2021 M-STEP Test Administration Manual (TAM)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Harem Fantasies and Music Videos: Contemporary Orientalist Representation
W&M ScholarWorks Dissertations, Theses, and Masters Projects Theses, Dissertations, & Master Projects 2007 Harem Fantasies and Music Videos: Contemporary Orientalist Representation Maya Ayana Johnson College of William & Mary - Arts & Sciences Follow this and additional works at: https://scholarworks.wm.edu/etd Part of the American Studies Commons, and the Music Commons Recommended Citation Johnson, Maya Ayana, "Harem Fantasies and Music Videos: Contemporary Orientalist Representation" (2007). Dissertations, Theses, and Masters Projects. Paper 1539626527. https://dx.doi.org/doi:10.21220/s2-nf9f-6h02 This Thesis is brought to you for free and open access by the Theses, Dissertations, & Master Projects at W&M ScholarWorks. It has been accepted for inclusion in Dissertations, Theses, and Masters Projects by an authorized administrator of W&M ScholarWorks. For more information, please contact [email protected]. Harem Fantasies and Music Videos: Contemporary Orientalist Representation Maya Ayana Johnson Richmond, Virginia Master of Arts, Georgetown University, 2004 Bachelor of Arts, George Mason University, 2002 A Thesis presented to the Graduate Faculty of the College of William and Mary in Candidacy for the Degree of Master of Arts American Studies Program The College of William and Mary August 2007 APPROVAL PAGE This Thesis is submitted in partial fulfillment of the requirements for the degree of Master of Arts Maya Ayana Johnson Approved by the Committee, February 2007 y - W ^ ' _■■■■■■ Committee Chair Associate ssor/Grey Gundaker, American Studies William and Mary Associate Professor/Arthur Krrtght, American Studies Cpllege of William and Mary Associate Professor K im b erly Phillips, American Studies College of William and Mary ABSTRACT In recent years, a number of young female pop singers have incorporated into their music video performances dance, costuming, and musical motifs that suggest references to dance, costume, and musical forms from the Orient. -

Lale Yurtseven: Okay, It's Recording Now
Lale Yurtseven: Okay, it's recording now. So, is there anybody volunteering to take notes. Teresa Morris: I can, if you send me the recording. But it's not going to get to everybody, until the fall Lale Yurtseven: That's fine. Yeah. We yeah we I I will send you the recording. That would be great. Thank you very much to resource. So I'm going to put to resize here. Lale Yurtseven: You are without the H right to Risa Lale Yurtseven: Yes. Oh, ah, Lale Yurtseven: Yes, that's right. Lale Yurtseven: Okay. Lale Yurtseven: All right, so Lale Yurtseven: Let's just go through the rest of the agenda here so we can Judy just send them minutes from last Lale Yurtseven: week's meeting and I guess the prior one which should be just a short summary because all we really did was go through the Lale Yurtseven: draft policy will probably do that and fall to to decide. You think that we can do that push that to the Fall Meeting as well. Teresa Morris: We'll have to Lale Yurtseven: Yeah. Teresa Morris: And if you can send me the Lale Yurtseven: I'll send you the recording. Lale Yurtseven: Okay, okay. Yeah. Judy Lariviere: And just before we review the minutes from last time I started going through the recording and there was a lot. There was so much discussion. So I don't think there. It's not all captured in the minute, so I can go back. I started going through the courting. -
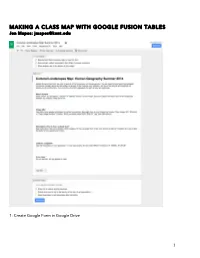
MAKING a CLASS MAP with GOOGLE FUSION TABLES Jen Mapes: [email protected]
MAKING A CLASS MAP WITH GOOGLE FUSION TABLES Jen Mapes: [email protected] 1: Create Google Form in Google Drive 1 2. Give form link (and further instructions) to students 2 3. When submission deadline has passed, Create a Fusion Table out of your “Responses” Spreadsheet (created automatically by Google Forms). If Fusion Tables does not show up as an option, you will need to “Connect more apps,” and select it. With a Kent account, you may need to go through an extra step. Ask me or a Help Desk person for assistance if you run into this problem. 3 This arrow will let you choose “change column” 4. Change type for your Lat/Long column to “Location.” Incorrect formats will be highlighted in yellow. 4 This arrow will let you choose “change column” 5. Change column for Image URL to Format: Eight Line Image 5 6 6. Choose the map tab, and your lat/longs will be geocoded on a map for you. If you use addresses instead, this may take an extra few minutes. 7. The option to configure your map should show up when your map is created. If it disappears, go to Tools/Change Map. You will then see two options: Change feature styles (the dots on the map), and change info window (what pops up when you click on the dots). 7 8. If you’d like to change the dots, or have them represented by different colors/styles depending on their values, then you’ll change the feature styles. Column allows you to use your spreadsheet (or form) to select what icon will appear with each submission. -

