Yes, SAS Can Do! Manage External Files with SAS Programming
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Copy — Copy file from Disk Or URL
Title stata.com copy — Copy file from disk or URL Syntax Description Options Remarks and examples Also see Syntax copy filename1 filename2 , options filename1 may be a filename or a URL. filename2 may be the name of a file or a directory. If filename2 is a directory name, filename1 will be copied to that directory. filename2 may not be a URL. Note: Double quotes may be used to enclose the filenames, and the quotes must be used if the filename contains embedded blanks. options Description public make filename2 readable by all text interpret filename1 as text file and translate to native text format replace may overwrite filename2 replace does not appear in the dialog box. Description copy copies filename1 to filename2. Options public specifies that filename2 be readable by everyone; otherwise, the file will be created according to the default permissions of your operating system. text specifies that filename1 be interpreted as a text file and be translated to the native form of text files on your computer. Computers differ on how end-of-line is recorded: Unix systems record one line-feed character, Windows computers record a carriage-return/line-feed combination, and Mac computers record just a carriage return. text specifies that filename1 be examined to determine how it has end-of-line recorded and that the line-end characters be switched to whatever is appropriate for your computer when the copy is made. There is no reason to specify text when copying a file already on your computer to a different location because the file would already be in your computer’s format. -

Windows Command Prompt Cheatsheet
Windows Command Prompt Cheatsheet - Command line interface (as opposed to a GUI - graphical user interface) - Used to execute programs - Commands are small programs that do something useful - There are many commands already included with Windows, but we will use a few. - A filepath is where you are in the filesystem • C: is the C drive • C:\user\Documents is the Documents folder • C:\user\Documents\hello.c is a file in the Documents folder Command What it Does Usage dir Displays a list of a folder’s files dir (shows current folder) and subfolders dir myfolder cd Displays the name of the current cd filepath chdir directory or changes the current chdir filepath folder. cd .. (goes one directory up) md Creates a folder (directory) md folder-name mkdir mkdir folder-name rm Deletes a folder (directory) rm folder-name rmdir rmdir folder-name rm /s folder-name rmdir /s folder-name Note: if the folder isn’t empty, you must add the /s. copy Copies a file from one location to copy filepath-from filepath-to another move Moves file from one folder to move folder1\file.txt folder2\ another ren Changes the name of a file ren file1 file2 rename del Deletes one or more files del filename exit Exits batch script or current exit command control echo Used to display a message or to echo message turn off/on messages in batch scripts type Displays contents of a text file type myfile.txt fc Compares two files and displays fc file1 file2 the difference between them cls Clears the screen cls help Provides more details about help (lists all commands) DOS/Command Prompt help command commands Source: https://technet.microsoft.com/en-us/library/cc754340.aspx. -
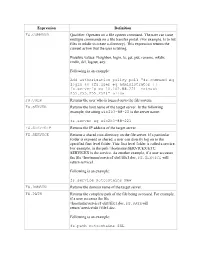
Expression Definition FS.COMMAND Qualifier. Operates on a File System Command
Expression Definition FS.COMMAND Qualifier. Operates on a file system command. The user can issue multiple commands on a file transfer portal. (For example, ls to list files or mkdir to create a directory). This expression returns the current action that the user is taking. Possible values: Neighbor, login, ls, get, put, rename, mkdir, rmdir, del, logout, any. Following is an example: Add authorization policy pol1 “fs.command eq login && (fs.user eq administrator || fs.serverip eq 10.102.88.221 –netmask 255.255.255.252)” allow FS.USER Returns the user who is logged on to the file system. FS.SERVER Returns the host name of the target server. In the following example, the string win2k3-88-22 is the server name: fs.server eq win2k3-88-221 FS.SERVERIP Returns the IP address of the target server. FS.SERVICE Returns a shared root directory on the file server. If a particular folder is exposed as shared, a user can directly log on to the specified first level folder. This first level folder is called a service. For example, in the path \\hostname\SERVICEX\ETC, SERVICEX is the service. As another example, if a user accesses the file \\hostname\service1\dir1\file1.doc, FS.SERVICE will return service1. Following is an example: fs.service notcontains New FS.DOMAIN Returns the domain name of the target server. FS.PATH Returns the complete path of the file being accessed. For example, if a user accesses the file \\hostname\service1\dir1\file1.doc, FS.PATHwill return \service\dir1\file1.doc. Following is an example: fs.path notcontains SSL Expression Definition FS.FILE Returns the name of the file being accessed. -

