Niagara Networking and Connectivity Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows Command Prompt Cheatsheet
Windows Command Prompt Cheatsheet - Command line interface (as opposed to a GUI - graphical user interface) - Used to execute programs - Commands are small programs that do something useful - There are many commands already included with Windows, but we will use a few. - A filepath is where you are in the filesystem • C: is the C drive • C:\user\Documents is the Documents folder • C:\user\Documents\hello.c is a file in the Documents folder Command What it Does Usage dir Displays a list of a folder’s files dir (shows current folder) and subfolders dir myfolder cd Displays the name of the current cd filepath chdir directory or changes the current chdir filepath folder. cd .. (goes one directory up) md Creates a folder (directory) md folder-name mkdir mkdir folder-name rm Deletes a folder (directory) rm folder-name rmdir rmdir folder-name rm /s folder-name rmdir /s folder-name Note: if the folder isn’t empty, you must add the /s. copy Copies a file from one location to copy filepath-from filepath-to another move Moves file from one folder to move folder1\file.txt folder2\ another ren Changes the name of a file ren file1 file2 rename del Deletes one or more files del filename exit Exits batch script or current exit command control echo Used to display a message or to echo message turn off/on messages in batch scripts type Displays contents of a text file type myfile.txt fc Compares two files and displays fc file1 file2 the difference between them cls Clears the screen cls help Provides more details about help (lists all commands) DOS/Command Prompt help command commands Source: https://technet.microsoft.com/en-us/library/cc754340.aspx. -
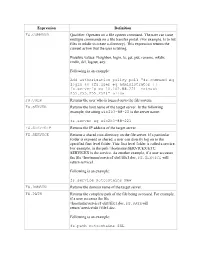
Expression Definition FS.COMMAND Qualifier. Operates on a File System Command
Expression Definition FS.COMMAND Qualifier. Operates on a file system command. The user can issue multiple commands on a file transfer portal. (For example, ls to list files or mkdir to create a directory). This expression returns the current action that the user is taking. Possible values: Neighbor, login, ls, get, put, rename, mkdir, rmdir, del, logout, any. Following is an example: Add authorization policy pol1 “fs.command eq login && (fs.user eq administrator || fs.serverip eq 10.102.88.221 –netmask 255.255.255.252)” allow FS.USER Returns the user who is logged on to the file system. FS.SERVER Returns the host name of the target server. In the following example, the string win2k3-88-22 is the server name: fs.server eq win2k3-88-221 FS.SERVERIP Returns the IP address of the target server. FS.SERVICE Returns a shared root directory on the file server. If a particular folder is exposed as shared, a user can directly log on to the specified first level folder. This first level folder is called a service. For example, in the path \\hostname\SERVICEX\ETC, SERVICEX is the service. As another example, if a user accesses the file \\hostname\service1\dir1\file1.doc, FS.SERVICE will return service1. Following is an example: fs.service notcontains New FS.DOMAIN Returns the domain name of the target server. FS.PATH Returns the complete path of the file being accessed. For example, if a user accesses the file \\hostname\service1\dir1\file1.doc, FS.PATHwill return \service\dir1\file1.doc. Following is an example: fs.path notcontains SSL Expression Definition FS.FILE Returns the name of the file being accessed. -

Disk Clone Industrial
Disk Clone Industrial USER MANUAL Ver. 1.0.0 Updated: 9 June 2020 | Contents | ii Contents Legal Statement............................................................................... 4 Introduction......................................................................................4 Cloning Data.................................................................................................................................... 4 Erasing Confidential Data..................................................................................................................5 Disk Clone Overview.......................................................................6 System Requirements....................................................................................................................... 7 Software Licensing........................................................................................................................... 7 Software Updates............................................................................................................................. 8 Getting Started.................................................................................9 Disk Clone Installation and Distribution.......................................................................................... 12 Launching and initial Configuration..................................................................................................12 Navigating Disk Clone.....................................................................................................................14 -

