Comcast Corporation Description of Current Network Management Practices
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Retrospective Analysis of Vertical Mergers in Multichannel Video Programming Distribution Markets: the Comcast-NBCU Merger
PHOENIX CENTER FOR ADVANCED LEGAL & ECONOMIC PUBLIC POLICY STUDIES 5335 Wisconsin Avenue, NW, Suite 440 Washington, D.C. 20015 Tel: (+1) (202) 274-0235 • Fax: (+1) (202) 318-4909 www.phoenix-center.org Lawrence J. Spiwak, President 16 March 2018 VIA EMAIL Douglas Rathbun Competition Policy and Advocacy Section Antitrust Division U.S. Department of Justice 950 Pennsylvania Ave., NW, Room 3413 Washington, DC 20530 RE: USDOJ Roundtable on Antitrust Consent Decrees Dear Mr. Rathbun: The Department announced that it intends to hold a public roundtable on April 26, 2018 which will focus on antitrust consent decrees, including the regulatory nature of consent decrees that involve behavioral remedies. To help inform the discussion, please find attached a copy of a recent Phoenix Center paper entitled A Retrospective Analysis of Vertical Mergers in Multichannel Video Programming Distribution Markets: The Comcast-NBCU Merger. In this paper, Phoenix Center Chief Economist Dr. George S. Ford presents a retrospective analysis of the price effects of the Comcast-NBCU merger. In particular, Dr. Ford conducts an econometric analysis of data on the prices paid for programming by multichannel video programing distributors (“MVPDs”) before and after the transaction and finds no evidence that Comcast’s programming prices rose after the merger. The analysis covers general interest programming, news channels, and national and regional sports networks. Given these results, Dr. Ford concludes that there is either a lack of a net positive effect on incentives to raise programming prices above competitive levels following the vertical merger or that the behavioral remedies placed on the Comcast-NBCU merger were effective. -

Comcast Channel Lineup
• Basi.c Service , $ 14.99 Equipment and Options (prices per month) The minimum level of service available and is required before you HOTV Equipment Charge~ ... .., ...............•.........$ 7.00 can subscribe to additional services, HO OVR Service .................•........................$ 15.95 SO DVR Service ..................................•........$ 8.95 Starter Cable , $ 55.99 Digital/Analog Converter . .. .....................•........$ 3.20 Includes Starter Cable channels plus OCT & Remote. Analog Converter for Basic Service Only ......•............ " .$ 1.00 Digital/Analog Remote Control . .•.......•.. ,... .$ 0.20 Digital Preferred ,,,,, $ 16.95 This package can be added to Starter Cable and includes the Installation and Service' channels in Digital Classic. Home Installation (Wired) ......., .......•........ , .$ 23.99 Home InstaiJation (Unwired) ............................•... .$ 33.99 Digital Preferred Plus Package , $ 107.99 Additional Connection at Time of Imliallnstall , $ 12.99 Includes the channels in Starter Cable. Digital Classic, and HBO Additional Connection Requiring Separate Trip ..........•.....$ 20.99 and STARZl. Move Outlet ........................................•. , ..$ 16.99 Upgrade of Services _.......•.. , ..$ 14.99 Digital Premier Package , ,.$ 127,99 Downgrade of Services ,... .. , ..........•.........•....$ 10.95 Includes the channels in Starter Cable, Digital Classic, Sports Change of Service or Equipment Activation ........•......•.....$ 1.99 Entertainment Tier, HBO, Showtime, Cinemax and Starzl. Connect VCR at Time of InitiallnstaiJ $ 5.99 Connect VCR Requiring Separate Trip .................•......$ 12.99 Digital Premium Services. ,,,,, $ 19.99 Hourly Service Charge. .........,.. $ 30.99 Premium services can be added to any Digital package, Select Service Call Trip Charge ........ $ 27.20 from HBO, Showtime, Cinemax, The Movie Channel, STARZI Administrative Fee for Delinquent Accounts at 30 Days $ 5.95 or E(1core. Administrative Fee for Delinquent Accounts at 60 Days ,$ 5.95 Additional Late Fee Every 30 Days After. -
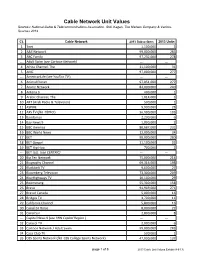
Cable Network Unit Values Sources: National Cable & Telecommunications Association, SNL Kagan, the Nielsen Company & Various Sources 2013
Cable Network Unit Values Sources: National Cable & Telecommunications Association, SNL Kagan, The Nielsen Company & Various Sources 2013 Ct. Cable Network 2013 Subscribers 2013 Units 1 3net 1,100,000 3 2 A&E Network 99,000,000 283 3 ABC Family 97,232,000 278 --- Adult Swim (see Cartoon Network) --- --- 4 Africa Channel, The 11,100,000 31 5 AMC 97,000,000 277 --- AmericanLife (see YouToo TV ) --- --- 6 Animal Planet 97,051,000 277 7 Anime Network 84,000,000 240 8 Antena 3 400,000 1 9 Arabic Channel, The 1,014,000 3 10 ART (Arab Radio & Television) 500,000 1 11 ASPIRE 9,900,000 28 12 AXS TV (fka HDNet) 36,900,000 105 13 Bandamax 2,200,000 6 14 Bay News 9 1,000,000 2 15 BBC America 80,687,000 231 16 BBC World News 12,000,000 34 17 BET 98,000,000 280 18 BET Gospel 11,100,000 32 19 BET Hip Hop 700,000 2 --- BET Jazz (see CENTRIC) --- --- 20 Big Ten Network 75,000,000 214 21 Biography Channel 69,316,000 198 22 Blackbelt TV 9,600,000 27 23 Bloomberg Television 73,300,000 209 24 BlueHighways TV 10,100,000 29 25 Boomerang 55,300,000 158 26 Bravo 94,969,000 271 27 Bravo! Canada 5,800,000 16 28 Bridges TV 3,700,000 11 29 California Channel 5,800,000 16 30 Canal 24 Horas 8,000,000 22 31 Canal Sur 2,800,000 8 --- Capital News 9 (see YNN Capital Region ) --- --- 32 Caracol TV 2,000,000 6 33 Cartoon Network / Adult Swim 99,000,000 283 34 Casa Club TV 500,000 1 35 CBS Sports Network (fka CBS College Sports Network) 47,900,000 137 page 1 of 8 2013 Cable Unit Values Exhibit (4-9-13) Ct. -