Mac Keyboard Shortcuts Cut, Copy, Paste, and Other Common Shortcuts
Mac keyboard shortcuts By pressing a combination of keys, you can do things that normally need a mouse, trackpad, or other input device. To use a keyboard shortcut, hold down one or more modifier keys while pressing the last key of the shortcut. For example, to use the shortcut Command-C (copy), hold down Command, press C, then release both keys. Mac menus and keyboards often use symbols for certain keys, including the modifier keys: Command ⌘ Option ⌥ Caps Lock ⇪ Shift ⇧ Control ⌃ Fn If you're using a keyboard made for Windows PCs, use the Alt key instead of Option, and the Windows logo key instead of Command. Some Mac keyboards and shortcuts use special keys in the top row, which include icons for volume, display brightness, and other functions. Press the icon key to perform that function, or combine it with the Fn key to use it as an F1, F2, F3, or other standard function key. To learn more shortcuts, check the menus of the app you're using. Every app can have its own shortcuts, and shortcuts that work in one app may not work in another. Cut, copy, paste, and other common shortcuts Shortcut Description Command-X Cut: Remove the selected item and copy it to the Clipboard. Command-C Copy the selected item to the Clipboard. This also works for files in the Finder. Command-V Paste the contents of the Clipboard into the current document or app. This also works for files in the Finder. Command-Z Undo the previous command. You can then press Command-Shift-Z to Redo, reversing the undo command. -

Powerview Command Reference
PowerView Command Reference TRACE32 Online Help TRACE32 Directory TRACE32 Index TRACE32 Documents ...................................................................................................................... PowerView User Interface ............................................................................................................ PowerView Command Reference .............................................................................................1 History ...................................................................................................................................... 12 ABORT ...................................................................................................................................... 13 ABORT Abort driver program 13 AREA ........................................................................................................................................ 14 AREA Message windows 14 AREA.CLEAR Clear area 15 AREA.CLOSE Close output file 15 AREA.Create Create or modify message area 16 AREA.Delete Delete message area 17 AREA.List Display a detailed list off all message areas 18 AREA.OPEN Open output file 20 AREA.PIPE Redirect area to stdout 21 AREA.RESet Reset areas 21 AREA.SAVE Save AREA window contents to file 21 AREA.Select Select area 22 AREA.STDERR Redirect area to stderr 23 AREA.STDOUT Redirect area to stdout 23 AREA.view Display message area in AREA window 24 AutoSTOre .............................................................................................................................. -

KEYBOARD SHORTCUTS (Windows)
KEYBOARD SHORTCUTS (Windows) Note: For Mac users, please substitute the Command key for the Ctrl key. This substitution with work for the majority of commands _______________________________________________________________________ General Commands Navigation Windows key + D Desktop to foreground Context menu Right click Alt + underlined letter Menu drop down, Action selection Alt + Tab Toggle between open applications Alt, F + X or Alt + F4 Exit application Alt, Spacebar + X Maximize window Alt, Spacebar + N Minimize window Ctrl + W Closes window F2 Renames a selected file or folder Open Programs To open programs from START menu: Create a program shortcut and drop it into START menu To open programs/files on Desktop: Select first letter, and then press Enter to open Dialog Boxes Enter Selects highlighted button Tab Selects next button Arrow keys Selects next (>) or previous button (<) Shift + Tab Selects previous button _______________________________________________________________________ Microsoft Word Formatting Ctrl + P Print Ctrl + S Save Ctrl + Z Undo Ctrl + Y Redo CTRL+B Make text bold CTRL+I Italicize CTRL+U Underline Ctrl + C Copy Ctrl + V Paste Ctrl + X Copy + delete Shift + F3 Change case of letters Ctrl+Shift+> Increase font size Ctrl+Shift+< Decrease font size Highlight Text Shift + Arrow Keys Selects one letter at a time Shift + Ctrl + Arrow keys Selects one word at a time Shift + End or Home Selects lines of text Change or resize the font CTRL+SHIFT+ > Increase the font size 1 KEYBOARD SHORTCUTS (Windows) CTRL+SHIFT+ < -

