Brigadier John Tiltman a Giant Among Cryptanalysts
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

'Global Intelligence Co-Operation Versus Accountability: New Facets
This article was downloaded by: [Aldrich, Richard J.] On: 2 April 2009 Access details: Access Details: [subscription number 910154969] Publisher Routledge Informa Ltd Registered in England and Wales Registered Number: 1072954 Registered office: Mortimer House, 37-41 Mortimer Street, London W1T 3JH, UK Intelligence and National Security Publication details, including instructions for authors and subscription information: http://www.informaworld.com/smpp/title~content=t713672628 Global Intelligence Co-operation versus Accountability: New Facets to an Old Problem Richard J. Aldrich Online Publication Date: 01 February 2009 To cite this Article Aldrich, Richard J.(2009)'Global Intelligence Co-operation versus Accountability: New Facets to an Old Problem',Intelligence and National Security,24:1,26 — 56 To link to this Article: DOI: 10.1080/02684520902756812 URL: http://dx.doi.org/10.1080/02684520902756812 PLEASE SCROLL DOWN FOR ARTICLE Full terms and conditions of use: http://www.informaworld.com/terms-and-conditions-of-access.pdf This article may be used for research, teaching and private study purposes. Any substantial or systematic reproduction, re-distribution, re-selling, loan or sub-licensing, systematic supply or distribution in any form to anyone is expressly forbidden. The publisher does not give any warranty express or implied or make any representation that the contents will be complete or accurate or up to date. The accuracy of any instructions, formulae and drug doses should be independently verified with primary sources. The publisher shall not be liable for any loss, actions, claims, proceedings, demand or costs or damages whatsoever or howsoever caused arising directly or indirectly in connection with or arising out of the use of this material. -

JACKDAWS by Ken Follett Outline: 18T Draft-Annotated
1 JACKDAWS by Ken Follett Outline: 18t draft-annotated PG: Think ofa more interesting title with ''jackdaws'' in it KF: Jackdaws by Night? AZ: The story will work to the extend to which you putpressure on Flick and Dieter. For Flick, the pressure can come from: • Dieter • Weaknesses in her team • Weaknesses ofresistors • Conflicts between communists and others • Fortescue • Love relationships • Germans in general For Dieter, it can come from: • Flick • Other resistants • Baecker • Rommel • Some deep inner yearning for concord between Germany and France 2 Preface: Exactly 50 women were sent into France as secret agents by the Special Operations Executive during the Second World War. Ofthose, 36 survived the war. The other 14 gave their lives. This novel is dedicated to all ofthem. List their names? Prologue: Some Dieter PoVin the Prologue. Sainte-Cecile is a fictional small town near the cathedral city ofReims, in the champagne district ofnorth-east France. It is 14 May 1944, and the country has been under Nazi occupation for four years. At the end ofa hot Sunday afternoon, the church bell rings a languid toll for the evening service. The square in the town centre is dominated by a walled chateau on its north side. It is a beautiful seventeenth century building, and a German officer and his wife, tourists, are taking photographs of it with a large camera on a tripod. AZ: The chateau should be more of a "character". KF: It couldbe a Gothic fantasy castle with fairy-tale turrets. It couldhave a moat. It should be very difficult to enter in all sorts ofways On the east ofthe square is the church. -

How I Learned to Stop Worrying and Love the Bombe: Machine Research and Development and Bletchley Park
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by CURVE/open How I learned to stop worrying and love the Bombe: Machine Research and Development and Bletchley Park Smith, C Author post-print (accepted) deposited by Coventry University’s Repository Original citation & hyperlink: Smith, C 2014, 'How I learned to stop worrying and love the Bombe: Machine Research and Development and Bletchley Park' History of Science, vol 52, no. 2, pp. 200-222 https://dx.doi.org/10.1177/0073275314529861 DOI 10.1177/0073275314529861 ISSN 0073-2753 ESSN 1753-8564 Publisher: Sage Publications Copyright © and Moral Rights are retained by the author(s) and/ or other copyright owners. A copy can be downloaded for personal non-commercial research or study, without prior permission or charge. This item cannot be reproduced or quoted extensively from without first obtaining permission in writing from the copyright holder(s). The content must not be changed in any way or sold commercially in any format or medium without the formal permission of the copyright holders. This document is the author’s post-print version, incorporating any revisions agreed during the peer-review process. Some differences between the published version and this version may remain and you are advised to consult the published version if you wish to cite from it. Mechanising the Information War – Machine Research and Development and Bletchley Park Christopher Smith Abstract The Bombe machine was a key device in the cryptanalysis of the ciphers created by the machine system widely employed by the Axis powers during the Second World War – Enigma. -

