Real-Time and Historic Location Surveillance After United States V
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Deerfield Beach News
TO REACH BOCA RATON NEWS KATCN NEWS PHONE 3767 Serving Boca- Raton and Deerfield Beach No. 4 Vol. 45 Boca Raton, Florida, Thursday, October 1, 1959 24 pages Price Ten Cents City Sanitarian Is Considered Dr. C. L. Brumback, medi- cal director of the Palm Beach Squirrel Puts Out Lights County Health Department, and Fireman Earl Troxell said a squirrel touching a transformer was Joseph C. Alvarez, chief sani- responsible for a power failure that cut out electrical service in tarian, appeared before the City Boca Raton, parts of Deerfield Beach and Delray Beach for more Commission in a committee meeting Monday to discuss the than two hours Tuesday evening. I possibility of a sanitarian for Troxell said the squirrel caused quite an explosion when it Boca Raton. came in contact with a transformer at a Florida Power and Light Alvarez told the commis- substation. sioners that a county sanitarian Service was off from 5:10 to 7:10 in most areas. employed full time in Delray Troxell said nothing was found of the squirrel. The accident Beach had been working out ex- happened at the Boca power plant, the fireman said. ceptionally well under an ar- "rangement in which the city and the state jointly pay the sani- City Commission Adopts tarian. Alvarez said a sanitarian would normally be selected New Civil Service Rules under the state merit system ex- New rules and regulations for amination and would work close- the Civil Service Board were a- Groundbreaking ly in conjunction with the County dopted by the City Commission Health Department Tuesday. -

A Fish in a Stream on Body and Memory in Virginia Woolf's
DOI: http://dx.doi.org/10.5007/2175-8026.2021.e79128 A FISH IN A STREAM ON BODY AND MEMORY IN VIRGINIA WOOLF’S “A SKETCH OF THE PAST” Ana Carolina de Carvalho Mesquita1* 1Independent Researcher, São Paulo, SP, Brasil Abstract This article examines the deadlocks foregrounded in recreating and reconstituting memory in Virginia Woolf’s “A Sketch of the Past” from the body’s perspective. “Body” is seen here as a category to reflect upon the meanings of women’s marginality and resistance. Of particular interest are the hiatuses of memory in “Sketch,” for recovering her own body and establishing a voice from within it constituted a conflicting and contradictory process, to which Virginia Woolf responded with unique narrative strategies. General and private perspectives merge, not only because of the troubles of not being personal when writing one’s own life but because Woolf claims that leaving out “the person to whom things happen” is undesirable. Even though she may meet silence when including herself personally in her writings, silence is embraced as a constituent. I suggest that much in the same way Woolf juxtaposes temporalities and subjectivities in “Sketch,” personality, impersonality, and their absence (or connectedness, which is another way of seeing it) are also juxtaposed in a kind of palimpsest that does not overlook corporeality but acknowledges it as essential. Keywords: Virginia Woolf; body; memory; women’s embodiment; life- writing * Translator, and PhD in Literary Theory and Comparative Literature by Universidade de São Paulo (USP). By Virginia Woolf, she has translated into Brazilian Portuguese “A Sketch of the Past” (Um esboço do passado, Nós, 2020), “The Death of the Moth” (A morte da mariposa, Nós, 2021), and the first volume of her Diaries (Diário I: 1915-1918, Nós, 2021). -

Univerzita Palackého V Olomouci Filozofická Fakulta
UNIVERZITA PALACKÉHO V OLOMOUCI FILOZOFICKÁ FAKULTA KATEDRA ANGLISTIKY A AMERIKANISTIKY Veronika Glaserová The Importance and Meaning of the Character of the Writer in Stephen King’s Works Diplomová práce Vedoucí práce: PhDr. Matthew Sweney, Ph.D. Olomouc 2014 Olomouc 2014 Prohlášení Prohlašuji, že jsem tuto diplomovou práci vypracovala samostatně pod odborným dohledem vedoucího práce a uvedla jsem předepsaným způsobem všechny použité podklady a literaturu. V Olomouci dne Podpis: Poděkování Děkuji vedoucímu práce za odborné vedení práce, poskytování rad a materiálových podkladů k práci. Contents Introduction ....................................................................................................................... 6 1. Genres of Stephen King’s Works ................................................................................. 8 1.1. Fiction .................................................................................................................... 8 1.1.1. Mainstream fiction ........................................................................................... 9 1.1.2. Horror fiction ................................................................................................. 10 1.1.3. Science fiction ............................................................................................... 12 1.1.4. Fantasy ........................................................................................................... 14 1.1.5. Crime fiction ................................................................................................. -

