Communication Networks: Sharing and Switches
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
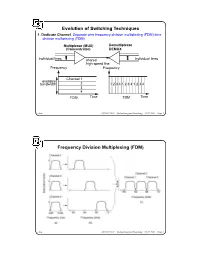
Evolution of Switching Techniques Frequency Division Multiplexing
Evolution of Switching Techniques 1. Dedicate Channel. Separate wire frequency division multiplexing (FDM) time division multiplexing (TDM) Multiplexor (MUX) Demultiplexor (Concentrator) DEMUX individual lines shared individual lines high speed line Frequency Frequency Channel 1 available bandwidth 2 1 2 3 4 1 2 3 4 1 2 3 4 3 4 FDM Time TDM Time chow CS522 F2001—Multiplexing and Switching—10/17/2001—Page 1 Frequency Division Multiplexing (FDM) chow CS522 F2001—Multiplexing and Switching—10/17/2001—Page 2 Wavelength Division Multiplexing chow CS522 F2001—Multiplexing and Switching—10/17/2001—Page 3 Impact of WDM z Many big organizations are starting projects to design WDM system or DWDN (Dense Wave Division Mutiplexing Network). We may see products appear in next three years.In Fujitsu and CCL/Taiwan, 128 different wavelengthes on the same strand of fiber was reported working in the lab. z We may have optical routers between end systems that can take one wavelenght signal, covert to different wavelenght, send it out on different links. Some are designing traditional routers that covert optical signal to electronical signal, and use time slot interchange based on high speed memory to do the switching, the convert the electronic signal back to optical signal. z With this type of optical networks, we will have a virtual circuit network, where each connection is assigned some wave length. Each connection can have 2.4 gbps tremedous bandwidth. z With inital 128 different wavelength, we can have about 10 end users. If each pair of end users needs to communicate simultaneously, it will use 10*10=100 different wavelength. -

~DRAFT~ CHAPTER 5: Link Layer
~DRAFT~ CHAPTER 5: Link layer Contents Network notes – Link layer ..................................................................................................................... 1 1 Context of Chapter .................................................................................................................. 2 2 Introduction ............................................................................................................................. 2 3 Objectives of Chapter/module ................................................................................................ 3 4 Services of the link layer ......................................................................................................... 4 5 Error detection ........................................................................................................................ 4 a. Parity check ............................................................................................................................. 4 b. Cyclic Redundancy Check ...................................................................................................... 5 6 Error Correction ...................................................................................................................... 5 7 MAC ....................................................................................................................................... 6 a. Fixed assigned MAC .............................................................................................................. -

Physical Layer Overview
ELEC3030 (EL336) Computer Networks S Chen Physical Layer Overview • Physical layer forms the basis of all networks, and we will first revisit some of fundamental limits imposed on communication media by nature Recall a medium or physical channel has finite Spectrum bandwidth and is noisy, and this imposes a limit Channel bandwidth: on information rate over the channel → This H Hz is a fundamental consideration when designing f network speed or data rate 0 H Type of medium determines network technology → compare wireless network with optic network • Transmission media can be guided or unguided, and we will have a brief review of a variety of transmission media • Communication networks can be classified as switched and broadcast networks, and we will discuss a few examples • The term “physical layer protocol” as such is not used, but we will attempt to draw some common design considerations and exams a few “physical layer standards” 13 ELEC3030 (EL336) Computer Networks S Chen Rate Limit • A medium or channel is defined by its bandwidth H (Hz) and noise level which is specified by the signal-to-noise ratio S/N (dB) • Capability of a medium is determined by a physical quantity called channel capacity, defined as C = H log2(1 + S/N) bps • Network speed is usually given as data or information rate in bps, and every one wants a higher speed network: for example, with a 10 Mbps network, you may ask yourself why not 10 Gbps? • Given data rate fd (bps), the actual transmission or baud rate fb (Hz) over the medium is often different to fd • This is for -

