Inside: Special Focus Issue: Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Setting up a Dial in PPP Server for Use with NX1500 Series Nexion Data Modems
Setting up a Dial In PPP Server for use with NX1500 series Nexion Data modems. A Linux server can provide many network services and all of these can be accessed by users via a dial up connection. Such services might include Email, Instant Messaging, BBS File Sharing and Internet access. This document applies to Red Hat Linux 7.3 and details only PPP Dial In setup. It requires Mgetty and PPPd to be installed – PPPd is installed by default. Mgetty. Installation To see if Mgetty is installed, run GnoRPM and click Find. Select Match Label from the list and enter mgetty. Click find. No result means Mgetty is not installed. Close the find window. To install, insert the Red Hat CD, mount it by right clicking the desktop and choosing Disks, CD-ROM. Click the Install button in GnoRPM, find Mgetty in the list and install by following the prompts etc. Unmount the drive the same way it was mounted. Mgetty must be run against each port to be monitored for dial in. To run Mgetty on COM 1, the command would be /sbin/mgetty –D ttyS0 where –D forces data mode (deny fax) and ttyS0 = COM 1. (ttyS1 is equivalent to COM 2). Most commonly the Mgetty command is added to /etc/inittab so it is automatically executed at startup and is also re-executed each time the process is terminated (modem hang up). For a modem on COM 1, add the following line to /etc/inittab: S0:2345:respawn:/sbin/mgetty –D ttyS0 The starting ‘S0’ is an arbitrary reference and can be any unique set of characters. -
Securecrt 7.3.6 Crack for Mac >>>
Securecrt 7.3.6 Crack For Mac >>> http://shurll.com/77o35 1 / 5 2 / 5 hash,,47850D6A1C717CEC4534B14525ED9BF2292DD905,,... VanDyke,,SecureCRT,,and,,SecureFX,,7 .3.6,,[Mac,,Os,,X],,[MAC599],,DOWNLOAD,,TORRENTSecureCRT,,for,,Mac,,OS,,X,,7.1... VanDyke,,Secu reCRT,,and,,SecureFX,,7.3.6,,[Mac,,Os,,X].torrent,,내부,,파일,,..Turn,,,your,,,computer,,,into,,,a,,,terminal,, ,server,,,using,,,Serial,,,to,,,Ethernet,,,Converter,,,with,,,its,,,amazing,,,capability,,,to,,,share,,,serial,,, devices,,,in,,,... Free,,,Download,,,SecureCRT,,,for,,,Mac,,,8.1.3,,,Build,,,1382,,,-,,,A,,,fully-featured,,,te rminal,,,emulator,,,as,,,well,,,as,,,a,,,SSH,,,and,,,Telnet,,,client,,,with,,,advanced,,,session,,,mana... Do wnload,,,VanDyke,,,SecureCRT,,,and,,,SecureFX,,,7.3.6,,,[Mac,,,Os,,,X],,,[MAC599],,,torrent,,,or,,,any,, ,other,,,torrent,,,from,,,Mac,,,category. SecureCRT®,,,7.3.6.963,,,for,,,MAC,,,|,,,40.7MbUsers,,,with,,,PCs,,,installed,,,with,,,Windows,,,8. Secu reCRT,,,provides,,,rock-solid,,,terminal,,,emulation,,,for,,,computing,,,professionals,,,,raising,,,product ivity,,,with,,,advanced,,,session,,,management,,,and,,,a,,,host,,,of,,,ways,,,to,,,save SecureCRT,,,for,,, Mac,,,,free,,,and,,,safe,,,downloadSecureCRT,,,supports,,,SSH2,,,,SSH1,,,,Telnet,,,,Telnet/SSL,,,,Serial, ,,,and,,,other,,,protocols..It,,,has,,,been,,,designed,,,to,,,be,,,used,,,during,,,the,,,high,,,stress,,,produc tion,,,... Torrentz,,,-,,,Fast,,,and,,,convenient,,,Torrents,,,Search,,,EngineApowersoft,,Screen,,Capture, ,Pro,,1.3.1,,InclTurn,,your,,computer,,into,,a,,terminal,,server,,using,,Serial,,to,,Ethernet,,Converter,, -

H2418.1 EMC-Computer Generated Solutions E-Mail Management and E-Discovery Solution Overview
