Characterising the Limits of the Openflow Slow-Path
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CPU ボードカタログ サポート CPU Intel :Core I7、Xeon-E5 Freescale :T4240、P4080、MPC8640D AMD :Radeon HD 6970M、HD 7970M GPGPU NVIDIA :Fermi、Kepler Architecture GPGPU
組込みシステム向け CPU ボードカタログ サポート CPU Intel :Core i7、Xeon-E5 Freescale :T4240、P4080、MPC8640D AMD :Radeon HD 6970M、HD 7970M GPGPU NVIDIA :Fermi、Kepler Architecture GPGPU サポートバス規格 OpenVPX VME/VXS CompactPCI PMC/XMC ATCA/AMC PCI Express 403102 Ⓒ MISH International Co., Ltd. MISH International Co., Ltd. ミッシュインターナショナルでは CPU ボードをスピーディに 導入頂けますよう、次のような サービスを提供しております CPU ボードのお貸出しサービス CPU ボードの性能評価検証サービス ミッシュインターナショナルでは、ユーザが実際に製品を導入する前に性能評価を実施していただけ ミッシュインターナショナルでは、専門の CPU ボードサポート技術者がお客様のご要望に応じて CPU ますよう各種評価用 CPU ボードをお貸出ししています。お貸出し時には、リアルタイム OS を含めた ボードの性能を評価・検証させていただきます。たとえばFFT の処理速度やボード間のデータ転送スピー CPU ボードに関するトータルな技術サポートを行っております。 ドの測定などユーザがシステムインテグレーションする上で必要なデータを検証の上、レポートさせて いただきます。(お客様のご要望内容によっては別途有償の場合もあります) CPU ボードの技術サポート ミッシュインターナショナルでは、専門のCPU ボードサポート技術者が導入前はもちろん、導入後もハー ド・ソフトの両面からお客様の技術サポートをいたします。CPU ボードのドライバソフトウェアやアプ リケーションの開発方法等をトータルにバックアップいたします。また、リアルタイム OS を含んだシ CPU ボード用フレームワークソフトウェアの開発サービス ステムインテグレーッションに関するアドバイスも対応しています。 CPU ボードを含んだ組込み用システムを構 築する上では、CPU ボードのハード・ソフ トに関する技術的な知識経験はもちろんです が、CPU ボード以外の A/D、D/A、DIO ボー ド等の各種 I/O ボードとのシームレスな高速 データ通信やリアルタイム OS を使用したイ ンテグレーションが必要です。当社では複数 のボードを使ったマルチ CPU ボードシステ ムやレーダ、ソナー、移動体通信等の無線信 号のリアルタイム処理等をトータルにサポートしています。全体的なデータのパスをサポートした『フ レームワークソフトウェア』の開発もお手伝いしています。ユーザは『フレームワークソフトウェア』 の開発を当社へ外注することにより、アプリケーションソフトウェアの開発や FPGA の開発に専念する ことが出来ます。(お客様のご要望内容によっては別途有償の場合もあります) インテル製 プロセッサ搭載 CPU ボード ボード CPU スピード 拡張 USB 耐環境 型名 プロセッサ メモリ NVRAM Ethernet インテル製 プロセッサ Core i7(Ivy Bridge)、 タイプ (Max) メザニン 2.0 仕様 Xeon E5-2648L x 2 32GB DDR3- 8MB NOR 1000BASE-T x 1 Level HDS6601 6U VPX 1.8GHz - 3 Xeon(8 Core) 搭載 CPU ボード (Sandy Bridge) -

Charactersing the Limits of the Openflow Slow-Path
Charactersing the Limits of the OpenFlow Slow-Path Richard Sanger, [email protected] Brad Cowie, [email protected] Matthew Luckie, [email protected] Richard Nelson, [email protected] University of Waikato, New Zealand 28 November 2018 The Question How slow is the slow-path? © THE UNIVERSITY OF WAIKATO • TE WHARE WANANGA O WAIKATO 2 Contents • Introduction to the Slow-Path • Motivation • Test Suite • Test Methodology • Results • Conclusions © THE UNIVERSITY OF WAIKATO • TE WHARE WANANGA O WAIKATO 3 OpenFlow Packet-in and Packet-out To move packets between the controller and network, packets are encapsulated in OpenFlow packet-in and packet-out messages and sent via the slow-path. © THE UNIVERSITY OF WAIKATO • TE WHARE WANANGA O WAIKATO 4 The Fast-Path ASIC OpenFlow Agent Ingress Egress OpenFlow Switch Network © THE UNIVERSITY OF WAIKATO • TE WHARE WANANGA O WAIKATO 5 The Slow-Path (Packet In) ASIC OpenFlow Agent Packet in OpenFlow Switch Network Control-Plane Network OpenFlow Application NIC Controller © THE UNIVERSITY OF WAIKATO • TE WHARE WANANGA O WAIKATO 6 Motivation: Control Traffic Requirements Control traffic is sensitive to bandwidth and latency Latency • Keep-alives • Flow Establishment (Reactive control) Bandwidth • Initial route exchange (BGP etc.) • Capture (Network debugging) • DoS (Misconfiguration, ICMP, etc.) © THE UNIVERSITY OF WAIKATO • TE WHARE WANANGA O WAIKATO 7 Motivation: Control Traffic Requirements Control traffic requirements must be met simultaneously. Example: consider the requirement of link detection probing. • Typical Bidirectional Forwarding Detection (BFD) requirements • < 50ms • 2,880pps (48 port switch) © THE UNIVERSITY OF WAIKATO • TE WHARE WANANGA O WAIKATO 8 Motivation: Shared Resource The slow-path is shared with all other OpenFlow messages. -

