2018-07-11 and for Information to the Iso Member Bodies and to the Tmb Members
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

(L3) - Audio/Picture Coding
Committee: (L3) - Audio/Picture Coding National Designation Title (Click here to purchase standards) ISO/IEC Document L3 INCITS/ISO/IEC 9281-1:1990:[R2013] Information technology - Picture Coding Methods - Part 1: Identification IS 9281-1:1990 INCITS/ISO/IEC 9281-2:1990:[R2013] Information technology - Picture Coding Methods - Part 2: Procedure for Registration IS 9281-2:1990 INCITS/ISO/IEC 9282-1:1988:[R2013] Information technology - Coded Representation of Computer Graphics Images - Part IS 9282-1:1988 1: Encoding principles for picture representation in a 7-bit or 8-bit environment :[] Information technology - Coding of Multimedia and Hypermedia Information - Part 7: IS 13522-7:2001 Interoperability and conformance testing for ISO/IEC 13522-5 (MHEG-7) :[] Information technology - Coding of Multimedia and Hypermedia Information - Part 5: IS 13522-5:1997 Support for Base-Level Interactive Applications (MHEG-5) :[] Information technology - Coding of Multimedia and Hypermedia Information - Part 3: IS 13522-3:1997 MHEG script interchange representation (MHEG-3) :[] Information technology - Coding of Multimedia and Hypermedia Information - Part 6: IS 13522-6:1998 Support for enhanced interactive applications (MHEG-6) :[] Information technology - Coding of Multimedia and Hypermedia Information - Part 8: IS 13522-8:2001 XML notation for ISO/IEC 13522-5 (MHEG-8) Created: 11/16/2014 Page 1 of 44 Committee: (L3) - Audio/Picture Coding National Designation Title (Click here to purchase standards) ISO/IEC Document :[] Information technology - Coding -

Guidelines on Cryptographic Algorithms Usage and Key Management
EPC342-08 Version 7.0 4 November 2017 [X] Public – [ ] Internal Use – [ ] Confidential – [ ] Strictest Confidence Distribution: Publicly available GUIDELINES ON CRYPTOGRAPHIC ALGORITHMS USAGE AND KEY MANAGEMENT Abstract This document defines guidelines on cryptographic algorithms usage and key management. Document Reference EPC342-08 Issue Version 7.0 Date of Issue 22 November 2017 Reason for Issue Maintenance of document Produced by EPC Authorised by EPC Document History This document was first produced by ECBS as TR 406, with its latest ECBS version published in September 2005. The document has been handed over to the EPC which is responsible for its yearly maintenance. DISCLAIMER: Whilst the European Payments Council (EPC) has used its best endeavours to make sure that all the information, data, documentation (including references) and other material in the present document are accurate and complete, it does not accept liability for any errors or omissions. EPC will not be liable for any claims or losses of any nature arising directly or indirectly from use of the information, data, documentation or other material in the present document. Conseil Européen des Paiements AISBL– Cours Saint-Michel 30A – B 1040 Brussels Tel: +32 2 733 35 33 – Fax: +32 2 736 49 88 Enterprise N° 0873.268.927 – www.epc-cep.eu – [email protected] © 2016 Copyright European Payments Council (EPC) AISBL: Reproduction for non-commercial purposes is authorised, with acknowledgement of the source Table of Content MANAGEMENT SUMMARY ............................................................. 5 1 INTRODUCTION .................................................................... 7 1.1 Scope of the document ...................................................... 7 1.2 Document structure .......................................................... 7 1.3 Recommendations ............................................................ 8 1.4 Implementation best practices ......................................... -

Introducing the IBM Z15 - the Enterprise Platform for Mission-Critical Hybrid Multicloud
IBM United States Hardware Announcement 119-027, dated September 12, 2019 Introducing the IBM z15 - The enterprise platform for mission-critical hybrid multicloud Table of contents 2 Overview 26 Product number 3 Key requirements 57 Publications 3 Planned availability date 60 Technical information 4 Description 72 Terms and conditions 22 Product positioning 74 Prices 24 Statement of general direction 117Order now 118Corrections At a glance Announcing the IBM(R) z15 Today's announcement extends the IBM Z(R) position as the industry-leading platform for mission-critical hybrid cloud, with new innovations across security, data privacy, and resilience. Data privacy and security Pervasive encryption easily encrypts all data associated with an application, database, or cloud service -- whether on premises or in the cloud, at rest or in flight. The IBM z15 extends this beyond the border of the IBM Z environment. • The new IBM Z Data Privacy Passports, in conjunction with IBM z15 and available via an IBM z15 only PID, is being designed to enforce security and privacy protections to data not only on Z, but across platforms. It provides a data-centric security solution that enables data to play an active role in its own protection. For more information about IBM Z Data Privacy Passports V1.0 beta program, see Software Announcement 219-452, dated September 12, 2019. • IBM Z Data Privacy for Diagnostics provides clients with the capability to protect sensitive data that may be included in diagnostic dumps. Now sensitive data can be tagged such that it can be identified in dumps with no impact to dump capture times. -

