Older Operating Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

PGP Desktop for Mac OS X Quick Start Guide Version 10.0
PGP Desktop for Mac OS X Quick Start Guide Version 10.0 In addition, use PGP Desktop to: What is PGP Desktop? y Use part of your hard drive space as an encrypted virtual disk volume with its own drive letter. PGP Desktop provides comprehensive security for desktops Create protected Zip archives. and laptops, making it possible for enterprises, workgroups, y and individuals to protect sensitive information without y Completely destroy files and folders so that nothing can changing the existing IT infrastructure or disrupting work recover them. processes. This award winning, easy-to-use solution encrypts email, files, virtual volumes, and entire disks from a single New to PGP Desktop? desktop application. Use this step-by-step guide to get started. You will find that, The PGP Desktop family of applications have been combined with PGP Desktop, protecting your data will be as easy as into several bundles. turning a key in a lock. y PGP Desktop Professional includes PGP Desktop Email y This Quick Start Guide helps you install PGP Desktop and and PGP Whole Disk Encryption get started. y PGP Whole Disk Encryption includes PGP Whole Disk y The PGP Desktop User’s Guide provides more detailed Encryption information on PGP Desktop. In it, you will learn what a keypair is, why you might want to create one, how to create one, and how to exchange keys with others so you can encrypt your own data and share data securely with Contents others. y What is PGP Desktop? (page 1) Note: A PGP Desktop license provides you with access to y New to PGP Desktop? (page 1) a certain set of PGP Desktop features. -

TRSDOS 6.2 to LS-DOS 6.3.0 Manual Update
LS-DOSÔ 6.3 UPDATE FOR TRSDOSâ 6.2.X The LS-DOS 6.3 release is an upgrade for the TRSDOS 6.2 operating system. Several important changes have been made to extend and enhance the operating system and its utilities. The date ranging has been expanded to accept dates through the year 1999. Files will now carry a modification time as well as a date. The DATECONV/CMD program is provided to translate version 6.2 or earlier disks to the 6.3 style dating. The user password has been eliminated from the system. The owner password still remains. The library command ID was added to display a customer service number. Several enhancements have been made to BASIC. The new DISKCOPY/CMD program will duplicate 5" double density floppy disks. Because the LS-DOS 6.3 update is a series of enhancements to TRSDOS 6.2, the primary documentation remains the 6.2 manual and Technical Reference manual. If you have a version of TRSDOS earlier than 6.2, you can obtain the manuals from Radio Shack under the catalog numbers 26-0316 (TRSDOS Version 6 [6.2 DOS manual and disk]), 26-2110 (Model 4/4D [6.2] Technical Reference Manual), or 26-1117 (6.2 DOS manual only). This documentation should be treated as an addendum to the TRSDOS 6.2 information. LS-DOS 6.3 installation instructions Before performing the upgrade, it is recommended that you make several backup copies of the 6.3 master disk. The simplest way to do this is to boot your system using the 6.3 diskette, insert a blank diskette to receive the copy in drive 1, and type the command: DISKCOPY :0 :1 When the copy finishes, you can insert another destination diskette and make another copy. -

This Document Explains How to Copy Ondemand5 Data to Your Hard Drive
Copying Your Repair DVD Data To Your Hard Drive Introduction This document explains how to copy OnDemand5 Repair data to your hard drive, and how to configure your OnDemand software appropriately. The document is intended for your network professional as a practical guide for implementing Mitchell1’s quarterly updates. The document provides two methods; one using the Xcopy command in a DOS window, and the other using standard Windows Copy and Paste functionality. Preparing your System You will need 8 Gigabytes of free space per DVD to be copied onto a hard drive. Be sure you have the necessary space before beginning this procedure. Turn off screen savers, power down options or any other program that may interfere with this process. IMPORTANT NOTICE – USE AT YOUR OWN RISK: This information is provided as a courtesy to assist those who desire to copy their DVD disks to their hard drive. Minimal technical assistance is available for this procedure. It is not recommended due to the high probability of failure due to DVD drive/disk read problems, over heating, hard drive write errors and memory overrun issues. This procedure is very detailed and should only be performed by users who are very familiar with Windows and/or DOS commands. Novice computers users should not attempt this procedure. Copying Repair data from a DVD is a time-consuming process. Depending on the speed of your processor and/or network, could easily require two or more hours per disk. For this reason, we recommend that you perform the actual copying of data during non-business evening or weekend hours. -

