Predatory Innovation: an Analysis of Allied Orthopedic V
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Wikipedia: Design of the FAT File System
Design of the FAT file system A FAT file system is a specific type of computer file system architecture and FAT a family of industry-standard file systems utilizing it. Developer(s) Microsoft, SCP, IBM, [3] The FAT file system is a legacy file system which is simple and robust. It Compaq, Digital offers good performance even in very light-weight implementations, but Research, Novell, cannot deliver the same performance, reliability and scalability as some Caldera modern file systems. It is, however, supported for compatibility reasons by Full name File Allocation Table: nearly all currently developed operating systems for personal computers and FAT12 (12- many home computers, mobile devices and embedded systems, and thus is a bit version), well suited format for data exchange between computers and devices of almost FAT16 (16- any type and age from 1981 through the present. bit versions), Originally designed in 1977 for use on floppy disks, FAT was soon adapted and FAT32 (32-bit version used almost universally on hard disks throughout the DOS and Windows 9x with 28 bits used), eras for two decades. Today, FAT file systems are still commonly found on exFAT (64- floppy disks, USB sticks, flash and other solid-state memory cards and bit versions) modules, and many portable and embedded devices. DCF implements FAT as Introduced 1977 (Standalone the standard file system for digital cameras since 1998.[4] FAT is also utilized Disk BASIC-80) for the EFI system partition (partition type 0xEF) in the boot stage of EFI- FAT12: August 1980 compliant computers. (SCP QDOS) FAT16: August 1984 For floppy disks, FAT has been standardized as ECMA-107[5] and (IBM PC DOS 3.0) ISO/IEC 9293:1994[6] (superseding ISO 9293:1987[7]). -

DR DOS for the Zfx86
DR DOS for the ZFx86 Cost Effective, Reliable, Rapid Deployment of Embedded Systems w DR DOS on the ZFx86 gets products to market quickly at the lowest development and ownership cost. w Thousands of compatible applications, drivers and utilities available free or at minimal cost. w Full documentation available. DR DOS 7.03 Key Features of DR DOS Online Manual - DRDOS is supplied with a complete The ideal embedded DOS system, online manual that contains detailed information about all designed for out-of-the-box of the features of the operating system including the basic implementation into ROM or Flash commands, and the advanced utilities. It also has online ROM with tools and associated help available for all its commands. documents available in the DRDOS Memory Management - Memory management features OEM Documentation Kit. include a set of device drivers and commands that enable w 100% MS-DOS 6.22 compatible.. you to manage memory efficiently and make as much memory as possible available to your applications. w Comprehensive DOS utility set DOS Protected Mode Services - DOS Protected Mode w Multitasking, with API for developers Services (DPMS) interface allows specially-implemented w DPMS memory manager in addition to DPMI device drivers and TSRs to operate in extended memory. w Stacker disk compression This makes more memory within the first megabyte w NWCACHE - disk caching program available to applications and other conventionally-written drivers and TSRs. Both Stacker* (the disk compression w EMM386 memory manager program), and NWCACHE (the disk cache) use DPMS. w DOS Protected Mode Services (DPMS) Disk Compression - The disk compression component w Multitasking enables you to store more information by compressing the w DR-DOS provides a full multitasking environment data. -

DR-Webspyder R Graphicaldos Web Browser
DR-WebSpyder R GraphicalDOS Web Browser A fcully ustomizable, > Information Kiosks DRlsow ystem r equirement > Network Computers for > Internet-Set-top Boxes Internet Browser > Compact embedded devices with display everage the proven DR-WebSpyder equips Many OEMs base their power and reliability of embedded OEMs of compact, embedded solutions on LDR-DOSR with a new x86-based devices with a industry standard PC graphical interface and set graphical Web browser. hardware to reduce the risk of Web protocols. Bring Running on DR-DOS (or any and cost associated with Internet access to your other current version of development. This same devices quickly and easily DOS), this fully configurable, logic applies to the software with DR-WebSpyderR . Low HTML 3.2 browser aids that is used. Embedded risk and low system developers in customizing OEMs that choose requirements are the key the navigation bar, fonts, DR-WebSpyder as the benefits to OEMs and system setup pages, E-mail, system browser and DR-DOS as the integrators. defaults, and more. operating system expand their available resources with Caldera DR-WebSpyder is a DR-WebSpyder also allows an extremely large pool of customizable, high- developers to pre-configure experienced developers and performance Web browser the browser to connect with proven development tools for your interactive specific service providers, for DOS. information kiosk, network making it easy for the end computer, Internet set-top user to simply plug in and The combination of DR-DOS box, and hand-held device. browse. and DR-WebSpyder creates the thinnest graphical DR-WebSpyder with navigation bar and on-screen keyboard Internet access client available. -