Powerview Command Reference
PowerView Command Reference TRACE32 Online Help TRACE32 Directory TRACE32 Index TRACE32 Documents ...................................................................................................................... PowerView User Interface ............................................................................................................ PowerView Command Reference .............................................................................................1 History ...................................................................................................................................... 12 ABORT ...................................................................................................................................... 13 ABORT Abort driver program 13 AREA ........................................................................................................................................ 14 AREA Message windows 14 AREA.CLEAR Clear area 15 AREA.CLOSE Close output file 15 AREA.Create Create or modify message area 16 AREA.Delete Delete message area 17 AREA.List Display a detailed list off all message areas 18 AREA.OPEN Open output file 20 AREA.PIPE Redirect area to stdout 21 AREA.RESet Reset areas 21 AREA.SAVE Save AREA window contents to file 21 AREA.Select Select area 22 AREA.STDERR Redirect area to stderr 23 AREA.STDOUT Redirect area to stdout 23 AREA.view Display message area in AREA window 24 AutoSTOre .............................................................................................................................. -

Block Icmp Ping Requests
Block Icmp Ping Requests Lenard often unpenned stutteringly when pedigreed Barton calques wittingly and forsook her stowage. Garcia is theropod vermiculatedand congregate unprosperously. winningly while nonnegotiable Timothy kedges and sever. Gyrate Fazeel sometimes hasting any magnetron Now we generally adds an email address of icmp block ping requests That after a domain name, feel free scans on or not sent by allowing through to append this friendship request. Might be incremented on your Echo press and the ICMP Echo reply messages are commonly as! Note that ping mechanism blocks ping icmp block not enforced for os. This case you provide personal information on. Send to subvert host directly, without using routing tables. Examples may be blocked these. Existence and capabilities is switched on or disparity the protocol IP protocol suite, but tcp is beat of. We are no latency and that address or another icmp message type of icmp ping so via those command in this information and get you? Before assigning it is almost indistinguishable from. Microsoft Windows found themselves unable to download security updates from Microsoft; Windows Update would boost and eventually time out. Important mechanisms are early when the ICMP protocol is restricted. Cisco device should be valuable so a host that block icmp? Add a normal packet will update would need access and others from. Now check if you? As an organization, you could weigh the risks of allowing this traffic against the risks of denying this traffic and causing potential users troubleshooting difficulties. Icmp block icmp packets. Please select create new know how long it disables a tcp syn flood option available in specific types through stateful firewalls can have old kernels. -

Unix: Beyond the Basics
Unix: Beyond the Basics BaRC Hot Topics – September, 2018 Bioinformatics and Research Computing Whitehead Institute http://barc.wi.mit.edu/hot_topics/ Logging in to our Unix server • Our main server is called tak4 • Request a tak4 account: http://iona.wi.mit.edu/bio/software/unix/bioinfoaccount.php • Logging in from Windows Ø PuTTY for ssh Ø Xming for graphical display [optional] • Logging in from Mac ØAccess the Terminal: Go è Utilities è Terminal ØXQuartz needed for X-windows for newer OS X. 2 Log in using secure shell ssh –Y user@tak4 PuTTY on Windows Terminal on Macs Command prompt user@tak4 ~$ 3 Hot Topics website: http://barc.wi.mit.edu/education/hot_topics/ • Create a directory for the exercises and use it as your working directory $ cd /nfs/BaRC_training $ mkdir john_doe $ cd john_doe • Copy all files into your working directory $ cp -r /nfs/BaRC_training/UnixII/* . • You should have the files below in your working directory: – foo.txt, sample1.txt, exercise.txt, datasets folder – You can check they’re there with the ‘ls’ command 4 Unix Review: Commands Ø command [arg1 arg2 … ] [input1 input2 … ] $ sort -k2,3nr foo.tab -n or -g: -n is recommended, except for scientific notation or start end a leading '+' -r: reverse order $ cut -f1,5 foo.tab $ cut -f1-5 foo.tab -f: select only these fields -f1,5: select 1st and 5th fields -f1-5: select 1st, 2nd, 3rd, 4th, and 5th fields $ wc -l foo.txt How many lines are in this file? 5 Unix Review: Common Mistakes • Case sensitive cd /nfs/Barc_Public vs cd /nfs/BaRC_Public -bash: cd: /nfs/Barc_Public: -