Avionics Hardware Issues 2010/11/19 Chih-Hao Sun Avionics Software--Hardware Issue -History
Avionics Hardware Issues 2010/11/19 Chih-hao Sun Avionics Software--Hardware Issue -History -HW Concepts History -FPGA vs ASIC The Gyroscope, the first auto-pilot device, was -Issues on • Avionics Computer introduced a decade after the Wright Brothers -Avionics (1910s) Computer -PowerPC • holds the plane level automatically -Examples -Energy Issue • is connected to computers for missions(B-17 and - Certification B-29 bombers) and Verification • German V-2 rocket(WWII) used the earliest automatic computer control system (automatic gyro control) • contains two free gyroscopes (a horizontal and a vertical) 2 Avionics Software--Hardware Issue -History -HW Concepts History -FPGA vs ASIC Avro Canada CF-105 Arrow fighter (1958) first used -Issues on • Avionics Computer analog computer to improve flyability -Avionics Computer is used to reduce tendency to yaw back and forth -PowerPC • -Examples F-16 (1970s) was the first operational jet fighter to use a -Energy Issue • fully-automatic analog flight control system (FLCS) - Certification and Verification • the rudder pedals and joysticks are connected to “Fly-by-wire” control system, and the system adjusts controls to maintain planes • contains three computers (for redundancy) 3 Avionics Software--Hardware Issue -History -HW Concepts History -FPGA vs ASIC NASA modified Navy F-8 with digital fly-by wire system in -Issues on • Avionics Computer 1972. -Avionics Computer • MD-11(1970s) was the first commercial aircraft to adopt -PowerPC computer-assisted flight control -Examples -Energy Issue The Airbus A320 series, late 1980s, used the first fully-digital - • Certification fly-by-wire controls in a commercial airliner and Verification • incorporates “flight envelope protection” • calculates that flight envelope (and adds a margin of safety) and uses this information to stop pilots from making aircraft outside that flight envelope. -

Chapter 1. Origins of Mac OS X
1 Chapter 1. Origins of Mac OS X "Most ideas come from previous ideas." Alan Curtis Kay The Mac OS X operating system represents a rather successful coming together of paradigms, ideologies, and technologies that have often resisted each other in the past. A good example is the cordial relationship that exists between the command-line and graphical interfaces in Mac OS X. The system is a result of the trials and tribulations of Apple and NeXT, as well as their user and developer communities. Mac OS X exemplifies how a capable system can result from the direct or indirect efforts of corporations, academic and research communities, the Open Source and Free Software movements, and, of course, individuals. Apple has been around since 1976, and many accounts of its history have been told. If the story of Apple as a company is fascinating, so is the technical history of Apple's operating systems. In this chapter,[1] we will trace the history of Mac OS X, discussing several technologies whose confluence eventually led to the modern-day Apple operating system. [1] This book's accompanying web site (www.osxbook.com) provides a more detailed technical history of all of Apple's operating systems. 1 2 2 1 1.1. Apple's Quest for the[2] Operating System [2] Whereas the word "the" is used here to designate prominence and desirability, it is an interesting coincidence that "THE" was the name of a multiprogramming system described by Edsger W. Dijkstra in a 1968 paper. It was March 1988. The Macintosh had been around for four years. -

