A: Irst3responses.Rel.Wpd
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

GBCC-CIS-1 Page 1 Micro-Soft’S Macro-Impact
CIS111 GBCC Renee Dodge CIS111 Mid-Term – Fall 2010 For your mid-term, I would like you to conduct some research on the history of computers. Select a milestone or event that you feel had a significant impact on the overall development of computers and how we use computers today. Be sure you not only provide your opinion as to why you feel this milestone is significant, but also provide historical proof - actual facts as to how this event shaped the development and use of computers. For this assignment, please complete the following: 1. Choose a topic 2. Research your topic and locate at least 5 different sources of information, overall. o At least 3 sources should be Internet websites. o Remember: Wikipedia is NOT an acceptable research source. 3. In addition to the Internet, you should also utilize the library online resources (EBSCO database, e-Books, etc). o At least 2 different sources of information should be online library resources. o If you have never used the library online resources before, you may ask me for a brief overview of how to use them or see Becky Clerkin in the library for help. 4. Include your research findings in a 5-page paper and be sure to properly cite where you found your information. If you are not sure how to cite references check out the following link: How to Cite Books, Magazines, and Web Sites in a Research Paper: http://www.lib.duke.edu/libguide/works_cited.htm 5. Upload your research paper to the Digital Drop BoX no later than Wednesday, October 27th at 11:59pm. -

A Guide to Discuss Ethical Issues in Digital Research Second Edition
Ethical challenges in digital research 2nd edition ETHICAL CHALLENGES IN DIGITAL RESEARCH A guide to discuss ethical issues in digital research Second edition Ethical challenges in digital research 2nd edition Ethical challenges in digital research – A guide to discuss ethical issues in digital research Second edition January 2020 Developed by DIGETIK at Aalborg University as part of DIGHUMLAB Authors Line Lisberg Christensen, Research Assistant Malene Charlotte Larsen, Associate Professor Layout Steffen Madsen, DIGHUMLAB i Ethical challenges in digital research 2nd edition I. Introduction to document The ever-changing development of digital technologies and digital infrastructure makes it necessary for us as researchers to change approaches to digital research within the humanities. In terms of research ethics, we can no longer use traditional laws and guidelines that only match the non-digital world. In a time where it is necessary to change and re-think our ways of doing research, we bring to you this second version of Ethical Challenges in Digital Research to initiate discussions about ethical research and to help guide you in your digital research. The compound may serve you as a guideline to ethical research, a helpful tool to those in need of inspiration or merely as a list of literature that is relevant to your field, whether that is: big data, surveillance, privacy, games and gamification, ethics in studies with children and adolescents, health research, journalism, ethnographic studies, visual methods, vulnerable groups, web archives, economy, risky business for researchers or one of the many other categories in this collection of ethical digital research. We initially created this document with the intention of helping scholars reflect and discuss the ethical dimensions of their digital research, whilst providing guidance and insight about how to deal with these issues. -
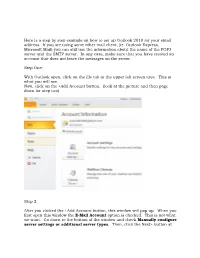
Here Is a Step by Step Example on How to Set up Outlook 2010 for Your Email Address
Here is a step by step example on how to set up Outlook 2010 for your email address. If you are using some other mail client, (ie. Outlook Express, Microsoft Mail) you can still use the information about the name of the POP3 server and the SMTP server. In any case, make sure that you have created an account that does not leave the messages on the server. Step One: With Outlook open, click on the file tab in the upper left screen area. This is what you will see. Now, click on the +Add Account button. (look at the picture and then page down for step two) Step 2: After you clicked the +Add Account button, this window will pop up. When you first open this window the E-Mail Account option is checked. This is not what we want. Go down to the bottom of the window and check Manually configure server settings or additional server types. Then, click the Next> button at the bottom of the window. (look at the picture and then page down for step three) Step 3: After you clicked the Next > button, this window will pop up. This time, the correct selection is already chosen. If, for some reason it is not checked, please check the Internet E-Mail and then click the Next> button at the bottom of the window. look at the picture and then page down for step four) Step 4: After you clicked the Next> button, this window will pop up. User Informatio n: This window is set up for the Red Knights Regalia Treasurer. -

