Redmond Counterintelligence Chapter 2010
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

1 ISR Asset Visibility and Collection Management Optimization Through
ISR asset visibility and collection management optimization through knowledge models and automated reasoning Anne-Claire Boury-Brisset1, Michael A. Kolodny2, Tien Pham2 (1) Defence Research and Development (2) U.S. Army Research Laboratory Canada 2800 Powder Mill Road 2459 de la Bravoure Road Adelphi, MD 20783-1197 Quebec, QC, G3J 1X5, Canada [email protected] [email protected] [email protected] Abstract The increasing number and diversity of information sources makes ISR operations more and more challenging; this is especially true in a coalition environment. Optimizing the discovery and utility of coalition ISR assets when facing multiple requests for information, and enhancing the data to decisions process by gathering mission-relevant information to consumers will require automated tools in support of collection planning and assessment. Defence R&D Canada and the US Army Research Laboratory have related research activities in the area of ISR asset interoperability and information collection. In this paper, we present these projects and collaborative efforts to enhance ISR interoperability, through plug-and-play ISR interoperability and semantic knowledge representation of ISR concepts as well as approaches to maximize the utilization of available ISR collection assets. Keywords: Intelligence, Surveillance, Reconnaissance, information collection, sensors, UGS, standards, ontology. Published in the KSCO-2016 conference proceedings, ICCRTS-KSCO 2016 DRDC-RDDC-2016-P144 © Her Majesty the Queen in Right of Canada, as represented by the Minister of National Defence, 2016 © Sa Majesté la Reine (en droit du Canada), telle que représentée par le ministre de la Défense nationale, 2016 1 1. -

Secure Communications Over Open Networks (A Handbook for Paranoids)
Secure Communications over Open Networks (A Handbook for Paranoids) 1 Disclaimer • Security requires a paranoid mindset – If you’re going to play then you need to look at the big picture – This tutorial is intended to give a background on communications security – You could spend your life doing this stuff and still make mistakes • Nothing is secure 2 Just because you’re paranoid doesn’t mean “they” aren’t out to get you. THEM 3 The Elusive “They” • During this tutorial, I will refer to “them” a lot – You decide who “they” are -- every paranoid has different enemies • Hackers / Industrial Spies • Thought police • KGB / SMERSH / UN • CIA / IRS / ATF / NSA / NRA / U.N.C.L.E. • Orbital Mind Control Lasers / Illuminati / etc. 4 Before You Start • Risk Assessment: – What are you trying to hide? – How much will it hurt if “they” find it out? – How hard will “they” try? – How much are you willing to spend? “spend” means a combination of: •Time •Pain • Money 5 Why Secure Communications? • To carry out a business transaction – E-Commerce • To coordinate operations (Command and Control) – Remote management • To protect information – Privacy – Confidentiality 6 The Environment • Communications security is the land of cost/benefit analysis – Make getting your data too expensive for the attacker and they may not even try – Make protecting your data too expensive for yourself and you may be unable to operate 7 Target Analysis • Target analysis is the (hypothetical) art of analyzing a target’s communications security to identify the weakest link • You’d better do it, because “they” will do it, too 8 Target Analysis RF emissions (TEMPEST) Phone taps Laser bounce Radio audio bugs audio bugs 9 Target Analysis • Sweep your computer for bugs • Work only inside a metal cage w/no windows • Store the computer in a safe • Don’t use the local power grid to power your crypto systems …etc. -