VISIT to BLETCHLEY PARK
REPORT of STAR GROUP – VISIT to BLETCHLEY PARK It was 8-30 on the damp drizzly Monday morning of 5th October when our intrepid group of bleary-eyed third-agers left Keyworth to visit the former codebreaking and cipher centre at Bletchley Park. As we progressed south along the M1 motorway the weather started to clear and by the time we arrived in Milton Keynes the rain and drizzle had stopped. For me the first stop was a cup of coffee in the Block C Visitor Centre. We moved out of the Visitor Centre and towards the lake. We were told that many a wartime romantic coupling around this beautiful lake had led to marriage. The beautiful Bletchley Park Lake So… Moving on. We visited the Mansion House with it’s curious variety of styles of architecture. The original owners of the estate had travelled abroad extensively and each time they returned home they added an extension in the styles that they visited on their travels. The Mansion House At the Mansion we saw the sets that had been designed for the Film “The Imitation Game.” The attention to detail led one to feel that you were back there in the dark days of WWII. History of The Mansion Captain Ridley's Shooting Party The arrival of ‘Captain Ridley's Shooting Party’ at a mansion house in the Buckinghamshire countryside in late August 1938 was to set the scene for one of the most remarkable stories of World War Two. They had an air of friends enjoying a relaxed weekend together at a country house. -

41760779079990.Pdf
.CONFIS~Ti;~691 BBS'l'RIOHJB· THE DISTBIBUTION OF THIS SPECIAL TEXT WILL BE RESTRICTED TO REGULARLY ENROLLED EXTENSION COURSE STUDENTS, 'l'O MILITARY PERSONNEL, AND TO OTHER PERSONS COMING WITHIN THE MEANING OF THE PHRASE "FOR OFFICIAL USE ONLY/, ·. ARMY EXTENSION COURSES ~,· ·~~cY-l~~ I!LA)f'~'~ ~ \_ -·----------;-- --·· SPECIAL TEXT No. 166 ADVANCED MILITARY CRYPTOGRAPHY Szcoxn (19'3) EDmox PREPARED UNDER THE DIRECTION OF THE CHIEF SIGNAL OFFICER FOR USE WITH 'I1fE ARMY EXTENSION COURSES .',; ,_ • RSS'fRI<ffRB document contains information affecting the nat1 defense of the United States within the meaning of die · nage Act (U.S. C. -Y,. ~:>· 50: 31, 32). The transmission o · ocument · · or the revelation of its contents in any nl:an any unauthorized person is prohibited. + UNITED STATES GOVERNMENT PRINTING OFFICE ~ (o ~ ~ WASHINGTON : 19'3 . ,. 7.~0NFIDENTIAL Peclassified and approved for release by NSA on 01-14-2014 pursuant to E.O. 1352§ REF ID:A64691 ,·J/ 30 April 1959 Th.is document is re-graded "eEm'!BBrff " of DOD Directive 5200.l dated 8 ~ UP and by autharity of the Directar '2t1:.!i Security ~ncy. ' Paul~w~ S. Willard Colonel, AOC Adjutant Ge.nera.J. • ~· WAR DEPARTMENT, • WAsmNGTON, Februa1"JI S, 1948. Tbis revision of Special Text No. 166, Advanced Milita.ry Cryptog raphy (1935), for use with the Anny Extension Courses, is published for the information and guidance of all concerned. BY ORDEB OF THE SlilCBlilTAB.Y OF wAB! :,. G. o. M.ARSHAT,T., General, Ohiejoj8f4. OFFICIAL! JAMES A. ULIO, Major Gemral, 7?i.e Adjut,ant Geneml,. (XI) • SPECIAL TEXT NO. -

