Locating the Source of Message Diffusion in the Anonymous Network Ying-Shou ZHONG1, Nan-Fang LI2, Li-Li YANG3 and Xu WANG4,* 1No
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Prevalence and Risk Factors of Refractive
Wang et al. BMC Ophthalmology (2021) 21:260 https://doi.org/10.1186/s12886-021-01996-2 RESEARCH Open Access Prevalence and risk factors of refractive error in Qinghai, China: a cross-sectional study in Han and Tibetan adults in Xining and surrounding areas Meng Wang†, Linyang Gan†, Jiantao Cui1, Guangliang Shan2, Ting Chen1, Xianghua Wang2, Yuhan Wang1, Li Pan2, Zhanquan Li3, Sen Cui3, Airong Yang3, Wenfang Li3, Guoqiang Jia3, Ximing Han3, Huijing He2, Yong Zhong1* and Jin Ma1* Abstract Background: Our study aimed to explore the prevalence and risk factors of refractive error (RE) in Han and Tibetan population aged 50–79 years in Xining and surrounding areas in Qinghai Province on Qinghai-Tibet Plateau. Methods: As part of the China National Health Survey, our cross-sectional study compared the age-adjusted prevalence of RE in Han and Tibetan older adults aged 50–79 years in Xining and surrounding areas. A multivariate logistic regression model was used to identify risk factors for myopia and hyperopia. Results: Among 769 Han participants and 476 Tibetan participants, the age-adjusted prevalence of myopia (spherical equivalent (SE) < − 0.5D), hyperopia (SE > + 0.5D), high myopia (SE < -6.0D) and astigmatism (cylindrical equivalent > = 0.5D) is 28.56, 22.82, 2.80, and 69.38%. Han participants have higher age-adjusted prevalence of myopia (32.93% vs 21.64%, p < 0.001), high myopia (3.93% vs 1.02%, p = 0.001) and astigmatism (72.14% vs 64.94%, p = 0.021) compared to Tibetan participants. Being Tibetan is the protective factor of myopia compared to being Han (OR 0.58, 95%CI 0.42–0.79, p < 0.001). -
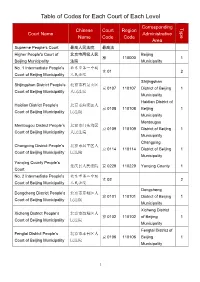
Table of Codes for Each Court of Each Level
Table of Codes for Each Court of Each Level Corresponding Type Chinese Court Region Court Name Administrative Name Code Code Area Supreme People’s Court 最高人民法院 最高法 Higher People's Court of 北京市高级人民 Beijing 京 110000 1 Beijing Municipality 法院 Municipality No. 1 Intermediate People's 北京市第一中级 京 01 2 Court of Beijing Municipality 人民法院 Shijingshan Shijingshan District People’s 北京市石景山区 京 0107 110107 District of Beijing 1 Court of Beijing Municipality 人民法院 Municipality Haidian District of Haidian District People’s 北京市海淀区人 京 0108 110108 Beijing 1 Court of Beijing Municipality 民法院 Municipality Mentougou Mentougou District People’s 北京市门头沟区 京 0109 110109 District of Beijing 1 Court of Beijing Municipality 人民法院 Municipality Changping Changping District People’s 北京市昌平区人 京 0114 110114 District of Beijing 1 Court of Beijing Municipality 民法院 Municipality Yanqing County People’s 延庆县人民法院 京 0229 110229 Yanqing County 1 Court No. 2 Intermediate People's 北京市第二中级 京 02 2 Court of Beijing Municipality 人民法院 Dongcheng Dongcheng District People’s 北京市东城区人 京 0101 110101 District of Beijing 1 Court of Beijing Municipality 民法院 Municipality Xicheng District Xicheng District People’s 北京市西城区人 京 0102 110102 of Beijing 1 Court of Beijing Municipality 民法院 Municipality Fengtai District of Fengtai District People’s 北京市丰台区人 京 0106 110106 Beijing 1 Court of Beijing Municipality 民法院 Municipality 1 Fangshan District Fangshan District People’s 北京市房山区人 京 0111 110111 of Beijing 1 Court of Beijing Municipality 民法院 Municipality Daxing District of Daxing District People’s 北京市大兴区人 京 0115 -

