The Foreign Office Cryptanalytic Section
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Paris Apartment Is a Work of Fiction
READI NG GROUP GU I DE PhotosOfYou_TPTextFP Epilogue 2019-11-26 15:34:54 335 AUTHOR’S NOTE The Paris Apartment is a work of fiction. While a product of my imagination, the premises and characters I’ve chosen to create are inspired by real people and real events. The characters of Sophie Seymour and Estelle Allard were shaped by the experiences and courage of Virginia Hall, Pearl Witherington Cornioley, Christine Granville, Josephine Baker, Nancy Wake, and Andrée de Jongh. Their memoirs, interviews, and stories only give us an idea of how truly extraordinary each of these women was. Sophie’s work at Bletchley Park was based on the real men and women who worked tirelessly against time and almost im- possible odds to decode Nazi encryption devices. Most of us have heard of the Enigma cipher and the remarkable work by Alan Turing and his team to break that cipher. Told less often seems to be the story of Tommy Flowers and Bill Tutte, who, together with their teams, developed Colossus—the machine that was able to break the Lorenz cipher, known as Tunny at Bletchley. The Lorenz cipher was favoured by Hitler and used by High Command—and for good reason. It was a far more powerful than the Enigma and capable of exceedingly complex en- cryptions. Additionally, unlike the Enigma, it did not depend ParisApartment_TPtext1P Author’s Note 2020-10-01 21:13:57 395 396 AUTHOR’S NOTE on Morse code. Attached to a teleprinter, it automatically encrypted outgoing messages and decrypted incoming mes- sages, allowing longer messages to be transmitted with greater ease. -

TICOM: the Last Great Secret of World War II Randy Rezabek Version of Record First Published: 27 Jul 2012
This article was downloaded by: [Randy Rezabek] On: 28 July 2012, At: 18:04 Publisher: Routledge Informa Ltd Registered in England and Wales Registered Number: 1072954 Registered office: Mortimer House, 37-41 Mortimer Street, London W1T 3JH, UK Intelligence and National Security Publication details, including instructions for authors and subscription information: http://www.tandfonline.com/loi/fint20 TICOM: The Last Great Secret of World War II Randy Rezabek Version of record first published: 27 Jul 2012 To cite this article: Randy Rezabek (2012): TICOM: The Last Great Secret of World War II, Intelligence and National Security, 27:4, 513-530 To link to this article: http://dx.doi.org/10.1080/02684527.2012.688305 PLEASE SCROLL DOWN FOR ARTICLE Full terms and conditions of use: http://www.tandfonline.com/page/terms-and- conditions This article may be used for research, teaching, and private study purposes. Any substantial or systematic reproduction, redistribution, reselling, loan, sub-licensing, systematic supply, or distribution in any form to anyone is expressly forbidden. The publisher does not give any warranty express or implied or make any representation that the contents will be complete or accurate or up to date. The accuracy of any instructions, formulae, and drug doses should be independently verified with primary sources. The publisher shall not be liable for any loss, actions, claims, proceedings, demand, or costs or damages whatsoever or howsoever caused arising directly or indirectly in connection with or arising out of the use of this material. Intelligence and National Security Vol. 27, No. 4, 513–530, August 2012 TICOM: The Last Great Secret of World War II RANDY REZABEK* ABSTRACT Recent releases from the National Security Agency reveal details of TICOM, the mysterious 1945 operation targeting Germany’s cryptologic secrets. -