1. Xcopy 2. No, You Cannot Use the Xcopy Command in Your Assignment
Intro to Operating Systems CNET 173 Assignment #4 Windows / LINUX Command Line Commands You are to list twenty-five command line commands of each operating system (WINDOWS and LINUX). That’s twenty- five WINDOWS commands and twenty-five LINUX commands. For each command you are to give: 1. The command a. Description/Attribute of the command b. Syntax of the command and c. A maximum of five Parameters used with the command and a description of the parameter. (If there are less than five parameters, list all parameters associated with the command.) Each command should be numbered and grouped (all WINDOWS commands with WINDOWS commands). Command information should be listed in the 1, a, b, c order listed above (i.e. command, description, syntax and parameters). This assignment must be typed and submitted through CANVAS. It should include a title page consisting of your name, course name, number, day and time, assignment name, instructor’s name, and due date and the assignment instructions. Example listed below. Windows Command Line Commands 1. xcopy a) Description - Copies files and directories, including subdirectories. b) Syntax xcopy Source [Destination] [/w] [/p] [/c] [/v] [/q] [/f] [/l] [/g] [/d[:mm-dd-yyyy]] [/u] [/i] [/s [/e]] [/t] [/k] [/r] [/h] [{/a|/m}] [/n] [/o] [/x] [/exclude:file1[+[file2]][+[file3]] [{/y|/-y}] [/z] c) Parameters /w : Displays the following message and waits for your response before starting to copy files: Press any key to begin copying file(s) /p : Prompts you to confirm whether you want to create each destination file. /c : Ignores errors. /v : Verifies each file as it is written to the destination file to make sure that the destination files are identical to the source files. -

How to Cheat at Windows System Administration Using Command Line Scripts
www.dbebooks.com - Free Books & magazines 405_Script_FM.qxd 9/5/06 11:37 AM Page i How to Cheat at Windows System Administration Using Command Line Scripts Pawan K. Bhardwaj 405_Script_FM.qxd 9/5/06 11:37 AM Page ii Syngress Publishing, Inc., the author(s), and any person or firm involved in the writing, editing, or produc- tion (collectively “Makers”) of this book (“the Work”) do not guarantee or warrant the results to be obtained from the Work. There is no guarantee of any kind, expressed or implied, regarding the Work or its contents.The Work is sold AS IS and WITHOUT WARRANTY.You may have other legal rights, which vary from state to state. In no event will Makers be liable to you for damages, including any loss of profits, lost savings, or other incidental or consequential damages arising out from the Work or its contents. Because some states do not allow the exclusion or limitation of liability for consequential or incidental damages, the above limitation may not apply to you. You should always use reasonable care, including backup and other appropriate precautions, when working with computers, networks, data, and files. Syngress Media®, Syngress®,“Career Advancement Through Skill Enhancement®,”“Ask the Author UPDATE®,” and “Hack Proofing®,” are registered trademarks of Syngress Publishing, Inc.“Syngress:The Definition of a Serious Security Library”™,“Mission Critical™,” and “The Only Way to Stop a Hacker is to Think Like One™” are trademarks of Syngress Publishing, Inc. Brands and product names mentioned in this book are trademarks or service marks of their respective companies. -

Falcon DOS Portable Terminals Advanced User's Guide
! " #$% & " ' ()**%++,,,&% & " !"# $ $ % &' $ % ( ( % )*+ (*,' (% $ )(+ $ - !!. !!/$ 0 1 2 + + 2 3'4 0 5 -../ .+ 0 % &6 (*, % $ & & &/,( % & & ( &/,( 0 &(*, % & ! "#$%#$&#'%#'&( !! ! )!* 0 $ $ 0 3&7 4 8 $ 9 8 % 2 $ : $ 1 0 ; < $ ; * $ , . % $ / ) = ) $ # 0 , $ # 0 ( ( " & > 0 & > ? ! % , < 9 $ ; 0 ++ . 0 + = 0 & 2 -
![[D:]Path[...] Data Files](https://docslib.b-cdn.net/cover/6104/d-path-data-files-996104.webp)
[D:]Path[...] Data Files
Command Syntax Comments APPEND APPEND ; Displays or sets the search path for APPEND [d:]path[;][d:]path[...] data files. DOS will search the specified APPEND [/X:on|off][/path:on|off] [/E] path(s) if the file is not found in the current path. ASSIGN ASSIGN x=y [...] /sta Redirects disk drive requests to a different drive. ATTRIB ATTRIB [d:][path]filename [/S] Sets or displays the read-only, archive, ATTRIB [+R|-R] [+A|-A] [+S|-S] [+H|-H] [d:][path]filename [/S] system, and hidden attributes of a file or directory. BACKUP BACKUP d:[path][filename] d:[/S][/M][/A][/F:(size)] [/P][/D:date] [/T:time] Makes a backup copy of one or more [/L:[path]filename] files. (In DOS Version 6, this program is stored on the DOS supplemental disk.) BREAK BREAK =on|off Used from the DOS prompt or in a batch file or in the CONFIG.SYS file to set (or display) whether or not DOS should check for a Ctrl + Break key combination. BUFFERS BUFFERS=(number),(read-ahead number) Used in the CONFIG.SYS file to set the number of disk buffers (number) that will be available for use during data input. Also used to set a value for the number of sectors to be read in advance (read-ahead) during data input operations. CALL CALL [d:][path]batchfilename [options] Calls another batch file and then returns to current batch file to continue. CHCP CHCP (codepage) Displays the current code page or changes the code page that DOS will use. CHDIR CHDIR (CD) [d:]path Displays working (current) directory CHDIR (CD)[..] and/or changes to a different directory. -