Year 2010 Issues on Cryptographic Algorithms
Year 2010 Issues on Cryptographic Algorithms Masashi Une and Masayuki Kanda In the financial sector, cryptographic algorithms are used as fundamental techniques for assuring confidentiality and integrity of data used in financial transactions and for authenticating entities involved in the transactions. Currently, the most widely used algorithms appear to be two-key triple DES and RC4 for symmetric ciphers, RSA with a 1024-bit key for an asymmetric cipher and a digital signature, and SHA-1 for a hash function according to international standards and guidelines related to the financial transactions. However, according to academic papers and reports regarding the security evaluation for such algorithms, it is difficult to ensure enough security by using the algorithms for a long time period, such as 10 or 15 years, due to advances in cryptanalysis techniques, improvement of computing power, and so on. To enhance the transition to more secure ones, National Institute of Standards and Technology (NIST) of the United States describes in various guidelines that NIST will no longer approve two-key triple DES, RSA with a 1024-bit key, and SHA-1 as the algorithms suitable for IT systems of the U.S. Federal Government after 2010. It is an important issue how to advance the transition of the algorithms in the financial sector. This paper refers to issues regarding the transition as Year 2010 issues in cryptographic algorithms. To successfully complete the transition by 2010, the deadline set by NIST, it is necessary for financial institutions to begin discussing the issues at the earliest possible date. This paper summarizes security evaluation results of the current algorithms, and describes Year 2010 issues, their impact on the financial industry, and the transition plan announced by NIST. -

Technical Standards Catalogue VERSION 6.2
e-Government Technical Standards Catalogue VERSION 6.2 FINAL September 2005 Technical Standards Catalogue / version 6.2 final / September 2005 1 CONTENTS 1 INTRODUCTION ...........................................................................................................................3 2 CHANGES FROM PREVIOUS VERSION..................................................................................4 3 ISSUES UNDER CONSIDERATION............................................................................................5 4 INTERCONNECTION ...................................................................................................................7 TABLE 1 SPECIFICATIONS FOR INTERCONNECTIVITY.......................................................................7 TABLE 2 SPECIFICATIONS FOR WEB SERVICES ..............................................................................10 5 DATA INTEGRATION ................................................................................................................16 TABLE 3 SPECIFICATIONS FOR DATA INTEGRATION ...........................................................................16 6 CONTENT MANAGEMENT METADATA ...............................................................................19 TABLE 4 SPECIFICATIONS FOR CONTENT MANAGEMENT METADATA .................................................19 TABLE 5 SPECIFICATIONS FOR IDENTIFIERS .......................................................................................20 7 E-SERVICES ACCESS.................................................................................................................23 -

Forcepoint DLP Supported File Formats and Size Limits
Forcepoint DLP Supported File Formats and Size Limits Supported File Formats and Size Limits | Forcepoint DLP | v8.8.1 This article provides a list of the file formats that can be analyzed by Forcepoint DLP, file formats from which content and meta data can be extracted, and the file size limits for network, endpoint, and discovery functions. See: ● Supported File Formats ● File Size Limits © 2021 Forcepoint LLC Supported File Formats Supported File Formats and Size Limits | Forcepoint DLP | v8.8.1 The following tables lists the file formats supported by Forcepoint DLP. File formats are in alphabetical order by format group. ● Archive For mats, page 3 ● Backup Formats, page 7 ● Business Intelligence (BI) and Analysis Formats, page 8 ● Computer-Aided Design Formats, page 9 ● Cryptography Formats, page 12 ● Database Formats, page 14 ● Desktop publishing formats, page 16 ● eBook/Audio book formats, page 17 ● Executable formats, page 18 ● Font formats, page 20 ● Graphics formats - general, page 21 ● Graphics formats - vector graphics, page 26 ● Library formats, page 29 ● Log formats, page 30 ● Mail formats, page 31 ● Multimedia formats, page 32 ● Object formats, page 37 ● Presentation formats, page 38 ● Project management formats, page 40 ● Spreadsheet formats, page 41 ● Text and markup formats, page 43 ● Word processing formats, page 45 ● Miscellaneous formats, page 53 Supported file formats are added and updated frequently. Key to support tables Symbol Description Y The format is supported N The format is not supported P Partial metadata -

Metadefender Core V4.17.3
MetaDefender Core v4.17.3 © 2020 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of MetaDefender Core 14 1. Quick Start with MetaDefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Process Files with MetaDefender Core 21 2. Installing or Upgrading MetaDefender Core 22 2.1. Recommended System Configuration 22 Microsoft Windows Deployments 22 Unix Based Deployments 24 Data Retention 26 Custom Engines 27 Browser Requirements for the Metadefender Core Management Console 27 2.2. Installing MetaDefender 27 Installation 27 Installation notes 27 2.2.1. Installing Metadefender Core using command line 28 2.2.2. Installing Metadefender Core using the Install Wizard 31 2.3. Upgrading MetaDefender Core 31 Upgrading from MetaDefender Core 3.x 31 Upgrading from MetaDefender Core 4.x 31 2.4. MetaDefender Core Licensing 32 2.4.1. Activating Metadefender Licenses 32 2.4.2. Checking Your Metadefender Core License 37 2.5. Performance and Load Estimation 38 What to know before reading the results: Some factors that affect performance 38 How test results are calculated 39 Test Reports 39 Performance Report - Multi-Scanning On Linux 39 Performance Report - Multi-Scanning On Windows 43 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. -

Digital Recording of Performing Arts: Formats and Conversion
detailed approach also when the transfer of rights forms part of an employment contract between the producer of Digital recording of performing the recording and the live crew. arts: formats and conversion • Since the area of activity most probably qualifies as Stijn Notebaert, Jan De Cock, Sam Coppens, Erik Mannens, part of the ‘cultural sector’, separate remuneration for Rik Van de Walle (IBBT-MMLab-UGent) each method of exploitation should be stipulated in the Marc Jacobs, Joeri Barbarien, Peter Schelkens (IBBT-ETRO-VUB) contract. If no separate remuneration system has been set up, right holders might at any time invoke the legal default mechanism. This default mechanism grants a proportionate part of the gross revenue linked to a specific method of exploitation to the right holders. The producer In today’s digital era, the cultural sector is confronted with a may also be obliged to provide an annual overview of the growing demand for making digital recordings – audio, video and gross revenue per way of exploitation. This clause is crucial still images – of stage performances available over a multitude of in order to avoid unforeseen financial and administrative channels, including digital television and the internet. Essentially, burdens in a later phase. this can be accomplished in two different ways. A single entity can act as a content aggregator, collecting digital recordings from • Determine geographical scope and, if necessary, the several cultural partners and making this content available to duration of the transfer for each way of exploitation. content distributors or each individual partner can distribute its own • Include future methods of exploitation in the contract. -
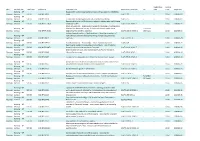
Alert Detailed Alert Timeframe Reference Document Title Developing
Registration Current Alert Detailed alert Timeframe Reference Document title Developing committee VA date stage Stage date Warning – NP Guidance for multiple organizations implementing a common (ISO50001) Warning decision SDT 36 ISO/NP 50009 EnMS ISO/TC 301 - - 10.60 2018-06-10 Warning – NP Warning decision SDT 36 ISO/NP 31050 Guidance for managing emerging risks to enhance resilience ISO/TC 262 - - 10.60 2018-06-14 Warning – NP Reproducibility of the LOD of binary methods in collaborative and in-house Warning decision SDT 36 ISO/NP TS 27878 validation studies ISO/TC 69/SC 6/WG 1 - - 10.60 2018-06-25 Safety of machinery -- Ergonomic principles for the design of sorting cabins Warning – NP intended for the manual sorting of dry household and similar waste TO CHECK Warning decision - ISO/NP TR 23474 originating from selective collection ISO/TC 159/SC 3/WG 4 (ISO lead) - 10.60 2018-06-30 Surface chemical analysis -- Depth profiling -- Quantitative analysis of Warning – NP multi-element alloy films by depth profiling analysis using reference Warning decision SDT 36 ISO/NP 23473 materials ISO/TC 201/SC 4 - - 10.60 2018-06-28 Warning – NP Warning decision SDT 36 ISO/NP 23472-1 Foundry machinery -- Terminology -- Part 1: Fundamental terms ISO/TC 306 - - 10.60 2018-06-27 Warning – NP Experimental designs for evaluation of uncertainty -- Use of factorial Warning decision SDT 36 ISO/NP TS 23471 designs for determining uncertainty functions ISO/TC 69/SC 6/WG 7 - - 10.60 2018-06-25 Warning – NP Determination of heavy water isotopic purity by Fourier -