Visa Application – Section 2.5 Detailing Mailing Addresses & Phone Numbers for Locations in China
Visa Application – Section 2.5 Detailing Mailing Addresses & Phone Numbers for Locations in China It is important to note that your travel arrangements are not finalized until you receive your official adoption itinerary. There is a chance that you will be staying at a different hotel than those included below. * = indicates a hotel that is specific to families adopting from the Gansu, Guangdong, Guizhou or Shaanxi province Holiday Inn Hefei Zugong Plaza Hotel (Anhui) (Gansu) 1104 Changjiang Dong Rd, No.543 Donggangxi Road, Hefei 230001 Chengguan District, Phone: 86-551-2206666 Lanzhou, Gansu, China 730000 Phone: 86931-881.9999 Sofitel Hefei Grand Park (Anhui) Mingyuan Xindu Hotel Fanhua Road, Hefei 230601 (Guangxi) Phone: 86-551-2216688 No. 38 Xinming Road, Nanning Phone: 86-771-2118988 Radisson BLU Hotel (Beijing) China Hotel Marriott No. A East Beishanhuan Road, (Guangzhou) Chao Yang District Liu Hua Road, Guangzhou 510015 Phone: 86-10-59223388 Phone: 86-20-86666888 Metro Park Lido Hotel* Novotel Guiyang Downtown (Beijing) (Guizhou) No. 6 Jiangtailu, Chaoyang District, No. 8, Zhanghua North Road Beijing, China 100004 Guiyang, Guizhou 550002 Phone: 8610-64376688 Phone: 86-851-858-1888 Howard Johnson Plaza Wanda Holiday-Inn (Chongqing) (Heilongjiang) International Trade Center, No. 90 Jinwei Road, No.66 Qingnian Rd, 400010 Harbin, 150010 Phone: 86-23-63666666 Phone: 86-451-84226611 JW Marriott Chongqing Crowne Plaza Hotel (Chongqing) (Henan) 77 Qing Nian Road, Yu Zhong District No.115 Jinshui Road, Chongqing Zhengzhou 450003 Phone: 86-23-63888888 Phone: 86-371-65950055 Lakeside Hotel Fengleyuan Hotel (Fujian) (Henan) No. 158 Hubing Road, Fuzhou 350003 North Nanyang Rd Phone: 86-591-87839888 Phone: 86-371-66771188 Hua Yang Plaza Hotel (Henan) No. -

2021 First Quarterly Results
Hong Kong Exchanges and Clearing Limited and The Stock Exchange of Hong Kong Limited take no responsibility for the contents of this announcement, make no representation as to its accuracy or completeness and expressly disclaim any liability whatsoever for any loss howsoever arising from or in reliance upon the whole or any part of the contents of this announcement. (A joint stock limited company incorporated in the People’s Republic of China with limited liability) (Stock Code: 6030) 2021 FIRST QUARTERLY RESULTS This announcement is made pursuant to the disclosure obligations under Rule 13.09 of the Rules Governing the Listing of Securities on The Stock Exchange of Hong Kong Limited (the “Listing Rules”) and the Inside Information Provisions (as defined under the Listing Rules) under Part XIVA of the Securities and Futures Ordinance (Cap. 571 of the Laws of Hong Kong). The unaudited results of the Group for the first quarter ended 31 March 2021 are summarized as follows: • The Group recorded an operating revenue of RMB16,396,868,531.02; the net profit attributable to owners of the parent amounted to RMB5,164,799,333.48. • This report was prepared in accordance with the relevant disclosure requirements applicable to quarterly reports of listed companies issued by the China Securities Regulatory Commission. • The financial information contained in this report was prepared in accordance with the PRC GAAP. The contents of this report are consistent with the relevant announcement published by the Company on the Shanghai Stock Exchange. This -

20200227141213545.Pdf
Founded in 2007, SHAN SHUI Conservation Center is a Chinese NGO homegrown and dedicated to conservation practices. Together with our partners - communities, academic institutions, governments, companies, and media, we support local initiatives to defend the land we depend on. We focus our work on the most biologically diverse areas: Sanjiangyuan, the Mountains of Southwest China, and the Lancang River Basin. CONTENTS Nature Watch 22 Nature Watch Joint Action Base 23 The Chairman’s Foreword 01 Nature Watch Databases 24 The Executive Director’s Message 03 Nature Watch Data Application 25 Work Map 05 Snow Leopard Survey and Conservation Report 25 EIA Early Warning 25 Highlights 2018 07 An Urgent Call to Updat China Red 25 Lists (Fauna & Flora) Community-based Conservation 09 26 Snow Leopards and Grassland 10 Urban Biodiversity Recovery Snow Leopard Research and Conservation 11 Guilin Esquel Shi Ru Park 27 Wetland Research and Conservation 12 Beijing’s Urban Wetland Ecosystem 28 Sustainable Grassland Management 13 National Park Pilot Program 14 Communication and Fundraising 29 Communication 30 Giant Pandas and Forest 15 Fundraising Monitor and Patrol 16 31 Community Development 17 About Us 32 Policy Advocacy 18 Board Members 33 Forest Conservation and Recovery in Yunnan 19 Financial Overview 35 Yunlong : Multi-Value Forest Recovery 20 Staff and Awards 36 Menglian Heishan Initiative 21 Acknowledgments 37 Naren and Sayong Community Protected Areas 21 The Chairman's Foreword A March Through Uncertainty Since it was founded in 2007, Shanshui Conservation -

The Spatio-Temporal Characteristics of the Coordinated Development Of
2019 International Conference on Power, Energy, Environment and Material Science (PEEMS 2019) ISBN: 978-1-60595-669-5 The Spatio-Temporal Characteristics of the Coordinated Development of Urbanization and Resources Environmental Carrying Capacity in Lanzhou-Xining Urban Agglomeration Wei-ping ZHANG and Pei-ji SHI* School of Geography and Environmental Sciences, Northwest Normal University, Lanzhou 730070, P.R. China *Corresponding author Keywords: Urbanization, Resource environmental carrying capacity, Coordination characteristics, Temporal and spatial patterns, Lanzhou-Xining urban agglomeration. Abstract. The coordination of urbanization and resources and environment is one of the key issues to promote regional social and economic development. This paper took Lanzhou-Xining urban agglomeration as the study area, constructed the evaluation index of urbanization and resource environmental carrying capacity first, and then used entropy method and the coordination degree model to measure the coordination of urbanization and resource environmental carrying capacity from 2005 to 2017. Results indicate that the overall index of urbanization and resource environmental carrying capacity of Lanzhou-Xining urban agglomeration shows an upward trend, and there are obvious spatial differences, especially between Lanzhou and Xining and the surrounding counties. The coordination degree of urbanization and resource environmental carrying capacity is between [0.5, 0.6), most of the counties are in a state of reluctance coordination, and the spatial distribution law of the degree is high in the east and low in the west. And the regional differences are gradually shrinking. There is a significant positive correlation between urbanization and capacity. The coordination status of Lanzhou and Xining provincial cities is relatively good, and the urbanization level is lower. -

World Bank Document
RP1549 v2 World Bank-financed Xining Water Environment Management Project Public Disclosure Authorized Social Assessment Report Public Disclosure Authorized Management Office of the World Bank-financed Xining Water Environment Management Project Public Disclosure Authorized Xining, Qinghai, China October 2013 Public Disclosure Authorized Contents 1. Introduction ................................................................................................................................. IV 1.1 Overview of the Project ...................................................................................................... 2 1.2 Scope of the Project ........................................................................................................... 2 1.3 Purpose of SA .................................................................................................................... 4 1.4 SA Methods ........................................................................................................................ 4 1.5 Key Concerns of SA ........................................................................................................... 6 2. Overview of the Project Area ....................................................................................................... 8 2.1 Natural Conditions and Administrative Divisions ................................................................ 8 2.2 Socioeconomic Profile ....................................................................................................... -

2.27 Qinghai Province Qinghai Qingjiang Industrial Group Co., Ltd
2.27 Qinghai Province Qinghai Qingjiang Industrial Group Co., Ltd., affiliated with Qinghai Provincial Prison Administration Bureau1, has 14 county-level units under its jurisdiction Legal representative of the prison company: Liu Jianjia, General Manager of Qinghai Qingjiang Industrial Group Co., Ltd.2 His official positions in the prison system: Member of Communist Party Branch and Deputy Director of Qinghai Provincial Prison Administration Bureau There are 14 county-level units under the Qinghai Provincial Prison Administration Bureau, including 10 county-level units, which are 8 prisons, one Central Hospital of the Bureau (Qinghai Red Cross Hospital) and one Bureau Logistic Service Center. Business areas: The company is responsible for the management of operating assets in the province’s prison system, and it assumes the responsibility of maintaining and increasing the value of assets within the scope of its management; production and operation of mechanical and electrical equipment, building materials and light industrial products; design and construction of industrial and civil construction projects, installation of water and electricity, and decoration; agricultural and livestock product production, processing, and operations; real estate development; information consulting No. Company Name of the Legal Person and Legal Registered Business Scope Company Notes on the Prison Name Prison, to which Shareholder(s) representative/ Capital Address the Company Title Belongs 1 Qinghai Qinghai Qinghai Provincial Liu Jianjia 856.81 The company is responsible for the 191 Kunlun Qinghai Provincial Prison Administration Qingjiang Provincial Prison Prison Member of million management of operating assets in East Road, Bureau4 is the functional organization Industrial Administration Administration Communist Party yuan the province’s prison system, and it Chengdong responsible for prison-related work in the Group Co., Bureau Bureau Branch and assumes the responsibility of District, province. -

A Comparative Study of Catastrophic Health Expenditure in Zhejiang And
Zhen et al. BMC Health Services Research (2018) 18:844 https://doi.org/10.1186/s12913-018-3658-9 RESEARCH ARTICLE Open Access A comparative study of catastrophic health expenditure in Zhejiang and Qinghai province, China Xuemei Zhen1, Hao Zhang1,2, Xiaoqian Hu1, Shuyan Gu1, Yuanyuan Li1, Yuxuan Gu1, Minzhuo Huang1, Xueshan Sun1, Jingming Wei1 and Hengjin Dong1* Abstract Background: China has made great achievements in health insurance coverage and healthcare financing; however, the rate of catastrophic health expenditure (CHE) was 13.0% in China in 2008, which is higher than that in some other countries. There remain some differences in life-style, national customs, medical conditions, and health consciousness in different provinces in China. This study aimed to compare the rates of households with CHE, further to explore the different performance of factors influencing CHE between Zhejiang and Qinghai province, China. Methods: Data were derived from the household surveys conducted in Zhejiang and Qinghai. Sampling on multi- stage stratified cluster random method was adopted. Household with CHE occurs when the out-of-pocket payment for health care equals to or exceeds 40% of a household’s income. Univariate and multivariate logistic regression analyses were used to identify the performance of factors of CHE. Results: A total of 1598 households were included in this study, including 995 in Zhejiang and 603 in Qinghai. The average rates of CHE in Zhejiang and Qinghai were 9.6 and 30.5%, respectively. We found that economic status of households and households headed by an employed person are the protective factors for CHE; and number of members with chronic diseases and number of inpatients in household are the risk factors for CHE in the two provinces. -

Foreign Investment Guide of the People's Republic of China
Foreign Investment Guide of the People's Republic of China 2020 Edition Ministry of Commerce of the People's Republic of China Foreign Investment Guide of the People's Republic of China (2020 Edition) Editorial Board Director: Wang Shouwen Members: Zong Changqing, Liu Dianxun, Yang Zhengwei Chu Shijia, Li Yongsha, Tang Wenhong Peng Gang, Jiang Wei, Wang Kaixuan Zhai Qian, Wang Xu, Sun Tong, Li Fei Editorial Staff: Zhu Bing, Li Yong, Wang Yi Wei Wei, Sun Lan, Zou Jingwen Kang Yiming, Ji Xiaoxu, Lu Qinhong Shi Chengjie, Wu Ming, Li Pengfei Zhang Huicong, Jiao Zheng, Liu Yujing Lu Hui Expert Panel: Qi Huan (Professor of China University of Political Science and Law, Doctoral Supervisor) Li Jiguang (Professor of University of International Business and Economics, Doctoral Supervisor) Guo Guixia (Professor of University of International Business and Economics, Doctoral Supervisor) Deng Huihui (Professor of University of International Business and Economics, Doctoral Supervisor) Lv Yue (Professor of University of International Business and Economics, Doctoral Supervisor) Zhao Zheng (Associate Research Fellow of Development Research Center of the State Council) Foreword In November 2019, President Xi Jinping stated in the keynote speech at the 2nd China International Import Expo that “China will continue to foster an enabling business environment that is based on market principles, governed by law, and up to international standards. We will give foreign investments greater market access to more sectors, shorten the negative list further, and -