Stephen-King-Book-List
BOOK NERD ALERT: STEPHEN KING ULTIMATE BOOK SELECTIONS *Short stories and poems on separate pages Stand-Alone Novels Carrie Salem’s Lot Night Shift The Stand The Dead Zone Firestarter Cujo The Plant Christine Pet Sematary Cycle of the Werewolf The Eyes Of The Dragon The Plant It The Eyes of the Dragon Misery The Tommyknockers The Dark Half Dolan’s Cadillac Needful Things Gerald’s Game Dolores Claiborne Insomnia Rose Madder Umney’s Last Case Desperation Bag of Bones The Girl Who Loved Tom Gordon The New Lieutenant’s Rap Blood and Smoke Dreamcatcher From a Buick 8 The Colorado Kid Cell Lisey’s Story Duma Key www.booknerdalert.com Last updated: 7/15/2020 Just After Sunset The Little Sisters of Eluria Under the Dome Blockade Billy 11/22/63 Joyland The Dark Man Revival Sleeping Beauties w/ Owen King The Outsider Flight or Fright Elevation The Institute Later Written by his penname Richard Bachman: Rage The Long Walk Blaze The Regulators Thinner The Running Man Roadwork Shining Books: The Shining Doctor Sleep Green Mile The Two Dead Girls The Mouse on the Mile Coffey’s Heads The Bad Death of Eduard Delacroix Night Journey Coffey on the Mile The Dark Tower Books The Gunslinger The Drawing of the Three The Waste Lands Wizard and Glass www.booknerdalert.com Last updated: 7/15/2020 Wolves and the Calla Song of Susannah The Dark Tower The Wind Through the Keyhole Talisman Books The Talisman Black House Bill Hodges Trilogy Mr. Mercedes Finders Keepers End of Watch Short -

The Stranger
Albert Camus THE STRANGER THE Stranger By ALBERT CAMUS Translated from the French by Stuart Gilbert VINTAGE BOOKS A Division of Random House NEW YORK 1 Albert Camus THE STRANGER VINTAGE BOOKS are published by Alfred A. Knopf, Inc. and Random House, Inc. Copyright 1942 by Librairie Gallimard as L’ÉTRANGER Copyright 1946 by ALFRED A. KNOPF, INC. All rights reserved. No part of this book may be reproduced in any form without permission in writing from the publisher, except by a reviewer who may quote brief passages in a review to be printed in a magazine or newspaper. Manufactured in the United States of America. Distributed in Canada by Random House of Canada Limited, Toronto. 2 Albert Camus THE STRANGER Contents Contents ........................................................................................................................3 Part One ........................................................................................................................4 I.................................................................................................................................. 4 II .............................................................................................................................. 14 III............................................................................................................................. 18 IV............................................................................................................................. 24 V ............................................................................................................................. -

Duality and Reflections in Stephen King's Writers Alexis Hitchcock
ABSTRACT A Dark Mirror: Duality and Reflections in Stephen King's Writers Alexis Hitchcock Director: Dr. Lynne Hinojosa, Ph.D. Stephen King is well known for popular horror fiction but has recently been addressed more thoroughly by literary critics. While most studies focus on horror themes and the relationships between various characters, this thesis explores the importance of the author characters in three works by Stephen King: Misery, The Dark Half, and The Shining. The introduction gives a background of Stephen King as an author of popular horror fiction and discusses two themes that are connected to his author characters: doppelgängers and duality, and the idea of the death of the author. The death of the author is the idea that an author's biography should not affect the interpretation of a text. Implicit in this idea is the notion that the separation of an author from his work makes the text more literary and serious. The second chapter on Misery explores the relationship between the author and the readership or fans and discusses Stephen King’s divide caused by his split between his talent as an author of popular fiction and a desire to be a writer of literary fiction. The third chapter concerning The Dark Half explores Stephen King’s use of the pseudonym Richard Bachman and the splitting this created within himself and the main character of his novel. The last chapter includes discussion of The Shining and the author character’s split in personality caused by alcohol and supernatural sources. Studying the author characters and their doppelgängers reveals the unique stance King takes on the “death of the author” idea and shows how he represents the splitting of the self within his works. -

