Ring Signatures for Anonymous Sourcing in Journalism ∗
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

1 Introduction
1 Introduction I. THE PROBLEM OF ANONYMITY NONYMOUS WRITING IS both an old and a new phenomenon. Before the Renaissance most writing was anonymous; many of the Aearly poems in anthologies are ascribed to ‘ Anon ’ . The medieval auctor (the term from which the word ‘ author ’ derives) was generally little more than a scribe, transcribing earlier texts. The name of the writer was irrelevant to the readers of a text, so it was immaterial that generally he was anonymous. 1 The identifi cation or naming of authors has been associated with the development of printing, and then subsequently with the role of copyright in ascribing property rights to them and the birth of the Romantic Author as a heroic fi gure at the end of the eighteenth century. 2 But even then a high proportion of novels were anonymous; between 1770 and 1800 over 70 per cent of novels were published without a named author, and during the 1820s the proportion rose to nearly 80 per cent. 3 There has certainly been a marked decline in anonymous writing in the late nineteenth and twentieth centuries, though some notable writers in this period have always, or sometimes, used pseudonyms (see section IV of this chapter and chapter 2 , section II), among them George Orwell (the pseudonym of Eric Blair), Sylvia Plath and Doris Lessing. The Internet is responsible for the revival of anonymous writing and indeed for many of the problems now associated with it. Many blogs are written under a pseudonym, though often the identity of the author is well known, as with Paul Staines, the author of the Guido Fawkes political blog. -

Domain-Specific Pseudonymous Signatures Revisited
Domain-Specific Pseudonymous Signatures Revisited Kamil Kluczniak Wroclaw University of Technology, Department of Computer Science [email protected] Abstract. Domain-Specific Pseudonymous Signature schemes were re- cently proposed for privacy preserving authentication of digital identity documents by the BSI, German Federal Office for Information Secu- rity. The crucial property of domain-specific pseudonymous signatures is that a signer may derive unique pseudonyms within a so called domain. Now, the signer's true identity is hidden behind his domain pseudonyms and these pseudonyms are unlinkable, i.e. it is infeasible to correlate two pseudonyms from distinct domains with the identity of a single signer. In this paper we take a critical look at the security definitions and construc- tions of domain-specific pseudonymous signatures proposed by far. We review two articles which propose \sound and clean" security definitions and point out some issues present in these models. Some of the issues we present may have a strong practical impact on constructions \provably secure" in this models. Additionally, we point out some worrisome facts about the proposed schemes and their security analysis. Key words: eID Documents, Privacy, Domain Signatures, Pseudonymity, Security Definition, Provable Security 1 Introduction Domain signature schemes are signature schemes where we have a set of users, an issuer and a set of domains. Each user obtains his secret keys in collaboration with the issuer and then may sign data with regards to his pseudonym. The crucial property of domain signatures is that each user may derive a pseudonym within a domain. Domain pseudonyms of a user are constant within a domain and a user should be unable to change his pseudonym within a domain, however, he may derive unique pseudonyms in each domain of the system. -

Lapp 1 the Victorian Pseudonym and Female Agency Research Thesis
Lapp 1 The Victorian Pseudonym and Female Agency Research Thesis Presented in partial fulfillment of the requirements for graduation with research distinction in English in the undergraduate colleges of The Ohio State University by Anna Lapp The Ohio State University April 2015 Project Advisor: Professor Robyn Warhol, Department of English Lapp 2 Chapter One: The History of the Pseudonym Anonymity disguises information. For authors, disguised or changed names shrouds their circumstance and background. Pseudonyms, or pen names, have been famously used to disguise one’s identity. The word’s origin—pseudṓnymon—means “false name”. The nom de plume allows authors to conduct themselves without judgment attached to their name. Due to an author’s sex, personal livelihood, privacy, or a combination of the three, the pen name achieves agency through its protection. To consider the overall protection of the pseudonym, I will break down the components of a novel’s voice. A text is written by a flesh-and-blood, or actual, author. Second, an implied author or omnipresent figure of agency is present throughout the text. Finally, the narrator relates the story to the readers. The pseudonym offers freedom for the actual author because the author becomes two-fold—the pseudonym and the real person, the implied author and the actual author. The pseudonym can take the place of the implied author by acting as the dominant force of the text without revealing the personal information of the flesh-and-blood author. Carmela Ciuraru, author of Nom de Plume: A (Secret) History of Pseudonyms, claims, “If the authorial persona is a construct, never wholly authentic (now matter how autobiographical the material), then the pseudonymous writer takes this notion to yet another level, inventing a construct of a construct” (xiii-xiv). -

Why Do People Seek Anonymity on the Internet?
Why Do People Seek Anonymity on the Internet? Informing Policy and Design Ruogu Kang1, Stephanie Brown2, Sara Kiesler1 Human Computer Interaction Institute1 Department of Psychology2 Carnegie Mellon University 5000 Forbes Ave., Pittsburgh, PA 15213 [email protected], [email protected], [email protected] ABSTRACT literature that exists mainly derives from studies of one or a In this research we set out to discover why and how people few online communities or activities (e.g., the study of seek anonymity in their online interactions. Our goal is to 4chan in [5]). We lack a full understanding of the real life inform policy and the design of future Internet architecture circumstances surrounding people’s experiences of seeking and applications. We interviewed 44 people from America, anonymity and their feelings about the tradeoffs between Asia, Europe, and Africa who had sought anonymity and anonymity and identifiability. A main purpose of the asked them about their experiences. A key finding of our research reported here was to learn more about how people research is the very large variation in interviewees’ past think about online anonymity and why they seek it. More experiences and life situations leading them to seek specifically, we wanted to capture a broad slice of user anonymity, and how they tried to achieve it. Our results activities and experiences from people who have actually suggest implications for the design of online communities, sought anonymity, to investigate their experiences, and to challenges for policy, and ways to improve anonymity tools understand their attitudes about anonymous and identified and educate users about the different routes and threats to communication. -