This Story Begins Sometime in the Early 1930S, When the Poles And
XYZ Prof. Włodzimierz Zawadzki Institute of Physics, Polish Academy of Sciences [email protected] Mathematicians are important, and not just in wartime. his story begins sometime in the early 1930s, developing programmable computers. Knox informed when the Poles and the French first took an Turing about the progress made by the Poles, and Tur- T interest in breaking the code generated by the ing built a sophisticated machine of his own that was Enigma encryption machines. The Enigma was a Ger- capable of cracking the increasingly complex Wehr- man-made electro-mechanical device that looked a bit macht codes. In a nod to the Polish pioneers, Turing like a typewriter with little lights, and prior to WWII too called his device “the bomb.” Despite the urgings they were available commercially. The decision to of British intelligence, Bertrand was reluctant to get crack the Enigma code proved far-sighted when the the Polish team out of Nazi-occupied France and into machines underwent a complex and classified rede- Bletchley Park. The team ended up in southern France sign for military purposes in the run-up to the war. and, at one point, in North Africa. Despite their con- Codebreaking challenges had earlier been handled tinuing insights, the Polish team’s direct contribution by linguists, but the Enigma’s rotor-encrypted codes to the breaking of the Enigma code diminished. required codebreakers with a mathematical back- When the United States joined the war, one of the ground. The Polish Cipher Bureau, an intelligence out- most difficult aspects of Enigma decryption focused fit located near Warsaw, set up a task force consisting on the communications of the German U-boat fleet, of Marian Rejewski, Henryk Zygalski and Jerzy Róży- which harassed American supply convoys crossing cki. -

Cryptographyorhioohulmuoft CRYPTOGRAPHY OR the HISTORY, PRINCIPLES, and PRACTICE of CIPHER-WRITING
Digitized by the Internet Archive in 2007 with funding from IVIicrosoft Corporation http://www.archive.org/details/cryptographyorhiOOhulmuoft CRYPTOGRAPHY OR THE HISTORY, PRINCIPLES, AND PRACTICE OF CIPHER-WRITING ^ w >TOGRA OR The History, Principles, and Practice OF CIPHER-WRITING e<^ BY Fl^EDWARD HULME, F.L.S., F.S.A U\ AUTHOR OF "familiar WILD FLOWERS," " MYTHLAND," " NATURAL HISTORY LORE AND LEGEND," "the birth and development OF ORNAMENT," " WAYSIDK SKETCHES," ETC Heres noiv mystery and hieroglyphic Ben Jonson— The Alchemysi. LONDON WARWICK HOUSE, SALISBURY SQUARE, E.C NEW YORK AND MELBOURNE — CONTENTS CHAPTER I PAGE Meaning of cryptography—Objections to its study—Its legitimate use and value—Historic examples of its employment—Deliglit in the mysterious—Many other ways of conveying secret information—Symbolism of action—The spoken word imprisoned and dispatched —A matter not necessarily secret because one cannot understand it — Egyptian hieroglypliics — Chinese characters—Indian mutiny Greek—Ancient Biblical cryptogram — Sheshach of Jeremiah — Sir Henry Eawlinson thereon—Statements for and against Julius Caesar's secret code—The waxed tablet of Demaratus—Difference between hidden and secret writing—The shaven head a writing tablet—Charle- magne and Alfred the Great as cryptographic experts —Mediaeval authorities—Trithemius the Benedictine " — " Steganographia —Dabbling in the black art Dr. Dee—Batista Porta's book on "Natural Majick" —Invisible writing—Chemical methods by vitriol, alum, etc. —Writing on glass or crystal—Papal In- quisition—Disappearing writing—Messages wrapped round rollers—Two methods—A slave's back the writing surface—Chemical methods of no great value ordinarily—Disadvantages of use— Action of light and heat—Chloride of cobalt, sulphate of copper, etc. -
PDF File, 139.89 KB
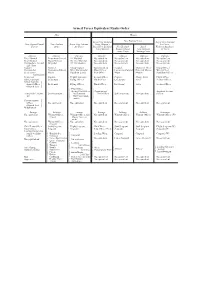
Armed Forces Equivalent Ranks Order Men Women Royal New Zealand New Zealand Army Royal New Zealand New Zealand Naval New Zealand Royal New Zealand Navy: Women’s Air Force: Forces Army Air Force Royal New Zealand New Zealand Royal Women’s Auxilliary Naval Service Women’s Royal New Zealand Air Force Army Corps Nursing Corps Officers Officers Officers Officers Officers Officers Officers Vice-Admiral Lieutenant-General Air Marshal No equivalent No equivalent No equivalent No equivalent Rear-Admiral Major-General Air Vice-Marshal No equivalent No equivalent No equivalent No equivalent Commodore, 1st and Brigadier Air Commodore No equivalent No equivalent No equivalent No equivalent 2nd Class Captain Colonel Group Captain Superintendent Colonel Matron-in-Chief Group Officer Commander Lieutenant-Colonel Wing Commander Chief Officer Lieutenant-Colonel Principal Matron Wing Officer Lieutentant- Major Squadron Leader First Officer Major Matron Squadron Officer Commander Lieutenant Captain Flight Lieutenant Second Officer Captain Charge Sister Flight Officer Sub-Lieutenant Lieutenant Flying Officer Third Officer Lieutenant Sister Section Officer Senior Commis- sioned Officer Lieutenant Flying Officer Third Officer Lieutenant Sister Section Officer (Branch List) { { Pilot Officer Acting Pilot Officer Probationary Assistant Section Acting Sub-Lieuten- 2nd Lieutenant but junior to Third Officer 2nd Lieutenant No equivalent Officer ant Navy and Army { ranks) Commissioned Officer No equivalent No equivalent No equivalent No equivalent No equivalent No -