Concurrent CP/M-86 User's Guide 1.1 What Concurrent CP/M-86 Is
Concurrent CP/M-86™ Operating System Concurrent CP/M-86™ Operating System User's Guide Copyright © 1982 Digital Research P.O. Box -579 160 Central Avenue Pacific Grove, CA 93950 (408) 649-3896 TWX 910 360 5001 All Rights Reserved COPYRIGHT Copyr ight © 1982 by Digi tal Research. All r igh ts reserved. No part of this pUblication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any language or compu ter language, in any form or by any means, electronic, mechanical, magnetic, optical, chemical, manual or otherwise, without the prior written permiss ion of Digital Research, Post Off ice Box 579, Pacific Grove, California, 93950. This manual is, however, tutorial in nature. Thus, the reader is granted permission to include the example programs, either in whole or in part, in his own programs. DISCLAIMER Digital Research makes no representations or warranties with respect to the contents hereof and specifically disclaims any ,implied warranties of merchantabil i ty or fitness for any particular purpose. Further, Digital Research reserves the right to revise this publication and to make changes f rom time to time in the content hereof wi thou t obligation of Digital Research to notify any person of such revision or changes. TRADEMARKS CP/M is a registered trademark of Digital Research. ASM-86, CP/M-86, Concurrent CP/M-86 and DDT-86 are trademarks of Digital Research. ED and TEX are utilities of Digital Research. Intel is a registered trademark of Intel Corporation. The IBM Personal Computer is a trade name of International Business Machines. -

Twenty Years of Berkeley Unix : from AT&T-Owned to Freely
Twenty Years of Berkeley Unix : From AT&T-Owned to Freely Redistributable Marshall Kirk McKusick Early History Ken Thompson and Dennis Ritchie presented the first Unix paper at the Symposium on Operating Systems Principles at Purdue University in November 1973. Professor Bob Fabry, of the University of California at Berkeley, was in attendance and immediately became interested in obtaining a copy of the system to experiment with at Berkeley. At the time, Berkeley had only large mainframe computer systems doing batch processing, so the first order of business was to get a PDP-11/45 suitable for running with the then-current Version 4 of Unix. The Computer Science Department at Berkeley, together with the Mathematics Department and the Statistics Department, were able to jointly purchase a PDP-11/45. In January 1974, a Version 4 tape was delivered and Unix was installed by graduate student Keith Standiford. Although Ken Thompson at Purdue was not involved in the installation at Berkeley as he had been for most systems up to that time, his expertise was soon needed to determine the cause of several strange system crashes. Because Berkeley had only a 300-baud acoustic-coupled modem without auto answer capability, Thompson would call Standiford in the machine room and have him insert the phone into the modem; in this way Thompson was able to remotely debug crash dumps from New Jersey. Many of the crashes were caused by the disk controller's inability to reliably do overlapped seeks, contrary to the documentation. Berkeley's 11/45 was among the first systems that Thompson had encountered that had two disks on the same controller! Thompson's remote debugging was the first example of the cooperation that sprang up between Berkeley and Bell Labs. -