With the New Power Mac G4, You'll Be Able to Make Movies
Power Mac G4 With the new Power Mac G4, you’ll be able to make movies, create music CDs, and even produce your own DVD videos. Now with five slots—one AGP 4X graphics slot and four high-performance PCI slots—it’s the most expandable Macintosh ever. Most of all, the Power Mac G4 is fast—with a PowerPC G4 processor at up to 733 megahertz, a state-of-the-art NVIDIA GeForce2 graphics card, and an improved system architecture. In fact, the multitalented Power Mac G4 redefines all previous notions of what a desktop computer can do. Power Mac G4 Features With outstanding performance, state-of-the-art graphics, and incredible expandability, the new Power Mac G4 is the fastest and most expandable Macintosh ever. But the Power Mac G4 Speed redefined • Fastest-ever PowerPC G4 with Velocity Engine, goes even further by including innovative tools for creating movies, music CDs, and even up to 733-MHz processing speed DVD videos. • Optional dual 533-MHz PowerPC G4 processors • New on-chip level 2 cache and backside level 3 Supercomputing-caliber processors and an improved system architecture give this computer cache (667-MHz and 733-MHz systems) • New high-performance graphics cards and AGP its power. Processor-intensive tasks such as color conversions, Gaussian blurs, and video special 4X slot effects execute faster than ever. In optimized applications such as Adobe Photoshop and Apple • 133-MHz system bus and PC133 SDRAM up Final Cut Pro, multiprocessor Power Mac G4 systems can achieve exponential gains in speed 1 to 1.5GB over single-processor systems. -
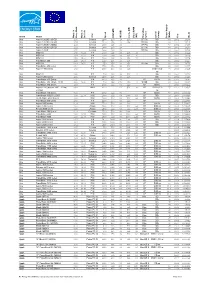
EC Energy Star Database Laptop Computers Archive 2001-2005
Brand Model Watts in Watts Mode Sleep in Watts On / Idle CPU Speed RAM (MB) HD (GB) (KB) Cache RAM Video (MB) Operating system optical storage Supply Power (Watts) Year PD_ID Acer Aspire 1202XC (10 GB) 2.76 Celeron 1200 256 10 256 XP Pro CD r 60 2002 10104 Acer Aspire 1202XC (20 GB) 2.74 Celeron 1200 256 20 256 XP Pro CD r 60 2002 10105 Acer Aspire 1200XV (10GB) 2.72 Celeron 1000 128 10 XP Pro CD r 60 2002 10106 Acer Aspire 1200XV (20 GB) 2.72 Celeron 1000 256 20 XP Pro CD r 60 2002 10107 Acer Aspire 1200X 2.72 Celeron 1000 128 10 XP Pro CD r 60 2002 10108 Acer MS2110 1.40 40.20 P 4 1700 128 20 256 16 CD r 70 2002 10112 Acer MS2114 1.60 41.00 P 4 1700 128 40 256 16 CD r 70 2002 10113 Acer MS2103 1.50 35.00 P 3 1200 128 20 256 11 CD r 70 2002 10114 Acer TravelMate 260 2.20 19.50 P 3 1130 256 20 256 CD r 60 2002 10115 Acer MS2109 2.20 19.50 P 3 150 256 20 256 XP Pro CD r 60 2002 10116 Acer TravelMate 270 series 2.12 P 4 1700 256 30 512 CD r 65 2002 10117 Acer Aspire 1400 Series 1.63 P 4 2000 256 30 512 DVD r / CD 90 2002 10118 rw Acer MS2101 1.40 P 3 700 128 30 512 8 CD r 50 2002 10119 Acer Aspire 1200 Series 2.66 Celeron 1300 256 20 256 CD r 60 2002 10120 Acer TravelMate 420 Series 2.15 P 4 2400 256 40 XP DVD r 90 2002 10121 Acer TravelMate 350 (XGA, 13.3") 8.80 18.80 P 3 700 248 9.59 256 8 W ME CD r 60 2003 10081 Acer TravelMate 530 Series 2.00 P 4 2400 512 40 512 XP DVD r 75 2003 1000211 Acer Aspire 1310 (also in 14.1", 2.9 kg 0.80 AMD 2000 60 512 32 XP DVD r / CD 75 2003 1003531 version) rw Acer TravelMate 430 Series 4.50 P 4 3060 512 -

Powerpc G5 White Paper December 2003 White Paper 2 Powerpc G5