Creep Show Licensed Psychologist with Of- Fices in the Tall Pine Center in Somerset
Inside: Time Off's Restaurant Guide Franklin News-Record Vol. 36, No. 12 Thursday, March 21, 1991 50 0 NEWS Chemical cloud still has officials perplexed By Laurie Lynn Strasser over how its source —• a leaky been in business two years, needs no because it's too dangerous," said said, because a deposit upon purchase Staff Writer container of hydrogen chloride — DEP operating permit because it is Somerset Recycling's owner, Bud usually serves as incentive for BRIEFS wound up at Somerset Recycling, not a full-scale recycling facility, Mr. Flynn. "We didn't find the tanks empties to be returned to the com- State officials have yet to de- located at 921 Route 27, in the first Staples said, adding that the only until Saturday when we were clean- pany that distributes them. termine who is accountable for a place. laws pertaining to a situation such as ing a pile of steel to ship out to a If the company that made them caustic chemical cloud that exuded Hydrogen chloride gas reacts with this come "after the fact." shredder in Newark." were still in business, Mr. Flynn said. from a Franklin junkyard, hovered Spring rec moisture, cither in the atmosphere or "Our emergency response people Purchasing metal by the truckload it would be responsible for disposal. over town and wafted into New in living organisms, to form have referred the matter to the can be like buying strawberries in the But in this case, he speculated, what- Brunswick for seven hours Saturday. Franklin Township's Depart- hydrochloric acid, which can irritate Division of Environmental Quality to supermarket, Mr. -

Extensions of Remarks Hon. Harold T. Johnson
January 6, 1969 '.EXTENSIONS OF REMARKS 247 REPORT OF TELLERS of the United States, as delivered to the 2228, New Senate Office Building, before Mr. CURTIS. Mr. President, on behalf President of the Senate, is as follows: the Committee on the Judiciary, on John of the tellers on the part of the Senate, The whole number of electors ap N. Mitchell, of New York, Attorney Gen I wish to report on the counting of the pointed to vote for Vice President of the eral-designate. vote for President and Vice President. United States is 538, of which a majority At the indicated time and place per The state of the vote for President of is 270. sons interested in the hearing may make the United States, as delivered to the SPIRO T. AGNEW, of the State of Mary such representations as may be pertinent. President of the Senate, is as follows: land, has received for Vice President of The whole number of electors ap the United States 301 votes. EDMUND s. MUSKIE, of the State of ADJOURNMENT UNTIL THURSDAY, pointed to vote for President of the JANUARY 9, 1969 United States is 538, of which a majority Maine, has received 191 votes. Curtis E. LeMay, of the State of Cali Mr. KENNEDY. Mr. President, if there is 270. fornia, has received 46 votes. is no further business to come before the Richard M. Nixon, of the State of New Senate, I move, in accordance with the York, has received for President of the previous order, that the Senate stand in United States 301 votes. -

EXTENSIONS of REMARKS 3683 SPELLMAN, Mr
February 18, 1976 EXTENSIONS OF REMARKS 3683 SPELLMAN, Mr. SYMINGTON, Mr. the Committee on Banking, Currency and H.J. Res. 813. Joint resolution authorizing HOWE. and Mr. BAUCUS) : Housing. and requesting the President to issue a proc H.R. 11960. A bill to amend the Federal By Mr. STEELMAN: lamation designating the 7 calendar days Election Oampaign Act of 1971 to provide H.R. 11965. A blll to amend the Federal commencing on April 30 of each year as Na that members of the Federal Election Com Election Campaign Act of 1974 to establish tional Beta Sigma Phi Week; to the Com mission shall be appointed by the President an independent establishment of the execu mittee on Post Office and Civil Service. of the United States; to the Commtttee on tive branch of the Government of the United By Mr. BADILLO: House Administmtion. States, a commission to be known as the Fed By Mr. KASTENMEIER (for himself, eral Election Commission, and for other pur H. Res. 1037. Resolution expressing the Mr. STEELMAN, and Mr. GREEN): poses; to the Committee on House Admin sense of the House disapproving the guide H.R. 11961. A bill to require candidates for istration. lines proposed by the Attorney General for Federal office, Members of the Congress, and By Mr. WOLFF (for himself, Ms. ABZUG, Domestic Security Investigations by the officers and employees of the United States Mr. ADDABBO, Mr. BADILLO, Ms. BURKE Federal Bureau of Investigation; to the to file statements with the Comptroller Gen of California, Mr. DU Po NT, Mr. Committee on the Judiciary. -