F I R I N G O P E R a T I O
Summer 2012 ▲ Vol. 2 Issue 2 ▲ Produced and distributed quarterly by the Wildland Fire Lessons Learned Center F I R I N G O P E R A T I O N S What does a good firing show look like? And, what could go wrong ? Once you By Paul Keller t’s an age-old truth. put fire down— Once you put fire down—you can’t take it back. I We all know how this act of lighting the match— you can’t when everything goes as planned—can help you accomplish your objectives. But, unfortunately, once you’ve put that fire on take it back. the ground, you-know-what can also happen. Last season, on seven firing operations—including prescribed fires and wildfires (let’s face it, your drip torch doesn’t know the difference)—things did not go as planned. Firefighters scrambled for safety zones. Firefighters were entrapped. Firefighters got burned. It might serve us well to listen to the firing operation lessons that our fellow firefighters learned in 2011. As we already know, these firing show mishaps—plans gone awry—aren’t choosey about fuel type or geographic area. Last year, these incidents occurred from Arizona to Georgia to South Dakota—basically, all over the map. In Arkansas, on the mid-September Rock Creek Prescribed Fire, that universal theme about your drip torch never distinguishing between a wildfire or prescribed fire is truly hammered home. Here’s what happened: A change in wind speed dramatically increases fire activity. Jackpots of fuel exhibit extreme fire behavior and torching of individual trees. -

Applying Library Values to Emerging Technology Decision-Making in the Age of Open Access, Maker Spaces, and the Ever-Changing Library
ACRL Publications in Librarianship No. 72 Applying Library Values to Emerging Technology Decision-Making in the Age of Open Access, Maker Spaces, and the Ever-Changing Library Editors Peter D. Fernandez and Kelly Tilton Association of College and Research Libraries A division of the American Library Association Chicago, Illinois 2018 The paper used in this publication meets the minimum requirements of Ameri- can National Standard for Information Sciences–Permanence of Paper for Print- ed Library Materials, ANSI Z39.48-1992. ∞ Cataloging-in-Publication data is on file with the Library of Congress. Copyright ©2018 by the Association of College and Research Libraries. All rights reserved except those which may be granted by Sections 107 and 108 of the Copyright Revision Act of 1976. Printed in the United States of America. 22 21 20 19 18 5 4 3 2 1 Contents Contents Introduction .......................................................................................................ix Peter Fernandez, Head, LRE Liaison Programs, University of Tennessee Libraries Kelly Tilton, Information Literacy Instruction Librarian, University of Tennessee Libraries Part I Contemplating Library Values Chapter 1. ..........................................................................................................1 The New Technocracy: Positioning Librarianship’s Core Values in Relationship to Technology Is a Much Taller Order Than We Think John Buschman, Dean of University Libraries, Seton Hall University Chapter 2. ........................................................................................................27 -

