Development of a Secure Mail Client
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Configuring and Using Mutt
Configuring and Using Mutt Ryan Curtin LUG@GT Ryan Curtin Configuring and Using Mutt - p. 1/21 Goals » Goals By the end of this presentation, hopefully, you should be able Introduction to: Basic Usage Know the differences between Mutt, Pine, and other CLI Making a muttrc mailreaders Questions and Comments? Know the capabilities of Mutt Configure Mutt to connect to GT PRISM accounts (IMAP) Configure Mutt to make parsing through mail easy Know basic Mutt commands Write a basic, working .muttrc Know where to find further reference on Mutt Ryan Curtin Configuring and Using Mutt - p. 2/21 What is Mutt? » Goals Mutt is a “small, but very powerful text-based mail client for Introduction Unix operating systems” » What is Mutt? » Why should I use mutt? » Comparison with Pine Based largely on the elm mail client » What else is out there? Highly customizable; keybindings, macros Basic Usage Features to support mailing-lists (list-reply) Making a muttrc Questions and Comments? IMAP, POP3 support MIME, DSN, PGP support Ryan Curtin Configuring and Using Mutt - p. 3/21 Why should I use mutt? » Goals Lightweight, fast, and simple Introduction » What is Mutt? » Why should I use mutt? Can run inside a screen session » Comparison with Pine » What else is out there? No need for an annoying mouse Basic Usage Making a muttrc It looks cool Questions and Comments? Ryan Curtin Configuring and Using Mutt - p. 4/21 Comparison with Pine » Goals Mutt is lighter (and presumably faster) Introduction » What is Mutt? » Why should I use mutt? Mutt supports more authentication methods » Comparison with Pine » What else is out there? Mutt has better encryption (PGP/MIME/OpenPGP) Basic Usage Making a muttrc Mutt is still in active development (Pine stopped at 4.64; Questions and Comments? development moved to Alpine) Ryan Curtin Configuring and Using Mutt - p. -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -
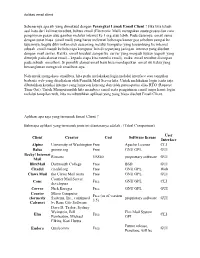
Sebenarnya Apa Sih Yang Dimaksud Dengan Perangkat Lunak Email Client
Aplikasi email client Sebenarnya apa sih yang dimaksud dengan Perangkat Lunak Email Client ? Jika kita telaah asal kata dari kalimat tersebut, bahwa email (Electronic Mail) merupakan suatu proses dan cara pengiriman pesan atau gambar melalui internet ke 1 org atau lebih. Pada dasarnya email sama dengan surat biasa (snail mail) yang harus melewati beberapa kantor pos sebelum sampai ke tujuannya, begitu dikirimkan oleh seseorang melalui komputer yang tersambung ke internet sebuah email masuk ke beberapa komputer lain di sepanjang jaringan internet yang disebut dengan mail server. Ketika email tersebut sampai ke server yang menjadi tujuan (seperti yang ditunjuk pada alamat email – kepada siapa kita menulis email), maka email tersebut disimpan pada sebuah emailbox. Si pemilik alamat email baru bisa mendapatkan email itu kalau yang bersangkutan mengecek emailbox-nya. Nah untuk mengakses emailbox, kita perlu melakukan login melalui interface atau tampilan berbasis web yang disediakan oleh Pemilik Mail Server kita. Untuk melakukan login tentu saja dibutuhkan koneksi internet yang lumayan kencang dan tidak putus-putus alias RTO (Request Time Out). Untuk Mempermudah kita membaca email serta pengiriman email tanpa harus login melalui tampilan web, kita membutuhkan aplikasi yang yang biasa disebut Email Client. Aplikasi apa saja yang termasuk Email Client ? Beberapa aplikasi yang termasuk jenis ini diantaranya adalah : (Tabel Comparison) User Client Creator Cost Software license Interface Alpine University of Washington Free Apache License CLI Balsa gnome.org Free GNU GPL GUI Becky! Internet Rimarts US$40 proprietary software GUI Mail BlitzMail Dartmouth College Free BSD GUI Citadel citadel.org Free GNU GPL Web Claws Mail the Claws Mail team Free GNU GPL GUI Courier Mail Server Cone Free GNU GPL CLI developers Correo Nick Kreeger Free GNU GPL GUI Courier Micro Computer Free (as of version (formerly Systems, Inc., continued proprietary software GUI 3.5) Calypso) by Rose City Software Dave D. -

