Identity Management (IDM) User Guide Version 1.0 01/07/2021
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Secure Authentication Mechanisms for the Management Interface in Cloud Computing Environments
UNIVERSITY OF BEIRA INTERIOR Engineering Secure Authentication Mechanisms for the Management Interface in Cloud Computing Environments Liliana Filipa Baptista Soares Dissertation Submitted in Partial Fulfillment of the Requirement for the Degree of Master of Science in Computer Science and Engineering (2nd Cycle Studies) Supervised by Prof. Dr. Pedro Ricardo Morais Inácio Covilhã, October 2013 ii To my beloved family, especially to my grandparents. iv Acknowledgements The endurance to overcome obstacles or predisposed objectives in life depends on how each one envisages them. It is up to each one to extract the most valuable lessons from each journey and transform them into knowledge. Without the guidance and support of very particular persons, it would have not been possible to accomplish this dissertation and many lessons would have not been learned. I hereby thank my mother and father, to whom I am mostly grateful, for helping me to achieve my goals, particularly those of my academic quest. I would like to thank my sister, Cátia, for her immeasurable support, and my grandparents, for always demonstrating their love and will to live. I am also grateful to my supervisor, Prof. Dr. Pedro Ricardo Morais Inácio, not only for the help, charisma and readiness he demonstrated to complete this stage, but also for being resourceful in aiding throughout other steps of my professional life. I also acknowledge the Multimedia Signal Processing – Covilhã Group at the Instituto de Telecomunicações, which hosted this dis- sertation work and the final project of my first degree, and the research folk in it, particularly Miguel Neto for lending me a smartcard reader temporarily. -

Dod Enterpriseidentity, Credential, and Access Management (ICAM)
UNCLASSIFIED DoD Enterprise Identity, Credential, and Access Management (ICAM) Reference Design Version 1.0 June 2020 Prepared by Department of Defense, Office of the Chief Information Officer (DoD CIO) DISTRIBUTION STATEMENT C. Distribution authorized to U.S. Government agencies and their contractors (Administrative or Operational Use). Other requests for this document shall be referred to the DCIO-CS. UNCLASSIFIED UNCLASSIFIED Document Approvals Prepared By: N. Thomas Lam IE/Architecture and Engineering Department of Defense, Office of the Chief Information Officer (DoD CIO) Thomas J Clancy, COL US Army CS/Architecture and Capability Oversight, DoD ICAM Lead Department of Defense, Office of the Chief Information Officer (DoD CIO) Approved By: Peter T. Ranks Deputy Chief Information Officer for Information Enterprise (DCIO IE) Department of Defense, Office of the Chief Information Officer (DoD CIO) John (Jack) W. Wilmer III Deputy Chief Information Officer for Cyber Security (DCIO CS) Department of Defense, Office of the Chief Information Officer (DoD CIO) ii UNCLASSIFIED UNCLASSIFIED Version History Version Date Approved By Summary of Changes 1.0 TBD TBD Renames and replaces the IdAM Portfolio Description dated August 2015 and the IdAM Reference Architecture dated April 2014. (Existing IdAM SDs and TADs will remain valid until updated versions are established.) Updates name from Identity and Access Management (IdAM) to Identity, Credential, and Access Management (ICAM) to align with Federal government terminology Removes and cancels -

Identity Management, Privacy, and Price Discrimination
Identity Management Identity Management, Privacy, and Price Discrimination In economics, privacy is usually discussed in the context of consumer preferences and price discrimination. But what forms of personal data privacy are compatible with merchants’ interests in knowing more about their consumers, and how can identity management systems protect information privacy while enabling personalization and price discrimination? ALESSANDRO n the economics literature, privacy is usually dis or her purchas ACQUISTI cussed in the context of consumer preferences ing history. Carnegie and reservation prices: merchants are interested Identity management systems can support such Mellon in finding out a consumer’s preferences because selective information revelation strategies by giving University Ifrom those they can infer the consumer’s maximum consumers greater control over which identities are willingness to pay for a good (his reservation price). established, which attributes are associated with them, The ability to identify consumers and track their pur and under what circumstances they’re revealed to oth chase histories, therefore, lets merchants charge prices ers. Therefore, such systems allow for transactions in that extract as much surplus as possible from the sale, which some level of information sharing is accompa which is what economists call price discrimination.1–3 nied by some level of information hiding. At the same In this context, consumer privacy concerns reduce to time, economic views of privacy that are more granu individuals’ -