The Microsoft Chronicles 205 Rudolph J.R
digitalcommons.nyls.edu Faculty Scholarship Articles & Chapters 2010 The icrM osoft hrC onicles Rudolph J.R. Peritz New York Law School Follow this and additional works at: https://digitalcommons.nyls.edu/fac_articles_chapters Part of the Antitrust and Trade Regulation Commons, and the Intellectual Property Law Commons Recommended Citation Peritz, Rudolph J.R., "The icrM osoft hrC onicles" (2010). Articles & Chapters. 1137. https://digitalcommons.nyls.edu/fac_articles_chapters/1137 This Article is brought to you for free and open access by the Faculty Scholarship at DigitalCommons@NYLS. It has been accepted for inclusion in Articles & Chapters by an authorized administrator of DigitalCommons@NYLS. Microsoft on Trial Legal and Economic Analysis of a Transatlantic Antitrust Case Edited by Luca Rubini Lecturer and Deputy Director of the Institute of European Law, Birmingham Law School, UK NEW HORIZONS IN COMPETITION LAW AND ECONOMICS Edward Elgar Cheltenham, UK• Northampton, MA, USA ( Tc-lS ~ ~;Lt tJ ~ fl 53f ;z.,,ot C © The editor and contributors severally 2010 All rights reserved. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical or photocopying, recording, or otherwise without the prior permission of the publisher. Published by Edward Elgar Publishing Limited The Lypiatts 15 Lansdown Road Cheltenham GlosGL502JA UK Edward Elgar Publishing, Inc. William Pratt House 9 Dewey Court Northampton Massachusetts O1060 USA A catalogue record for this book is available from the British Library Library of Congress Control Number: 2009941150 Mixed Sources Produd group from well-managed forests and other controlled sources www.fsc.org Cert no. -
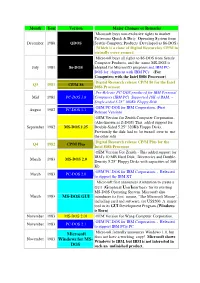
Microsoft Windows for MS
Month Year Version Major Changes or Remarks Microsoft buys non-exclusive rights to market Pattersons Quick & Dirty Operating System from December 1980 QDOS Seattle Computer Products (Developed as 86-DOS) (Which is a clone of Digital Researches C P/M in virtually every respect) Microsoft buys all rights to 86-DOS from Seattle Computer Products, and the name MS-DOS is July 1981 86-DOS adopted for Microsoft's purposes and IBM PC- DOS for shipment with IBM PCs (For Computers with the Intel 8086 Processor) Digital Research release CP/M 86 for the Intel Q3 1981 CP/M 86 8086 Processer Pre-Release PC-DOS produced for IBM Personal Mid 1981 PC-DOS 1.0 Computers (IBM PC) Supported 16K of RAM, ~ Single-sided 5.25" 160Kb Floppy Disk OEM PC-DOS for IBM Corporation. (First August 1982 PC-DOS 1.1 Release Version) OEM Version for Zenith Computer Corporation.. (Also known as Z-DOS) This added support for September 1982 MS-DOS 1.25 Double-Sided 5.25" 320Kb Floppy Disks. Previously the disk had to be turned over to use the other side Digital Research release CP/M Plus for the Q4 1982 CP/M Plus Intel 8086 Processer OEM Version For Zenith - This added support for IBM's 10 MB Hard Disk, Directories and Double- March 1983 MS-DOS 2.0 Density 5.25" Floppy Disks with capacities of 360 Kb OEM PC-DOS for IBM Corporation. - Released March 1983 PC-DOS 2.0 to support the IBM XT Microsoft first announces it intention to create a GUI (Graphical User Interface) for its existing MS-DOS Operating System. -