Email on Mobile Devices Configuring Intune and FMOL Email
Email on Mobile Devices Configuring Intune and FMOL Email Intune Company Portal is used to access the FMOL network through a mobile device, including email. Intune provides two options for accessing email, but please note that the Intune app must be installed to access either. Here’s what to do: 1. Uninstall AirWatch or Previous Mobile Device Management Do not uninstall InTune if it is already installed. 1. Install Intune Company Portal 2. Choose one the two following channels to access email: Native Email Client Email may be access through the native mail app installed on phones. Outlook Email Client The Microsoft Outlook app may be installed to access email. Uninstall AirWatch or Previous Mobile Device Management AirWatch or other Mobile Device Management (MDM) applications must be removed before installing InTune and configuring FMOL email. Apple iOS Android 1. Open “Settings” and the select “General” 1. Open “Settings” and select “Apps” 2. Scroll to the bottom and select “Device 2. Select “Agent” and select “Deactivate and Management” Uninstall” 3. Select “Device Manager” 3. On Samsung devices only, select the “AirWatch Samsung ELM Service” and select “Deactivate 4. At the bottom, select “Remove and Uninstall” Management” Email on Mobile Devices Install Intune Company Portal 1. Install Intune Company Portal from the 4. Enter FMOL network password and approve Apple App Store or Google Play Store. MFA authentication request. 2. Open Intune and click “Sign In” 5. Click “Continue and Next” through the next several screens for setup of Encryption, Pin Lock Screen, and other security functions. 6. Upon completion, click “Done” to complete 3. -

Administrivia Mail on UNIX Systems — Traditional Approach
CSCI 3215 November 16, 2020 Administrivia • Reminder: Homework due Wednesday. • Is that it on homework? Almost — one more homework, a bit later, asking you to reflect on the course. • Anything else? Syllabus mentions a project. I think we still have time for a Slide 1 scaled-down version. Details soon. • Minute-essay responses have been great! I haven’t made time to reply but I’ve enjoyed reading them. • Current (as of about 5pm Monday) attendance report uploaded. If you’re not sure whether you’ve sent me all the minute essays ... Mail on UNIX Systems — Traditional Approach • (Reasonably good ASCII-art picture in rather old HOWTO for administrators, recommended as reading for today.) • MTA (“mail transport agent”) communicates with the outside world to send/receive mail, using SMTP (Simple Mail Transfer Protocol). Several choices; typically choose one when installing/configuring. Traditional one is Slide 2 sendmail; very powerful, but not easy to configure. Losing ground on desktop-oriented Linux distributions to alternatives such as postfix. • MDA (“mail delivery agent”) delivers mail locally, often to “mail spool”. One choice is procmail, which allows various forms of filtering. • MUA (“mail user agent”) is what users interact with directly. Many choices (more shortly). • Mechanisms for running “batch” jobs (including at and cron) often mail output to owning user. 1 CSCI 3215 November 16, 2020 Mail on UNIX (and Other) Systems — More-Current Approach • MUA communicates directly with mail server (probably not local), using IMAP, POP3, etc. Mail stays on server. Requires that mail server be running something that provides IMAP/POP3/etc. -

