PGP Desktop for Mac OS X Quick Start Guide Version 10.0
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

TRSDOS 6.2 to LS-DOS 6.3.0 Manual Update
LS-DOSÔ 6.3 UPDATE FOR TRSDOSâ 6.2.X The LS-DOS 6.3 release is an upgrade for the TRSDOS 6.2 operating system. Several important changes have been made to extend and enhance the operating system and its utilities. The date ranging has been expanded to accept dates through the year 1999. Files will now carry a modification time as well as a date. The DATECONV/CMD program is provided to translate version 6.2 or earlier disks to the 6.3 style dating. The user password has been eliminated from the system. The owner password still remains. The library command ID was added to display a customer service number. Several enhancements have been made to BASIC. The new DISKCOPY/CMD program will duplicate 5" double density floppy disks. Because the LS-DOS 6.3 update is a series of enhancements to TRSDOS 6.2, the primary documentation remains the 6.2 manual and Technical Reference manual. If you have a version of TRSDOS earlier than 6.2, you can obtain the manuals from Radio Shack under the catalog numbers 26-0316 (TRSDOS Version 6 [6.2 DOS manual and disk]), 26-2110 (Model 4/4D [6.2] Technical Reference Manual), or 26-1117 (6.2 DOS manual only). This documentation should be treated as an addendum to the TRSDOS 6.2 information. LS-DOS 6.3 installation instructions Before performing the upgrade, it is recommended that you make several backup copies of the 6.3 master disk. The simplest way to do this is to boot your system using the 6.3 diskette, insert a blank diskette to receive the copy in drive 1, and type the command: DISKCOPY :0 :1 When the copy finishes, you can insert another destination diskette and make another copy. -

Instructions for Adept Utility Programs
Instructions for Adept Utility Programs Version 12.1 ¨ Adept Utility Disk For use with V+ 12.1 (Edit D & Later) FLIST README.TXT for program information General-Purpose Utility Programs Robot/Motion Utility Programs AdeptVision Utility Programs Network Utility Programs AdeptModules SPEC Data 1984-1997 by Adept Technology, Inc. Instructions for Adept Utility Programs Version 12.1 ¨ Adept Utility Disk For use with V+ 12.1 (Edit D & Later) FLIST README.TXT for program information General-Purpose Utility Programs Robot/Motion Utility Programs AdeptVision Utility Programs Network Utility Programs AdeptModules SPEC Data 1984-1997 by Adept Technology, Inc. Part # 00962-01000, Rev. A September, 1997 ® 150 Rose Orchard Way • San Jose, CA 95134 • USA • Phone (408) 432-0888 • Fax (408) 432-8707 Otto-Hahn-Strasse 23 • 44227 Dortmund • Germany • Phone (49) 231.75.89.40 • Fax(49) 231.75.89.450 adept 41, rue du Saule Trapu • 91300 • Massy • France • Phone (33) 1.69.19.16.16 • Fax (33) 1.69.32.04.62 te c hnology, inc. 1-2, Aza Nakahara Mitsuya-Cho • Toyohashi, Aichi-Ken • 441-31 • Japan • (81) 532.65.2391 • Fax (81) 532.65.2390 The information contained herein is the property of Adept Technology, Inc., and shall not be reproduced in whole or in part without prior written approval of Adept Technology, Inc. The information herein is subject to change without notice and should not be construed as a commitment by Adept Technology, Inc. This manual is periodically reviewed and revised. Adept Technology, Inc., assumes no responsibility for any errors or omissions in this document. -

Older Operating Systems
Older Operating Systems Class Notes # 10 Batch Files (Part 2) October 23, 2003 IF Condition When a given condition is true, the statement is executed. When the given condition is false, the statement is not executed. Figure one illustrates the flow chart for the IF condition. IF entry point No Decision Yes Statement (perform some action) IF exit point Figure 1: IF condition flow chart The IF condition tests the following three conditions: • The ERRORLEVEL of a program • Whether a string is equal to another string • Whether a file exists Using IF to test ERRORLEVEL The syntax for testing the ERRORLEVEL is: IF ERRORLEVEL number command This form of the IF condition determines whether the value of ERRORLEVEL is greater than or equal to a number specified in the number parameter. IF NOT ERRORLEVEL number command This form of the IF condition determines whether the value of ERRORLEVEL is not greater than or equal to a number specified in the number parameter. 1 If the specified condition is true, DOS executes the command specified in the command parameter. Otherwise, DOS skips to the next line in the batch file without executing the command in the command parameter. The only DOS commands that leave an ERRORLEVEL (exit) code are: BACKUP, DISKCOMP, DISKCOPY, FORMAT, GRAFTABL, KEYB, REPLACE, RESTORE, and XCOPY. Many other programs generate exit codes, however. For example, table one contains codes that are generated by the DISKCOPY command. Table one: DISKCOPY codes Code Description 0 The operation was successful. 1 A read/write error occurred that did not terminate the disk copy operation. -