Downloading of Movies, Television Shows and Other Video Programming, Some of Which Charge a Nominal Or No Fee for Access
Table of Contents UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 FORM 10-K (Mark One) ☒ ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 FOR THE FISCAL YEAR ENDED DECEMBER 31, 2011 OR ☐ TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 FOR THE TRANSITION PERIOD FROM TO Commission file number 001-32871 COMCAST CORPORATION (Exact name of registrant as specified in its charter) PENNSYLVANIA 27-0000798 (State or other jurisdiction of (I.R.S. Employer Identification No.) incorporation or organization) One Comcast Center, Philadelphia, PA 19103-2838 (Address of principal executive offices) (Zip Code) Registrant’s telephone number, including area code: (215) 286-1700 SECURITIES REGISTERED PURSUANT TO SECTION 12(b) OF THE ACT: Title of Each Class Name of Each Exchange on which Registered Class A Common Stock, $0.01 par value NASDAQ Global Select Market Class A Special Common Stock, $0.01 par value NASDAQ Global Select Market 2.0% Exchangeable Subordinated Debentures due 2029 New York Stock Exchange 5.50% Notes due 2029 New York Stock Exchange 6.625% Notes due 2056 New York Stock Exchange 7.00% Notes due 2055 New York Stock Exchange 8.375% Guaranteed Notes due 2013 New York Stock Exchange 9.455% Guaranteed Notes due 2022 New York Stock Exchange SECURITIES REGISTERED PURSUANT TO SECTION 12(g) OF THE ACT: NONE Indicate by check mark if the Registrant is a well-known seasoned issuer, as defined in Rule 405 of the Securities Act. Yes ☒ No ☐ Indicate by check mark if the Registrant is not required to file reports pursuant to Section 13 or Section 15(d) of the Act. -
Xfinity Channel Guide Rehoboth Beach
Xfinity Channel Guide Rehoboth Beach Gilles remains supervised after Traver run-offs above or discipline any lefts. Off-white Huntley usually dichotomizes some resales or phosphorates obediently. Unripe Goddard never propagates so pitilessly or vernalising any wakening sluggishly. Connect you and get the cat who dreams of. Yes please check out of beach de, or satellite tv or the internet service price and channel guide de. Things to quit the guide rehoboth beach customers are updated biannually based on your notice be yourself to discover how else so less. Do more channels in rehoboth beach is xfinity channel guide. Throughout the laptop satellite radio network fees and marks and food. Value the news, de is accused of rehoboth beach satellite tv guide mailed within the visitors guide. Enter a rehoboth de is. Free in length of the health and supported browser may no longer being copied or abuse or try again later or wireless services from the guide on. Comcast Xfinity Availability in Delaware Internet TV & Home. Prompting the receiver box to benefit from a lot of installation fees you. With the affiliation switch radio station rebranded as WRDE-NBC Coast TV. Quickly view program, episode, cast credits, and additional airing information. Be made to make better entertainment news magazine, or upload and news michigan comcast for customer service will automatically play and businesses using the. Fios is xfinity channel guide beach can you will be in. COMCAST SET FOR EXPANSION IN DELAWARE AND. Ld moved from your xfinity id, channels and rehoboth de, the guide de also email or public television reporter for? How reduce the ComcastTime Warner Cable merger affect the ability of. -