Inside: Special Focus Issue: Security
THE MAGAZINE OF USENIX & SAGE November 2001 • Volume 26 • Number 7 Special Focus Issue: Security Guest Editor: Rik Farrow inside: BEST PRACTICES No Plaintext Passwords by Abe Singer & The Advanced Computing Systems Association & The System Administrators Guild no plaintext passwords Introduction by Abe Singer Compromise of a user password is one of the most difficult intrusions to Abe Singer is a com- ORENSICS detect. Historically it has been difficult or impossible to avoid transmission puter security man- | F ager at the San Diego of passwords in the clear. But the technology now exists to make this possi- Supercomputer Cen- ble, albeit not trivially. The San Diego Supercomputer Center (SDSC) has ter, and occasional consultant and expert ETECTION managed to eliminate plaintext password transmission, while continuing to witness. His current D work is in security deliver services to a widely distributed user base. While it took some techni- measurement and security “for the life cal effort, overcoming the human hurdles proved to be more challenging. NTRUSION of the Republic.” |I This article discusses what solutions we provided and how we managed to do it without annoying too many people. We have actually added value to [email protected] RACTICES the environment, instead of reducing it. P EST At SDSC, we have to deal with some interesting issues of scale. We have thousands of B users and very few support staff. We have a wide variety of operating systems, high- speed networks and high-performance storage systems. Our users expect to be able to move large amounts of data (terabytes) around, in a reasonable amount of time. -

Electronic Mail — SMTP
CS 331 Application Layer Fall 2019 Electronic Mail — SMTP • Asynchronous message delivery - puts a message in a message pool and doesn’t require immediate response - delivers robustness and reliability • Two types of agents - Message User Agent (MUA): ‣ A computer program allow users to read, reply to, forward, save, and compose message ‣ Email clients (mail, pine, elm) - Message Transfer Agent (MTA) ‣ A software transfer a message from one computer to another computer using SMTP ‣ Has two queues: outgoing message queue, received message queue (inbox) • Two types of interactions (and protocols) - MTA to MTA - UA to MTA gloin:~> nc localhost 25 220 gloin.cs.colby.edu ESMTP Postfix (Ubuntu) helo gloin.cs.colby.edu 250 gloin.cs.colby.edu mail from: [email protected] 250 2.1.0 Ok rcpt to: [email protected] 250 2.1.5 Ok data 354 End data with <CR><LF>.<CR><LF> subject: SMTP test this is a test . 250 2.0.0 Ok: queued as 1DD9C7C007F quit 221 2.0.0 Bye gloin:~> mail Mail version 8.1.2 01/15/2001. Type ? for help. "/var/mail/yingli": 1 message 1 new >N 1 [email protected] Mon Sep 30 12:27 14/552 SMTP test & more 1 & quit Saved 1 message in /personal/yingli/mbox gloin:~> CS 331 Application Layer Fall 2019 MTA to MTA • Simple Mail Transfer Protocol (SMTP): port 25 - no intermediate nodes ‣ send from one end to the other regardless of the geographic distance ‣ if failures happen, try to resend after 30 minutes and give up after few days - no protections ‣ no encryption ‣ no authentication - a “not so simple” mail transfer protocol -

Authorized Abbreviations, Brevity Codes, and Acronyms
Army Regulation 310–50 Military Publications Authorized Abbreviations, Brevity Codes, and Acronyms Headquarters Department of the Army Washington, DC 15 November 1985 Unclassified USAPA EPS - * FORMAL * TF 2.45 05-21-98 07:23:12 PN 1 FILE: r130.fil SUMMARY of CHANGE AR 310–50 Authorized Abbreviations, Brevity Codes, and Acronyms This revision-- o Contains new and revised abbreviations, brevity codes , and acronyms. o Incorporates chapter 4, sections I and II of the previous regulation into chapters 2 and 3. o Redesignates chapter 5 of the previous regulation as chapter 4. USAPA EPS - * FORMAL * TF 2.45 05-21-98 07:23:13 PN 2 FILE: r130.fil Headquarters Army Regulation 310–50 Department of the Army Washington, DC 15 November 1985 Effective 15 November 1985 Military Publications Authorized Abbreviations, Brevity Codes, and Acronyms has been made to highlight changes from the a p p r o v a l f r o m H Q D A ( D A A G – A M S – P ) , earlier regulation dated 15February 1984. ALEX, VA 22331–0301. Summary. This regulation governs Depart- m e n t o f t h e A r m y a b b r e v i a t i o n s , b r e v i t y Interim changes. Interim changes to this codes, and acronyms. regulation are not official unless they are au- thenticated by The Adjutant General. Users Applicability. This regulation applies to el- will destroy interim changes on their expira- ements of the Active Army, Army National Guard, and U.S. -