External Commands
5/22/2018 External commands External commands Previous | Content | Next External commands are known as Disk residence commands. Because they can be store with DOS directory or any disk which is used for getting these commands. Theses commands help to perform some specific task. These are stored in a secondary storage device. Some important external commands are given below- MORE MOVE FIND DOSKEY MEM FC DISKCOPY FORMAT SYS CHKDSK ATTRIB XCOPY SORT LABEL 1. MORE:-Using TYPE command we can see the content of any file. But if length of file is greater than 25 lines then remaining lines will scroll up. To overcome through this problem we uses MORE command. Using this command we can pause the display after each 25 lines. Syntax:- C:\> TYPE <File name> | MORE C:\> TYPE ROSE.TXT | MORE or C: \> DIR | MORE 2. MEM:-This command displays free and used amount of memory in the computer. Syntax:- C:\> MEM the computer will display the amount of memory. 3. SYS:- This command is used for copy system files to any disk. The disk having system files are known as Bootable Disk, which are used for booting the computer. Syntax:- C:\> SYS [Drive name] C:\> SYS A: System files transferred This command will transfer the three main system files COMMAND.COM, IO.SYS, MSDOS.SYS to the floppy disk. 4. XCOPY:- When we need to copy a directory instant of a file from one location to another the we uses xcopy command. This command is much faster than copy command. Syntax:- C:\> XCOPY < Source dirname > <Target dirname> C:\> XCOPY TC TURBOC 5. -
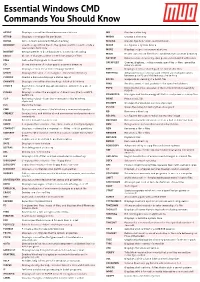
Essentials Windows CMD Command You Should Know
https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ https://www.makeuseof.com/tag/ 15-cmd-commands-every-windows-user-know/ https://www.makeuseof.com/tag/15-cmd-commands-every- Essentialwindows-user-know/ Windows https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ CMD https:// www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ https://www.makeuseof.com/tag/15-cmd- commands-every-windows-user-know/Commands You Should https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user- Know know/ https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ https:// www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ https://www.makeuseof.com/tag/15-cmd- ASSOC Displays or modifies file extension associations MD Creates a directory commands-every-windows-user-know/ https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user- ATTRIB Displays or changes file attributes MKDIR Creates a directory know/ https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ https:// BREAK Sets or clears extended CTRL+C checking MKLINK Creates Symbolic Links and Hard Links www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/BCDBOOT Used to copy critical files to the system partition and to crate a MODE Configures https://www.makeuseof.com/tag/15-cmd- a system device new system BCD store commands-every-windows-user-know/ https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-MORE Displays output one screen at a time BCDEDIT Sets properties in boot database -

Ch 7 Using ATTRIB, SUBST, XCOPY, DOSKEY, and the Text Editor
Using ATTRIB, SUBST, XCOPY, DOSKEY, and the Text Editor Ch 7 1 Overview The purpose and function of file attributes will be explained. Ch 7 2 Overview Utility commands and programs will be used to manipulate files and subdirectories to make tasks at the command line easier to do. Ch 7 3 Overview This chapter will focus on the following commands and programs: ATTRIB XCOPY DOSKEY EDIT Ch 7 4 File Attributes and the ATTRIB Command Root directory keeps track of information about every file on a disk. Ch 7 5 File Attributes and the ATTRIB Command Each file in the directory has attributes. Ch 7 6 File Attributes and the ATTRIB Command Attributes represented by single letter: S - System attribute H - Hidden attribute R - Read-only attribute A - Archive attribute Ch 7 7 File Attributes and the ATTRIB Command NTFS file system: Has other attributes At command line only attributes can change with ATTRIB command are S, H, R, and A Ch 7 8 File Attributes and the ATTRIB Command ATTRIB command: Used to manipulate file attributes Ch 7 9 File Attributes and the ATTRIB Command ATTRIB command syntax: ATTRIB [+R | -R] [+A | -A] [+S | -S] [+H | -H] [[drive:] [path] filename] [/S [/D]] Ch 7 10 File Attributes and the ATTRIB Command Attributes most useful to set and unset: R - Read-only H - Hidden Ch 7 11 File Attributes and the ATTRIB Command The A attribute (archive bit) signals file has not been backed up. Ch 7 12 File Attributes and the ATTRIB Command XCOPY command can read the archive bit. -