Learning Objectives ECHO Commands. Command. 10. Explain
. SA Learning Objectives After completing this chapter you will be able to: 1. List commands used in batch files. 2. List and explain batch file rules. 3. Use a batch file with a shortcut. 3. Explore the function of the REM, 4. Use the SHIFT command to move param- ECHO commands. eters. 4. Explain the use of batch files with shortcuts. 5. Use the IF command with strings for condi- 5. Explain the purpose and function of the tional processing. GOTO command. 6. Test for null values in a batch file. 6. Explain the purpose and function of the 7. Use the IF EXIST /IF SHIFT command. test for the existence of a file or a 7. Explain the purpose and function of the IF subdirectory. command. 8. Use the SET command. 8. Explain the purpose and function of the IF 9. Use the environment and environmental EXIST /IF variables in batch files. 9. Explain the purpose and function of the IF 10. Use the IF ERRORLEVEL command ERRORLEVEL command. XCOpy to write a batch file for testing exit 10. Explain the purpose and function of writing codes. programs. 11. Use the FOR...IN...OO command for repeti- 11. Explain the purpose and function of the tive processing. environment and environmental variables. 12. Use the CALL command in a batch file. 12. Explain the use of the SET command. 13. Explain the purpose and function of the Chapter Overview FOR...IN...OO command. You learned in Chapter 10 how to write simple 14. Explain the purpose and function of the batch files and use replaceable parameters. -

Timestamp Changes in Case of Copy Command (Win7, Win10)
Timestamp changes in case of copy command (Win7, Win10) Investigating timestamp differences between Windows 7 and Windows 10. I intended to figure out how MACB timestamps of the original and the newly created files are changing during a file copy in Windows. I also checked the differences between the results of the GUI based copy and paste method and the command line based copy command. I compared the changes in case of an in-volume copy and in case of copying to a different volume as well. Tools: These are the tools that were used during my investigation. • Microsoft Windows 10 64-bit v10.0.17134.345 • Microsoft Windows 7 Enterprise SP1 • FTK Imager 4.2 - for creating images about the drives and to save the MFT file • analyzeMFT.py - for MFT parsing (https://github.com/dkovar/analyzeMFT) MACB An NTFS volume stores 8 different timestamps for a single file. These timestamps are the followings: • Modified • Accessed • Changed (Info Entry date change) • Birth (file creation time) All of these 4 information snippets are stored in the $STANDARD_INFO and in the $FILE_NAME as well. The difference between the two attributes: • $STANDARD_INFO: can be modified by user level processes. Therefore it can be altered by anti-forensics utilities. • $FILE_NAME: can only be modified by the system kernel. No known anti-forensics tools can modify it. Method of investigation 1) I generated two files in an NTFS volume. 2) Copied one of the files with copy paste and the other one with copy command from command line into a different directory. 3) Generated two files in an NTFS volume to test out-of-volume copy. -

Linux Networking 101
The Gorilla ® Guide to… Linux Networking 101 Inside this Guide: • Discover how Linux continues its march toward world domination • Learn basic Linux administration tips • See how easy it can be to build your entire network on a Linux foundation • Find out how Cumulus Linux is your ticket to networking freedom David M. Davis ActualTech Media Helping You Navigate The Technology Jungle! In Partnership With www.actualtechmedia.com The Gorilla Guide To… Linux Networking 101 Author David M. Davis, ActualTech Media Editors Hilary Kirchner, Dream Write Creative, LLC Christina Guthrie, Guthrie Writing & Editorial, LLC Madison Emery, Cumulus Networks Layout and Design Scott D. Lowe, ActualTech Media Copyright © 2017 by ActualTech Media. All rights reserved. No portion of this book may be reproduced or used in any manner without the express written permission of the publisher except for the use of brief quotations. The information provided within this eBook is for general informational purposes only. While we try to keep the information up- to-date and correct, there are no representations or warranties, express or implied, about the completeness, accuracy, reliability, suitability or availability with respect to the information, products, services, or related graphics contained in this book for any purpose. Any use of this information is at your own risk. ActualTech Media Okatie Village Ste 103-157 Bluffton, SC 29909 www.actualtechmedia.com Entering the Jungle Introduction: Six Reasons You Need to Learn Linux ....................................................... 7 1. Linux is the future ........................................................................ 9 2. Linux is on everything .................................................................. 9 3. Linux is adaptable ....................................................................... 10 4. Linux has a strong community and ecosystem ........................... 10 5. -