Instructions for Adept Utility Programs
Instructions for Adept Utility Programs Version 12.1 ¨ Adept Utility Disk For use with V+ 12.1 (Edit D & Later) FLIST README.TXT for program information General-Purpose Utility Programs Robot/Motion Utility Programs AdeptVision Utility Programs Network Utility Programs AdeptModules SPEC Data 1984-1997 by Adept Technology, Inc. Instructions for Adept Utility Programs Version 12.1 ¨ Adept Utility Disk For use with V+ 12.1 (Edit D & Later) FLIST README.TXT for program information General-Purpose Utility Programs Robot/Motion Utility Programs AdeptVision Utility Programs Network Utility Programs AdeptModules SPEC Data 1984-1997 by Adept Technology, Inc. Part # 00962-01000, Rev. A September, 1997 ® 150 Rose Orchard Way • San Jose, CA 95134 • USA • Phone (408) 432-0888 • Fax (408) 432-8707 Otto-Hahn-Strasse 23 • 44227 Dortmund • Germany • Phone (49) 231.75.89.40 • Fax(49) 231.75.89.450 adept 41, rue du Saule Trapu • 91300 • Massy • France • Phone (33) 1.69.19.16.16 • Fax (33) 1.69.32.04.62 te c hnology, inc. 1-2, Aza Nakahara Mitsuya-Cho • Toyohashi, Aichi-Ken • 441-31 • Japan • (81) 532.65.2391 • Fax (81) 532.65.2390 The information contained herein is the property of Adept Technology, Inc., and shall not be reproduced in whole or in part without prior written approval of Adept Technology, Inc. The information herein is subject to change without notice and should not be construed as a commitment by Adept Technology, Inc. This manual is periodically reviewed and revised. Adept Technology, Inc., assumes no responsibility for any errors or omissions in this document. -

Word Processing)
Government of the people’s Republic of Bangladesh Affiliated University of International Computer Administration Foundation Bangladesh BASIC TRADE COURSE COMPUTER OPERATOR (WORD PROCESSING) Maintenance by Department of Exam Control & Certificate Distribution. House: ICA Administrative Building. Road: 6 Haricharan Roy Road, Faridabad, Sutrapur, Dhaka. Registrar Coll Center: 01742364899. E-mail: [email protected]; [email protected] Name of trades : Computer Applications Total contact hours : 75×4 = 300 hours. a. Computer Application Fundamentals Theory: 1. Basic computer hardware – system unit, monitor, keyboard, disk drives, disks and printer. 2. Computer keyboard and its functions. 3. Computer software and software and software packages. 4. Systematic approaches to start up a computer. 5. DOS and DOS commands CLS, DATE, TIME, Changing drive, DIR, TYPE, VER, VOL, LEVEL, DELETE, ERASE, COPY, RENAME. 6. General rules of typing. 7. Features of a typing CAL package. Practical: 8. Identify the different functional units of a computer. 9. Apply systematic approaches to start up a computer. 10. Recognize the different areas of the keyboard. 11. Apply the basic DOS commands CLS, DATE, TIME, Changing drive, DIR, TYPE, VER, VOL, LEVEL, DELETE, ERASW, COPY, RENAME. 12. Develop keyboard skills by following standard touch typing rules by using a simple Computer Assisted Learning (CAL) KEYBOARD package: 12.1 Drill on home keys (a s d f j k l ; spacebar). 12.2 Drill on (e i enter-key) cumulatively with above keys. 12.3 Drill on (r u) cumulatively with the above keys. 12.4 Drill on (g h) cumulatively with the above keys. 12.5 Drill on (t y) cumulatively with the above keys. -