Command Line Interface
Mastering AmigaDOS by Jeffrey Stanton and Dan Pinal RAARl,IS, Inc. 6711 Valjean Avenue Van Nuys, California 91406 Library of Congress Cataloging-in-Publication Data Stanton, Jeffrey. Mastering AmigaDOS. Includes index. 1. Amiga (Computer)--Programming. 2. AmigaDOS (Computer operating system) I. Pinal, Dan. II. Title. QA76.8.AI77S73 1986 005.4'465 86-10881 ISBN 0-912003-55-3 (pbk.) Editor Mia McCroskey 10987654321 ISBN 0-912003-55-3 Copyright @ 1986 by Arrays, Inc.lThe Book Division, Jeffrey Stanton and Dan Pinal. All rights reserved. Printed in the United States of America. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, phot9copying,: recording, or otherwise, without the prior written permission of Arrays, Inc.lThe Book Division. Amiga and AmigaDOS are trademarks of Commodore Business Machines, Inc. TABLE OF CONTENTS Introduction 5 Chapter 1: Workbench and AmigaDOS 7 Similarity between Workbench's Icon Filing System and AmigaDOS 7 Workbench Operations 10 Duplicating, Copying, & Initializing Disks 12 Moving a Tool, Project or Drawer 14 Moving a Tool, Project or Drawer to Another Disk 15 Renaming Disk & Files 15 Info 15 Special Menu Items 16 Chapter 2: Command Line Interface (CLI) 19 Disk & Device Names 20 Other Device Names 21 Filenames 23 Directories 23 Setting the Current Directory 24 Rerouting Input & Output 25 Using Directory Conventions & Logical Devices 26 Creating a RAM disk 27 Running Commands in Background 29 Activating the Command -

Amigados Command Reference
AMIGA REFERENCE GUIDE THIRD EDITION SHELDON LEEMON AND ARLAN R. LEVITAN The complete guide and tutorial to the convenience, flexibilily, and power of ArnlgaDOS version 1.3. ~ . COMPUTE!'s I . , AmigaDOS i Reference Guide Third Edition Sheldon Leemon and Alan R. Levitan COMPUTEI Books Radnor, Pennsylvania Cover design: Anthony Jacobson Editors: Gregg Keiser and Stephen Levy Copyright 1986, 1987, 1989, COMPUTE! Publications, Inc. All rights reserved. Reproduction or translation of any part of this work beyond that permitted by Sections 107 and 108 of the United States Copyright Act without the permission of the copyright owner is unlawful. Printed in the United States of America lO987654321 Library of Congress Cataloging-in-Publication Data Leemon, Sheldon. AmigaOOS reference guide. Rev. ed. of: Compute!'s AmigaOOS reference guide / Arlan R. Levitan and Sheldon Leemon. c1986. Includes index. 1. Amiga (Computer)--Programming. 2. AmigaOOS (Computer operating system) I. Levitan, Arlan R. II. Levitan, Arlan R. Compute!'s AmigaOOS reference guide. III. Title. QA76.8.A177L36 1989 005.4465 89-42831 ISBN 0-87455-194-3 The authors and publisher have made every effort in the preparation of this book to ensure the accuracy of the information. However, the information in this book are sold without warranty, either express or im plied. Neither the authors nor COMPUTE! Publications, Inc. will be liable for any damages caused or alleged to be caused directlv, indirectly, incidentally, or consequentially by the programs or information in this book. The opinions expressed in this book are solely those of the authors and are not necessarily those of COMPUTE' Publications, Inc. -
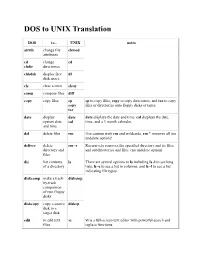
DOS to UNIX Translation
DOS to UNIX Translation DOS to... UNIX notes attrib change file chmod attributes cd change cd chdir directories chkdsk display free df disk space cls clear screen clear comp compare files diff copy copy files cp cp to copy files, copy to copy directories, and tar to copy copy files or directories onto floppy disks or tapes. tar date display date date displays the date and time, cal displays the date, system date cal time, and a 3 month calendar. and time del delete files rm Use caution with rm and wildcards, rm * removes all (no undelete option)! deltree delete rm -r Recursively removes the specified directory and its files directory and and subdirectories and files. (no undelete option) files dir list contents ls There are several options to ls including ls -l to see long of a directory lists, ls -c to see a list in columns, and ls -f to see a list indicating file types. diskcomp make a track- diskcmp by-track comparison of two floppy disks diskcopy copy a source diskcp disk to a target disk edit to edit text vi vi is a full-screen text editor with powerful search and files replace functions. edlin line editor ed ed and ex are predecessors of vi. ex fc compare two cmp cmp to compare binary files, diff compares two text files, files diff and diff3 compares three text files. diff3 find find text grep The UNIX find command finds files on the system, within a file and grep (global regular expression parser) finds text within a file. -