OS 386 Multiuser/Multitasking Operating System
OS 386 Multiuser/Multitasking Operating System REFERENCE GUIDE [Q] DIGITAL RESEARCH@ os REFERENCE GUIDE [jill DIGITAL RESEARCH~ COPYRIGHT Copyright © 1987 Digital Research Inc. All rights reserved. No part of this publication may be reproduced, transcribed, stored in a retrieval system, or translated into any language or computer language, in any form or by any means, electronic, mechanical, magnetic, optical, chemical, manual or otherwise without the prior written permission of Digital Research Inc, 60 Garden Court, Box DRI, Monterey, California 93942 DISCLAIMER DIGITAL RESEARCH MAKES NO REPRESENTATIONS OR WARRANTIES WITH RESPECT TO THE CONTENTS HEREOF AND SPECIFICALLY DISCLAIMS ANY IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR ANY PARTICULAR PURPOSE. Further Digital Research Inc. reserves the right to revise this publication and to make changes from time to time in the content hereof without obligation of Digital Research Inc to notify any person of such revision or changes. NOTICE TO USER This manual should not be construed as any representation or warranty with respect to the software named herein. Occasionally changes or variations exist in the software that are not reflected in the manual. Generally, if such changes or variations are known to exist and to affect the product significantly, a release note or READ.ME file accompanies the manual and the distribution disks. In that event, be sure to read the release note or READ.ME file before using the product. ii TRADEMARKS Digital Research and its logo, CP/M, and CP/M-86 are registered trademarks of Digital Research Inc. Cardfile, Concurrent, Concurrent DOS 386, Concurrent DOS XM, DR EDIX, DOS Plus and MP/M-86 are trademarks of Digital Research Inc. -

United States Court of Appeals for the FOURTH CIRCUIT
Case: 10-1482 Document: 35 Date Filed: 09/17/2010 Page: 1 No. 10-1482 IN THE United States Court of Appeals FOR THE FOURTH CIRCUIT dNOVELL, INCORPORATED, Plaintiff-Appellant, —v.— MICROSOFT CORPORATION, Defendant-Appellee. ON APPEAL FROM THE UNITED STATES DISTRICT COURT FOR THE DISTRICT OF MARYLAND BRIEF OF APPELLEE MICROSOFT CORPORATION RICHARD J. WALLIS DAVID B.TULCHIN STEVEN J. AESCHBACHER Counsel of Record MICROSOFT CORPORATION STEVEN L. HOLLEY One Microsoft Way SULLIVAN & CROMWELL LLP Redmond, Washington 98052 125 Broad Street (425) 882-8080 New York, New York 10004 (212) 558-4000 G. S TEWART WEBB VENABLE LLP 750 East Pratt Street, Suite 900 Baltimore, Maryland 21202 (410) 244-7400 Attorneys for Microsoft Corporation September 17, 2010 Case: 10-1482 Document: 35 Date Filed: 09/17/2010 Page: 2 UNITED STATES COURT OF APPEALS FOR THE FOURTH CIRCUIT DISCLOSURE OF CORPORATE AFFILIATIONS AND OTHER INTERESTS Only one form needs to be completed for a party even if the party is represented by more than one attorney. Disclosures must be filed on behalf of all parties to a civil, agency, bankruptcy or mandamus case. Corporate defendants in a criminal or post-conviction case and corporate amici curiae are required to file disclosure statements. Counsel has a continuing duty to update this information. No. _______ Caption: __________________________________________________ Pursuant to FRAP 26.1 and Local Rule 26.1, ______________________ who is _______________________, makes the following disclosure: (name of party/amicus) (appellant/appellee/amicus) 1. Is party/amicus a publicly held corporation or other publicly held entity? YES NO 2. Does party/amicus have any parent corporations? YES NO If yes, identify all parent corporations, including grandparent and great-grandparent corporations: 3. -