Solution Overview EMC-Computer Generated Solutions E-mail Management and E-discovery Solution The Big Picture • Saves time, money, and space on • Helps reduce help desk calls and e-mail servers because the application lessens IT time spent manually runs on a different server (no code is archiving e-mail loaded on the e-mail server) • Delivers a secure corporate e-mail sys- • Remote calls to e-mail servers allow tem that protects valuable intellectual Unlimited Mailbox to run 24 hours per property, as well as complying with day, seven days a week without any government regulatory standards impact on e-mail server performance regarding e-mail storage and retention • Supports all known e-mail platforms, • Delivers immediate time to value including Microsoft Exchange, Lotus by enabling businesses to conduct Domino, Novell GroupWise, SunOne, legal discovery in-house, minimizing and UNIX Sendmail the need for expensive outside e-discovery fees • Provides complete compatibility with double-byte character support •Lowers the total cost of ownership by reducing operational and adminis- • Reduces disk and tape storage trative costs with self-managing and required to back up mail servers and self-healing content-addressed improves the performance of the storage (CAS) backup and recovery of e-mails • Provides long-term data retention • Reduces e-mail server farm as older capabilities, so content cannot be messages are moved to stable, overwritten or changed and is kept for less-expensive media a definable period of time, ensuring •Reduces licensing fees for operating its authenticity and meeting regulatory and backup systems, maintenance requirements costs, and support communications costs A unique, flexible solution that reduces costs and provides faster, less-expensive, lower-risk e-discovery The number and size of e-mails received at any given company, any given day, is becoming increasingly difficult and costly to manage. -

Groupwise Internet Agent
GroupWise Internet Agent April 7, 2000 Novell Confidential Manual Rev 99a24 8 February 00 Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Novell, Inc. reserves the right to revise this publication and to make changes to its content, at any time, without obligation to notify any person or entity of such revisions or changes. Further, Novell, Inc. makes no representations or warranties with respect to any software, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Novell, Inc. reserves the right to make changes to any and all parts of Novell software, at any time, without any obligation to notify any person or entity of such changes. This product may require export authorization from the U.S. Department of Commerce prior to exporting from the U.S. or Canada. Copyright © 1993-1999 Novell, Inc. All rights reserved. No part of this publication may be reproduced, photocopied, stored on a retrieval system, or transmitted without the express written consent of the publisher. U.S. Patent Nos. 4,555,775; 4,580,218; 5,412,772; 5,701,459; 5,717,912; 5,760,772; 5,870,739; 5,873,079; 5,884,304; 5,903,755; 5,913,209; 5,924,096; 5,946,467; D393,457 and U.S. Patents Pending. Novell, Inc. 122 East 1700 South Provo, UT 84606 U.S.A. www.novell.com GroupWise Internet Agent February 2000 104-001304-001 Online Documentation: To access the online documentation for this and other Novell products, and to get updates, see www.novell.com/documentation. -

Install Sendmail Mail Server on Debian GNU / Linux
Walking in Light with Christ - Faith, Computing, Diary Articles & tips and tricks on GNU/Linux, FreeBSD, Windows, mobile phone articles, religious related texts http://www.pc-freak.net/blog Install Sendmail mail server on Debian GNU / Linux Author : admin Installing sendmail on Debian Linux is something not so common these days. As sendmail has been overshadowed by his competitors Exim and Postfix. By default Debian Linux comes with Exim (light) installed as Exim is tiny and perfectly suitable for dealing with small and mid-sized SMTP needs. The reason why sendmail has been moved out by its competitors over the last 15 years is sendmail configuration is one big hell and besides that sendmail has been well known for its many security remote exploit holes - making it a famous target for crackers. Well anyways in some cases sendmail is necessary to install especially if you have a client which wants to have it set up. In this short article I will show how very