Mastering Identity and Access Management
Whitepaper Mastering Identity and Access Management Contents Introduction ........................................................................................................................................................................ 1 Types of users ............................................................................................................................................................................ 2 Types of identities ..................................................................................................................................................................... 2 Local identities .................................................................................................................................................................... 2 Network identities .............................................................................................................................................................. 2 Cloud identities ................................................................................................................................................................... 2 IAM concepts ............................................................................................................................................................................. 3 IAM system overview ................................................................................................................................................................ 3 IAM system options -

Technical Design of Open Social Web for Crowdsourced Democracy
Project no. 610349 D-CENT Decentralised Citizens ENgagement Technologies Specific Targeted Research Project Collective Awareness Platforms D4.3 Technical Design of Open Social Web for Crowdsourced Democracy Version Number: 1 Lead beneficiary: OKF Due Date: 31 October 2014 Author(s): Pablo Aragón, Francesca Bria, Primavera de Filippi, Harry Halpin, Jaakko Korhonen, David Laniado, Smári McCarthy, Javier Toret Medina, Sander van der Waal Editors and reviewers: Robert Bjarnason, Joonas Pekkanen, Denis Roio, Guido Vilariño Dissemination level: PU Public X PP Restricted to other programme participants (including the Commission Services) RE Restricted to a group specified by the consortium (including the Commission Services) CO Confidential, only for members of the consortium (including the Commission Services) Approved by: Francesca Bria Date: 31 October 2014 This report is currently awaiting approval from the EC and cannot be not considered to be a final version. FP7 – CAPS - 2013 D-CENT D4.3 Technical Design of Open Social Web for Crowdsourced Democracy Contents 1 Executive Summary ........................................................................................................................................................ 6 Description of the D-CENT Open Democracy pilots ............................................................................................. 8 Description of the lean development process .......................................................................................................... 10 Hypotheses statements -

Identity Management
Identity Management A White Paper by: Skip Slone & The Open Group Identity Management Work Area A Joint Work Area of the Directory Interoperability Forum, Messaging Forum, Mobile Management Forum, and Security Forum March, 2004 Copyright © 2004 The Open Group All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior permission of the copyright owners. The materials contained in Appendix B of this document is: Copyright © 2003 Securities Industry Middleware Council, Inc. (SIMC). All rights reserved. The Open Group has been granted permission to reproduce the materials in accordance with the publishing guidelines set out by SIMC. The materials have previously been published on the SIMC web site (www.simc-inc.org). Boundaryless Information Flow is a trademark and UNIX and The Open Group are registered trademarks of The Open Group in the United States and other countries. All other trademarks are the property of their respective owners. Identity Management Document No.: W041 Published by The Open Group, March, 2004 Any comments relating to the material contained in this document may be submitted to: The Open Group 44 Montgomery St. #960 San Francisco, CA 94104 or by Electronic Mail to: [email protected] www.opengroup.org A White Paper Published by The Open Group 2 Contents Executive Summary 4 Introduction 5 Key Concepts 6 Business Value of Identity Management 17 Identity Management -