What Is Counterintelligence? and How Lessons on Counterintelligence Might Enrich Their Courses
Association of Former Intelligence Officers From AFIO's The Intelligencer 7700 Leesburg Pike, Suite 324 Journal of U.S. Intelligence Studies Falls Church, Virginia 22043 Web: www.afio.com , E-mail: [email protected] Volume 20 • Number 2 • $15 single copy price Fall/Winter 2013 ©2013, AFIO measure what an adversary knows about us? How do we determine whether or not we are successful in keeping our secrets and projecting the image we wish Guide to the Study of Intelligence to project? How do we know what and whom to trust?3 This article is a short cut to some basic concepts about counterintelligence: what it is and is not. Educa- tors in history, government, political science, ethics, law and cognitive psychology should consider whether What is Counterintelligence? and how lessons on counterintelligence might enrich their courses. Recommended additional readings are suggested in the footnotes. A Guide to Thinking A general introductory course on U.S. counter- and Teaching about CI intelligence should have five key learning objectives: Understanding the meaning of counterintelli- gence, its place within intelligence studies, and by Michelle K. Van Cleave its role in international relations as an instrument of statecraft.4 Understanding the difference between tactical WHY STUDY COUNTERINTELLIGENCE? and strategic CI,5 the difference between CI and security,6 and the range of foreign intelligence he study of “counterintelligence” is rare in aca- 3. Consider for example the deception paradox: “Alertness to demia. While modern courses on international deception presumably prompts a more careful and systematic relations often include intelligence, they usually review of the evidence. -

Countering FIE Threats: Best Practices
i Countering FIE Threats: Best Practices Effective programs to counter foreign intelligence entity (FIE) threats are focused on three overarching outcomes: Promote CI and Identify and 1. Identification of foreign intelligence threats security training assess risks to and sharing of threat information and awareness sensitive assets 2. Safeguarding of sensitive information, assets, and activities Establish Share threat programs Develop and 3. Prevention and detection of insider threats information countering implement and warnings FIE threats mitigation internally and strategies The best practices detailed in this Guide, from identifying externally and assessing risks to promoting training and awareness, are complementary program components that, when employed together, can effectively shield your organization Integrate counter-FIE efforts across the from FIE threats. organization The National Counterintelligence and Security Center (NCSC) is charged with leading and supporting the counterintelligence (CI) and security activities of the U.S. government, the U.S. Intelligence Community, and U.S. private sector entities that are at risk of intelligence collection, penetration, or attack by foreign adversaries and malicious insiders. The capabilities and activities described in this Guide are exemplars of program components delineated as requirements in numerous strategies, policies, and guidelines. This Guide is a living document and will be updated to reflect improved and innovative ways to achieve the above outcomes. In addition, organization-specific capabilities and activities may be defined and implemented to ensure unique needs are met. Finally, nothing in this document shall be construed as authorization for any organization to conduct activities not otherwise authorized under statute, executive order, or other applicable law, policy, or regulation, nor does this document obviate an organization’s responsibility to conduct activities that are otherwise mandated, directed, or recommended for execution under the same. -

Cyber Counterintelligence - Deception, Distortion, Dishonesty
#RSAC SESSION ID: CYBER COUNTERINTELLIGENCE - DECEPTION, DISTORTION, DISHONESTY Jeff Bardin Dr. Khatuna Mshvidobadze Chief Intelligence Officer Principal Treadstone 71 Cyberlight Global Associates @Treadstone71LLC [email protected] 5 2 Agenda Taxonomy Types of Denial Deception Dimensions of D&D Tactics Deception Chain (see your handout) and Deception Planning D&D Russian Historical Information Criminals & Kids Notable Events Georgia US Election Background Warfare Dis-information / France – Information Complexity of Formation of cyber Troll Factories Major Players TV5Monde Warfare on Social Outsourcing troops Media Forming public Interagency Socio-Cultural Conclusions - opinion Rivalries Differences Recommendations 3 Denial and Deception - Lifecycle Types of Denial and Deception Resource Diversion Uncertainty Intelligence Proactivity Depletion • Direct an • Waste an • Cause the • Monitor and • Use adversary’s adversary’s adversary to analyze deception attention time and doubt the adversary techniques to from real energy on veracity of a behavior detect assets toward obtaining and discovered during previously bogus ones. analyzing vulnerability intrusion unknown false or stolen attempts to attacks that information. information. inform future other defense defensive efforts. tools may miss. 4 Deception Planning Consideration of all critical components of the operation. Deny, deceive, create propaganda RSA Conference - Bardin and Mshvidobadze Western Dogs Dogs Lie Like Dotards - We will hack their sites and bring them down 5 Dimensions -