INDUSTRY LEADERS INVEST in CALDERA SYSTEMS, INC. Sun
INDUSTRY LEADERS INVEST IN CALDERA SYSTEMS, INC. Sun, Citrix, Novell, SCO, Egan-Managed Capital and Chicago Venture PartnersTake Equity Positions in Linux Company. Submitted by: Archetype (Text100) Tuesday, 11 January 2000 OREM, UT - January 10, 2000 - Caldera Systems, Inc., today announced that it will receive $30 million in private equity financing from technology and investment leaders including: * Sun Microsystems, Inc. * Citrix * Novell * SCO * Chicago Venture Partners * Egan-Managed Capital Caldera Systems will use the capital provided by these investors to fund operations and accelerate the growth and acceptance of Linux. "We are encouraged by the support of these technology leaders - which we take as an endorsement of the Linux industry as a whole and the Open Source movement in particular - and we look forward to their strategic counsel," said Ransom Love, President and CEO of Caldera Systems, Inc. "Given our strategic goal of enabling access to any application on any platform with any device, an investment in a Linux company such as Caldera makes perfect sense," according to John Cunningham, Citrix Chief Financial Officer. "Sun's investment in Caldera is a testament to our support of Open computing," said Jonathan Schwartz, vice president of Sun's Equity Investment Portfolio. "We're the leading provider of UNIX server systems and a longtime supporter and supplier of Open Source technologies," said Mike Orr, senior vice president of Marketing, SCO. "We look forward to furthering the relationship with Caldera by working together on initiatives that bring Linux and UNIX closer together." "Novell is the broadest supplier of Net infrastructure software," said Carl Ledbetter, Novell senior vice president for business and corporate development. -

Collesarsi Ad Internet \
REVIVAL IN RETE: I VECCHI SISTEMI OPERATIVI NAVIGANO ANCORA S Collesarsi ad internet \ r> Fate rivivere il vostro vecchio 486 trasformandolo in un internet box dos per navigare in rete senza spendere troppo di Marco lannacone [email protected] L Molti lettori si chiederanno che motivo possa esserci ad utilizzare stema potrebbe avere i requisiti necessari per gestire applicazioni un sistema operativo che ha oltre 15 anni per accedere alla grande grafiche per navigare nel web e gestire la posta elettronica. rete, quando con meno di due milioni è possibile comprare un La diffusione del World Wide Web ha dimostrato l'importanza della recentissimo Pentium multimediale equipaggiato con l'ultima ver filosofia client-server, nella quale i dati e i servizi sono messi a di sione di Win95 (OSR2). In realtà proprio questo (sbagliato) modo di sposizione da macchine dedicate (i server), mentre l'utente finale pensare ha fatto si che oggi per potere scrivere un documento, (client) deve solo visualizzarli tramite apposite applicazioni. un'e-mail, o fare dei calcoli sia necessario disporre di una macchina Le informazioni a disposizione sono moltissime, ed è inutile sovrac con almeno 32Mb di ram e un disco rigido da 2Gb. caricare la propria macchina con pesanti elaborazioni quando si I programmi (e i sistemi operativi) di casa Microsoft sembrano fare può fare svolgere il lavoro duro ad un computer remoto, per poi a gara nel richiedere un numero sempre più alto di risorse, pur for ottenere il risultato comodamente sul proprio schermo. Seguendo la nendo funzionalità simili generazione dopo generazione. E' davvero logica evoluzione di questa filosofia, che senso ha caricare sulla un approccio completamente diverso da quello riscontrabile in altri propria macchina un mastodontico word processor (di cui magari si sistemi operativi, quali ad esempio Linux, FreeBSD, Qnx, che sono usa solo una piccola parte delle funzioni) quando si potrebbe utiliz tuff oggi in grado di funzionare sia su 386 con 2Mb di ram che su zarne uno remoto? grossi server della SUN (ovviamente con prestazioni diverse). -
Closed Systems January 1St, 2021
1980 1981 1982 1983 1984 1985 1986 1987 1988 1989 1990 1991 1992 1993 1994 1995 1996 1997 1998 1999 2000 2001 2002 2003 2004 Enhanced DR-DOS 7.01.07 2005 2006 2007 2008 2009 2010 2011 Enhanced DR-DOS 7.01.08 2012 2013 2014 2015 2016 2017 2018 2019 2020 FreeDOS alpha 0.05 DR-DOS/OpenDOS 7.01.01 march 6, 2005 july 21, 2011 FreeDOS FreeDOS alpha 0.1 FreeDOS alpha 0.2 FreeDOS beta 0.3 FreeDOS beta 0.4 FreeDOS beta 0.5 FreeDOS beta 0.6 FreeDOS beta 0.7 FreeDOS beta 0.8 july 2002 FreeDOS beta 0.9 FreeDOS 1.0 FreeDOS 1.1 january 12, 1998 april 21, 1999 FreeDOS 1.2 DR-DOS 3.41 june 29, 1994 march 25, 1998 october 28, 1998 april 9, 2000 august 10, 2000 march 18, 2001 september 7, 2001 april 7, 2002 september 28, 2004 september 3, 2006 january 2, 2012 december 25, 2016 DOS Plus 1.0 DOS Plus 2.01 DR-DOS 3.31 DR-DOS 5.0 DR-DOS 6.0 Novell DOS 7.0 OpenDOS 7.01 Caldera DR-OpenDOS 7.02 DR-DOS 7.04 DR-DOS 7.05 DR-DOS 8.0 DR-DOS 8.1 1985 may 28, 1988 june 1989 may 1990 december 1993 february 1997 december 1997 Caldera DR-DOS 7.02 DR-DOS 7.03 november 30, 1999 october 2005 september 1991 march 1998 january 6, 1999 august 19, 1999 march 30, 2004 Xbox Xbox Xbox Xbox 360 (announced) Xbox Xbox 360 Xbox One (beta) (announced) november 15, 2001 (announced) march 9, 2000 may 12, 2005 november 22, 2005 november 22, 2013 october 1999 january 6, 2001 Windows Embedded for Point of Service Windows Server 2008 Foundation april 1, 2009 MS-DOS 1.24 MS-DOS 1.25 MS-DOS 2.01 MS-DOS 2.11 MS-DOS 3.05 MS-DOS 3.3 MS-DOS 3.3 MS-DOS 3.31 MS-DOS 4.01 MS-DOS 5.0 MS-DOS 5.0a MS-DOS -