basic sendmail installation on Debian host is done. blackstar:~# apt-get install sendmail-bin sensible-mda Reading package lists... Done Building dependency tree Reading state information... Done The following extra packages will be installed: sendmail-base sendmail-cf sensible-mda Suggested packages: sendmail-doc logcheck resolvconf sasl2-bin The following packages will be REMOVED: exim4 exim4-base exim4-config exim4-daemon-light sa-exim task-mail-server The following NEW packages will be installed: sendmail-base sendmail-bin sendmail-cf 0 upgraded, 3 newly installed, 6 to remove and 26 not upgraded. Need to get 1,626 kB of archives. -
Understanding Email Sending in Nagios XI
The Industry Standard In Infrastructure Monitoring Nagios XI Understanding Email Sending Purpose This document describes how Nagios XI sends emails and explains how to configure your email settings. Nagios XI uses email to send notifications as well as for sending reports. Target Audience This document is intended for use by Nagios Administrators who want to understand in detail how emails are sent by Nagios XI. Navigation Email settings in Nagios XI are located in Admin > System Config > Manage Email Settings. 1295 Bandana Blvd N, St. Paul, MN 55108 [email protected] US: 1-888-624-4671 INTL: 1-651-204-9102 www.nagios.com © 2017 Nagios Enterprises, LLC. All rights reserved. Nagios, the Nagios logo, and Nagios graphics are the servicemarks, trademarks, or registered trademarks owned by Nagios Enterprises. All other servicemarks and trademarks are the property of their respective owner. Page 1 / 7 Updated – September, 2018 The Industry Standard In Infrastructure Monitoring Nagios XI Understanding Email Sending Web Browser Behavior There are some behaviors of your web browser which you need to be aware of. A lot of different web browsers will auto-complete / auto-populate fields on a web page when it loads. This usually only occurs when it sees a common field that does not have a value, it may have a saved value for that "named field" and hence it will populate that field with that saved value. If you open the Manage Email Settings page in Nagios XI you might notice that the username and password fields are already populated. You know that you didn't put a value in here, especially when this is the first time you've visited this page on a fresh install of Nagios XI. -

Postfix−Cyrus−Web−Cyradm−HOWTO
Postfix−Cyrus−Web−cyradm−HOWTO Luc de Louw luc at delouw.ch Revision History Revision 1.2.0 2002−10−16 Revised by: ldl The first release of the 1.2 version. Revision 1.1.7 2002−10−15 Revised by: ldl Added Michael Muenz' hints for SMTP AUTH, corrected ca−cert related mistake, improved SGML code (more metadata), updated the software mentioned in the document. Revision 1.1.6 2002−06−14 Revised by: ldl Added sasl_mech_list: PLAIN to imapd.conf, added web−cyradm Mailinglist, added more to web−cyradm Revision 1.1.5 2002−06−11 Revised by: ldl Added new SQL query to initialize web−cyradm to have full data integrity in the MySQL Database, mysql−mydestination.cf reported to be operational as expected. Revision 1.1.4 2002−05−15 Revised by: ldl Added description what is needed in /etc/services Another fix for pam_mysql compile, updated software versions. Revision 1.1.3 2002−05−08 Revised by: ldl Added more description for web−cyradm, fix for wrong path of the saslauthdb−socket, Fix for wrong place of com_err.h, protection of the TLS/SSL private key. Revision 1.1.2 2002−04−29 Revised by: ldl Added description for Redhat users how to install the init scripts. Revision 1.1.1 2002−04−29 Revised by: ldl Fixed bug in configuring cyrus−IMAP (disabled unused kerberos authentication) Revision 1.1.0 2002−04−28 Revised by: ldl Initial support for building cyrus from source, dropped binary installation for Cyrus, because configuration has changed with Release 2.1.x Revision 1.0.2 2002−04−25 Revised by: ldl Added basic description for sieve and correct sender handling, minor fixes to db related stuff, Added mysql−lookup for »mydestination« , fixed bug for building postfix with mysql support. -