Remnants of Al-Qaeda in Saudi Arabia: Current Assessment
Remnants of al-Qaeda in Saudi Arabia: Current Assessment Washington, DC - November 9th, 2006 Center for Strategic and International Studies Nawaf Obaid Managing Director Counter-Terrorism in the Kingdom • Since May 2003, Saudi security forces have captured ~845 individuals with direct or indirect links to al-Qaeda. • Over 400 have attended “ideological re-education programs.” • 264 al-Qaeda commanders, logisticians, theologians, financiers and fighters have been captured or killed. • Of 26 members that comprised first “most wanted” list, all but one have been killed or captured and all five initial al-Qaeda cells have been identified, infiltrated and decimated. • Of 36 second-tier operatives comprising second “most wanted” list: • 20 had already fled the Kingdom when list was published • Of remaining 16, only 4 have not been killed or captured • This group carried out recent failed attack on Abqaiq • Over 25 major terrorist attacks have been foiled since May 2003. Saudi National Security Assessment Project 2 Counter-Terrorism in the Kingdom (cont.) • Four of the main routes used by terrorists to smuggle themselves, fighters, weapons and drugs have been identified. • Close surveillance had resulted in hundreds of interceptions on the Saudi-Yemeni border. • The largest of the al-Qaeda safe houses used for logistical support has been destroyed. As have three in Riyadh, two in Qassim, two in the Eastern Province, one in Najran and three in the Western Province (Makkah, Madinah and Jeddah). • Several arrests of fighters returning from Afghanistan and Pakistan have been made over the past several months. Important Note: They had no attack plan and no clear command structure, focused exclusively on avoiding Saudi security services. -

The First Americans the 1941 US Codebreaking Mission to Bletchley Park
United States Cryptologic History The First Americans The 1941 US Codebreaking Mission to Bletchley Park Special series | Volume 12 | 2016 Center for Cryptologic History David J. Sherman is Associate Director for Policy and Records at the National Security Agency. A graduate of Duke University, he holds a doctorate in Slavic Studies from Cornell University, where he taught for three years. He also is a graduate of the CAPSTONE General/Flag Officer Course at the National Defense University, the Intelligence Community Senior Leadership Program, and the Alexander S. Pushkin Institute of the Russian Language in Moscow. He has served as Associate Dean for Academic Programs at the National War College and while there taught courses on strategy, inter- national relations, and intelligence. Among his other government assignments include ones as NSA’s representative to the Office of the Secretary of Defense, as Director for Intelligence Programs at the National Security Council, and on the staff of the National Economic Council. This publication presents a historical perspective for informational and educational purposes, is the result of independent research, and does not necessarily reflect a position of NSA/CSS or any other US government entity. This publication is distributed free by the National Security Agency. If you would like additional copies, please email [email protected] or write to: Center for Cryptologic History National Security Agency 9800 Savage Road, Suite 6886 Fort George G. Meade, MD 20755 Cover: (Top) Navy Department building, with Washington Monument in center distance, 1918 or 1919; (bottom) Bletchley Park mansion, headquarters of UK codebreaking, 1939 UNITED STATES CRYPTOLOGIC HISTORY The First Americans The 1941 US Codebreaking Mission to Bletchley Park David Sherman National Security Agency Center for Cryptologic History 2016 Second Printing Contents Foreword ................................................................................ -