Gianna to Accept L100 Award at Conference Fox Films President
O C V ΓΡΑΦΕΙ ΤΗΝ ΙΣΤΟΡΙΑ Bringing the news ΤΟΥ ΕΛΛΗΝΙΣΜΟΥ to generations of ΑΠΟ ΤΟ 1915 The National Herald Greek Americans A WEEKLY GREEK AMERICAN PUBLICATION c v www.thenationalherald.com VOL. 11, ISSUE 529 December 1, 2007 $1.00 GREECE: 1.75 EURO Gianna To Convicted Greek American Spy to Complete his Parole in Greece Accept L100 After 14 Years of Federal Prison and House Award At Arrest, Steven Lalas Reunites with his Family By Evan C. Lambrou telligence officers whenever he Special to The National Herald traveled to northern Greece to see Conference his family in Kavala. He continued NEW YORK – Steven J. Lalas, a for- to disseminate information after be- mer United States embassy employ- ing transferred to the U.S. Embassy Behrakis Invites Greek ee turned Greek spy, returned to in Athens in 1990. Greece last Sunday, November 25, Mr. Lalas, a native of New Schools To Apply For to serve the remainder of his parole Hampshire, came under suspicion after spending almost 12 years in following a conversation between Leadership 100 Grants federal prison, ending a spectacular someone from the Greek Embassy espionage affair between the two in Washington and a State Depart- By Theodore Kalmoukos countries. ment official in February 1993. Special to the National Herald The issue is now referred to High-ranking Greek diplomats ap- Greek judicial authorities, which parently boasted of being well in- BOSTON, Mass. – The Archbishop will determine the terms of the ad- formed of U.S. plans for the Balkans Iakovos Leadership 100 Endow- justment to Mr. -

Historical Dictionary of Russian and Soviet Intelligence
Russia • Military / Security Historical Dictionaries of Intelligence and Counterintelligence, No. 5 PRINGLE At its peak, the KGB (Komitet Gosudarstvennoy Bezopasnosti) was the largest HISTORICAL secret police and espionage organization in the world. It became so influential DICTIONARY OF in Soviet politics that several of its directors moved on to become premiers of the Soviet Union. In fact, Russian president Vladimir V. Putin is a former head of the KGB. The GRU (Glavnoe Razvedvitelnoe Upravleniye) is the principal intelligence unit of the Russian armed forces, having been established in 1920 by Leon Trotsky during the Russian civil war. It was the first subordinate to the KGB, and although the KGB broke up with the dissolution of the Soviet Union in 1991, the GRU remains intact, cohesive, highly efficient, and with far greater resources than its civilian counterparts. & The KGB and GRU are just two of the many Russian and Soviet intelli- gence agencies covered in Historical Dictionary of Russian and Soviet Intelligence. Through a list of acronyms and abbreviations, a chronology, an introductory HISTORICAL DICTIONARY OF essay, a bibliography, and hundreds of cross-referenced dictionary entries, a clear picture of this subject is presented. Entries also cover Russian and Soviet leaders, leading intelligence and security officers, the Lenin and Stalin purges, the gulag, and noted espionage cases. INTELLIGENCE Robert W. Pringle is a former foreign service officer and intelligence analyst RUSSIAN with a lifelong interest in Russian security. He has served as a diplomat and intelligence professional in Africa, the former Soviet Union, and Eastern Europe. For orders and information please contact the publisher && SOVIET Scarecrow Press, Inc. -
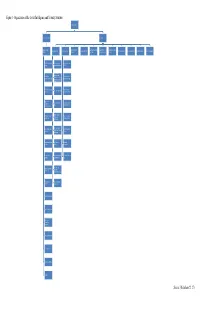
Organization of the Soviet Intelligence and Security Structure Source
Figure 1- Organization of the Soviet Intelligence and Security Structure General Chairman First Deputy Chairman Chief, GRU Deputy Chairman Space Intelligence Operational/ Technical Administrative/ Directorate for Foreign First Deputy Chief Chief of Information Personnel Directorate Political Department Financial Department Eighth Department Archives Department (KGB) Directorate Directorate Technical Directorate Relations First Chief Directorate First Directorate: Seventh Directorate: (Foreign) Europe and Morocco NATO Second Directorate: North and South Second Chief Eighth Directorate: America, Australia, Directorate (Internal) Individual Countries New Zealand, United Kingdom Fifth Chief Directorate Ninth Directorate: Third Directorate: Asia (Dissidents) Military Technology Eighth Chief Fourth Directorate: Tenth Directorate: Directorate Africa Military Economics (Communications) Fifth Directorate: Chief Border Troops Eleventh Directorate: Operational Directorates Doctrine, Weapons Intelligence Sixth Directorate: Third (Armed Forces) Twelfth Directorate: Radio, Radio-Technical Directorate Unknown Intelligence Seventh (Surveillance) First Direction: Institute of Directorate Moscow Information Ninth (Guards) Second Direction: East Information Command Directorate and West Berlin Post Third: National Technical Operations Liberation Directorate Movements, Terrorism Administration Fourth: Operations Directorate from Cuba Personnel Directorate Special Investigations Collation of Operational Experience State Communications Physical Security Registry and Archives Finance Source: (Richelson 22, 27) Figure 2- Organization of the United States Intelligence Community President National Security Advisor National Security DNI State DOD DOJ DHS DOE Treasury Commerce Council Nuclear CIO INR USDI FBI Intelligence Foreign $$ Flow Attachés Weapons Plans DIA NSA NGA NRO Military Services NSB Coast Guard Collection MSIC NGIC (Army) MRSIC (Air Analysis AFMic Force) NCTC J-2's ONI (Navy) CIA Main DIA INSCOM (Army) NCDC MIA (Marine) MIT Source: (Martin-McCormick) . -