PowerPC G5 White Paper December 2003 White Paper 2 PowerPC G5 Contents Page 3 Introduction Page 4 The World’s First 64-Bit Desktop Processor An Exponential Leap in Computing Power Memory Addressing up to 18 Exabytes High-Precision Calculations in a Single Clock Cycle Clock Speeds up to 2GHz Industry-Leading 1GHz Frontside Bus Full Support for Symmetric Multiprocessing Native Compatibility with 32-Bit Application Code Page 7 Next-Generation PowerPC Architecture Ultrafast Access to Data and Instructions Highly Parallel Execution Core Aggressive Queuing and Register Renaming Optimized 128-Bit Velocity Engine Two Double-Precision Floating-Point Units Two Integer Units Two Load/Store Units Condition Register Three-Component Branch Prediction Logic State-of-the-Art Process Technology from IBM Page 11 Technical Specifications White Paper 3 PowerPC G5 Introduction Key Features The revolutionary PowerPC G5 changes everything you know about personal computing. Suddenly, the next generation of high-performance applications for design and graphics, • 64-bit architecture, capable of addressing media production, and scientific research is possible and practical on the desktop. That’s 18 exabytes of memory • Clock speeds up to 2GHz because the PowerPC G5 brings a 64-bit architecture to the Mac platform—ushering in • 1GHz frontside bus for throughput of up to an exciting new era in personal computing. 8 GBps per processor The introduction of the PowerPC G5 is a product of Apple’s partnership with IBM, lever- • Dual independent 1GHz frontside buses in aging the most advanced chip design and manufacturing expertise in the world. The dual processor systems results are phenomenal: 130-nanometer fabrication technology, 2GHz clock speeds, and • Superscalar execution core supporting up to an all-new PowerPC architecture. -

Powerbook G4 Computer
Developer Note PowerBook G4 Computer December 2000 Apple Computer, Inc. Helvetica and Palatino are registered © 1999, 2000Apple Computer, Inc. trademarks of Heidelberger All rights reserved. Druckmaschinen AG, available from Linotype Library GmbH. No part of this publication may be reproduced, stored in a retrieval ITC Zapf Dingbats is a registered system, or transmitted, in any form trademark of International Typeface or by any means, mechanical, Corporation. electronic, photocopying, recording, OpenGL is a registered trademark of or otherwise, without prior written Silicon Graphics, Inc. permission of Apple Computer, Inc., PowerPC is a trademark of except to make a backup copy of any International Business Machines documentation provided on Corporation, used under license CD-ROM. therefrom. The Apple logo is a trademark of Apple Computer, Inc. Simultaneously published in the Use of the “keyboard” Apple logo United States and Canada. (Option-Shift-K) for commercial purposes without the prior written Even though Apple has reviewed this consent of Apple may constitute manual, APPLE MAKES NO trademark infringement and unfair WARRANTY OR REPRESENTATION, competition in violation of federal EITHER EXPRESS OR IMPLIED, WITH and state laws. RESPECT TO THIS MANUAL, ITS No licenses, express or implied, are QUALITY, ACCURACY, granted with respect to any of the MERCHANTABILITY, OR FITNESS technology described in this book. FOR A PARTICULAR PURPOSE. AS A Apple retains all intellectual RESULT, THIS MANUAL IS SOLD “AS property rights associated with the IS,” AND YOU, THE PURCHASER, ARE technology described in this book. ASSUMING THE ENTIRE RISK AS TO This book is intended to assist ITS QUALITY AND ACCURACY. application developers to develop IN NO EVENT WILL APPLE BE LIABLE applications only for Apple-labeled FOR DIRECT, INDIRECT, SPECIAL, or Apple-licensed computers. -