Forensic Methods and Tools for Web Environments
Forensic Methods and Tools for Web Environments by Michael Kent Mabey A Dissertation Presented in Partial Fulfillment of the Requirements for the Degree Doctor of Philosophy Approved November 2017 by the Graduate Supervisory Committee: Gail-Joon Ahn, Co-Chair Adam Doupé, Co-Chair Stephen S. Yau Joohyung Lee Ziming Zhao ARIZONA STATE UNIVERSITY December 2017 ABSTRACT The Web is one of the most exciting and dynamic areas of development in today’s technology. However, with such activity, innovation, and ubiquity have come a set of new challenges for digital forensic examiners, making their jobs even more difficult. For examiners to become as effective with evidence from the Web as they currently are with more traditional evidence, they need (1) methods that guide them to know how to approach this new type of evidence and (2) tools that accommodate web environments’ unique characteristics. In this dissertation, I present my research to alleviate the difficulties forensic examiners currently face with respect to evidence originating from web environments. First, I introduce a framework for web environment forensics, which elaborates on and addresses the key challenges examiners face and outlines a method for how to approach web-based evidence. Next, I describe my work to identify extensions installed on encrypted web thin clients using only a sound understanding of these systems’ inner workings and the metadata of the encrypted files. Finally, I discuss my approach to reconstructing the timeline of events on encrypted web thin clients by using service provider APIs as a proxy for directly analyzing the device. In each of these research areas, I also introduce structured formats that I customized to accommodate the unique features of the evidence sources while also facilitating tool interoperability and information sharing. -

The SPS Google Docs and Drive 21 Day Challenge!
Welcome to the SPS Google Docs and Drive 21 Day Challenge! There is a popular notion that it takes 21 days to create a new habit and I thought it might be fun to break up the district's introduction to Google Docs and Drive into 21 bitesized chunks. Hence, the SPS Google Drive 21 day challenge! Look for a new (and small) Google Drive tip each day via district email for the next 21 school days. Hopefully, this approach will make trying out the new tools easier, more manageable, and maybe even a little fun. In addition to the 21 day challenge tips, you should check out these other Google Docs and Drive resources: ● Google Docs and Drive Basics,https://www.google.com/edu/training/tools/drive/level1.html ● Google Docs and Drive uses in the classroom,https://www.google.com/edu/training/tools/drive/level2.html Day 1 How do I get to Google Drive? Let's start with a quick and easy tip! Like the other tools included in Google Apps for Education (Calendar, Sites, etc.), Google Drive can be quickly accessed right from your email screen. Here's how: 1. Click the "Grid" icon at the top of the screen next to your email address (or your picture if you've added one) 2. Click the icon for "Drive" 3. A new browser tab or window will open displaying your Google Drive 4. If you're using a modern web browser like Google Chrome or Mozilla Firefox, you can easily switch back and forth between your Mail and your Drive just by clicking on the corresponding tabs at the top of the browser window BTW, if you want to get a good, quick overview of what Google Drive is and why you would even want to use it, take a look at these short videos. -

Teaching Strategies for Improving Algebra Knowledge in Middle and High School Students
EDUCATOR’S PRACTICE GUIDE A set of recommendations to address challenges in classrooms and schools WHAT WORKS CLEARINGHOUSE™ Teaching Strategies for Improving Algebra Knowledge in Middle and High School Students NCEE 2015-4010 U.S. DEPARTMENT OF EDUCATION About this practice guide The Institute of Education Sciences (IES) publishes practice guides in education to provide edu- cators with the best available evidence and expertise on current challenges in education. The What Works Clearinghouse (WWC) develops practice guides in conjunction with an expert panel, combining the panel’s expertise with the findings of existing rigorous research to produce spe- cific recommendations for addressing these challenges. The WWC and the panel rate the strength of the research evidence supporting each of their recommendations. See Appendix A for a full description of practice guides. The goal of this practice guide is to offer educators specific, evidence-based recommendations that address the challenges of teaching algebra to students in grades 6 through 12. This guide synthesizes the best available research and shares practices that are supported by evidence. It is intended to be practical and easy for teachers to use. The guide includes many examples in each recommendation to demonstrate the concepts discussed. Practice guides published by IES are available on the What Works Clearinghouse website at http://whatworks.ed.gov. How to use this guide This guide provides educators with instructional recommendations that can be implemented in conjunction with existing standards or curricula and does not recommend a particular curriculum. Teachers can use the guide when planning instruction to prepare students for future mathemat- ics and post-secondary success. -

The Future of Reputation: Gossip, Rumor, and Privacy on the Internet
GW Law Faculty Publications & Other Works Faculty Scholarship 2007 The Future of Reputation: Gossip, Rumor, and Privacy on the Internet Daniel J. Solove George Washington University Law School, [email protected] Follow this and additional works at: https://scholarship.law.gwu.edu/faculty_publications Part of the Law Commons Recommended Citation Solove, Daniel J., The Future of Reputation: Gossip, Rumor, and Privacy on the Internet (October 24, 2007). The Future of Reputation: Gossip, Rumor, and Privacy on the Internet, Yale University Press (2007); GWU Law School Public Law Research Paper 2017-4; GWU Legal Studies Research Paper 2017-4. Available at SSRN: https://ssrn.com/abstract=2899125 This Article is brought to you for free and open access by the Faculty Scholarship at Scholarly Commons. It has been accepted for inclusion in GW Law Faculty Publications & Other Works by an authorized administrator of Scholarly Commons. For more information, please contact [email protected]. Electronic copy available at: https://ssrn.com/ abstract=2899125 The Future of Reputation Electronic copy available at: https://ssrn.com/ abstract=2899125 This page intentionally left blank Electronic copy available at: https://ssrn.com/ abstract=2899125 The Future of Reputation Gossip, Rumor, and Privacy on the Internet Daniel J. Solove Yale University Press New Haven and London To Papa Nat A Caravan book. For more information, visit www.caravanbooks.org Copyright © 2007 by Daniel J. Solove. All rights reserved. This book may not be reproduced, in whole or in part, including illustrations, in any form (beyond that copying permitted by Sections 107 and 108 of the U.S. -

Songs by Title
Karaoke Song Book Songs by Title Title Artist Title Artist #1 Nelly 18 And Life Skid Row #1 Crush Garbage 18 'til I Die Adams, Bryan #Dream Lennon, John 18 Yellow Roses Darin, Bobby (doo Wop) That Thing Parody 19 2000 Gorillaz (I Hate) Everything About You Three Days Grace 19 2000 Gorrilaz (I Would Do) Anything For Love Meatloaf 19 Somethin' Mark Wills (If You're Not In It For Love) I'm Outta Here Twain, Shania 19 Somethin' Wills, Mark (I'm Not Your) Steppin' Stone Monkees, The 19 SOMETHING WILLS,MARK (Now & Then) There's A Fool Such As I Presley, Elvis 192000 Gorillaz (Our Love) Don't Throw It All Away Andy Gibb 1969 Stegall, Keith (Sitting On The) Dock Of The Bay Redding, Otis 1979 Smashing Pumpkins (Theme From) The Monkees Monkees, The 1982 Randy Travis (you Drive Me) Crazy Britney Spears 1982 Travis, Randy (Your Love Has Lifted Me) Higher And Higher Coolidge, Rita 1985 BOWLING FOR SOUP 03 Bonnie & Clyde Jay Z & Beyonce 1985 Bowling For Soup 03 Bonnie & Clyde Jay Z & Beyonce Knowles 1985 BOWLING FOR SOUP '03 Bonnie & Clyde Jay Z & Beyonce Knowles 1985 Bowling For Soup 03 Bonnie And Clyde Jay Z & Beyonce 1999 Prince 1 2 3 Estefan, Gloria 1999 Prince & Revolution 1 Thing Amerie 1999 Wilkinsons, The 1, 2, 3, 4, Sumpin' New Coolio 19Th Nervous Breakdown Rolling Stones, The 1,2 STEP CIARA & M. ELLIOTT 2 Become 1 Jewel 10 Days Late Third Eye Blind 2 Become 1 Spice Girls 10 Min Sorry We've Stopped Taking Requests 2 Become 1 Spice Girls, The 10 Min The Karaoke Show Is Over 2 Become One SPICE GIRLS 10 Min Welcome To Karaoke Show 2 Faced Louise 10 Out Of 10 Louchie Lou 2 Find U Jewel 10 Rounds With Jose Cuervo Byrd, Tracy 2 For The Show Trooper 10 Seconds Down Sugar Ray 2 Legit 2 Quit Hammer, M.C. -