Enigma Cryptanalysis - Beginnings
Enigma Cryptanalysis - Beginnings Gaurish Korpal∗ [email protected] July 15, 2015 Abstract Any message may be hidden in two basic ways. The methods of steganography conceal the very existence of the message, for example invisible inks and microdots. The methods of cryptography, on the other hand, do not conceal the presence of a secret message but render it unintelligible as ciphertext, to outsiders by various transformations of the plaintext. Breaking ciphers require ingenuity, creativity and a little math. In this article our focus will be on breaking Enigma ciphers. The skill involved in breaking ciphers is called cryptanalysis. Keywords. Enigma, cryptanalysis, cypher, Caesar, Vigen`ere,Rejewski, Zygalski, Bomba, Bombe 1 Cipher not Code A code is a mapping from some meaningful unit (word, sentence, phrase) into something else (usually a shorter group of symbols). A code requires a codebook, it is simply a list of these mappings. For example we could make up a code where the word Apple is written as 67, historical example of this is \Zimmermann Telegram Code" for more details refer [7]. Ciphers do not involve meaning. Instead they are mechanical operations (known as algorithms) which are performed on the individual or small chunks of letters. A code is stored as a mapping in a codebook, while ciphers transform individual symbols according to an algorithm. It was definitively stated in 1883 by the Dutch linguist Auguste Kerckhoffs von Nieuwenhof in his book La Cryptographie militaire: Kerckhoffs' Principle: The security of a cryptosystem must not depend on keeping secret the crypto-algorithm. The security depends only on keeping secret the key. -

Román Ceano © Román Ceano
La máquina enigma Román Ceano © Román Ceano. Todos los derechos reservados. El libro fue compilado de http://www.kriptopolis.org/enigma La fotografía sacada de http://enigma.wikispaces.com/file/view/enigma.jpg/30598271 Preludio En el verano de 1938, una pequeña localidad del condado de Buckingham vio perturbada su tranquilidad por la llegada de unos estrafalarios visitantes. Se trataba de hombres de aspecto próspero pero descuidado, acompañados por chicas que los lugareños juzgaron sospechosamente guapas y alegres. Estaban dirigidos al parecer por un tal Capitán Ridley, y decían que el motivo de su presencia era la caza. Ninguna de las camareras que les servían la cena en los hotelitos de la zona les oyó comentar anécdota cinegética alguna, lo cual era congruente con el hecho de que faltaban meses para la temporada. Lo que sí les oyeron comentar eran los opíparos almuerzos con que se obsequiaban. Estos debían tener lugar en la propiedad llamada Bletchley Park, puesto que allí se dirigían todos en sus coches cada mañana y de allí volvían cada tarde. Todo el mundo en Bletchley conocía la finca, sin duda la mejor de la comarca. La había creado sesenta años antes un exitoso corredor de bolsa de Londres llamado Herbert Leon, deseoso de disfrutar de la vida rural de las clases altas victorianas. Presidía la finca una mansión cuya fachada lucía una grotesca mezcla de estilos, que imitaba los palacios de las grandes familias rurales que habían sido reformados varias veces durante centurias. En la parte trasera había un gran patio, separado del edificio principal, donde estaban las cuadras, una enorme despensa donde guardar fruta fresca para el invierno y varias edificaciones auxiliares que recreaban de manera muy fidedigna el centro de operaciones de una propiedad rural.