MPC5645S, Qorivva MPC5645S Microcontroller Data Sheet
Freescale Semiconductor Document Number: MPC5645S Data Sheet: Technical Data Rev. 12, 10/2014 MPC5645S 416 TEPBGA 208 LQFP 27 mm × 27 mm 28 mm × 28 mm Qorivva MPC5645S 176 LQFP Microcontroller Data Sheet 24 mm × 24 mm The Qorivva MPC5645S represents a new generation of 1 Overview . 2 32-bit microcontrollers targeting single-chip automotive 1.1 Device comparison. 2 instrument cluster applications. MPC5645S devices are part 1.2 Block diagram. 4 ® 1.3 Feature list . 5 of the MPC56xxS family of Power Architecture -based 1.4 Feature details . 7 devices. This family has been designed with an emphasis on 2 Pinout and signal descriptions . 24 providing cost-effective and high quality graphics capabilities 2.1 176 LQFP package pinout . 24 in order to satisfy the increasing market demand for color 2.2 208 LQFP package pinout . 25 Thin Film Transistor (TFT) displays within the vehicle 2.3 416 TEPBGA package pinout. 26 2.4 Signal description . 26 cockpit. Traditional cluster functions, such as gauge drive, 3 System design information. 59 real time counter, and sound generation are also integrated on 3.1 Power-up sequencing. 59 each device. 4 Electrical characteristics. 59 4.1 Introduction. 59 Devices in the MPC56xxS family contain between 256 KB 4.2 Parameter classification . 60 and 2 MB internal flash memory. The family allows for easy 4.3 Absolute maximum ratings . 60 expansion and covers a broad range of cluster applications 4.4 Recommended operating conditions . 62 from low to high-end enabling users to design a complete 4.5 Thermal characteristics . 64 4.6 EMI (electromagnetic interference) characteristics . -

Power Mac G4 Computer
Developer Note Power Mac G4 Computer December 2000 Apple Computer, Inc. Adobe is a trademark of Adobe Even though Apple has reviewed this © 1999, 2000 Apple Computer, Inc. Systems Incorporated or its manual, APPLE MAKES NO All rights reserved. subsidiaries and may be registered in WARRANTY OR REPRESENTATION, certain jurisdictions. EITHER EXPRESS OR IMPLIED, WITH No part of this publication may be RESPECT TO THIS MANUAL, ITS reproduced, stored in a retrieval Helvetica and Palatino are registered QUALITY, ACCURACY, system, or transmitted, in any form trademarks of Heidelberger MERCHANTABILITY, OR FITNESS or by any means, mechanical, Druckmaschinen AG, available from FOR A PARTICULAR PURPOSE. AS A electronic, photocopying, recording, Linotype Library GmbH. RESULT, THIS MANUAL IS SOLD “AS or otherwise, without prior written ITC Zapf Dingbats is a registered IS,” AND YOU, THE PURCHASER, ARE permission of Apple Computer, Inc., trademark of International Typeface ASSUMING THE ENTIRE RISK AS TO except to make a backup copy of any Corporation. ITS QUALITY AND ACCURACY. documentation provided on OpenGL is a registered trademark of CD-ROM. Silicon Graphics, Inc. IN NO EVENT WILL APPLE BE LIABLE The Apple logo is a trademark of FOR DIRECT, INDIRECT, SPECIAL, PowerPC is a trademark of INCIDENTAL, OR CONSEQUENTIAL Apple Computer, Inc. International Business Machines Use of the “keyboard” Apple logo DAMAGES RESULTING FROM ANY Corporation, used under license DEFECT OR INACCURACY IN THIS (Option-Shift-K) for commercial therefrom. purposes without the prior written MANUAL, even if advised of the consent of Apple may constitute Simultaneously published in the possibility of such damages. trademark infringement and unfair United States and Canada. -