External Commands
5/22/2018 External commands External commands Previous | Content | Next External commands are known as Disk residence commands. Because they can be store with DOS directory or any disk which is used for getting these commands. Theses commands help to perform some specific task. These are stored in a secondary storage device. Some important external commands are given below- MORE MOVE FIND DOSKEY MEM FC DISKCOPY FORMAT SYS CHKDSK ATTRIB XCOPY SORT LABEL 1. MORE:-Using TYPE command we can see the content of any file. But if length of file is greater than 25 lines then remaining lines will scroll up. To overcome through this problem we uses MORE command. Using this command we can pause the display after each 25 lines. Syntax:- C:\> TYPE <File name> | MORE C:\> TYPE ROSE.TXT | MORE or C: \> DIR | MORE 2. MEM:-This command displays free and used amount of memory in the computer. Syntax:- C:\> MEM the computer will display the amount of memory. 3. SYS:- This command is used for copy system files to any disk. The disk having system files are known as Bootable Disk, which are used for booting the computer. Syntax:- C:\> SYS [Drive name] C:\> SYS A: System files transferred This command will transfer the three main system files COMMAND.COM, IO.SYS, MSDOS.SYS to the floppy disk. 4. XCOPY:- When we need to copy a directory instant of a file from one location to another the we uses xcopy command. This command is much faster than copy command. Syntax:- C:\> XCOPY < Source dirname > <Target dirname> C:\> XCOPY TC TURBOC 5. -

Storage Data Movement Offload
Storage Data Movement Offload Frederick Knight NetApp 2011 Storage Developer Conference. © NetApp. All Rights Reserved. Storage Data Movement Offload What is Storage Data Movement Offload? Why is it important? What are the uses? How does it work? 2011 Storage Developer Conference. © NetApp. All Rights Reserved. 2 Moving Data the old way READ DATA STATUS WRITE DATA STATUS READ HOST STORAGE DATA STATUS WRITE DATA STATUS 2011 Storage Developer Conference. © NetApp. All Rights Reserved. 3 What Is It? Storage Data Movement Offload Also called - Copy Offload Storage device copies the data Data does not move through the host Two Techniques Single command current data copy Multi-command Read/Write model 2011 Storage Developer Conference. © NetApp. All Rights Reserved. 4 Why Is It Important? Copies data faster Saves bandwidth for real work Saves I/O bus (fabric/network) bandwidth Saves host I/O adapter bandwidth Saves host memory bandwidth Offloads work from the host to storage Gets you back to real work faster 2011 Storage Developer Conference. © NetApp. All Rights Reserved. 5 How Copy Offload works Copy Manager in the device Manages the movement of the data Two models of operation EXTENDED COPY (XCOPY) operations TOKEN based operations 2011 Storage Developer Conference. © NetApp. All Rights Reserved. 6 How XCOPY works Copy Manager in the device Manages the movement of the data Operates on data currently in the blocks EXTENDED COPY command provides: Identifiers for the Logical Units The SRC starting LBA The DST starting LBA The length A whole lot more optional stuff (including tapes) 2011 Storage Developer Conference. © NetApp. All Rights Reserved. -
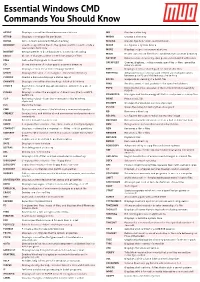
Essentials Windows CMD Command You Should Know
https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ https://www.makeuseof.com/tag/ 15-cmd-commands-every-windows-user-know/ https://www.makeuseof.com/tag/15-cmd-commands-every- Essentialwindows-user-know/ Windows https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ CMD https:// www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ https://www.makeuseof.com/tag/15-cmd- commands-every-windows-user-know/Commands You Should https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user- Know know/ https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ https:// www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ https://www.makeuseof.com/tag/15-cmd- ASSOC Displays or modifies file extension associations MD Creates a directory commands-every-windows-user-know/ https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user- ATTRIB Displays or changes file attributes MKDIR Creates a directory know/ https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ https:// BREAK Sets or clears extended CTRL+C checking MKLINK Creates Symbolic Links and Hard Links www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/BCDBOOT Used to copy critical files to the system partition and to crate a MODE Configures https://www.makeuseof.com/tag/15-cmd- a system device new system BCD store commands-every-windows-user-know/ https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-MORE Displays output one screen at a time BCDEDIT Sets properties in boot database