TB-1052 Digital Video Systems
IRIS TECHNICAL BULLETIN TB-1052 Digital Video Systems Subject: Installing and Running Check Disk on XP Embedded Systems Hardware: TotalVision-TS Software: IRIS DVS XPe Ver. 11.04 and Earlier (Including FX and non-FX Units) Release Date: 12/22/08 SUMMARY IRIS DVS units initially produced prior to January 1, 2009 may not have complete support for running chkdsk.exe even though the chkdsk.exe file exist in the Windows/System32 directory. This Technical Bulletin describes how to install and run the Check Disk (ChkDsk) utility to minimize file corruption problems and potential RAW Disk failures. INSTALLING SOFTWARE Several additional files are needed to be installed on the DVS hard drive. You can get a copy of these files at the IRIS Web Service Site www.SecurityTexas.com/service. Download the “Check Disk Upgrade” package and follow the instructions in the ReadMe file of that zip file on how to upgrade the files on the DVS. Once the files are copied to the hard drive, highlight the file “EVENTVWR.MSC” and then select “File- >Pin to Start Menu” to provide an easy way to access the Event Viewer. After the required software has been installed run Windows File Explorer and select the C:\BankIRIS_NT directory. Double-click on the AUTOCHECK.REG file. Answer YES in response to the two prompts to update the registry. Expert Mode: To verify that the registry changes were done you can select “Start->Run” and type in “RegEdit.exe” to run the Registry Editor. Select the key “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Sesion Manager”. Select the key "BootExecute". -

Niagara Networking and Connectivity Guide
Technical Publications Niagara Networking & Connectivity Guide Tridium, Inc. 3951 Westerre Parkway • Suite 350 Richmond, Virginia 23233 USA http://www.tridium.com Phone 804.747.4771 • Fax 804.747.5204 Copyright Notice: The software described herein is furnished under a license agreement and may be used only in accordance with the terms of the agreement. © 2002 Tridium, Inc. All rights reserved. This document may not, in whole or in part, be copied, photocopied, reproduced, translated, or reduced to any electronic medium or machine-readable form without prior written consent from Tridium, Inc., 3951 Westerre Parkway, Suite 350, Richmond, Virginia 23233. The confidential information contained in this document is provided solely for use by Tridium employees, licensees, and system owners. It is not to be released to, or reproduced for, anyone else; neither is it to be used for reproduction of this control system or any of its components. All rights to revise designs described herein are reserved. While every effort has been made to assure the accuracy of this document, Tridium shall not be held responsible for damages, including consequential damages, arising from the application of the information given herein. The information in this document is subject to change without notice. The release described in this document may be protected by one of more U.S. patents, foreign patents, or pending applications. Trademark Notices: Metasys is a registered trademark, and Companion, Facilitator, and HVAC PRO are trademarks of Johnson Controls Inc. Black Box is a registered trademark of the Black Box Corporation. Microsoft and Windows are registered trademarks, and Windows 95, Windows NT, Windows 2000, and Internet Explorer are trademarks of Microsoft Corporation. -

Networking TCP/IP Troubleshooting 7.1
IBM IBM i Networking TCP/IP troubleshooting 7.1 IBM IBM i Networking TCP/IP troubleshooting 7.1 Note Before using this information and the product it supports, read the information in “Notices,” on page 79. This edition applies to IBM i 7.1 (product number 5770-SS1) and to all subsequent releases and modifications until otherwise indicated in new editions. This version does not run on all reduced instruction set computer (RISC) models nor does it run on CISC models. © Copyright IBM Corporation 1997, 2008. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents TCP/IP troubleshooting ........ 1 Server table ............ 34 PDF file for TCP/IP troubleshooting ...... 1 Checking jobs, job logs, and message logs .. 63 Troubleshooting tools and techniques ...... 1 Verifying that necessary jobs exist .... 64 Tools to verify your network structure ..... 1 Checking the job logs for error messages Netstat .............. 1 and other indication of problems .... 65 Using Netstat from a character-based Changing the message logging level on job interface ............. 2 descriptions and active jobs ...... 65 Using Netstat from System i Navigator .. 4 Other job considerations ....... 66 Ping ............... 7 Checking for active filter rules ...... 67 Using Ping from a character-based interface 7 Verifying system startup considerations for Using Ping from System i Navigator ... 10 networking ............ 68 Common error messages ....... 13 Starting subsystems ........ 68 PING parameters ......... 14 Starting TCP/IP .......... 68 Trace route ............ 14 Starting interfaces ......... 69 Using trace route from a character-based Starting servers .......... 69 interface ............ 15 Timing considerations ........ 70 Using trace route from System i Navigator 15 Varying on lines, controllers, and devices .