Docid: 383869,.9
.. DOCID: 383869,.9 / ,1/111 [ Der Fall WICHER:GermanKnowledge of i Polish Success on ENIGMA BY JOSEPH A. MEYER T'op Bed pi blat'" a In 19.39 the Germans found evidf'nce. including decrypts, that a Polish cryptanalytic organization, WICHER: had been readin!! the ENIGMA. Documents and interrogations did not reveal how the ma chine could have been read, and after some changes in the indicator system and plug/fings, the matter was dropped. In 1943, further evidence of prewar Polish success, and the Mrong appearance that Navy ENIGMA was being read by the British and US., caused a crypto security crisis. A spy in the U.S. NavyDepartment reported the reading of V-boat keys. ENIGMA security was studied. and many changes in the machine and its uWf.:e were undertaken. By 1944 the Germans acted and spoke as if they knew ENIGMA traffic was being read by the Allies, but they suspected betrayal or compromise of keys. Medium grade ciphers were also improved, and radiQ security was much im proVf'd. Users were forbidden to send secret or top .~ecrf!t information or operational orders over ENIGMA. Through all of this. German con /idence in the TUNNY cipher teleprinter (which wa.~ al.~o being read) neller wavered. The key to German suspicions of ENIGMA appears to have been the knowledge of Polish prewar successes; after which the wartime ENIGMA exploitation hunk by a thread for five and one-half ~~. I I. DER FALL WICHER' 1n late 19:39. after their rapid conquest of Poland. the German OKH (Oberkommando des Heeres, Army High Command) and OKW (Oherkommando der Wehrmacht, Armed Forces High Command) cryptanalysts obtained definite proof, incllldin~ decrypts of German messag-cs. -
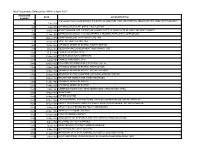
NSA Documents Released to NARA in April 2011
NSA Documents Released to NARA in April 2011 ACCESSION DATE ACCESSION TITLE NUMBER RECOLLECTIONS CONCERNING THE BIRTH OF ONE-TIME TAPE AND PRINTING-TELEGRAPH MACHINE CRYPTOGRAPHY 23 1-Jul-1956 268 1-Jul-1944 JAPANESE MERCHANT SHIPS, FIRST EDITION 593 9-May-1946 QUESTIONNAIRE FOR INSPECTION LIAISON VISITS TO FIELD UNITS OF ARMY SECURITY AGENCY 793 11-Apr-1951 OPERATIONS (AFSAG 1228) MANUEVERS & TRAINING EXERCISES & OPERATIONS 807 12-Dec-1950 COMPROMISES OF CRYPTOSYSTEMS 1950 821 24-Apr-1952 JOINT AUTHENTICATION 1952 963 10-Oct-1944 JAPANESE ORDER OF BATTLE, FOURTH EDITION 978 4-Dec-1952 RESEARCH AND DEVELOPMENT (R&D) BOARD, 1952 1022 15-Jul-1946 CHINESE PERSONS, SP-W 1027 10-Jun-1948 RUSSIAN ELECTORAL DISTRICTS 1029 1-Aug-1946 CHINESE RAILROADS, SP-X 1086 12-Dec-1956 DISASTER AND EMERGENCY PLANNING 1952-56 1155 13-Apr-1944 JAPANESE ORDER OF BATTLE, FIRST EDITION 1156 15-May-1944 JAPANESE ORDER OF BATTLE, SECOND EDITION 1158 11-Aug-1945 ORDER OF BATTLE BULLETINS, JAPANESE GROUND FORCES 1215 30-Nov-1945 MACARTHUR SEARCH FOR WINDS MESSAGES 1250 31-Mar-1945 JAPANESE ORDER OF BATTLE 1250 31-Mar-1945 JAPANESE ORDER OF BATTLE 1530 2-Mar-1949 COMBINED COMMUNICATIONS BOARD COUNTERMEASURES PANEL 1607 17-May-1948 SLIDE TUBE 1608 25-May-1954 CIPHER MACHINE 1617 31-Dec-1949 CRYPTOGRAPHIC SYSTEMS SUBMITTED FOR CONSIDERATION FOR MILITARY USE 1632 17-Jun-1946 AMBER-19 CATEGORY AND 3 CATEGORY WEIGHTING SCHEMES FOR TEST PROBLEM 1807 4-May-1953 AFSA CIVILIAN PERSONNEL POLICY MEMORANDA 1811 21-Dec-1951 AFSA-03 TELEPHONE LISTINGS 1812 14-Feb-1949 AFSA PERSONNEL -

The British "Inner Sanctum" of Modern Weaponized Intelligence Discovered
7/12/2019 Americans for Innovation: THE BRITISH "INNER SANCTUM" OF MODERN WEAPONIZED INTELLIGENCE DISCOVERED More Create Blog Sign In To ensure you are reading the latest post, click the logo above. SEARCH by topic, keyword or phrase. Type in Custom Search box e.g. "IBM Eclipse Foundation" or "racketeering" Custom Search Tuesday, June 25, 2019 SENIOR EXECUTIVE SERVICE (SES) THE BRITISH "INNER SANCTUM" OF MODERN HIJACKED THE INTERNET WEAPONIZED INTELLIGENCE DISCOVERED Michael McKibben EXPOS… British & American spies weaponized modern intelligence to enrich themselves, their knights, bankers, lawyers, accountants, propagandists and war corporations thru continuous fake enemies and contrived conflicts Click here to download a raw *.mp4 version of this video Their “Inner Sanctum” brotherhood took an “ULTRA oath” not to reveal even the existence of their Mar. 05, 1946 agreement and only DEEP STATE Member grudgingly allowed the FBI to join SHADOW GOVERNMENT U.S. Maj. Gen. James E. Freeze, ASA, NSA was groomed by the 1946 “Inner Sanctum,” created Echelon, then stole and weaponized Leader POSTER Harvard | Yale | Stanford | Oxbridge (Cambridge, Technologies’ social networking invention Oxford) | Sycophants The Senior Executive Service (SES) and IBM hired tens of thousands of LEGEND: Some corruptocrat photos German scientists from Operation TICOM (Target Intelligence in this blog contain a stylized Christian Committee linked to Bletchley Park that includes Operation Paperclip Celtic Wheel Cross in the background alongside the text as just one of its projects) to staff U.S. corporations using stolen IP "Corruption Central" meaning we have put the person's conduct under the microscope and CONTRIBUTING WRITERS | OPINION | AMERICANS FOR INNOVATION | JUN. -

NSA-FOIACASELOG-2016.Pdf
This document is made available through the declassification efforts and research of John Greenewald, Jr., creator of: The Black Vault The Black Vault is the largest online Freedom of Information Act (FOIA) document clearinghouse in the world. The research efforts here are responsible for the declassification of hundreds of thousands of pages released by the U.S. Government & Military. Discover the Truth at: http://www.theblackvault.com NATIONAL SECURITY AGENCY CENTRAL SECURITY SERVICE FORT GEORGE G. MEADE, MARYLAND 20755-6000 FOIA Case: 100503A 4 April 2017 JOHN GREENEWALD Dear Mr. Greenewald: This responds to your Freedom of Information Act (FOIA) request dated 1 January 2017 which was received by this office on 2 January 2017, for "a copy of the FOIA case log for calendar year 2016." For purposes of this request and based on the information you provided in your letter, you are considered an "all other" requester. As such, you are allowed 2 hours of search and the duplication of 100 pages at no cost. Since processing fees were minimal, no fees were assessed. Your request has been processed under the FOIA, and the logs for calendar year 2016 are enclosed, along with a FOIA Case Dispositions reference sheet that explains the final case dispositions. Please be advised that the logs do not contain the number of pages released. They contain a final disposition if the case was closed at the time the logs were created. If there is no final disposition, the case was still pending at the time the logs were created. Certain information has been deleted from the enclosures. -

BP's Sturgeon, the FISH That Laid No Eggs
BP’s Sturgeon, The FISH That Laid No Eggs Frode Weierud CERN, Div. SL, CH-1211 Geneva 23, Switzerland 1 Introduction The German armed forces employed three different types of teleprinter cipher machines during the Second World War, the Lorenz machines SZ40 and SZ42 also called Tunny by Bletchley Park (BP), the Siemens & Halske Schl¨ussel- fernschreibmaschine (SFM) T52, and the one-time-tape machine T43, also manufactured by Siemens. The Lorenz machines, which existed in three dif- ferent models, SZ40, SZ42a, and SZ42b, are well known as the machines that were broken at BP with the aid of Colossus. The Siemens T52 existed in four functionally distinct models, T52a/b, T52c and T52ca — which was a mod- ified version of the T52c machine, T52d, and T52e, all going under the BP code name of Sturgeon, while the Siemens T43 probably was the unbreakable machine that BP called Thrasher. The T43 machine came into use relatively late in the war and appears to have been used only on a few selected circuits. This paper will explain in detail the events that led to BP breaking the Sturgeon machines. In 1964, the Swedish Under-Secretary of State Erik Bo- heman first revealed that Sweden had broken the German Geheimschreiber (T52) during the Second World War. [7] In 1967, David Kahn gave fur- ther details about this achievement. [25] However, it was only in 1984, when Hinsley et al. published part one of the third volume of “British Intelligence in the Second World War,” that it was officially acknowledged that BP also had experienced some success against the Siemens T52. -

20151019-Website TICOM and the INTELLIGENCE CORPS CIGY
1 TICOM and the Intelligence Corps DRAMATIS PERSONAE TICOM TEAM 1 PERSONNEL *Oeser, O. Wing Commander RAFVR. (Chief TRO) A Cambridge psychologist and friend of Winterbotham, he had joined Hut 3 in the summer of 1940. In 1941 he was Hut 3 Dep. Air Advisor. By June 1942 was Head of Hut 3(Air) and by late 1942 he was head of the newly formed Hut 3(L) where he made Enigma and Fish priority decisions. He became professor of psychology at the University of Melbourne. By the age of 27 he had graduated from four universities in three countries and had gained doctorates in two disciplines. *Campaigne, H. Lieutenant Commander USNR (Deputy Chief) As a young man with a PhD in mathematics he had sent the navy a homemade design for an encryption device which was rejected. He gained his commission in December 1941. He was eventually to become NSA research chief as head of REMP (Research, Engineering, Math & Physics). Barringer, H. Capt AUS. (US Army). Carter, T. Captain IC (Intelligence Corps) A Lieutenant though there was a Captain TM Carter at the time in the Corps working in ‘Special employment’ which usually referred to serving in MI5, MI6, MI8; there is no record of his working at B.P.. Cockerell, H. Lieutenant RNVR He served in the Naval Section of B.P. where he was department head of N.S.111J Administration and Manning. After TICOM, he and Pickering stayed on in Germany in search of various wanted persons Coolidge, J. Lieutenant (J.G) USNR Crowe, R. Major AUS. -