Volume Serial Numbers and Format Date/Time Verification
Volume Serial Numbers and Format Date/Time Verification Written by Craig Wilson, MSc MBCS CITP Digital Detective Group October 2003 (updated June 2005) Table of Contents Table of Contents ............................................................................................................................... 2 Introduction......................................................................................................................................... 3 Format Date/Time............................................................................................................................................................3 Naming Conventions .......................................................................................................................................................3 Volume Serial Number ....................................................................................................................................................3 Date/Time Calculation – Method One .............................................................................................................................4 Alternative Verification – Method Two.............................................................................................................................5 FAT Directory Entry Structure .........................................................................................................................................6 Summary ........................................................................................................................................... -

MS-DOS Commands
Source is from http://www.usask.ca/its/online_docs/msdos.html MS-DOS Commands Disk Commands FORMAT: Prepares a disk so that MS-DOS can use it. Formatting a disk erases all the information on the disk, so be careful. Example: FORMAT A: CHKDSK: Checks for problems and repairs corrupted disks. A disk can sometimes get corrupted when, for example, the power is turned off while a program is still running. Example: CHKDSK C: DISKCOPY: Duplicates diskettes. Use this command to copy important diskettes, like newly purchased programs. Example: DISKCOPY A: B: Directory Manipulation Commands MKDIR (MD): Makes a directory on the disk. Example: MD C:\DOS RMDIR (RD): Removes empty directories from the disk. Example: RD C:\DOS CHDIR (CD): Changes the current working directory. Example: CD C:\DOS PATH: Provides a list of directories where MS-DOS can find programs. Put this in your AUTOEXEC.BAT file. Example: PATH C:\;C:\DOS File Copying & Backup Commands COPY: Copies files between disks or directories. Example: COPY C:\AUTOEXEC.BAT A: XCOPY: Copies files, or entire directories with their subdirectories, to other disks or directories. Example: XCOPY C:\DOS C:\OLD_DOS /S BACKUP: Copies entire hard disks onto many floppy diskettes to create a backup copy of the hard disk. Example: BACKUP C:\*.* A: /S /F RESTORE: Restores the BACKUP files back onto your hard disk. Example: RESTORE A: C:\*.* File Management Commands DIR: Lists the files in a directory or disk. It includes file and directory names, file sizes, and file creation dates. Example: DIR C:\ TYPE: Displays the contents of a file on your computer screen. -

Microsoft® MS-DOS® 3.3 Reference
Microsoft® MS-DOS® 3.3 Reference HP 9000 Series 300/800 Computers HP Part Number 98870-90050 Flin- HEWLETT ~~ PACKARD Hewlett-Packard Company 3404 East Harmony Road, Fort Collins, Colorado 80525 NOTICE The information contained In this document is subject to change without notice HEWLETT-PACKARD MAKES NO WARRANTY OF ANY KIND WITH REGARD TO THIS MANUAL. INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. Hewlett-Packard shall not be liable for errors contained herein or direct. indirect. special, incidental or consequential damages in connection with the furnishing, performance, or use of this material WARRANTY A copy of the specific warranty terms applicable to your Hewlett-Packard product and replacement parts can be obtained from your local Sales and Service Office MS -DOS is a US registered trademark of Microsoft, Incorporated. LOTUS and 1-2-3 are registered trademarks of LOTUS Development Corporation. Copynght 1988. 1989 Hewlett-Packard Company This document contains proprietary information which is protected by copyright. All rights are reserved. No part of this document may be photocopied. reproduced or translated to another language without the prior written consent of Hewlett-Packard Company. The information contained in this document is subject to change without notice. Restricted Rights Legend Use. duplication or disclosure by the Government is subject to restrictions as set forth in paragraph (b)(3)(B) of the Rights in Technical Data and Software clause in DAR 7-104.9(a). Use of this manual and flexible disc(s) or tape cartridge(s) supplied for this pack is restricted to this product only.