Wikipedia: Design of the FAT File System
Design of the FAT file system A FAT file system is a specific type of computer file system architecture and FAT a family of industry-standard file systems utilizing it. Developer(s) Microsoft, SCP, IBM, [3] The FAT file system is a legacy file system which is simple and robust. It Compaq, Digital offers good performance even in very light-weight implementations, but Research, Novell, cannot deliver the same performance, reliability and scalability as some Caldera modern file systems. It is, however, supported for compatibility reasons by Full name File Allocation Table: nearly all currently developed operating systems for personal computers and FAT12 (12- many home computers, mobile devices and embedded systems, and thus is a bit version), well suited format for data exchange between computers and devices of almost FAT16 (16- any type and age from 1981 through the present. bit versions), Originally designed in 1977 for use on floppy disks, FAT was soon adapted and FAT32 (32-bit version used almost universally on hard disks throughout the DOS and Windows 9x with 28 bits used), eras for two decades. Today, FAT file systems are still commonly found on exFAT (64- floppy disks, USB sticks, flash and other solid-state memory cards and bit versions) modules, and many portable and embedded devices. DCF implements FAT as Introduced 1977 (Standalone the standard file system for digital cameras since 1998.[4] FAT is also utilized Disk BASIC-80) for the EFI system partition (partition type 0xEF) in the boot stage of EFI- FAT12: August 1980 compliant computers. (SCP QDOS) FAT16: August 1984 For floppy disks, FAT has been standardized as ECMA-107[5] and (IBM PC DOS 3.0) ISO/IEC 9293:1994[6] (superseding ISO 9293:1987[7]). -

DR DOS for the Zfx86
DR DOS for the ZFx86 Cost Effective, Reliable, Rapid Deployment of Embedded Systems w DR DOS on the ZFx86 gets products to market quickly at the lowest development and ownership cost. w Thousands of compatible applications, drivers and utilities available free or at minimal cost. w Full documentation available. DR DOS 7.03 Key Features of DR DOS Online Manual - DRDOS is supplied with a complete The ideal embedded DOS system, online manual that contains detailed information about all designed for out-of-the-box of the features of the operating system including the basic implementation into ROM or Flash commands, and the advanced utilities. It also has online ROM with tools and associated help available for all its commands. documents available in the DRDOS Memory Management - Memory management features OEM Documentation Kit. include a set of device drivers and commands that enable w 100% MS-DOS 6.22 compatible.. you to manage memory efficiently and make as much memory as possible available to your applications. w Comprehensive DOS utility set DOS Protected Mode Services - DOS Protected Mode w Multitasking, with API for developers Services (DPMS) interface allows specially-implemented w DPMS memory manager in addition to DPMI device drivers and TSRs to operate in extended memory. w Stacker disk compression This makes more memory within the first megabyte w NWCACHE - disk caching program available to applications and other conventionally-written drivers and TSRs. Both Stacker* (the disk compression w EMM386 memory manager program), and NWCACHE (the disk cache) use DPMS. w DOS Protected Mode Services (DPMS) Disk Compression - The disk compression component w Multitasking enables you to store more information by compressing the w DR-DOS provides a full multitasking environment data. -

Motivations of Participating in Open Source Projects
Proceedings of the 34th Hawaii International Conference on System Sciences - 2001 Working for Free? – Motivations of Participating in Open Source Projects Alexander Hars Shaosong Ou IOM Department IOM Department Marshall School of Business Marshall School of Business University of Southern California University of Southern California [email protected] [email protected] Abstract the public, including the right to use, to redistribute and to The success of the Linux operating system has modify the software free of charge. This is a direct demonstrated the viability of an alternative form of challenge to the established assumptions about software software development – open source software – that markets that threatens the position of commercial challenges traditional assumptions about software software vendors. markets. Understanding what drives open source The open source phenomenon raises many interesting developers to participate in open source projects is questions. Its proponents regard it as a paradigmatic crucial for assessing the impact of open source software. change where the economics of private goods built on the This article identifies two broad types of motivations that scarcity of resources are replaced by the economics of account for their participation in open source projects. public goods where scarcity is not an issue. Critics argue The first category includes internal factors such as that open source software will always be relegated to intrinsic motivation and altruism, and the second niche areas, that it cannot compete with their commercial category focuses on external rewards such as expected opponents in terms of product stability and reliability future returns and personal needs. This article also [15], and that open source projects lack the capability to reports the results of a survey administered to open innovate. -