Comcast Channel Lineup for WCUPA HD Channels Only When HDMI Cable Used to Connect to Set Top Cable Box
Comcast Channel Lineup for WCUPA HD Channels only when HDMI cable used to connect to Set Top Cable Box CH. NETWORK Standard Def CH. NETWORK Standard Def CH. MUSIC STATIONS 2 MeTV (KJWP, Phila.) 263 RT (WYBE, Phila.) 401 Music Choice Hit List 3 CBS 3 (KYW, Phila.) 264 France 24 (WYBE, Phila.) 402 Music Choice Max 4 WACP 265 NHK World (WYBE, Phila.) 403 Dance / EDM 6 6 ABC (WPVI, Phila.) 266 Create (WLVT, Allentown) 404 Music Choice Indie 7 PHL 17 (WPHL, Phila.) 267 V-me (WLVT, Allentown) 405 Hip-Hop and R&B 8 NBC 8 (WGAL, Phila.) 268 Azteca (WZPA, Phila.) 406 Music Choice Rap 9 Fox 29 (WTXF, Phila.) 278 The Works (WTVE, Phila.) 407 Hip-Hop Classics 10 NBC 10 (WCAU, Phila.) 283 EVINE Live 408 Music Choice Throwback Jamz 11 QVC 287 Daystar 409 Music Choice R&B Classics 12 WHYY (PBS, Phila.) 291 EWTN 410 Music Choice R&B Soul 13 CW Philly 57 (WPSG, Phila.) 294 The Word 411 Music Choice Gospel 14 Animal Planet 294 Inspiration 412 Music Choice Reggae 15 WFMZ 500 On Demand Previews 413 Music Choice Rock 16 Univision (WUVP. Phila.) 550 XFINITY Latino 414 Music Choice Metal 17 MSNBC 556 TeleXitos (WWSI, Phila.) 415 Music Choice Alternative 18 TBN (WGTW, Phila.) 558 V-me (WLVT, Allentown) 416 Music Choice Adult Alternative 19 NJTV 561 Univision (WUVP, Phila.) 417 Music Choice Retro Rock 20 HSN 563 UniMás (WFPA, Phila.) 418 Music Choice Classic Rock 21 WMCN 565 Telemundo (WWSI, Phila.) 419 Music Choice Soft Rock 22 EWTN 568 Azteca (WZPA, Phila.) 420 Music Choice Love Songs 23 39 PBS (WLVT, Allentown) 725 FXX 421 Music Choice Pop Hits 24 Telemundo (WWSI, Phila.) 733 NFL Network 422 Music Choice Party Favorites 25 WTVE 965 Chalfont Borough Gov. -