Lovejoy United Presbyterian Church Online Worship February 14, 2021 10:15 AM Sunday School at 9:00 AM
LoveJoy United Presbyterian Church Online Worship February 14, 2021 10:15 AM Sunday School at 9:00 AM Watch/Participate online: lovejoyupc.org/live and click ‘Connect Via Zoom’ Participate by phone: +1 (312) 626-6799 and enter the meeting ID: 611 784 858# Gathering ❧ Thy sovereign majesty may we in glory see, Call to Worship and to eternity The glory of God shines love and adore. like a consuming fire. We have seen the glory of God Prayer of Confession in the face of Jesus Christ. God of all glory, beauty, and grace, The voice of God thunders we have tried to hide from you— like a mighty storm. to hide our faces, to hide our sin— Out of the cloud, God speaks: yet you have never hidden your love for us. This is my beloved Son; listen to him! We have tried to search for you— in temples, in clouds, on mountaintops— Prayer of the Day yet you have already revealed yourself to us Hymn - 2 - Come, Thou Almighty King in the face of Jesus Christ. Forgive us, and transform us 1 Come, thou almighty King, so that our lives may shine help us thy name to sing; with your glory, beauty, and grace; help us to praise: through Jesus Christ our Lord. Father, all glorious, o'er all victorious, Silent Prayers come, and reign over us, Ancient of Days. Assurance of Forgiveness 2 Come, thou incarnate Word, Word merciful, mighty Lord, ❧ our prayer attend. Time with the Children Come, and thy people bless, and give thy word success; Prayer for Illumination Spirit of holiness, Psalm 50:1-6 on us descend. -
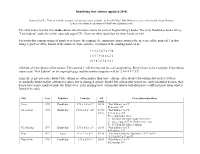
Identifying First Editions (Updated 2018) the Table Below Lists the First Trade
Identifying first editions (updated 2018) Compiled by Bev Vincent with the assistance of materials made available by Rich DeMars, John Mastrocco, Steve Oelrich and Shaun Nauman. E-mail corrections or questions to [email protected] The table below lists the first trade edition identification criteria for each of Stephen King's books. The early Doubleday books all say "First Edition" explicitly on the copyright page (CP). There are other identifiers for these books as well. For books that contain strings of numbers to denote the printing, the important consideration is the presence of the numeral 1 in that string, regardless of the format of the numbers. Some possible variations of the printing numbers are: 1 2 3 4 5 6 7 8 9 10 1 3 5 7 9 10 8 6 4 2 10 9 8 7 6 5 4 3 2 1 All three of these denote a first edition. The numeral 1 will be removed for a second printing. Black House is the exception. First edition copies state "First Edition" on the copyright page and the number sequence will be "2 4 6 8 9 7 5 3". Trim size is given because Book Club editions are often smaller than trade editions. Also, Book Club edition dust jackets (DJ) are occasionally found on first editions to replace lost or damaged jackets. Book Club edition dust jackets are easily identified because they do not have a price marked inside the front cover. Later printing trade edition dust jackets will often have a different price from what is found in the table. -

You've Seen the Movie, Now Play The
“YOU’VE SEEN THE MOVIE, NOW PLAY THE VIDEO GAME”: RECODING THE CINEMATIC IN DIGITAL MEDIA AND VIRTUAL CULTURE Stefan Hall A Dissertation Submitted to the Graduate College of Bowling Green State University in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY May 2011 Committee: Ronald Shields, Advisor Margaret M. Yacobucci Graduate Faculty Representative Donald Callen Lisa Alexander © 2011 Stefan Hall All Rights Reserved iii ABSTRACT Ronald Shields, Advisor Although seen as an emergent area of study, the history of video games shows that the medium has had a longevity that speaks to its status as a major cultural force, not only within American society but also globally. Much of video game production has been influenced by cinema, and perhaps nowhere is this seen more directly than in the topic of games based on movies. Functioning as franchise expansion, spaces for play, and story development, film-to-game translations have been a significant component of video game titles since the early days of the medium. As the technological possibilities of hardware development continued in both the film and video game industries, issues of media convergence and divergence between film and video games have grown in importance. This dissertation looks at the ways that this connection was established and has changed by looking at the relationship between film and video games in terms of economics, aesthetics, and narrative. Beginning in the 1970s, or roughly at the time of the second generation of home gaming consoles, and continuing to the release of the most recent consoles in 2005, it traces major areas of intersection between films and video games by identifying key titles and companies to consider both how and why the prevalence of video games has happened and continues to grow in power.