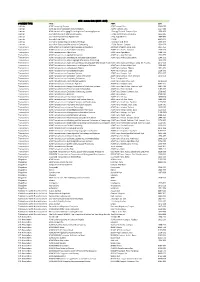
A ACM Transactions on Trans. 1553 TITLE ABBR ISSN ACM Computing Surveys ACM Comput. Surv. 0360‐0300 ACM Journal
ACM - zoznam titulov (2016 - 2019) CONTENT TYPE TITLE ABBR ISSN Journals ACM Computing Surveys ACM Comput. Surv. 0360‐0300 Journals ACM Journal of Computer Documentation ACM J. Comput. Doc. 1527‐6805 Journals ACM Journal on Emerging Technologies in Computing Systems J. Emerg. Technol. Comput. Syst. 1550‐4832 Journals Journal of Data and Information Quality J. Data and Information Quality 1936‐1955 Journals Journal of Experimental Algorithmics J. Exp. Algorithmics 1084‐6654 Journals Journal of the ACM J. ACM 0004‐5411 Journals Journal on Computing and Cultural Heritage J. Comput. Cult. Herit. 1556‐4673 Journals Journal on Educational Resources in Computing J. Educ. Resour. Comput. 1531‐4278 Transactions ACM Letters on Programming Languages and Systems ACM Lett. Program. Lang. Syst. 1057‐4514 Transactions ACM Transactions on Accessible Computing ACM Trans. Access. Comput. 1936‐7228 Transactions ACM Transactions on Algorithms ACM Trans. Algorithms 1549‐6325 Transactions ACM Transactions on Applied Perception ACM Trans. Appl. Percept. 1544‐3558 Transactions ACM Transactions on Architecture and Code Optimization ACM Trans. Archit. Code Optim. 1544‐3566 Transactions ACM Transactions on Asian Language Information Processing 1530‐0226 Transactions ACM Transactions on Asian and Low‐Resource Language Information Proce ACM Trans. Asian Low‐Resour. Lang. Inf. Process. 2375‐4699 Transactions ACM Transactions on Autonomous and Adaptive Systems ACM Trans. Auton. Adapt. Syst. 1556‐4665 Transactions ACM Transactions on Computation Theory ACM Trans. Comput. Theory 1942‐3454 Transactions ACM Transactions on Computational Logic ACM Trans. Comput. Logic 1529‐3785 Transactions ACM Transactions on Computer Systems ACM Trans. Comput. Syst. 0734‐2071 Transactions ACM Transactions on Computer‐Human Interaction ACM Trans. -

Central Library: IIT GUWAHATI
Central Library, IIT GUWAHATI BACK VOLUME LIST DEPARTMENTWISE (as on 20/04/2012) COMPUTER SCIENCE & ENGINEERING S.N. Jl. Title Vol.(Year) 1. ACM Jl.: Computer Documentation 20(1996)-26(2002) 2. ACM Jl.: Computing Surveys 30(1998)-35(2003) 3. ACM Jl.: Jl. of ACM 8(1961)-34(1987); 43(1996);45(1998)-50 (2003) 4. ACM Magazine: Communications of 39(1996)-46#3-12(2003) ACM 5. ACM Magazine: Intelligence 10(1999)-11(2000) 6. ACM Magazine: netWorker 2(1998)-6(2002) 7. ACM Magazine: Standard View 6(1998) 8. ACM Newsletters: SIGACT News 27(1996);29(1998)-31(2000) 9. ACM Newsletters: SIGAda Ada 16(1996);18(1998)-21(2001) Letters 10. ACM Newsletters: SIGAPL APL 28(1998)-31(2000) Quote Quad 11. ACM Newsletters: SIGAPP Applied 4(1996);6(1998)-8(2000) Computing Review 12. ACM Newsletters: SIGARCH 24(1996);26(1998)-28(2000) Computer Architecture News 13. ACM Newsletters: SIGART Bulletin 7(1996);9(1998) 14. ACM Newsletters: SIGBIO 18(1998)-20(2000) Newsletters 15. ACM Newsletters: SIGCAS 26(1996);28(1998)-30(2000) Computers & Society 16. ACM Newsletters: SIGCHI Bulletin 28(1996);30(1998)-32(2000) 17. ACM Newsletters: SIGCOMM 26(1996);28(1998)-30(2000) Computer Communication Review 1 Central Library, IIT GUWAHATI BACK VOLUME LIST DEPARTMENTWISE (as on 20/04/2012) COMPUTER SCIENCE & ENGINEERING S.N. Jl. Title Vol.(Year) 18. ACM Newsletters: SIGCPR 17(1996);19(1998)-20(1999) Computer Personnel 19. ACM Newsletters: SIGCSE Bulletin 28(1996);30(1998)-32(2000) 20. ACM Newsletters: SIGCUE Outlook 26(1998)-27(2001) 21.