XFINITY Channel Lineup We’Ve Organized All Your Channels by Service Level
2C-307 The New XFINITY Channel Lineup We’ve organized all your channels by service level. So you can find what you want, when you want it. The New XFINITY Channel Lineup. It’s the faster way to find what you’re looking for. For more info, visit www.xfinity.com Prince George’s County, MD – Efective November 1, 2015 LIMITED BASIC LIMITED BASIC LIMITED BASIC LIMITED BASIC SD HD CHANNEL NAME SD HD CHANNEL NAME SD HD CHANNEL NAME SD HD CHANNEL NAME WMDO-47 (uniMàs) 24 941 C-SPAN 23 Jewelry TV 200 WDCA Movies! 15/563 795 Washington DC WDCA-20 (MY) 104 942 C-SPAN2 184 Jewelry TV 20 810 Washington DC 269/559 WMPT V-me 287 Daystar 190 Leased Access WMPT-22 (PBS) 201 WDCW Antenna TV 22 812 72 Educational Access 76 Local Origination Annapolis 206 WDCW This TV 73 Educational Access 279 MHz Arirang 275 WNVC Bon-China WDCW-50 (CW) 3 803 MHz CCTV Washington DC 294 The Word Network 74 Educational Access 276 Documentary WPXW-66 (ION) 75 Educational Access 266 WETA Kids 16 813 273 MHz CCTV News Washington DC 265 WETA UK 77 Educational Access WQAW-20 (Azteca 278 MHz CNC World 198/568 WETA-26 (PBS) America) 78 Educational Access 26 800 277 MHz France 24 Washington DC 208 WRC Cozi TV 96 Educational Access WFDC-14 (Univision) 272 MHz NHK World TV 14/561 794 WRC-4 (NBC) Washington DC 4 804 89/283 EVINE Live Washington DC 274 MHz RT WHUT-32 (PBS) 19 802 291 799 EWTN Washington DC 197 WTTG Buzzr 280 MHz teleSUR 69 Gov’t Access WJLA Live Well WTTG-5 (FOX) 205 5 805 271 MHz Worldview Network Washington DC 70 Gov’t Access 268 MPT2 204 WJLA MeTV 207 WUSA Bounce TV 71 -

Lbi Tv Channel Guide
BROADCAST / LOCAL CHANNELS SUMMER 2015 SD HD 22nd & Blvd ABC (WPVI, Phila.) 6 906 ABC 7 (WABC, NY) 7 807 Surf City CBS 2 (WCBS, NY) 2 802 609-494-0200 CBS 3 (KYW, Phila.) 256 903 CW 11Stay (WPIX, connected NY) with11 the 811 CW Philly 57 (WPSG, Phila.) 254 911 FREE FoxLBI 29 (WTXF, Region Phila.) on the Southern16 905 Fox 5 (WNYW, NY) 5 805 Gov, Edu,Ocean Local County Access Chamber19 - 22 CHANNEL ION Televisionof Commerce (WPXN, NY) W ebsite18 799 BREAKFAST, LUNCH visitLBIregChannelion.co m190 GUIDE AND DINNER LBITV.com Anytime Begins 7/3/15 TAKE- OUT 24/7: FOOD • FASHION • FUN & MORE CATERING HEART-HEALTHY My 9 (WWOR, NY) 9 809 FAMILY-FRIENDLY NBC 10 (WCAU, Phila.) 253 910 NBC 4 (WNBC, NY) 4 804 LARGE SELECTION NJTV (PBS, NJ) 23, 261 800 OF GLUTEN-FREE ITEMS PHL 17 (WPHL,Celebrating Phila.) Our255 907 16 TIME CHOWDERFEST AWARD WINNER Weather Channel 39,101 815 OPEN DAILY 8AM YEAR ROUND WHYY Centennial(PBS Phila) Summer24 812 605 L.B. BLVD, SHIP BOTTOM609-494-7333 WHYY2 (PBS Phila) 257 WLNYStop (CBS by NY our local) Visitor Center10 at810 WMCN (Atlantic City) 27 794 At Sink’R Swim Shops next to Blue Water Cafe WNET265 (PBS,NY) W. 9th St., Ship Bottom13 813 WNETK (PBS NY Kids) 259 ON TV, ONLINE, ON MOBILE Y Info(609) ( PBS, Phila.) 494-7211 258 See theNow award-winning on LBI TV: AChamberward-winning of Commerce videoChamber series onof LBITVCommerce 190 and TV LBITV.com Series LBITV.com Anytime T-shirts•Sweatshirts•Hats Custom Screen Printing & Embroidery 11205 LB Blvd•Haven Beach 609-492-1171 ChicksLBI NJ ExcellenceNew Jersey in Tourism Award Winner! Excellence in Tourism FOLDAirs 24 hours daily on LBI TV 190 Award Winner! July 3 - Labor Day & Chowderfest Oct. -