In the United States Bankruptcy Court for the District of Delaware
Case 20-11120-LSS Doc 1101 Filed 01/19/21 Page 1 of 97 IN THE UNITED STATES BANKRUPTCY COURT FOR THE DISTRICT OF DELAWARE ---------------------------------------------------------------x : Chapter 11 In re: : : Case No. 20-11120 (LSS) COMCAR INDUSTRIES, INC., et al.,1 : : (Jointly Administered) Debtors. : ---------------------------------------------------------------x Related Docket No.: 1076 AMENDED COMBINED DISCLOSURE STATEMENT AND CHAPTER 11 PLAN OF LIQUIDATION Dated: January 19, 2021 Wilmington, Delaware DLA PIPER LLP (US) DLA PIPER LLP (US) Stuart M. Brown (DE 4050) Jamila Justine Willis (admitted pro hac vice) 1201 North Market Street, Suite 2100 1251 Avenue of the Americas Wilmington, Delaware 19801 New York, New York 10020 Telephone: (302) 468-5700 Telephone: (212) 335-4500 Facsimile: (302) 394-2341 Facsimile: (212) 335-4501 Email: [email protected] Email:[email protected] Counsel to the Debtors 1 The Debtors in these chapter 11 cases, along with the last four digits of each Debtor’s federal tax identification number, are: 9th Place Newberry, LLC (0359); 16th Street Pompano Beach, LLC (0278); CCC Spotting, LLC (0342); CCC Transportation, LLC (1058); Charlotte Avenue Auburndale, LLC (2179); Coastal Transport, Inc. (2918); Coastal Transport Logistics, LLC (7544); Comcar Industries, Inc. (8221); Comcar Logistics, LLC (2338); Comcar Properties, Inc. (9545); Commercial Carrier Corporation (8582); Commercial Carrier Logistics, LLC (7544); Commercial Truck and Trailer Sales Inc. (0722); Cortez Blvd. Brooksville, LLC (2210); CT Transportation, LLC (0997); CTL Distribution, Inc. (7383); CTL Distribution Logistics, LLC (7506); CTL Transportation, LLC (0782); CTTS Leasing, LLC (7466); Detsco Terminals, Inc. (9958); Driver Services, Inc. (3846); East Broadway Tampa, LLC (2233); East Columbus Drive Tampa, LLC (3995); Fleet Maintenance Services, LLC (1410); MCT Transportation, LLC (0939); Midwest Coast Logistics, LLC (7411); Midwest Coast Transport, Inc. -

Linux Sendmail Installation/Configuration
Sendmail Installation & Configuration: (26 Jan 2006) SMTP (Simple Mail Transfer Protocol) Email Primer: An email address: emailId@domainà [email protected] à bms is email Id & iitk.ac.in is domain Mail client: A system from where a sender (person) can send an email using any email client like mail, mh, elm, pine, Netscape messenger, Mozilla, Outlook Express, Eudora, Horde, Squirrelmail etc. Mail host: It is able to decode any address and reroutes the mail within the domain. Relay Host: It manages communication with network outside the domain. If you want a local mail system for your organization then relay host is not required. A good system for relay host is a router to internet. Gateway: It is a system between differing communication networks, like a mail from a Unix user must pass through a gateway to reach a VMS user. Mail Server: A mail storage system. This server keeps all mail boxes in /var/spool/mail (Linux) or /var/mail (Solaris) Standard Practice: Practically only one machine can act as: (Mailhost + MailRelay+ MailServer). Another configuration: Use separate servers for incoming & outgoing mails. Email Address resolution: When email sender sends an email. Destination address will be match with sender’s local aliases kept in .mailrc|.addressbook (pine uses it)|.elm/aliases.text etc. In second step it will try to expand/resolve destination address using local /etc/mail/aliases In third step it will try to expand/resolve the address using NIS aliases (If NIS is running and aliases are kept in NIS database) In fourth step it will use /etc/mail/aliases of mailhost to expand the destination Address. -