Espionage Against the United States by American Citizens 1947-2001
Technical Report 02-5 July 2002 Espionage Against the United States by American Citizens 1947-2001 Katherine L. Herbig Martin F. Wiskoff TRW Systems Released by James A. Riedel Director Defense Personnel Security Research Center 99 Pacific Street, Building 455-E Monterey, CA 93940-2497 REPORT DOCUMENTATION PAGE Form Approved OMB No. 0704-0188 The public reporting burden for this collection of information is estimated to average 1 hour per response, including the time for reviewing instructions, searching existing data sources, gathering and maintaining the data needed, and completing and reviewing the collection of information. Send comments regarding this burden estimate or any other aspect of this collection of information, including suggestions for reducing the burden, to Department of Defense, Washington Headquarters Services, Directorate for Information Operations and Reports (0704- 0188), 1215 Jefferson Davis Highway, Suite 1204, Arlington, VA 22202-4302. Respondents should be aware that notwithstanding any other provision of law, no person shall be subject to any penalty for failing to comply with a collection of information if it does not display a currently valid OMB control number. PLEASE DO NOT RETURN YOUR FORM TO THE ABOVE ADDRESS. 1. REPORT DATE (DDMMYYYY) 2. REPORT TYPE 3. DATES COVERED (From – To) July 2002 Technical 1947 - 2001 4. TITLE AND SUBTITLE 5a. CONTRACT NUMBER 5b. GRANT NUMBER Espionage Against the United States by American Citizens 1947-2001 5c. PROGRAM ELEMENT NUMBER 6. AUTHOR(S) 5d. PROJECT NUMBER Katherine L. Herbig, Ph.D. Martin F. Wiskoff, Ph.D. 5e. TASK NUMBER 5f. WORK UNIT NUMBER 7. PERFORMING ORGANIZATION NAME(S) AND ADDRESS(ES) 8. -

Spy Culture and the Making of the Modern Intelligence Agency: from Richard Hannay to James Bond to Drone Warfare By
Spy Culture and the Making of the Modern Intelligence Agency: From Richard Hannay to James Bond to Drone Warfare by Matthew A. Bellamy A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy (English Language and Literature) in the University of Michigan 2018 Dissertation Committee: Associate Professor Susan Najita, Chair Professor Daniel Hack Professor Mika Lavaque-Manty Associate Professor Andrea Zemgulys Matthew A. Bellamy [email protected] ORCID iD: 0000-0001-6914-8116 © Matthew A. Bellamy 2018 DEDICATION This dissertation is dedicated to all my students, from those in Jacksonville, Florida to those in Port-au-Prince, Haiti and Ann Arbor, Michigan. It is also dedicated to the friends and mentors who have been with me over the seven years of my graduate career. Especially to Charity and Charisse. ii TABLE OF CONTENTS Dedication ii List of Figures v Abstract vi Chapter 1 Introduction: Espionage as the Loss of Agency 1 Methodology; or, Why Study Spy Fiction? 3 A Brief Overview of the Entwined Histories of Espionage as a Practice and Espionage as a Cultural Product 20 Chapter Outline: Chapters 2 and 3 31 Chapter Outline: Chapters 4, 5 and 6 40 Chapter 2 The Spy Agency as a Discursive Formation, Part 1: Conspiracy, Bureaucracy and the Espionage Mindset 52 The SPECTRE of the Many-Headed HYDRA: Conspiracy and the Public’s Experience of Spy Agencies 64 Writing in the Machine: Bureaucracy and Espionage 86 Chapter 3: The Spy Agency as a Discursive Formation, Part 2: Cruelty and Technophilia -