The Foreign Office Cryptanalytic Section
3486663 , I ;ARMY SECURITY AGENCY Washington" D. C. _Ieclassifi ed and appw'.;ed for , elease by ~~SA, on 09- '17-2008 ~Iursuantt() E,O, '12958, as amended FC:II.A Case #52925 EUROPEAN l).XISSIGNAL I.NTELLIGENCF IN WORLD WAR AS REVEALED BY flTICOM '! INVESTIGATIONS AWD BY OTHER PRISONER OF 'WAR INTERROGATIONS AND CAPTURED MATERIAL, PRINCIPALLY GERMAN / VOLUME 6--THE' FOREIGN OFFICE CRYPTABALYTIC SEqTION Prepared lli"1.der CHIEF, ARlIlY SECURITY AGENCY ~ -11 ~:~ '1 May 1946 , )N" ~;~,J'V ~ WDGAS-14.~· '. '9fOIP §1EQ;~, CREAPf -J j ! DOClD: 3486663 , 'VOLWi~,6.' :,'TJ!E' FOREic,N' OR~~GE <CRYP~.I\NALYTIC 'S:EC'TI ON '." . «v."(" I 1. HlstoPy' ap.d Leading Pe~·fJo.i1~:L::i.tle~r 'chapter.... • ,I ,C:b.apt;~s)i'> II .1~' Inte~'cept; :Int~rcept Contiol a.nd~ Trart.io,.' Amily,'sis ,,' , C;ha:pt;~;,r III ~JC1~yp~ana,lysls dh.e:Pt~r IV Lis.1sonand Collabora.tion 'i'tlthOther :¢.~ypt~~Eilyt1c ~ . ".". '". 3-5 Agencieu' ;, u~ Sectiq~.qf,- th~ G.ert!!at.lFOI'~ign Chapter vi"' The Gr.yptograph1c . " " Otflce (Pers Z' Cht),--;" ' ,., "',, '.'" DOCID: 3486663 VOLUME 6 THE FOREIGN OFFIC£ CRYPTANALYTIC SECTION (PER Z S) Chapter I ~ Histo~"y and Le~g Personalities I Paragraph .:. '. ( '.' . .." ,.... " . ~ ~.() ~ Introductiorl I) C 0 0 .0 0- I) 0 Q 0 Co t'f c:l 0'" (l tl e .·0 c • 0 0> 0 0 0 a 00 C • 0 t,}. '00 0.. 1 ,..... ,German For'sign Office Organization :etir Cl"yptanalysls,?, ~ CODlInun.:tcatlons,ll and Security. 0.0 ••••••• ••• '••• 0 •• 00 •• " 2 History, 8,nd Strength. 0.0' ~,' 0 ••••••••• 0 ••••••• ~ ••• ".," .'. -

TICOM Archive
PUBLIC RECORD OFFICE Group/Class Piece (date) (Signed) IE C ( 20 Grosvenor Square AS/mdj 17 September 1947 L.S.I. : Director, f /i+.*.»nt.ion; TICOM). of Selchow. Subject: Interrogation report is t ransmitted herewith The attached TICGM v JJ interrogation of you consider further for your information. If SELCHOW. I will WILLIAM G . BARTLETT, Lt. Col., GSC, U.S. Army, Senior U.S. Liaison Officer. i if I i JPO 757 Septeater 1>4fit ! 13/MCL/ab 3 of Selc;;ow - • - • 7: Interrogation TO: IDWD Detachment c/o ?,miuay Attacno Lon on, En. a; nn Raval Fleet po^t Office Ho (to be passeu to TICO*^) 1. Pursaant to request of Army Secur ty Agency, »,•-. ;:.i:.., Lon j or ir. orsu tion concerning Seichow of the German Ministry oi Foreign Affaire^ the inclosed report is forwarded as a pr<ai y inl-rro .r tioa report o Seichow coxiiucttu by a representative of Army Security Agency, Europe at Fraaki'art aa Main, 2 Septeaber 1947. 2, It ia re aesteu hat t tleaa uarters bo at vised whetner ur- ther interrogation of Seicnow is uesireu by TI>»OM, and if so, that specific i ueations be forwarded to this Headquarters lor nse in the in- terro^ation. 3. A copy of the incloeea report nas been forwarded to Aray Security A.r-ency, Wai:nin^ton ana that Agency has also be 3 re-, aestec to aavise hex---. • orther interrogt tion is desirable. Incl R0BE1.T T. WALKFR Report of In terror ail n Lt. Colonel, Si.nal Corps w sum TICOL/l-208 ,TION REPORT ON KURT SELCHOu, FU. -