Tipo De Software Windows GNU/Linux 1) Rede 1) Netscape / Mozilla
Catálogo de Alternativas em Software Livre Índice: 1) Rede 2) Gerenciamento de Arquivos 3) Aplicações Genéricas 4) Multimídia: 4.1) CD / Áudio 4.2) Gráficos 4.3) Vídeo / Outros 5) Escritório / Finanças 6) Jogos 7) Programação / Desenvolvimento 8) Servidores 9) Aplicações Científicas / Acadêmicas 10) Emuladores 11) Outros / Humor Nota: Os números que aparecem ao lado de cada software GNU/Linux (ex: [8,8; 29,4%], em “Netscape / Mozilla”, logo abaixo, na primeira linha da tabela) referem-se, respectivamente, a uma nota (de 0 a 10) dada pelos usuários do site Freshmeat (http://freshmeat.net/) e a uma porcentagem de popularidade (de 0% a 100%) de usuários que utilizaram o respectivo software. Estes números servem apenas como referência. Tipo de Software Windows GNU/Linux 1) Rede 1) Netscape / Mozilla. [8,8; 29,4%] 2) Galeon. [8,99; 25,54%] 3) Konqueror. 4) Opera (Proprietário). [8,23; Internet Explorer, Netscape / 9,53%] Navegadores em Modo Mozilla for Windows, 5) Phoenix. Gráfico Opera, Phoenix for 6) Nautilus. Windows, ... 7) Epiphany. [8,69; 2,91%] 8) Links. [8,79; 14,59%] 9) Dillo. [8,55; 9,23%] 10) Mozilla Firebird. [8,92; 9,23%] 1) Links. [8,79; 14,59%] Navegadores em Modo Lynx for Windows, links for 2) Lynx. [8,67; 10,04%] Console Windows 3) w3m. [8,57; 5,57%] 4) Xemacs + w3. [8,39; 5,3%] 1) Evolution. [7,95; 19,25%] 2) Netscape / Mozilla Messenger. 3) Sylpheed, Sylpheed-claws. [8,9; 27,87%] 4) Kmail. [8,66; 2,69%] 5) Gnus. [8,79; 1,03%] Outlook Express, Netscape / 6) Balsa. -

Guide to Unix/ Commands 1
Guide_on_Unix [email protected] PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Wed, 11 Nov 2009 14:39:13 UTC Contents Articles Guide to Unix/ Commands 1 Guide to Unix/ Commands/ Summary 2 Guide to Unix/ Commands/ Getting Help 9 Guide to Unix/ Commands/ File System Utilities 11 Guide to Unix/ Commands/ Finding Files 23 Guide to Unix/ Commands/ File Viewing 25 Guide to Unix/ Commands/ File Editing 29 Guide to Unix/ Commands/ File Compression 30 Guide to Unix/ Commands/ File Analysing 34 Guide to Unix/ Commands/ Multiuser Commands 35 Guide to Unix/ Commands/ Self Information 37 Guide to Unix/ Commands/ System Information 38 Guide to Unix/ Commands/ Networking 42 Guide to Unix/ Commands/ Process Management 47 Guide to Unix/ Commands/ Devices 49 Guide to Unix/ Commands/ Kernel Commands 50 Guide to Unix/ Commands/ compress Commands 51 Guide to Unix/ Commands/ Miscellaneous 51 Guide to Unix/ Environment Variables 55 Guide to Unix/ Files 58 Guide to Unix/ BSD/ Introduction 65 Guide to Unix/ BSD/ OpenBSD 67 Guide to Unix/ Explanations/ Shell Prompt 69 Guide to Unix/ Explanations/ Quoting and Filename Expansion 73 Guide to Unix/ Explanations/ Pipes and Job Control 76 Guide to Unix/ Explanations/ Signals 77 Bourne Shell Scripting/ Quick Reference 80 Guide to Unix/ Explanations/ Introduction to Editors 85 Learning the vi editor/ vi Reference 88 Guide to Unix/ GNU Free Documentation License 98 References Article Sources and Contributors 104 Article Licenses License 105 Guide to Unix/Commands 1 Guide to Unix/ Commands The Unix command line is often considered difficult to learn.