DR-Webspyder R Graphicaldos Web Browser
DR-WebSpyder R GraphicalDOS Web Browser A fcully ustomizable, > Information Kiosks DRlsow ystem r equirement > Network Computers for > Internet-Set-top Boxes Internet Browser > Compact embedded devices with display everage the proven DR-WebSpyder equips Many OEMs base their power and reliability of embedded OEMs of compact, embedded solutions on LDR-DOSR with a new x86-based devices with a industry standard PC graphical interface and set graphical Web browser. hardware to reduce the risk of Web protocols. Bring Running on DR-DOS (or any and cost associated with Internet access to your other current version of development. This same devices quickly and easily DOS), this fully configurable, logic applies to the software with DR-WebSpyderR . Low HTML 3.2 browser aids that is used. Embedded risk and low system developers in customizing OEMs that choose requirements are the key the navigation bar, fonts, DR-WebSpyder as the benefits to OEMs and system setup pages, E-mail, system browser and DR-DOS as the integrators. defaults, and more. operating system expand their available resources with Caldera DR-WebSpyder is a DR-WebSpyder also allows an extremely large pool of customizable, high- developers to pre-configure experienced developers and performance Web browser the browser to connect with proven development tools for your interactive specific service providers, for DOS. information kiosk, network making it easy for the end computer, Internet set-top user to simply plug in and The combination of DR-DOS box, and hand-held device. browse. and DR-WebSpyder creates the thinnest graphical DR-WebSpyder with navigation bar and on-screen keyboard Internet access client available. -

John A. Weeks III [email protected]
John A. Weeks III [email protected] 1438 McAndrews Road East (612) 720-2854 Burnsville, MN 55337 John Weeks Skill Inventory: 1. Open Systems • HP9000, IBM RS/6000, Sun Enterprise Server • HP/UX, AIX, SunOS, Solaris, Linux, SCO UNIX, Xenix, 386/ix • Siemens SINIX, Sequent DYNIX, DEC OSF1, DG/UX, NCR, UNISYS • SVID, 4BSD, POSIX, XPG/4, i18n (Internationalization) • System Architecture, Capacity Planning, Disaster Recovery • System Administration, Performance Tuning, Back-up & Restore • UNIX Networking (DNS, NFS, NIS, R-commands, Internet) • Database Management (Sybase, Oracle, RDB, Informix) • Application Development, PERL, C, C++-Programming • Shell Programming (sh, csh, ksh, bash, AWK, sed, PERL, vi) • System Security, Security Audits, PAM, S2/S3 System Scanners • Best/1, BMC Patrol, Tivoli, NetView-6000, HP OPenview • Redundant & High Availability Systems • Veritas Volume Manager, File System, Cluster Manager, DMP • DASD, JBOD Disk Arrays, Raid Disk Arrays, Storage Area Networks 2. Networking • Most popular protocols (TCP/IP, IPX/SPX, NetBIOS, NetBEUI) • AppleTalk, AppleTalk Phase 2, LocalTalk, EtherTalk, TokenTalk • Exposure to SNA, DecNET, XNS, SCSI over Fiber Optic Cable • ODI, NDIS, Packet Driver, WinSock • CSU/DSU, TIU, NT1, Modem • Terminal Servers, Multiport Cards, Remote Access Servers • Hub, MAU, Repeater, Concentrator • Bridges, Smart Bridge, Learning Bridge, Network Switch • Router (Cisco, Wellfleet, Morningstar), BRouters • 56KB, Analog, DDS, Fractional T-1, T-1, T-3, DS-3 • ISDN, ATM, Frame Relay, DSL, Broadband • Category 3, Category 5, ThinNet, ThickNet, Fiber Optic, Coax • Ethernet, Fast Ethernet, Gigabit Ethernet, Token Ring, FDDI, ArcNet • RIP, OSPF, EGRP, Source Routing, NAT • SNMP, HP OpenView, SunNet Manager, MRTG • Pentascanner, Sniffer, Novell LANalyzer Skill Inventory: Weeks, Page 1 3.