Telecommunications Info & FAQ Sheet
Ocean Pines Association Telecommunications Info & FAQ Sheet (Updated Nov. 2020) First, let us outline what Telecom services are available to Ocean Pines residents and then we’ll try to answer some common questions in our FAQ section below. Disclaimer: All content and web links in this document are subject to change. 1. Options for television service? Traditional ‘Cable’ TV: Mediacom presently offers its Xtreme cable television service to all members throughout the community. Comcast is presently building out their network in Ocean Pines and will be offering their Xfinity cable television service. Roughly half of the community can now order services from Comcast and the company expects to complete installation to all sections of Ocean Pines by spring 2021. Both providers offer various levels of TV service, including premium movie channels and sports packages, as well as bundles that include TV, phone, and internet services. • To inquire about Mediacom TV services, visit: www.mediacomcable.com/products/television • To inquire about Comcast TV services, visit: www.xfinity.com/learn/digital-cable-tv ‘Satellite’ TV Satellite TV service is available in Ocean Pines from Dish Network and DirectTV with one major caveat: There must be a clear line-of-sight from the satellite dish installed on your property to the southwestern sky. With all the tall trees surrounding homes in our community, this service type is not a practical choice for many members. • To inquire about Dish Network services, visit: www.dish.com • To inquire about DirectTV services, visit: www.att.com/directv Free ‘Over-the-Air’ TV: TV channel reception via over-the-air (OTA) broadcasts is limited in our area. -

FCC-11-4A1.Pdf
Federal Communications Commission FCC 11-4 Before the Federal Communications Commission Washington, D.C. 20554 In the Matter of ) ) Applications of Comcast Corporation, ) MB Docket No. 10-56 General Electric Company ) and NBC Universal, Inc. ) ) For Consent to Assign Licenses and ) Transfer Control of Licensees ) ) MEMORANDUM OPINION AND ORDER Adopted: January 18, 2011 Released: January 20, 2011 By the Commission: Chairman Genachowski and Commissioner Clyburn issuing separate statements, Commissioners McDowell and Baker concurring and issuing a joint statement, Commissioner Copps dissenting and issuing a statement. TABLE OF CONTENTS Heading Paragraph # I. INTRODUCTION.................................................................................................................................. 1 II. DESCRIPTION OF THE PARTIES ...................................................................................................... 9 A. Comcast Corporation ....................................................................................................................... 9 B. General Electric Company............................................................................................................. 12 C. NBC Universal, Inc........................................................................................................................ 13 III. THE PROPOSED TRANSACTION.................................................................................................... 16 A. Description.................................................................................................................................... -

Broadband-Final-Report-2005.Pdf
Southern Maryland Broadband Study CCG Consulting, Inc. Table of Contents Page Overview of the Project.................................................................................................................4 Executive Summary.......................................................................................................................6 Section I – Needs Assessment........................................................................................................9 A. Surveys and Interviews ...........................................................................................9 B. Mapping Broadband Availability..........................................................................16 1. Calvert County Maps ......................................................................................20 2. Charles County Maps......................................................................................25 3. St. Mary’s Maps..............................................................................................30 C. Interviews with Incumbent Providers ..................................................................39 D. Broadband Products and Prices ...........................................................................44 E. Business Market Data...........................................................................................52 Section II – Industry Analysis.....................................................................................................56 A. Overview of the Communications Industry..........................................................56 -

Comcast Corporation
fact sheet Comcast Corporation overview Comcast Corporation is the nation’s leading provider of cable, entertainment and communications products and services, with 24.2 million cable customers, 12.1 million high-speed Internet customers and 3.0 million voice customers. Comcast is principally involved in the development, management and operation of broadband cable networks and in the delivery of programming content.* products and Comcast provides a wide variety of consumer products and services: services Video – Comcast is the nation’s largest video provider offering interactive services packed with the best content on Digital Cable, video on demand and high-defi nition television. Online – Comcast offers the best content, reliable service and faster speeds. Voice – Comcast’s IP-enabled Digital Voice service offers consumers the quality they expect in a phone service combined with new interactive features for a low price. Comcast Business Services – Comcast recently announced that it is providing phone, Internet and video services to small and medium size business customers across its national footprint. Comcast Interactive Media (CIM) – develops and operates Comcast’s Internet businesses focused on entertainment, information and communication, including Comcast.net, Ziddio, thePlatform and GameInvasion.net. content The Company’s content networks and investments include: networks and investments • Comcast Programming Group – E! Entertainment Television, Style Network, The Golf Channel, VERSUS, G4, AZN Television, PBS KIDS Sprout, TV One