Ts 124 482 V14.0.0 (2017-04)
ETSI TS 124 482 V14.0.0 (2017-04) TECHNICAL SPECIFICATION LTE; Mission Critical Services (MCS) identity management; Protocol specification (3GPP TS 24.482 version 14.0.0 Release 14) 3GPP TS 24.482 version 14.0.0 Release 14 1 ETSI TS 124 482 V14.0.0 (2017-04) Reference RTS/TSGC-0124482ve00 Keywords LTE ETSI 650 Route des Lucioles F-06921 Sophia Antipolis Cedex - FRANCE Tel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16 Siret N° 348 623 562 00017 - NAF 742 C Association à but non lucratif enregistrée à la Sous-Préfecture de Grasse (06) N° 7803/88 Important notice The present document can be downloaded from: http://www.etsi.org/standards-search The present document may be made available in electronic versions and/or in print. The content of any electronic and/or print versions of the present document shall not be modified without the prior written authorization of ETSI. In case of any existing or perceived difference in contents between such versions and/or in print, the only prevailing document is the print of the Portable Document Format (PDF) version kept on a specific network drive within ETSI Secretariat. Users of the present document should be aware that the document may be subject to revision or change of status. Information on the current status of this and other ETSI documents is available at https://portal.etsi.org/TB/ETSIDeliverableStatus.aspx If you find errors in the present document, please send your comment to one of the following services: https://portal.etsi.org/People/CommiteeSupportStaff.aspx Copyright Notification No part may be reproduced or utilized in any form or by any means, electronic or mechanical, including photocopying and microfilm except as authorized by written permission of ETSI. -
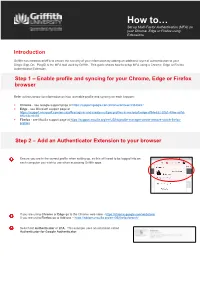
How to Install MFA Browser Authenicator Extension
How to… Set up Multi-Factor Authentication (MFA) on your Chrome, Edge or Firefox using Extensions Introduction Griffith has introduced MFA to ensure the security of your information by adding an additional layer of authentication to your Single Sign-On. PingID is the MFA tool used by Griffith. This guide shows how to setup MFA using a Chrome, Edge or Firefox Authenticator Extension. Step 1 – Enable profile and syncing for your Chrome, Edge or Firefox browser Refer to links below for information on how to enable profile and syncing for each browser: • Chrome - see Google support page at https://support.google.com/chrome/answer/2364824? • Edge - see Microsoft support page at https://support.microsoft.com/en-us/office/sign-in-and-create-multiple-profiles-in-microsoft-edge-df94e622-2061-49ae-ad1d- 6f0e43ce6435 • Firefox - see Mozilla support page at https://support.mozilla.org/en-US/kb/profile-manager-create-remove-switch-firefox- profiles Step 2 – Add an Authenticator Extension to your browser Ensure you are in the correct profile when setting up, as this will need to be logged into on each computer you wish to use when accessing Griffith apps. If you are using Chrome or Edge go to the Chrome web store - https://chrome.google.com/webstore/ If you are using Firefox go to Add-ons – https://addons.mozilla.org/en-GB/firefox/search/ Search for Authenticator or 2FA. This example uses an extension called Authenticator for Google Authenticator. Select Add Select Add Extension Your browser will confirm the extension has been added. Step 3 – Set up the Authenticator Extension as the primary authenticating method Once the Authenticator extension is added, click on the extension icon then click on the Pencil icon. -

Securing Digital Identities in the Cloud by Selecting an Apposite Federated Identity Management from SAML, Oauth and Openid Connect
Securing Digital Identities in the Cloud by Selecting an Apposite Federated Identity Management from SAML, OAuth and OpenID Connect Nitin Naik and Paul Jenkins Defence School of Communications and Information Systems Ministry of Defence, United Kingdom Email: [email protected] and [email protected] Abstract—Access to computer systems and the information this sensitive data over insecure channels poses a significant held on them, be it commercially or personally sensitive, is security and privacy risk. This risk can be mitigated by using naturally, strictly controlled by both legal and technical security the Federated Identity Management (FIdM) standard adopted measures. One such method is digital identity, which is used to authenticate and authorize users to provide access to IT in the cloud environment. Federated identity links and employs infrastructure to perform official, financial or sensitive operations users’ digital identities across several identity management within organisations. However, transmitting and sharing this systems [1], [2]. FIdM defines a unified set of policies and sensitive information with other organisations over insecure procedures allowing identity management information to be channels always poses a significant security and privacy risk. An transportable from one security domain to another [3], [4]. example of an effective solution to this problem is the Federated Identity Management (FIdM) standard adopted in the cloud Thus, a user accessing data/resources on one secure system environment. The FIdM standard is used to authenticate and could then access data/resources from another secure system authorize users across multiple organisations to obtain access without both systems needing individual identities for the to their networks and resources without transmitting sensitive single user. -