Lecture 8: Overview of Computer Networking Roadmap
Lecture 8: Overview of Computer Networking Slides adapted from those of Computer Networking: A Top Down Approach, 5th edition. Jim Kurose, Keith Ross, Addison-Wesley, April 2009. Roadmap ! what’s the Internet? ! network edge: hosts, access net ! network core: packet/circuit switching, Internet structure ! performance: loss, delay, throughput ! media distribution: UDP, TCP/IP 1 What’s the Internet: “nuts and bolts” view PC ! millions of connected Mobile network computing devices: server Global ISP hosts = end systems wireless laptop " running network apps cellular handheld Home network ! communication links Regional ISP " fiber, copper, radio, satellite access " points transmission rate = bandwidth Institutional network wired links ! routers: forward packets (chunks of router data) What’s the Internet: “nuts and bolts” view ! protocols control sending, receiving Mobile network of msgs Global ISP " e.g., TCP, IP, HTTP, Skype, Ethernet ! Internet: “network of networks” Home network " loosely hierarchical Regional ISP " public Internet versus private intranet Institutional network ! Internet standards " RFC: Request for comments " IETF: Internet Engineering Task Force 2 A closer look at network structure: ! network edge: applications and hosts ! access networks, physical media: wired, wireless communication links ! network core: " interconnected routers " network of networks The network edge: ! end systems (hosts): " run application programs " e.g. Web, email " at “edge of network” peer-peer ! client/server model " client host requests, receives -

Networking Packet Broadcast Storms
Lesson Learned Networking Packet Broadcast Storms Primary Interest Groups Balancing Authorities (BAs) Generator Operators (GOPs) Reliability Coordinators (RCs) Transmission Operators (TOPs) Transmission Owners (TOs) that own and operate an Energy Management System (EMS) Problem Statement When a second network cable was connected from a voice over internet protocol (VOIP) phone to a network switch lacking proper settings, a packet broadcast storm prevented network communications from functioning, and supervisory control and data acquisition (SCADA) was lost for several hours. Broadcast storm events have also arisen from substation local area network (LAN) issues. Details A conference room was set up for a training class that needed to accommodate multiple PCs. The bridge protocol data unit (BPDU) packet propagation prevention setting was disabled on a port in the conference room in order to place a network switch off of that port. Upon completion of the training, the network switch was removed; however, the BPDU packet propagation setting was inadvertently not restored. As part of a telephone upgrade project, the traditional phone in this conference room was recently replaced by a VOIP phone. Later, an additional network cable was connected to the output port of this VOIP phone into a secondary network jack within the conference room. When the second network cable was connected from a VOIP phone to a network switch lacking proper settings, a switching loop resulted. Spanning tree protocol is normally used to prevent switching loops from propagating broadcast packets continuously until the network capacity is overwhelmed. A broadcast packet storm from the switching loop prevented network communications from functioning and SCADA was lost for several hours. -

Guidelines on Mobile Device Forensics
NIST Special Publication 800-101 Revision 1 Guidelines on Mobile Device Forensics Rick Ayers Sam Brothers Wayne Jansen http://dx.doi.org/10.6028/NIST.SP.800-101r1 NIST Special Publication 800-101 Revision 1 Guidelines on Mobile Device Forensics Rick Ayers Software and Systems Division Information Technology Laboratory Sam Brothers U.S. Customs and Border Protection Department of Homeland Security Springfield, VA Wayne Jansen Booz-Allen-Hamilton McLean, VA http://dx.doi.org/10.6028/NIST.SP. 800-101r1 May 2014 U.S. Department of Commerce Penny Pritzker, Secretary National Institute of Standards and Technology Patrick D. Gallagher, Under Secretary of Commerce for Standards and Technology and Director Authority This publication has been developed by NIST in accordance with its statutory responsibilities under the Federal Information Security Management Act of 2002 (FISMA), 44 U.S.C. § 3541 et seq., Public Law (P.L.) 107-347. NIST is responsible for developing information security standards and guidelines, including minimum requirements for Federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate Federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130, Section 8b(3), Securing Agency Information Systems, as analyzed in Circular A- 130, Appendix IV: Analysis of Key Sections. Supplemental information is provided in Circular A- 130, Appendix III, Security of Federal Automated Information Resources. Nothing in this publication should be taken to contradict the standards and guidelines made mandatory and binding on Federal agencies by the Secretary of Commerce under statutory authority. -