Pace and Scale of Restoration As It Relates to the Blue Mountains Forest Plan Revision
Public Workshop on Pace & Scale of Restoration and the Blue Mountains Forest Plan Revision Hosted by the Wallowa County Natural Resources Advisory Committee (NRAC) Enterprise, Oregon | July 28, 2015 These notes reflect the best efforts of the notetaker to capture the discussion of meeting participants, but in no way are these notes a word-for-word transcript as the notetaker may have unintentionally missed some statements or dialogue. Also, the notes do not attempt to correct or clarify any statements made by participants. Participants: Cynthia Warnock, Mike Hayward, Bruce Dunn, Roy Garten, John Hilloch, Ed Minalia, Ross Stenkamp, Gina Birkmaier, Jack Snyder, Mark Bujanovich, Chad Nash, Tim Newton, Don Bronson, Raider Heck, Jeff Jenkins, Greg Barreto, Kristal Jenkins, Wendy Falk, Peggy Kite Martin, Mike Fack, Lesslie Jones, Sam Magera, Otilia Thiel, Patrick Thiel, Heather Melville, Elwayne Henderson, Jack Southworth US Forest Service (FS) participants: Tom Montoya, Kris Stein, Jake Lubera, Sabrina Stadler, Gunnar Carnwath, Peter Fargo (notetaker) Organizations represented: Wallowa County, Wallowa County NRAC, local logging industry, local ranching industry, Oregon State University Extension Service, Oregon State House of Representatives, and USFS -- Introduction – Jack Southworth, Facilitator, High Desert Partnership: We are here to discuss the Pace and Scale of Restoration as it relates to the Blue Mountains Forest Plan Revision. We’ll begin with introductions around the room and then hear from NRAC members. Introductions around the -

Honey Sheets: What Happens to Leaked Google Spreadsheets?
Honey Sheets: What Happens To Leaked Google Spreadsheets? Martin Lazarov, Jeremiah Onaolapo, and Gianluca Stringhini University College London [email protected],fj.onaolapo,[email protected] Abstract suite that provides business tools like official email ad- dresses, calendars, online storage space, and document Cloud-based documents are inherently valuable, due to processing services. the volume and nature of sensitive personal and business Consequently, a considerable amount of valuable in- content stored in them. Despite the importance of such formation is stored in online accounts, including sensi- documents to Internet users, there are still large gaps in tive personal information and business secrets. These in the understanding of what cybercriminals do when they turn attract cybercriminals seeking to make profit from illicitly get access to them by for example compromising such information. To gain access to such online ac- the account credentials they are associated with. In this counts, cybercriminals typically target owners of the ac- paper, we present a system able to monitor user activity counts with phishing attacks, and sometimes, malware. on Google spreadsheets. We populated 5 Google spread- Often, databases containing user credentials are also at- sheets with fake bank account details and fake funds tacked, and credentials in them get stolen. transfer links. Each spreadsheet was configured to re- Stolen credentials are usually sold by cybercriminals port details of accesses and clicks on links back to us. in underground marketplaces, to other cybercriminals for To study how people interact with these spreadsheets in malicious purposes. Depending on the nature of the com- case they are leaked, we posted unique links pointing to promised accounts, some are used to send unsolicited the spreadsheets on a popular paste site.