Integrator's Guide / Forgerock Identity Management 6.0
Integrator's Guide / ForgeRock Identity Management 6.0 Latest update: 6.0.0.6 Anders Askåsen Paul Bryan Mark Craig Andi Egloff Laszlo Hordos Matthias Tristl Lana Frost Mike Jang Daly Chikhaoui Nabil Maynard ForgeRock AS 201 Mission St., Suite 2900 San Francisco, CA 94105, USA +1 415-599-1100 (US) www.forgerock.com Copyright © 2011-2017 ForgeRock AS. Abstract Guide to configuring and integrating ForgeRock® Identity Management software into identity management solutions. This software offers flexible services for automating management of the identity life cycle. This work is licensed under the Creative Commons Attribution-NonCommercial-NoDerivs 3.0 Unported License. To view a copy of this license, visit https://creativecommons.org/licenses/by-nc-nd/3.0/ or send a letter to Creative Commons, 444 Castro Street, Suite 900, Mountain View, California, 94041, USA. ForgeRock® and ForgeRock Identity Platform™ are trademarks of ForgeRock Inc. or its subsidiaries in the U.S. and in other countries. Trademarks are the property of their respective owners. UNLESS OTHERWISE MUTUALLY AGREED BY THE PARTIES IN WRITING, LICENSOR OFFERS THE WORK AS-IS AND MAKES NO REPRESENTATIONS OR WARRANTIES OF ANY KIND CONCERNING THE WORK, EXPRESS, IMPLIED, STATUTORY OR OTHERWISE, INCLUDING, WITHOUT LIMITATION, WARRANTIES OF TITLE, MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, NONINFRINGEMENT, OR THE ABSENCE OF LATENT OR OTHER DEFECTS, ACCURACY, OR THE PRESENCE OF ABSENCE OF ERRORS, WHETHER OR NOT DISCOVERABLE. SOME JURISDICTIONS DO NOT ALLOW THE EXCLUSION OF IMPLIED WARRANTIES, SO SUCH EXCLUSION MAY NOT APPLY TO YOU. EXCEPT TO THE EXTENT REQUIRED BY APPLICABLE LAW, IN NO EVENT WILL LICENSOR BE LIABLE TO YOU ON ANY LEGAL THEORY FOR ANY SPECIAL, INCIDENTAL, CONSEQUENTIAL, PUNITIVE OR EXEMPLARY DAMAGES ARISING OUT OF THIS LICENSE OR THE USE OF THE WORK, EVEN IF LICENSOR HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

Oracle Data Sheet
ORACLE DATA SHEET ORACLE IDENTITY MANAGER 11g KEY FEATURES Oracle Identity Manager is a highly flexible and scalable • Self-service identity management enterprise identity administration system that provides operational drives user productivity, increases user and business efficiency by providing centralized administration & satisfaction and optimizes IT efficiency • Universal delegated administration complete automation of identity and user provisioning events enhances security and reduces costs across enterprise as well as extranet applications. It manages the • Requests with approval workflows and entire identity and role lifecycle to meet changing business and policy-driven provisioning improves IT efficiency, enhances security and regulatory requirements and provides essential reporting and enables compliance compliance functionalities. By applying the business rules, roles, • Password management reduces IT and audit policies, it ensures consistent enforcement of identity help desk costs, and improves service based controls and reduces ongoing operational and compliance levels • Integration solutions featuring Adapter costs. Factory and pre-configured connectors enables quick and low cost system integration Introduction Oracle Identity Manager is a highly flexible and scalable enterprise identity management KEY BENEFITS system that is designed to administer user access privileges across a company's resources • Increased security: Enforce internal throughout the entire identity management life cycle, from initial on-boarding to final -

SAP Identity Management Password Hook Configuration Guide Company
CONFIGURATION GUIDE | PUBLIC Document Version: 1.0 – 2019-11-25 SAP Identity Management Password Hook Configuration Guide company. All rights reserved. All rights company. affiliate THE BEST RUN 2019 SAP SE or an SAP SE or an SAP SAP 2019 © Content 1 SAP Identity Management Password Hook Configuration Guide.........................3 2 Overview.................................................................. 4 3 Security and Policy Issues.....................................................5 4 Files and File Locations .......................................................6 5 Installing and Upgrading Password Hook..........................................8 5.1 Installing Password Hook....................................................... 8 5.2 Upgrading Password Hook...................................................... 9 6 Configuring Password Hook....................................................11 7 Integrating with the Identity Center.............................................18 8 Implementation Considerations................................................21 9 Troubleshooting............................................................22 SAP Identity Management Password Hook Configuration Guide 2 PUBLIC Content 1 SAP Identity Management Password Hook Configuration Guide The purpose of the SAP Identity Management Password Hook is to synchronize passwords from a Microsoft domain to one or more applications. This is achieved by capturing password changes from the Microsoft domain and updating the password in the other applications