Research on the System Structure of IPV9 Based on TCP/IP/M
International Journal of Advanced Network, Monitoring and Controls Volume 04, No.03, 2019 Research on the System Structure of IPV9 Based on TCP/IP/M Wang Jianguo Xie Jianping 1. State and Provincial Joint Engineering Lab. of 1. Chinese Decimal Network Working Group Advanced Network, Monitoring and Control Shanghai, China 2. Xi'an, China Shanghai Decimal System Network Information 2. School of Computer Science and Engineering Technology Ltd. Xi'an Technological University e-mail: [email protected] Xi'an, China e-mail: [email protected] Wang Zhongsheng Zhong Wei 1. School of Computer Science and Engineering 1. Chinese Decimal Network Working Group Xi'an Technological University Shanghai, China Xi'an, China 2. Shanghai Decimal System Network Information 2. State and Provincial Joint Engineering Lab. of Technology Ltd. Advanced Network, Monitoring and Control e-mail: [email protected] Xi'an, China e-mail: [email protected] Abstract—Network system structure is the basis of network theory, which requires the establishment of a link before data communication. The design of network model can change the transmission and the withdrawal of the link after the network structure from the root, solve the deficiency of the transmission is completed. It solves the problem of original network system, and meet the new demand of the high-quality real-time media communication caused by the future network. TCP/IP as the core network technology is integration of three networks (communication network, successful, it has shortcomings but is a reasonable existence, broadcasting network and Internet) from the underlying will continue to play a role. Considering the compatibility with structure of the network, realizes the long-distance and the original network, the new network model needs to be large-traffic data transmission of the future network, and lays compatible with the existing TCP/IP four-layer model, at the a solid foundation for the digital currency and virtual same time; it can provide a better technical system to currency of the Internet. -
Circuit-Switched Coherence
Circuit-Switched Coherence ‡Natalie Enright Jerger, ‡Mikko Lipasti, and ?Li-Shiuan Peh ‡Electrical and Computer Engineering Department, University of Wisconsin-Madison ?Department of Electrical Engineering, Princeton University Abstract—Circuit-switched networks can significantly lower contention, overall system performance can degrade by 20% the communication latency between processor cores, when or more. This latency sensitivity coupled with low link uti- compared to packet-switched networks, since once circuits are set up, communication latency approaches pure intercon- lization motivates our exploration of circuit-switched fabrics nect delay. However, if circuits are not frequently reused, the for CMPs. long set up time and poorer interconnect utilization can hurt Our investigations show that traditional circuit-switched overall performance. To combat this problem, we propose a hybrid router design which intermingles packet-switched networks do not perform well, as circuits are not reused suf- flits with circuit-switched flits. Additionally, we co-design a ficiently to amortize circuit setup delay. This observation prediction-based coherence protocol that leverages the exis- motivates a network with a hybrid router design that sup- tence of circuits to optimize pair-wise sharing between cores. The protocol allows pair-wise sharers to communicate di- ports both circuit and packet switching with very fast circuit rectly with each other via circuits and drives up circuit reuse. reconfiguration (setup/teardown). Our preliminary results Circuit-switched coherence provides overall system perfor- show this leading to up to 8% improvement in overall system mance improvements of up to 17% with an average improve- performance over a packet-switched fabric. ment of 10% and reduces network latency by up to 30%. -

Medium Access Control Layer
Telematics Chapter 5: Medium Access Control Sublayer User Server watching with video Beispielbildvideo clip clips Application Layer Application Layer Presentation Layer Presentation Layer Session Layer Session Layer Transport Layer Transport Layer Network Layer Network Layer Network Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller Data Link Layer Data Link Layer Data Link Layer Computer Systems and Telematics (CST) Physical Layer Physical Layer Physical Layer Institute of Computer Science Freie Universität Berlin http://cst.mi.fu-berlin.de Contents ● Design Issues ● Metropolitan Area Networks ● Network Topologies (MAN) ● The Channel Allocation Problem ● Wide Area Networks (WAN) ● Multiple Access Protocols ● Frame Relay (historical) ● Ethernet ● ATM ● IEEE 802.2 – Logical Link Control ● SDH ● Token Bus (historical) ● Network Infrastructure ● Token Ring (historical) ● Virtual LANs ● Fiber Distributed Data Interface ● Structured Cabling Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.2 Design Issues Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.3 Design Issues ● Two kinds of connections in networks ● Point-to-point connections OSI Reference Model ● Broadcast (Multi-access channel, Application Layer Random access channel) Presentation Layer ● In a network with broadcast Session Layer connections ● Who gets the channel? Transport Layer Network Layer ● Protocols used to determine who gets next access to the channel Data Link Layer ● Medium Access Control (MAC) sublayer Physical Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.4 Network Types for the Local Range ● LLC layer: uniform interface and same frame format to upper layers ● MAC layer: defines medium access .. -