Biblioteca Antispam De Propósito Geral
Universidade Federal do Rio de Janeiro Escola Politécnica Departamento de Eletrônica e de Computação LibAntispam – Biblioteca Antispam de Propósito Geral Autor: _________________________________________________ Rafael Jorge Csura Szendrodi Orientador: _________________________________________________ Prof. Jorge Lopes de Souza Leão, Dr. Ing. Examinador: _________________________________________________ Prof. Antônio Cláudio Gómez de Sousa, M. Sc. Examinador: _________________________________________________ Prof. Aloysio de Castro Pinto Pedroza, Dr. DEL Maio de 2009 DEDICATÓRIA Dedico este trabalho: À Zeus (Jupiter), deus do Céu e da Terra, pai e rei dos deuses e dos homens, senhor do Olímpio e deus supremo deste universo. À Hera (Juno), rainha dos deuses, protetora da vida, das mulheres, da fecundidade e do matrimônio. À Athena (Miverva), deusa da sabedoria, do oficio, da inteligência e da guerra justa. Protetora do povo de Atenas. À Ártemis (Diana), deusa da caça, da natureza, da colheita, da serena luz da lua, dos nascimentos e protetora das Amazonas. À Afrodite (Venus), deusa da beleza e do amor, mãe de Enéias, fundador da raça romana, e matriarca da dinastia Julia (a dinastia de Julio Cesar). À minha mãe, Ildi e ao meu pai Gyorgy, pelo meu nascimento e por, de certa forma, terem contribuído para que eu me moldasse no que sou hoje. ii AGRADECIMENTO Ao povo brasileiro que contribuiu de forma significativa à minha formação e estada nesta Universidade. Este projeto é uma pequena forma de retribuir o investimento e confiança em mim depositados. Ao professor Leão, meu orientador neste projeto, por ter aceitado me guiar nesta minha jornada final do meu curso. Aos professores Baruqui (meu orientador acadêmico), Joarez, Gabriel, Petraglia e Mariane, meus amigos há vários anos que sempre me incentivaram a não desistir do curso de eletrônica. -
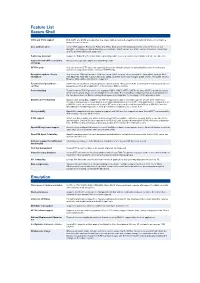
Feature List Secure Shell
Feature List Secure Shell SSH1 and SSH2 support Both SSH1 and SSH2 are supported in a single client, providing the maximum in flexibility when connecting to a range of remote servers. User authentication SecureCRT supports Password, Public Key (RSA, DSA, and X.509 including Smart Cards), Kerberos v5 (via GSSAPI), and Keyboard Interactive when connecting to SSH2 servers. For SSH1 servers, Password, Public Key, and TIS authentications are supported. Public Key Assistant Support for Public Key Assistant makes uploading public keys to an SSH2 server simple and safe for end users. Support for GSSAPI secured key Mechanisms supported depend on GSSAPI provider. exchange SFTP in a tab You can open an SFTP tab to the same SSH2 session without having to re-authenticate to perform file transfer operations using an interactive, text-based SFTP utility. Encryption ciphers: Strong The maximum 2048 bits length of DSA keys under SSH2 provides strong encryption. SecureCRT supports AES- encryption 128, AES-192, AES-256, Twofish, Blowfish, 3DES, and RC4 when connecting to SSH2 servers. For SSH1 servers, Blowfish, DES, 3DES, and RC4 are supported. Password and passphrase SSH2 session passwords and passphrases can be cached, letting SecureCRT and SecureFX share passwords and caching passphrases while either application or the Activator utility is running. Port forwarding Tunnel common TCP/IP protocols (for example, POP3, IMAP4, HTTP, SMTP) via SecureCRT to a remote Secure Shell server using a single, secure, multiplexed connection. Port forwarding configuration has been integrated into the tree-based Session Options dialog allowing easier configuration for securing TCP/IP application data. Dynamic port forwarding Dynamic port forwarding simplifies how TCP/IP application data is routed through the Secure Shell connection. -