Annual Development Report on China's Trademark Strategy 2013
Annual Development Report on China's Trademark Strategy 2013 TRADEMARK OFFICE/TRADEMARK REVIEW AND ADJUDICATION BOARD OF STATE ADMINISTRATION FOR INDUSTRY AND COMMERCE PEOPLE’S REPUBLIC OF CHINA China Industry & Commerce Press Preface Preface 2013 was a crucial year for comprehensively implementing the conclusions of the 18th CPC National Congress and the second & third plenary session of the 18th CPC Central Committee. Facing the new situation and task of thoroughly reforming and duty transformation, as well as the opportunities and challenges brought by the revised Trademark Law, Trademark staff in AICs at all levels followed the arrangement of SAIC and got new achievements by carrying out trademark strategy and taking innovation on trademark practice, theory and mechanism. ——Trademark examination and review achieved great progress. In 2013, trademark applications increased to 1.8815 million, with a year-on-year growth of 14.15%, reaching a new record in the history and keeping the highest a mount of the world for consecutive 12 years. Under the pressure of trademark examination, Trademark Office and TRAB of SAIC faced the difficuties positively, and made great efforts on soloving problems. Trademark Office and TRAB of SAIC optimized the examination procedure, properly allocated examiners, implemented the mechanism of performance incentive, and carried out the “double-points” management. As a result, the Office examined 1.4246 million trademark applications, 16.09% more than last year. The examination period was maintained within 10 months, and opposition period was shortened to 12 months, which laid a firm foundation for performing the statutory time limit. —— Implementing trademark strategy with a shift to effective use and protection of trademark by law. -
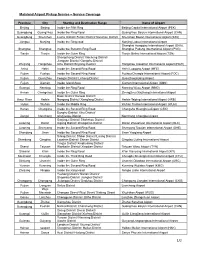
Mainland Airport Pickup Service – Service Coverage
Mainland Airport Pickup Service – Service Coverage Province City Starting and Destination Range Name of Airport Beijing Beijing Inside the Fifth Ring Beijing Capital International Airport (PEK) Guangdong Guangzhou Inside the Ring Road Guangzhou Baiyun International Airport (CAN) Guangdong Shenzhen Luohu District/ Futian District/ Nanshan District Shenzhen Baoan International Airport (SZX) Jiangsu Nanjing Inside the Ring road Nanjing Lukou International Airport Shanghai Hongqiao International Airport (SHA), Shanghai Shanghai Inside the Suburbs Ring Road Shanghai Pudong International Airport (PVG) Tianjin Tianjin Inside the Outer Ring Tianjin Binhai International Airport (TSN) Shangcheng District/ Xiacheng District/ Jianggan District/ Gongshu District/ Zhejiang Hangzhou Xihu District/ Binjiang Dustrict Hangzhou Xiaoshan International Airport (HGH) Anhui Hefei Inside the Second Ring Road Hefei Luogang Airport (HFE) Fujian Fuzhou Inside the Second Ring Road Fuzhou Changle International Airport (FOC) Fujian Quanzhou Fengze District/ Licheng District Quanzhoujinjiang Airport Fujian Xiamen Inside Island Area Xiamen International Airport (XMN) Guangxi Nanning Inside the Ring Road Nanning Wuxu Airport (NNG) Henan Chengchou Inside the Outer Ring Zhengzhou Xinzheng International Airport Daoli District/ Daowai District/ Amur River Harbin Nangang District/ Xiangfang District Harbin Taiping International Airport (HRB) Hubei Wuhan Inside the Middle Ring Wuhan Tianhe International Airport (WUH) Hunan Changsha Inside the Second Ring Road Changsha Huanghua