C:\Documents and Settings\Pxr\Desktop\Newman
A Symposium Honoring Judge Jon O. Newman’s Thirty Years on the Bench forthcoming New York Law Review © 2002 Peter S. Menell Envisioning Copyright Law’s Digital Future Peter S. Menell1 “May you live in interesting times.”2 Copyright initially developed in response to the printing press and gradually evolved to encompass other methods of mechanically storing and reproducing works of authorship, such as photography, motion pictures, and sound recordings. The advent of broadcasting -- the ability to perform works at distant points -- led to the expansion of copyright to encompass exploitation of creative expression in new markets. The digital revolution represents a third distinct wave of technological innovation that portends significant changes in copyright protection. By bringing about new modes of expression (such as computer programming and digital sampling of music) and empowering anyone with a computer and an Internet connection to flawlessly, inexpensively, and instantaneously reproduce and distribute works of authorship on a wide scale, digital technology represents possibly the most profound challenge to copyright law. This article divides the analysis of digital technology into two categories: (1) squeezing computer software within copyright’s non-functionally oriented protection regime and (2) developing new rules and governance institutions to address the ease of reproduction and porosity of the digital platform. Part I of the article traces the two decades of evolution of copyright protection for computer software and demonstrates that copyright law has proven quite adaptable to this hybrid of expressive and utilitarian creativity. The courts have enabled copyright law to serve effectively as an anti-piracy regime without allowing it to intrude unduly into patent law’s domain. -

IBM Further Extends the Mqseries Version 5 Product Family
Software Announcement October 3, 2000 IBM Further Extends the MQSeries Version 5 Product Family Overview A new Capacity Unit table applies to (Refer to the Planning Information all MQSeries Version 5.2 platforms section.) Companies need to implement and also to all new orders for other e-business integration rapidly. base MQSeries products priced by MQSeries messaging is a simple Capacity Units. (Refer to the way to couple systems and Planning Information section.) applications together. This allows Internet users, and other Key Prerequisites applications, controlled access to existing data, such as account • MQSeries for AIX, V5.2: transactions. RS/6000 running AIX 4.3.2 or 4.3.3 Business integration across many applications is a common element of • MQSeries for AS/400, V5.2: successful implementation. Other AS/400 running OS/400 V4R4 or MQSeries family members, such as V4R5 MQSeries Integrator and MQSeries • MQSeries for HP-UX, V5.2: HP Workflow, give you the tools to add machines or Stratus Continuum, value outside the basic message all running HP-UX V10.20 or V11.x queuing paradigm. • MQSeries for Sun Solaris, V5.2: MQSeries, Version 5.2 brings new SunSPARC or Sun UltraSPARC — enhanced performance levels and desktop or server running Sun extends the set of supported Solaris 2.6, 7, or 8 platforms. Now MQSeries supports many offerings of Linux, including • MQSeries for Linux, V5.2: Intel Caldera OpenLinux, Red Hat, SuSE, 32-bit or compatible systems and TurboLinux, as well as support capable of running Linux for Microsoft Windows 2000. (Kernel 2.2) Operation is also added on a new • MQSeries for Windows NT and release of Sun Solaris and for Windows 2000, V5.2: Intel or existing releases of AIX , HP-UX, compatible systems capable of AS/400 , and Windows NT . -