F. Circuit Switching
CSE 3461: Introduction to Computer Networking and Internet Technologies Circuit Switching Presentation F Study: 10.1, 10.2, 8 .1, 8.2 (without SONET/SDH), 8.4 10-02-2012 A Closer Look At Network Structure: • network edge: applications and hosts • network core: —routers —network of networks • access networks, physical media: communication links d. xuan 2 1 The Network Core • mesh of interconnected routers • the fundamental question: how is data transferred through net? —circuit switching: dedicated circuit per call: telephone net —packet-switching: data sent thru net in discrete “chunks” d. xuan 3 Network Layer Functions • transport packet from sending to receiving hosts application transport • network layer protocols in network data link network physical every host, router network data link network data link physical data link three important functions: physical physical network data link • path determination: route physical network data link taken by packets from source physical to dest. Routing algorithms network network data link • switching: move packets from data link physical physical router’s input to appropriate network data link application router output physical transport network data link • call setup: some network physical architectures require router call setup along path before data flows d. xuan 4 2 Network Core: Circuit Switching End-end resources reserved for “call” • link bandwidth, switch capacity • dedicated resources: no sharing • circuit-like (guaranteed) performance • call setup required d. xuan 5 Circuit Switching • Dedicated communication path between two stations • Three phases — Establish (set up connection) — Data Transfer — Disconnect • Must have switching capacity and channel capacity to establish connection • Must have intelligence to work out routing • Inefficient — Channel capacity dedicated for duration of connection — If no data, capacity wasted • Set up (connection) takes time • Once connected, transfer is transparent • Developed for voice traffic (phone) g. -

Application Note: 2-Cell Test Environment
Application Note 2-cell Test Environment MD8475A Signalling Tester 1. Background to LTE Rollout Mobile phones appearing in the late 1980s soon experienced rapid evolution of functions from 1990 to 2000 and also spread worldwide as key communications infrastructure. The mobile phone is not limited to just two-way communications between two people but also supports sending and receiving of Short Message Services (SMS), web browsing using the Internet, application and video download, etc., and has become a popular and key cultural tool supporting a fuller lifestyle for many people. Figure 1. Evolution on UE According to one research company, total mobile phone (terminal) shipments at the end of 2010 were valued at $38 billion split between 45% for 2G phones and 49% for 3G. Table 1. Mobile Terminal Shipments Mobile Terminal Shipments ($38 billion total) LTE 1.3% WiMAX 4.0% W-CDMA 40.0% CDMA 9.3% GSM 45.4% 1 MD8475A-E-F-1 The purpose of the shift from 2G to 3G systems was to make more efficient use of frequency bandwidths and was closely related to the explosive growth of the Internet. While still maintaining the easy portability of a mobile phone, users were able to access the information they needed easily at any time and place using the Internet. Similarly to growth of 3G technology, the requirements of LTE systems, which is are positioned in the market as 3.9G to maintain competitiveness with coming 4G systems, are being examined. Connectivity with IP-based core networks must be maintained to support multimedia applications and ubiquitous networks using the packet domain. -

Application of Ethernet Networking Devices Used for Protection and Control Applications in Electric Power Substations
Application of Ethernet Networking Devices Used for Protection and Control Applications in Electric Power Substations Report of Working Group P6 of the Power System Communications and Cybersecurity Committee of the Power and Energy Society of IEEE September 12, 2017 1 IEEE PES Power System Communications and Cybersecurity Committee (PSCCC) Working Group P6, Configuring Ethernet Communications Equipment for Substation Protection and Control Applications, has existed during the course of report development as Working Group H12 of the IEEE PES Power System Relaying Committee (PSRC). The WG designation changed as a result of a recent IEEE PES Technical Committee reorganization. The membership of H12 and P6 at time of approval voting is as follows: Eric A. Udren, Chair Benton Vandiver, Vice Chair Jay Anderson Galina Antonova Alex Apostolov Philip Beaumont Robert Beresh Christoph Brunner Fernando Calero Christopher Chelmecki Thomas Dahlin Bill Dickerson Michael Dood Herbert Falk Didier Giarratano Roman Graf Christopher Huntley Anthony Johnson Marc LaCroix Deepak Maragal Aaron Martin Roger E. Ray Veselin Skendzic Charles Sufana John T. Tengdin 2 IEEE PES PSCCC P6 Report, September 2017 Application of Ethernet Networking Devices Used for Protection and Control Applications in Electric Power Substations Table of Contents 1. Introduction ...................................................................................... 10 2. Ethernet for protection and control .................................................. 10 3. Overview of Ethernet message