Hacks, Leaks and Disruptions | Russian Cyber Strategies
CHAILLOT PAPER Nº 148 — October 2018 Hacks, leaks and disruptions Russian cyber strategies EDITED BY Nicu Popescu and Stanislav Secrieru WITH CONTRIBUTIONS FROM Siim Alatalu, Irina Borogan, Elena Chernenko, Sven Herpig, Oscar Jonsson, Xymena Kurowska, Jarno Limnell, Patryk Pawlak, Piret Pernik, Thomas Reinhold, Anatoly Reshetnikov, Andrei Soldatov and Jean-Baptiste Jeangène Vilmer Chaillot Papers HACKS, LEAKS AND DISRUPTIONS RUSSIAN CYBER STRATEGIES Edited by Nicu Popescu and Stanislav Secrieru CHAILLOT PAPERS October 2018 148 Disclaimer The views expressed in this Chaillot Paper are solely those of the authors and do not necessarily reflect the views of the Institute or of the European Union. European Union Institute for Security Studies Paris Director: Gustav Lindstrom © EU Institute for Security Studies, 2018. Reproduction is authorised, provided prior permission is sought from the Institute and the source is acknowledged, save where otherwise stated. Contents Executive summary 5 Introduction: Russia’s cyber prowess – where, how and what for? 9 Nicu Popescu and Stanislav Secrieru Russia’s cyber posture Russia’s approach to cyber: the best defence is a good offence 15 1 Andrei Soldatov and Irina Borogan Russia’s trolling complex at home and abroad 25 2 Xymena Kurowska and Anatoly Reshetnikov Spotting the bear: credible attribution and Russian 3 operations in cyberspace 33 Sven Herpig and Thomas Reinhold Russia’s cyber diplomacy 43 4 Elena Chernenko Case studies of Russian cyberattacks The early days of cyberattacks: 5 the cases of Estonia, -

The European Union Approach to Disinformation and Misinformation the Case of the 2019 European Parliament Elections
University of Strasbourg European Master’s Degree in Human Rights and Democratisation A.Y. 2018/2019 The European Union approach to disinformation and misinformation The case of the 2019 European Parliament elections Author: Shari Hinds Supervisor: Dr Florence Benoit- Rohmer Abstract In the last years, the phenomenon of so called “fake news” on social media has become more and more discussed, in particular after the 2016 US elections. The thesis examines how the European Union is approaching “fake news” on social media, taking the 2019 European Parliament elections as a case study. This research favours the words “disinformation” and “misinformation”, over “fake news”. It, firstly, explores the different way of spreading disinformation and misinformation and how this can affect our human rights. This thesis will, secondly, focus on the different approaches, remedies and solutions to false information, outlining their limits, in order to recommend to the European Union, the best policies to tackle the phenomenon. The research will, thirdly, focuses on how the European Institutions are currently approaching this issue on social media and the steps that have been taken to protect European citizens from disinformation and misinformation; at this purpose the relevant European policy documents will be analysed. This analysis is necessary to understand the ground of the EU elections. The thesis will conclude with the case study of 2019 European Parliament elections. It will find if there have been cases of disinformation on social media and if the actions taken by the European Union have been enough to protect the second largest elections in the world. Key words: fake news, disinformation, misinformation, co-regulation, Russian disinformation campaigns, European Union, 2019 European Parliament elections.