Central Intelligence Agency FOIA Request Logs, 2000-2005
Central Intelligence Agency FOIA request logs, 2000-2005 Brought to you by AltGov2 www.altgov2.org/FOIALand ... , Calendar Year 2000 FOIA Case Log Creation Date Case Number Case Subject 03-Jan-00 F-2000-00001 IMPACT VISA CARD HOLDERS 03-Jan-0O F-2000-00003 WILLIAM CHARLE BUMM JSC RADEL, LTD; ELTEK COMPANY WIDEBAND SYSTEMS DIGITAL FREQUENCY DISCRIMINATOR; ED 03-Jan-00 F-2000-00004 BATKO OR BATKO INTERNATIONAL; COLONEL SERGEY SUKARAEV 03-Jan-0O F-2000-00005 INFO ON FATHER 04-Jan-00 F-2000-00006 JOHN CHRISLAW 04-Jan-00 F-2000-00007 1999 BOMBING OF CHINESE EMBASSY IN BELGRADE, YUGOSLAVIA. 04-Jan-00 F-2000-00008 COMMANDER IAN FLEMING 04-Jan-00 F-2000-00009 MALCOLM X AND ELIJAH MUHAMMAD AND HIS SON, AKBAR MUHAMMAD AND THE NATION OF ISLAM 04-Jan-00 F-2000-00010 WILLIAM STEPHENSON 04-Jan-00 F-2000-00011 SIX DECEASED INDIVIDUALS WITH CRIMINAL BACKGROUND 04-Jan-00 F-2000-00012 INFO ON ARGENTINA 04-Jan-00 F-2000-00013 ENRIQUE FUENTES LEON, MANUEL MUNOZ ROCHA, AND ERNESTO ANCIRA JR. 04-Jan-00 F-2000-00014 SOVIET ESPIONAGE IN AND AGAINST THE UNITED STATES 04-Jan-00 F-2000-00015 SOVIET ESPIONAGE IN AND AGAINST THE UNITED STATES SPECIFIC INFO ON CIA POSITIONS RELATING TO THE INFORMATION SYSTEMS CONTACTS AND 04-Jan-00 F-2000-00016 PURCHASING- OFFICERS 04-Jan-00 F-2000-00017 MKULTRA CDROMS 04-Jan-00 F-2000-00018 CIA PROJECTS ON OR AROUND 9 APRIL 1959 04-Jan-00 F-2000-00019 JERZY PAWLOWSKI 04-Jan-00 F-2000-00020 PERSONNEL FILES OF ALDRICH AMES 05-Jan-00 F-2000-00026 PERSONNEL FILES OF ALDRICH AMES 05-Jan-00 F-2000-00027 32 PAGE LETTER AND TWO TDK TAPES ON HER PROBLEMS 05-Jan-00 F-2000-00028 EMERSON T. -

From Axis Surprises to Allied Victories from AFIO's the INTELLIGENCER
Association of Former Intelligence Officers From AFIO's The Intelligencer 7700 Leesburg Pike, Suite 324 Journal of U.S. Intelligence Studies Falls Church, Virginia 22043 Web: www.afio.com, E-mail: [email protected] Volume 22 • Number 3 • $15 single copy price Winter 2016-17 ©2017, AFIO The Bleak Years: 1939 – Mid-1942 GUIDE TO THE STUDY OF INTELLIGENCE The Axis powers repeatedly surprised Poland, Britain, France, and others, who were often blinded by preconceptions and biases, in both a strategic and tactical sense. When war broke out on September 1, 1939, the Polish leadership, ignoring their own intelligence, lacked an appreciation of German mili- tary capabilities: their cavalry horses were no match From Axis Surprises to Allied for German Panzers. British Prime Minister Neville Chamberlain misread Hitler’s intentions, unwilling to Victories accept the evidence at hand. This was the consequence of the low priority given to British intelligence in the The Impact of Intelligence in World War II period between wars.3 Near the end of the “Phony War” (September 3, 1939 – May 10, 1940) in the West, the Germans engi- By Peter C. Oleson neered strategic, tactical, and technological surprises. The first came in Scandinavia in early April 1940. s governments declassify old files and schol- ars examine the details of World War II, it is Norway Aapparent that intelligence had an important The April 9 German invasion of Norway (and impact on many battles and the length and cost of this Denmark) was a strategic surprise for the Norwegians catastrophic conflict. As Nigel West noted, “[c]hanges and British.