Technolabs TL-VDS600-14
AdvancedTCA CompactPCI and AdvancedTCA Systems Resource Guide 2007 Accessories TechnoLabs ss17 Località Boschetto • L’Aquila, 67100 Italy +39 0862344516 technolabs.it TL-VDS600-14 The TL-VDS600-14 is a 14-slot PICMG 3.0 AdvancedTCA compliant backplane, designed and built for a central office environment. TechnoLabs offers a family of opti- mized AdvancedTCA shelves. The backplane supports a maximum of 14 slots in dual star topology where a pair of hub boards provides FEATURES redundant interconnects between node boards with Dimensions 12U (H) , 450 mm (W) signal speeds up to 3.125 Gbps. Rack mountable 19" (23"and 600x600 with adaptor) The system is capable of dissipating as much power as 14-slot dual star backplane with signal speeds up to 3.125 Gbps 200 W per single slot by two redundant primary 48 V Dual redundant IPMBs; Dual shelf manager and alarm panel power feeds. Dual 48 Vdc input terminals Power connectors are mounted on the two rear PEMs. Two Power Entry Modules (PEMs) An intelligent system management is responsible for Three pluggable removable fan trays with air filtering the whole shelf’s health status and correct functional- Advanced front rear cooling ity. The basic software on the system is based on Linux. Management interface (RMCP, CLI, WEB, SNMP) A web interface and standard telecom are provided. RoHS and WEEE compliant For more information, contact: [email protected] RSC# 32793 @ www.compactpci-systems.com/rsc CompactPCI and AdvancedTCA Systems Resource Guide 2007 Accessories Mellanox Technolgies 2900 Stender Way • Santa Clara, CA 95054 408-970-3400 www.mellanox.com InfiniScale III The InfiniScale III is Mellanox’s third generation InfiniBand switch device used to create reliable, scal- able, and easy to manage switch fabrics for compute, communication, storage, and embedded applications. -

Small but Powerful Signal Processing Sub-Systems
High-performance signal processing applications require far tecture for signal-processing multiprocessors is to place up to four more processing power than a single microprocessor can pro- AltiVec-enabled G4s on the same bus. Examples exist from sev- vide. Such high-end signal processing solutions currently exist eral suppliers. Most use a single-host bridge to load and unload as dedicated multiboard systems. Most also require a system four processors on a shared PowerPC bus. Typically this host host, typically a single board computer (SBC), which provides bridge gets data from a single PCI bus segment, which in turn needed support functions, such as system setup and initializa- comes through a single bridge from another shared PCI or VME tion, network communications, and human interface. bus (see Figure 1). The data throughput in and out of the board is limited by the slowest part of the path, which in this case is the However, as electronic components shrink, systems designers PCI bus, typically operating at a peak of 266 Mbytes/sec. want balanced high-performance, high-bandwidth signal pro- cessing in smaller dimensions, ideally as a single board sub-sys- tem. Frequently, this requirement is satisfied by multiple proces- sors on a single board, either performing parallel operations on individual data sets, or forming pipelines in which data is manip- ulated by one CPU and then sent to another for more processing. As processing demands increase, data bandwidth can become the bottleneck to maximizing system performance. Leading-edge sig- nal processing systems are designed to process a continuous data stream.