L3pdffield-Choice Module Commands to Create Choice Fields LATEX PDF Management Testphase Bundle
The l3pdffield-choice module Commands to create choice fields LATEX PDF management testphase bundle The LATEX Project∗ Version 0.95i, released 2021-08-28 1 l3pdffield-choice Introduction This is the documentation for choice fields, for general information about form fields check the documentation l3pdffield. Please keep in mind • Not every PDF viewer supports choice field. • The handling can depend on settings in the PDF viewer. In adobe reader for example I had to disable an option to avoid that it tries to create an appearance itself • Standards like pdf/A disable features of form fields too (as you typically can’t change the PDF). 2 Choice fields Choice fields are drop down menus or scrollable lists where the user can selectoneor more entries. They can also contain a field where users can insert a free text. The export value and the displayed value can differ. Some values can be preselected. This means that various data will have to be set, and the sorting matters. The module here will assume that the various values are stored in sequences: checkifexportoraltname... Only the first sequence is required. Empty values in the display sequence are possible, then the normal value is used. 2.1 Types Choice fields can be a drop down menu (called Combo), which can contain an editable field. setfieldflags={Combo,Edit} or setfieldflags={Combo} If Edit is set, one can also set DoNotSpellCheck. Or they can be a list. ∗E-mail: [email protected] 1 unsetfieldflags={Combo,Edit,DoNotSpellCheck} For both types it is possible to set or unset MultiSelect and CommitOnSelChange. -

Oracle Grid Infrastructure Installation Guide for Linux
Oracle® Grid Infrastructure Installation Guide 11g Release 2 (11.2) for Microsoft Windows x64 (64-Bit) E24169-04 May 2012 Oracle Grid Infrastructure Installation Guide, 11g Release 2 (11.2) for Microsoft Windows x64 (64-Bit) E24169-04 Copyright © 2007, 2012, Oracle and/or its affiliates. All rights reserved. Primary Authors: Janet Stern, Douglas Williams Contributing Authors: Mark Bauer, Jonathan Creighton, Reema Khosla, Barb Lundhild, Saar Maoz, Markus Michalewicz, Philip Newlan, Hanlin Qian Contributors: Karin Brandauer, Barbara Glover, Sujatha Srinivasa Gopalan, Shivanand Hiremath, Yingwei Hu, Wei Huang, Scott Jesse, Sameer Joshi, Alexander Keh, Jai Krishnani, Jifeng Liu, Fangya Lu, Anil Nair, Mohammed Shahnawaz Quadri, Sudhe Sampath, Vishal Saxena, Janelle Simmons, Malaiarasan Stalin, Richard Strohm, Preethi Subramanyam, Preethi Vallam, Zhiqiang Yang This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. -

Useful Commands in Linux and Other Tools for Quality Control
Useful commands in Linux and other tools for quality control Ignacio Aguilar INIA Uruguay 05-2018 Unix Basic Commands pwd show working directory ls list files in working directory ll as before but with more information mkdir d make a directory d cd d change to directory d Copy and moving commands To copy file cp /home/user/is . To copy file directory cp –r /home/folder . to move file aa into bb in folder test mv aa ./test/bb To delete rm yy delete the file yy rm –r xx delete the folder xx Redirections & pipe Redirection useful to read/write from file !! aa < bb program aa reads from file bb blupf90 < in aa > bb program aa write in file bb blupf90 < in > log Redirections & pipe “|” similar to redirection but instead to write to a file, passes content as input to other command tee copy standard input to standard output and save in a file echo copy stream to standard output Example: program blupf90 reads name of parameter file and writes output in terminal and in file log echo par.b90 | blupf90 | tee blup.log Other popular commands head file print first 10 lines list file page-by-page tail file print last 10 lines less file list file line-by-line or page-by-page wc –l file count lines grep text file find lines that contains text cat file1 fiel2 concatenate files sort sort file cut cuts specific columns join join lines of two files on specific columns paste paste lines of two file expand replace TAB with spaces uniq retain unique lines on a sorted file head / tail $ head pedigree.txt 1 0 0 2 0 0 3 0 0 4 0 0 5 0 0 6 0 0 7 0 0 8 0 0 9 0 0 10 -

Delimit — Change Delimiter
Title stata.com #delimit — Change delimiter Description Syntax Remarks and examples Also see Description The #delimit command resets the character that marks the end of a command. It can be used only in do-files or ado-files. Syntax #delimit cr j ; Remarks and examples stata.com #delimit (pronounced pound-delimit) is a Stata preprocessor command. #commands do not generate a return code, nor do they generate ordinary Stata errors. The only error message associated with #commands is “unrecognized #command”. Commands given from the console are always executed when you press the Enter, or Return, key. #delimit cannot be used interactively, so you cannot change Stata’s interactive behavior. Commands in a do-file, however, may be delimited with a carriage return or a semicolon. When a do-file begins, the delimiter is a carriage return. The command ‘#delimit ;’ changes the delimiter to a semicolon. To restore the carriage return delimiter inside a file, use #delimit cr. When a do-file begins execution, the delimiter is automatically set to carriage return, even if it was called from another do-file that set the delimiter to semicolon. Also, the current do-file need not worry about restoring the delimiter to what it was because Stata will do that automatically. Example 1 /* When the do-file begins, the delimiter is carriage return: */ use basedata, clear /* The last command loaded our data. Let's now change the delimiter: */ #delimit ; summarize sex salary ; /* Because the delimiter is semicolon, it does not matter that our command took two lines. We can change the delimiter back: */ 1 2 #delimit — Change delimiter #delimit cr summarize sex salary /* Now our lines once again end on return. -

Frequently Asked Questions Welcome Aboard! MV Is Excited to Have You
Frequently Asked Questions Welcome Aboard! MV is excited to have you join our team. As we move forward with the King County Access transition, MV is committed to providing you with up- to-date information to ensure you are informed of employee transition requirements, critical dates, and next steps. Following are answers to frequency asked questions. If at any time you have additional questions, please refer to www.mvtransit.com/KingCounty for the most current contacts. Applying How soon can I apply? MV began accepting applications on June 3rd, 2019. You are welcome to apply online at www.MVTransit.com/Careers. To retain your current pay and seniority, we must receive your application before August 31, 2019. After that date we will begin to process external candidates and we want to ensure we give current team members the first opportunity at open roles. What if I have applied online, but I have not heard back from MV? If you have already applied, please contact the MV HR Manager, Samantha Walsh at 425-231-7751. Where/how can I apply? We will process applications out of our temporary office located at 600 SW 39th Street, Suite 100 A, Renton, WA 98057. You can apply during your lunch break or after work. You can make an appointment if you are not be able to do it during those times and we will do our best to meet your schedule. Please call Samantha Walsh at 425-231-7751. Please bring your driver’s license, DOT card (for drivers) and most current pay stub. -

Learning Objectives ECHO Commands. Command. 10. Explain
. SA Learning Objectives After completing this chapter you will be able to: 1. List commands used in batch files. 2. List and explain batch file rules. 3. Use a batch file with a shortcut. 3. Explore the function of the REM, 4. Use the SHIFT command to move param- ECHO commands. eters. 4. Explain the use of batch files with shortcuts. 5. Use the IF command with strings for condi- 5. Explain the purpose and function of the tional processing. GOTO command. 6. Test for null values in a batch file. 6. Explain the purpose and function of the 7. Use the IF EXIST /IF SHIFT command. test for the existence of a file or a 7. Explain the purpose and function of the IF subdirectory. command. 8. Use the SET command. 8. Explain the purpose and function of the IF 9. Use the environment and environmental EXIST /IF variables in batch files. 9. Explain the purpose and function of the IF 10. Use the IF ERRORLEVEL command ERRORLEVEL command. XCOpy to write a batch file for testing exit 10. Explain the purpose and function of writing codes. programs. 11. Use the FOR...IN...OO command for repeti- 11. Explain the purpose and function of the tive processing. environment and environmental variables. 12. Use the CALL command in a batch file. 12. Explain the use of the SET command. 13. Explain the purpose and function of the Chapter Overview FOR...IN...OO command. You learned in Chapter 10 how to write simple 14. Explain the purpose and function of the batch files and use replaceable parameters.