Emutos and Atari 16/32 Bit Machines
EMUTOS AND ATARI 16/32 BIT MACHINES Very briefly ;-) Christian Zietz – September 2020 1985 Atari ST • 68000 CPU @ 8 MHz • Initially 512 kB RAM, later up to 4 MB • 2 color modes and a high-res (640 x 400) monochrome mode • Initially separate floppy drive, later builtin 720k drive • MIDI Atari 1040STF – © Bill Bertram, 2006 1985 TOS • GEM UI and GEMDOS originally licensed from Digital Research • But independently developed further by Atari • Entirely in ROM • Single-task • GUI with desktop metaphor • Text mode for command line applications also available 1989 1990/1991 1992 Atari STE Atari TT & MegaSTE Atari Falcon • More colors • Workstations • 68030 • PCM sound • MegaSTE: 16 MHz, • DSP • TOS 1.06/1.62 FPU, VME bus • True-color graphics • TT: 68030, FPU, more • TOS 4 RAM, VME bus, high- res up to 1280 x 960 • TOS 2 & 3 Sea Of Colour demo by Dead Hackers Society on Atari STE Atari TT – by Tim Kovack Atari Falcon – © Wikipedia user LosHawlos 1996 1999 2001 Atari Corp. ceases Caldera releases PC EmuTOS development operations GEM under GPL begins • IP rights go to game • Shares a common • Born out of necessity: company Hasbro / ancestor with TOS bundle a legal TOS Infogrames / Atari with emulators • But they diverged • Atari TOS is still • Based on PC GEM copyrighted • E.g. restrictions code imposed by an Apple lawsuit • Own development of low level BIOS/XBIOS for Atari HW • Many improvements since! 2020: EMUTOS 1.0 What makes EmuTOS special? Supports all Atari computers and some non-Atari machines (even Amiga!) Also great for emulators, e.g., API to Aranym and Hatari Provided in many variants (ROM & RAM versions) in several languages Built-in hard disk driver with PC (FAT16) partition and filesystem support Built-in command line interface (EmuCON) Support for 3rd party hardware, e.g. -

SCO Sues Novell to Stay Afloat
Now They Own It, Now They Don’t: SCO Sues Novell to Stay Afloat Eben Moglen∗ February 5, 2004 The SCO licensing campaign—which has been all bark and no bite since its introduction by way of threatening letters to the Fortune 1500 last summer—lost a wheel last month, and is now headed for the wall. From the beginning of this irresponsible attack on the freedom of free software, SCO has promulgated public positions about the nature of its supposed rights that conflicted with facts known to the free software com- munity, and relied upon legal positions that were untenable given the real state of facts. SCO supposedly responded to demands to see some evidence of code copied from Sys V Unix into the Linux program, first in a pub- lic presentation in August and then in a court filing in January. But both “demonstrations” actually showed that SCO was claiming copyright in- fringement in material whose copyright it didn’t own. Now, a new party has begun casting serious legal doubt on SCO’s ownership of the rights on which it bases its demands for license fees, to the complete destruction of SCO’s licensing campaign. The new party raising fundamental legal doubt about SCO’s copyrights is SCO itself. 1 You Can’t Sue Over What You Don’t Own The SCO Group claims to hold copyrights in AT&T’s implementations of Unix as a consequence of a conveyance by Novell to SCO’s predecessor in interest, Caldera. Novell and SCO have disagreed throughout about the ∗Eben Moglen is professor of law at Columbia University Law School.