Secure Configuration and Management of Linux Systems
Secure Configuration and Management of Linux Systems using a Network Service Orchestrator Vijay Satti A Thesis in The Department of Concordia Institute for Information Systems Engineering Presented in Partial Fulfillment of the Requirements for the Degree of Master of Applied Science at Concordia University Montréal, Québec, Canada May 2019 c Vijay Satti, 2019 CONCORDIA UNIVERSITY School of Graduate Studies This is to certify that the thesis prepared By: Vijay Satti Entitled: Secure Configuration and Management of Linux Systems using a Network Service Orchestrator and submitted in partial fulfillment of the requirements for the degree of Master of Applied Science complies with the regulations of this University and meets the accepted standards with respect to originality and quality. Signed by the Final Examining Committee: Chair Dr. Walter Lucia Examiner Dr. Anjali Agarwal Examiner Dr. Amr Youssef Supervisor Dr. J. William Atwood Approved by Dr. Chadi Assi, Graduate Program Director Department of Concordia Institute for Information Systems Engineering 2019 Dr. Amir Asif, Dean Faculty of Engineering and Computer Science Abstract Secure Configuration and Management of Linux Systems using a Network Service Orchestrator Vijay Satti Manual management of the configuration of network devices and computing devices (hosts) is an error-prone task. Centralized automation of these tasks can lower the costs of management, but can also introduce unknown or unanticipated security risks. Miscon- figuration (deliberate (by outsiders) or inadvertent (by insiders)) can expose a system to significant risks. Centralized network management has seen significant progress in recent years, result- ing in model-driven approaches that are clearly superior to previous "craft" methods. Host management has seen less development. -

Configuring and Using Mutt
Configuring and Using Mutt Ryan Curtin LUG@GT Ryan Curtin Configuring and Using Mutt - p. 1/21 Goals » Goals By the end of this presentation, hopefully, you should be able Introduction to: Basic Usage Know the differences between Mutt, Pine, and other CLI Making a muttrc mailreaders Questions and Comments? Know the capabilities of Mutt Configure Mutt to connect to GT PRISM accounts (IMAP) Configure Mutt to make parsing through mail easy Know basic Mutt commands Write a basic, working .muttrc Know where to find further reference on Mutt Ryan Curtin Configuring and Using Mutt - p. 2/21 What is Mutt? » Goals Mutt is a “small, but very powerful text-based mail client for Introduction Unix operating systems” » What is Mutt? » Why should I use mutt? » Comparison with Pine Based largely on the elm mail client » What else is out there? Highly customizable; keybindings, macros Basic Usage Features to support mailing-lists (list-reply) Making a muttrc Questions and Comments? IMAP, POP3 support MIME, DSN, PGP support Ryan Curtin Configuring and Using Mutt - p. 3/21 Why should I use mutt? » Goals Lightweight, fast, and simple Introduction » What is Mutt? » Why should I use mutt? Can run inside a screen session » Comparison with Pine » What else is out there? No need for an annoying mouse Basic Usage Making a muttrc It looks cool Questions and Comments? Ryan Curtin Configuring and Using Mutt - p. 4/21 Comparison with Pine » Goals Mutt is lighter (and presumably faster) Introduction » What is Mutt? » Why should I use mutt? Mutt supports more authentication methods » Comparison with Pine » What else is out there? Mutt has better encryption (PGP/MIME/OpenPGP) Basic Usage Making a muttrc Mutt is still in active development (Pine stopped at 4.64; Questions and Comments? development moved to Alpine) Ryan Curtin Configuring and Using Mutt - p. -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae