Ch 7 Using ATTRIB, SUBST, XCOPY, DOSKEY, and the Text Editor
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Copy — Copy file from Disk Or URL
Title stata.com copy — Copy file from disk or URL Syntax Description Options Remarks and examples Also see Syntax copy filename1 filename2 , options filename1 may be a filename or a URL. filename2 may be the name of a file or a directory. If filename2 is a directory name, filename1 will be copied to that directory. filename2 may not be a URL. Note: Double quotes may be used to enclose the filenames, and the quotes must be used if the filename contains embedded blanks. options Description public make filename2 readable by all text interpret filename1 as text file and translate to native text format replace may overwrite filename2 replace does not appear in the dialog box. Description copy copies filename1 to filename2. Options public specifies that filename2 be readable by everyone; otherwise, the file will be created according to the default permissions of your operating system. text specifies that filename1 be interpreted as a text file and be translated to the native form of text files on your computer. Computers differ on how end-of-line is recorded: Unix systems record one line-feed character, Windows computers record a carriage-return/line-feed combination, and Mac computers record just a carriage return. text specifies that filename1 be examined to determine how it has end-of-line recorded and that the line-end characters be switched to whatever is appropriate for your computer when the copy is made. There is no reason to specify text when copying a file already on your computer to a different location because the file would already be in your computer’s format. -

Attachment D to Adm. Memo No. 004 INSTRUCTIONS FOR
Attachment D to Adm. Memo No. 004 INSTRUCTIONS FOR FORMATTING A DISKETTE Formatting is the preparation of diskettes for storage of information. There are several different versions of the format command that can be used. The version that you use depends upon the type of diskette and the type of disk drive in which the diskette is being formatted. In order for us to be able to read the Tuition Grant diskettes you send, the diskettes should be properly formatted. Below is a table that identifies the more commonly used diskette types and disk drive specifications. The correct version of the format command will appear in the row for your diskette type and drive type. The format command uses the parameter “d:” to indicate the disk drive designation. For example, your 5 ¼ drive may be the “A:” drive. Instead of typing “FORMAT D:”, replace the drive designation with “A:” and type “FORMAT A:”. To verify that the disks were formatted correctly, perform the CHKDSK command on the newly formatted diskette. The format for the CHKDSK command is “CHKDSK d:”. When the command returns the disk information, compare it to the information in the fourth column of the table that corresponds to your diskette type and disk drive.. If the “total disk space” numbers are the same, the diskette is formatted correctly. DISK TYPE DRIVE TYPE FORMAT COMMAND SPACE INFO. 5 ¼” DSDD DSDD FORMAT d: 362,496 bytes total disk space 5 ¼” DSDD HD FORMAT d: /T:40 /N:9 362,496 bytes total disk space 5 ¼” HD DSDD Cannot be formatted 5 ¼” HD HD FORMAT d: 1,213,952 bytes total disk space 3 ½” DSDD DSDD FORMAT d: 730,112 bytes total disk space 3 ½” DSDD HD FORMAT d: /T:80 /N:9 730,112 bytes total disk space 3 ½” HD DSDD Cannot be formatted 3 ½” HD HD FORMAT d: 1,457,664 bytes total disk space 3 ½” DSHD FORMAT d: 1,457,664 bytes total disk space. -

Windows Command Prompt Cheatsheet
Windows Command Prompt Cheatsheet - Command line interface (as opposed to a GUI - graphical user interface) - Used to execute programs - Commands are small programs that do something useful - There are many commands already included with Windows, but we will use a few. - A filepath is where you are in the filesystem • C: is the C drive • C:\user\Documents is the Documents folder • C:\user\Documents\hello.c is a file in the Documents folder Command What it Does Usage dir Displays a list of a folder’s files dir (shows current folder) and subfolders dir myfolder cd Displays the name of the current cd filepath chdir directory or changes the current chdir filepath folder. cd .. (goes one directory up) md Creates a folder (directory) md folder-name mkdir mkdir folder-name rm Deletes a folder (directory) rm folder-name rmdir rmdir folder-name rm /s folder-name rmdir /s folder-name Note: if the folder isn’t empty, you must add the /s. copy Copies a file from one location to copy filepath-from filepath-to another move Moves file from one folder to move folder1\file.txt folder2\ another ren Changes the name of a file ren file1 file2 rename del Deletes one or more files del filename exit Exits batch script or current exit command control echo Used to display a message or to echo message turn off/on messages in batch scripts type Displays contents of a text file type myfile.txt fc Compares two files and displays fc file1 file2 the difference between them cls Clears the screen cls help Provides more details about help (lists all commands) DOS/Command Prompt help command commands Source: https://technet.microsoft.com/en-us/library/cc754340.aspx. -

PGP Desktop for Mac OS X Quick Start Guide Version 10.0
PGP Desktop for Mac OS X Quick Start Guide Version 10.0 In addition, use PGP Desktop to: What is PGP Desktop? y Use part of your hard drive space as an encrypted virtual disk volume with its own drive letter. PGP Desktop provides comprehensive security for desktops Create protected Zip archives. and laptops, making it possible for enterprises, workgroups, y and individuals to protect sensitive information without y Completely destroy files and folders so that nothing can changing the existing IT infrastructure or disrupting work recover them. processes. This award winning, easy-to-use solution encrypts email, files, virtual volumes, and entire disks from a single New to PGP Desktop? desktop application. Use this step-by-step guide to get started. You will find that, The PGP Desktop family of applications have been combined with PGP Desktop, protecting your data will be as easy as into several bundles. turning a key in a lock. y PGP Desktop Professional includes PGP Desktop Email y This Quick Start Guide helps you install PGP Desktop and and PGP Whole Disk Encryption get started. y PGP Whole Disk Encryption includes PGP Whole Disk y The PGP Desktop User’s Guide provides more detailed Encryption information on PGP Desktop. In it, you will learn what a keypair is, why you might want to create one, how to create one, and how to exchange keys with others so you can encrypt your own data and share data securely with Contents others. y What is PGP Desktop? (page 1) Note: A PGP Desktop license provides you with access to y New to PGP Desktop? (page 1) a certain set of PGP Desktop features. -
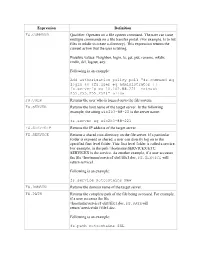
Expression Definition FS.COMMAND Qualifier. Operates on a File System Command
Expression Definition FS.COMMAND Qualifier. Operates on a file system command. The user can issue multiple commands on a file transfer portal. (For example, ls to list files or mkdir to create a directory). This expression returns the current action that the user is taking. Possible values: Neighbor, login, ls, get, put, rename, mkdir, rmdir, del, logout, any. Following is an example: Add authorization policy pol1 “fs.command eq login && (fs.user eq administrator || fs.serverip eq 10.102.88.221 –netmask 255.255.255.252)” allow FS.USER Returns the user who is logged on to the file system. FS.SERVER Returns the host name of the target server. In the following example, the string win2k3-88-22 is the server name: fs.server eq win2k3-88-221 FS.SERVERIP Returns the IP address of the target server. FS.SERVICE Returns a shared root directory on the file server. If a particular folder is exposed as shared, a user can directly log on to the specified first level folder. This first level folder is called a service. For example, in the path \\hostname\SERVICEX\ETC, SERVICEX is the service. As another example, if a user accesses the file \\hostname\service1\dir1\file1.doc, FS.SERVICE will return service1. Following is an example: fs.service notcontains New FS.DOMAIN Returns the domain name of the target server. FS.PATH Returns the complete path of the file being accessed. For example, if a user accesses the file \\hostname\service1\dir1\file1.doc, FS.PATHwill return \service\dir1\file1.doc. Following is an example: fs.path notcontains SSL Expression Definition FS.FILE Returns the name of the file being accessed. -

Disk Clone Industrial
Disk Clone Industrial USER MANUAL Ver. 1.0.0 Updated: 9 June 2020 | Contents | ii Contents Legal Statement............................................................................... 4 Introduction......................................................................................4 Cloning Data.................................................................................................................................... 4 Erasing Confidential Data..................................................................................................................5 Disk Clone Overview.......................................................................6 System Requirements....................................................................................................................... 7 Software Licensing........................................................................................................................... 7 Software Updates............................................................................................................................. 8 Getting Started.................................................................................9 Disk Clone Installation and Distribution.......................................................................................... 12 Launching and initial Configuration..................................................................................................12 Navigating Disk Clone.....................................................................................................................14 -