JPEG XR an Image Coding Standard
International Journal of Computer and Electrical Engineering, Vol.4, No.2, April 2012 JPEG XR an Image Coding Standard Savita S. Jadhav and Sandeep K. Jadhav implementations of the encoder and decoder as simple as Abstract—JPEG XR is an emerging image coding standard, possible. For the compression of digital image, the Joint based on HD Photo developed by Microsoft technology. It Photographic Experts Group, the first international image supports high compression performance twice as high as the de coding standard for continuous-tone natural images, was facto image coding system, namely JPEG, and also has an advantage over JPEG 2000 in terms of computational cost. defined in 1992. JPEG is a well-known image compression JPEG XR is expected to be widespread for many devices format today because of the population of digital still camera including embedded systems in the near future. This and Internet. Another image coding standard, JPEG2000 [3], review-based paper proposes a novel architecture for JPEG XR was finalized in 2001. Differed from JPEG standard, a encoding. This paper gives discussion of image partition and Discrete Cosine Transform based coder, the JPEG2000 uses windowing techniques. Further frequency transform and a Discrete Wavelet Transform based coder for better coding quantization is also addressed. A brief insight into Predication, Adaptive Encode and Packetization has been provided in the efficiency. The JPEG2000 not only enhances the paper. compression, but also includes many new features, such as quality scalability, resolution scalability, region of interest, Index Terms—JPEG XR, encoder, PCT, quantization, and lossy/lossless coding in a unified framework. -

Hardware Security Modules: Attacks and Secure Configuration
Hardware Security Modules: Attacks and Secure Configuration Graham Steel Graham Steel April 2014 Graham Steel - HSM Attacks and Secure Configuration April 2014 - 2/ 56 Secure Hardware History Military: WW2 Enigma machines - captured machines used to help break codes NSA devices with explosive tamper resistance - http://www.nsa.gov/about/cryptologic_heritage/museum/ Commercial: IBM: Cryptoprocessors for mainframes - tamper-resistant switches on case ATMs (cash machines) - Encrypted PIN Pads (EPPs) and Hardware Security Modules (HSMs) Graham Steel - HSM Attacks and Secure Configuration April 2014 - 3/ 56 Secure Hardware History - 2 Cryptographic Smartcards - chip contains cryptoprocessor and keys in memory - used in SIM cards, credit cards, ID cards, transport::: Authentication tokens - generate One-Time Passwords, sometimes USB connection Trusted Platform Module (TPM) - now standard (but unused) in most PC laptops The future.. - Secure Elements in mobile phones, cars,::: Graham Steel - HSM Attacks and Secure Configuration April 2014 - 4/ 56 Example - Cash Machine Network I Introduced in the UK in the late 1960s I First modern machines (with DES) in the 70s and 80s I More than 2 million ATMs worldwide I Network is now global and ubiquitous (at least in cities) Graham Steel - HSM Attacks and Secure Configuration April 2014 - 5/ 56 Simplified Network Schematic ATM Maestro UK SocGen HSBC Graham Steel - HSM Attacks and Secure Configuration April 2014 - 6/ 56 HSMs I Manufacturers include IBM, nCipher, Thales, Utimaco, HP I Cost around $20 000 Graham Steel - HSM Attacks and Secure Configuration April 2014 - 7/ 56 A Word About Your PIN IBM 3624 method: 1. Write account number (PAN) as 0000AAAAAAAAAAAA 2. 3DES encrypt under a PDK (PIN Derivation Key), decimalise first digits 3. -

The JPEG XR Image Coding Standard
[standards in a NUTSHELL] Frédéric Dufaux, Gary J. Sullivan, and Touradj Ebrahimi The JPEG XR Image Coding Standard PEG XR is the newest image cod- baseline JPEG, but raw encoding has imaging and other flexible image inter- ing standard from the JPEG com- very high storage capacity requirements, action usage scenarios. mittee. It primarily targets the is generally camera specific, and typically JPEG XR’s architecture reflects the representation of continuous-tone lacks interoperability and published for- new requirements specific to high/ still images such as photographic mat documentation. extended dynamic range functionalities. Jimages and achieves high image quality, JPEG XR (ITU-T T.832 | ISO/IEC The traditional baseline JPEG coding on par with JPEG 2000, while requiring 29199-2) is a new image coding system format uses a bit depth of eight for each low computational resources and storage primarily targeting the representation of the three red green blue (RGB) color capacity. Moreover, it effectively address- of continuous-tone still images such as channels, resulting in 256 values per es the needs of emerging high dynamic photographic images. It is designed to channel or 16,777,216 color values. range imagery applications by including address the limitations of today’s for- However, more demanding applications support for a wide range of image repre- mats and to simultaneously achieve may require a bit depth of 16, providing sentation formats. high image quality while limiting com- 65,536 representable values for each putational resource and storage capacity channel or over 2.8 * 1014 color values BACKGROUND requirements. Moreover, it aims at pro- for a three-channel RGB image.