F.A.Q. Series ROM-DOS TM
21520 30th Drive SE #110 Bothell, WA 98021 USA Tel: (425) 951-8086 Fax: (425) 951-8095 [email protected] [email protected] www.datalight.com TM ROM-DOS F.A.Q. Series Question: Assuming they don't want FAT32, Long Filename support, or Sockets, why should my customer upgrade to the newest ROM-DOS? Answer: Since our first FAT32 and LFN release 4.00.1091, there have been several improvements to the core ROM- DOS kernel. This core code is used primarily for our DOS 6.22 compatible compilations, and then extended in the case of a FAT32 or Long Filename build. The 4.00.1091 release is also a new code base and there will be no further upgrades to the previous DOS 6.22 code. In order to obtain new features, fixes, and support a customer must upgrade to release 4.00.1091 or greater. Along with the performance enhancements for both size and speed, several corrections have been made to the ROM-DOS kernel. These include stack and memory issues, disk access issues, and compatibility with the former market leader in DOS. Most of the ROM-DOS utilities have also been improved for size and speed, along with bug fixes. The major changes happened with the XCOPY, HIMEM, MSCDEX, CHKDSK, FDISK and FORMAT utilities. In the realm of international support, the Euro was added to the keyboard and display driver code. ROM- DOS and PC-DOS 2000 are the only non-GUI operating systems to support the Euro. Finally, new ROM-DOS utilities have been added. -

TRSDOS 6.2 to LS-DOS 6.3.0 Manual Update
LS-DOSÔ 6.3 UPDATE FOR TRSDOSâ 6.2.X The LS-DOS 6.3 release is an upgrade for the TRSDOS 6.2 operating system. Several important changes have been made to extend and enhance the operating system and its utilities. The date ranging has been expanded to accept dates through the year 1999. Files will now carry a modification time as well as a date. The DATECONV/CMD program is provided to translate version 6.2 or earlier disks to the 6.3 style dating. The user password has been eliminated from the system. The owner password still remains. The library command ID was added to display a customer service number. Several enhancements have been made to BASIC. The new DISKCOPY/CMD program will duplicate 5" double density floppy disks. Because the LS-DOS 6.3 update is a series of enhancements to TRSDOS 6.2, the primary documentation remains the 6.2 manual and Technical Reference manual. If you have a version of TRSDOS earlier than 6.2, you can obtain the manuals from Radio Shack under the catalog numbers 26-0316 (TRSDOS Version 6 [6.2 DOS manual and disk]), 26-2110 (Model 4/4D [6.2] Technical Reference Manual), or 26-1117 (6.2 DOS manual only). This documentation should be treated as an addendum to the TRSDOS 6.2 information. LS-DOS 6.3 installation instructions Before performing the upgrade, it is recommended that you make several backup copies of the 6.3 master disk. The simplest way to do this is to boot your system using the 6.3 diskette, insert a blank diskette to receive the copy in drive 1, and type the command: DISKCOPY :0 :1 When the copy finishes, you can insert another destination diskette and make another copy. -

Mac Keyboard Shortcuts Cut, Copy, Paste, and Other Common Shortcuts
Mac keyboard shortcuts By pressing a combination of keys, you can do things that normally need a mouse, trackpad, or other input device. To use a keyboard shortcut, hold down one or more modifier keys while pressing the last key of the shortcut. For example, to use the shortcut Command-C (copy), hold down Command, press C, then release both keys. Mac menus and keyboards often use symbols for certain keys, including the modifier keys: Command ⌘ Option ⌥ Caps Lock ⇪ Shift ⇧ Control ⌃ Fn If you're using a keyboard made for Windows PCs, use the Alt key instead of Option, and the Windows logo key instead of Command. Some Mac keyboards and shortcuts use special keys in the top row, which include icons for volume, display brightness, and other functions. Press the icon key to perform that function, or combine it with the Fn key to use it as an F1, F2, F3, or other standard function key. To learn more shortcuts, check the menus of the app you're using. Every app can have its own shortcuts, and shortcuts that work in one app may not work in another. Cut, copy, paste, and other common shortcuts Shortcut Description Command-X Cut: Remove the selected item and copy it to the Clipboard. Command-C Copy the selected item to the Clipboard. This also works for files in the Finder. Command-V Paste the contents of the Clipboard into the current document or app. This also works for files in the Finder. Command-Z Undo the previous command. You can then press Command-Shift-Z to Redo, reversing the undo command. -

The Ask Leo! ® Guide to Routine Maintenance 2 Contents the Ask Leo! Manifesto
The Ask Leo! Guide to Routine Maintenance Simple steps to make your computer last longer and run faster. By Leo A. Notenboom An Ask Leo! ebook ISBN: 978-1-937018-10-8 (pdf) Copyright © 2013 The Ask Leo! ® Guide to Routine Maintenance 2 http://askleo.com Contents The Ask Leo! Manifesto ......................................................................................................................................... 7 Be sure to register your book! ................................................................................................................................. 8 Introduction – 12 months or 12,000 miles .............................................................................................................. 9 Back Up ................................................................................................................................................................ 10 Creating a System Repair Disk ............................................................................................................................. 11 Creating a Windows 7 System Repair disc ....................................................................................................... 11 A System Repair disc might not be all you think ............................................................................................. 12 A System Repair disc is not a System Installation disc .................................................................................... 13 A System Installation disc IS a System Repair disc -

Chapter 19 RECOVERING DIGITAL EVIDENCE from LINUX SYSTEMS
Chapter 19 RECOVERING DIGITAL EVIDENCE FROM LINUX SYSTEMS Philip Craiger Abstract As Linux-kernel-based operating systems proliferate there will be an in evitable increase in Linux systems that law enforcement agents must process in criminal investigations. The skills and expertise required to recover evidence from Microsoft-Windows-based systems do not neces sarily translate to Linux systems. This paper discusses digital forensic procedures for recovering evidence from Linux systems. In particular, it presents methods for identifying and recovering deleted files from disk and volatile memory, identifying notable and Trojan files, finding hidden files, and finding files with renamed extensions. All the procedures are accomplished using Linux command line utilities and require no special or commercial tools. Keywords: Digital evidence, Linux system forensics !• Introduction Linux systems will be increasingly encountered at crime scenes as Linux increases in popularity, particularly as the OS of choice for servers. The skills and expertise required to recover evidence from a Microsoft- Windows-based system, however, do not necessarily translate to the same tasks on a Linux system. For instance, the Microsoft NTFS, FAT, and Linux EXT2/3 file systems work differently enough that under standing one tells httle about how the other functions. In this paper we demonstrate digital forensics procedures for Linux systems using Linux command line utilities. The ability to gather evidence from a running system is particularly important as evidence in RAM may be lost if a forensics first responder does not prioritize the collection of live evidence. The forensic procedures discussed include methods for identifying and recovering deleted files from RAM and magnetic media, identifying no- 234 ADVANCES IN DIGITAL FORENSICS tables files and Trojans, and finding hidden files and renamed files (files with renamed extensions. -

Your Performance Task Summary Explanation
Lab Report: 11.2.5 Manage Files Your Performance Your Score: 0 of 3 (0%) Pass Status: Not Passed Elapsed Time: 6 seconds Required Score: 100% Task Summary Actions you were required to perform: In Compress the D:\Graphics folderHide Details Set the Compressed attribute Apply the changes to all folders and files In Hide the D:\Finances folder In Set Read-only on filesHide Details Set read-only on 2017report.xlsx Set read-only on 2018report.xlsx Do not set read-only for the 2019report.xlsx file Explanation In this lab, your task is to complete the following: Compress the D:\Graphics folder and all of its contents. Hide the D:\Finances folder. Make the following files Read-only: D:\Finances\2017report.xlsx D:\Finances\2018report.xlsx Complete this lab as follows: 1. Compress a folder as follows: a. From the taskbar, open File Explorer. b. Maximize the window for easier viewing. c. In the left pane, expand This PC. d. Select Data (D:). e. Right-click Graphics and select Properties. f. On the General tab, select Advanced. g. Select Compress contents to save disk space. h. Click OK. i. Click OK. j. Make sure Apply changes to this folder, subfolders and files is selected. k. Click OK. 2. Hide a folder as follows: a. Right-click Finances and select Properties. b. Select Hidden. c. Click OK. 3. Set files to Read-only as follows: a. Double-click Finances to view its contents. b. Right-click 2017report.xlsx and select Properties. c. Select Read-only. d. Click OK. e.