Freedom of Expression, Encryption, and Anonymity: Civil Society and Private Sector Perceptions
Freedom of Expression, Encryption, and Anonymity: Civil Society and Private Sector Perceptions Joint collaboration to inform the work of the UN Special Rapporteur on the promotion and protection of the right to freedom of opinion and expression Research Team World Wide Web Foundation Renata Avila Centre for Internet and Human Rights at European University Viadrina Ben Wagner Thomas Behrndt Oficina Antivigilância at the Institute for Technology and Society - ITS Rio Joana Varon Lucas Teixeira Derechos Digitales Paz Peña Juan Carlos Lara 2 About the Research In order to swiftly provide regional input for the consultation of the United Nations Special Rapporteur on the protection and promotion of the right to opinion and expression, the World Wide Web Foundation1, in partnership with the Centre for Internet and Human Rights at European University Viadrina, Oficina Antivigilância2 at the Institute for Technology and Society - ITS Rio3 in Brazil, and Derechos Digitales4 in Latin America, have conducted collaborative research on the use of encryption and anonymity in digital communications. The main goal of this initiative was to collect cases to highlight regional peculiarities from Latin America and a few other countries from the Global South, while debating the relationships within encryption, anonymity, and freedom of expression. This research was supported by Bertha Foundation.5 The core of the research was based on two different surveys focused on two target groups. The first was a series of interviews among digital and human rights organizations as well as potential users of the technologies to determine the level of awareness about both the anonymity and encryption technologies, to collect perceptions about the importance of these technologies to protect freedom of expression, and to have a brief overview of the legal framework and corporate practices in their respective jurisdictions. -

How to Leak a Secret: Theory and Applications of Ring Signatures
How to Leak a Secret: Theory and Applications of Ring Signatures Ronald L. Rivest1, Adi Shamir2, and Yael Tauman1 1 Laboratory for Computer Science, Massachusetts Institute of Technology, Cambridge, MA 02139, 2 Computer Science department, The Weizmann Institute, Rehovot 76100, Israel. Abstract. In this work we formalize the notion of a ring signature, which makes it possible to specify a set of possible signers without re- vealing which member actually produced the signature. Unlike group sig- natures, ring signatures have no group managers, no setup procedures, no revocation procedures, and no coordination: any user can choose any set of possible signers that includes himself, and sign any message by using his secret key and the others' public keys, without getting their approval or assistance. Ring signatures provide an elegant way to leak authoritative secrets in an anonymous way, to sign casual email in a way that can only be veri¯ed by its intended recipient, and to solve other problems in multiparty computations. Our main contribution lies in the presentation of e±cient constructions of ring signatures; the general concept itself (under di®erent terminology) was ¯rst introduced by Cramer et al. [CDS94]. Our constructions of such signatures are unconditionally signer-ambiguous, secure in the random oracle model, and exceptionally e±cient: adding each ring member in- creases the cost of signing or verifying by a single modular multiplication and a single symmetric encryption. We also describe a large number of extensions, modi¯cations and applications of ring signatures which were published after the original version of this work (in Asiacrypt 2001). -

Names in Toni Morrison's Novels: Connections
INFORMATION TO USERS This manuscript has been reproduced from the microfilm master. UMI films the text directly from the original or copy submitted. Thus, some thesis and dissertation copies are in typewriter face, while others may be from any type of computer printer. The quality or this reproduction is dependent upon the quaUty or the copy submitted. Broken or indistinct print, colored or poor quality illustrations and photographs, print bleedthrough, substandard margins, and improper alignment can adversely affect reproduction. In the unlikely. event that the author did not send UMI a complete manuscript and there are missing pages, these will be noted. Also, if unauthorized copyright material had to be removed, a note will indicate the deletion. Oversize materials (e.g., maps, drawings, charts) are reproduced by sectioning the original, beginning at the upper left-hand comer and continuing from left to right in equal sections with small overlaps. Each original is also photographed in one exposure and is included in reduced form at the back of the book. Photographs included in the original manuscript have been reproduced xerographically in this copy. Higher quality 6" x 9" black and white photographic prints are available for any photographs or illustrations appearing in this copy for an additional charge. Contact UMI directly to order. UMI A. Bell & Howell Information Company 300 North Zeeb Road. Ann Arbor. Ml48106·1346 USA 313!761·4700 8001521·0600 .. -------------------- ----- Order Number 9520522 Names in Toni Morrison's novels: Connections Clayton, Jane Burris, Ph.D. The University of North Carolina at Greensboro, 1994 Copyright @1994 by Clayton, Jane Burris. -

Electronic Signatures in German, French and Polish Law Perspective
Article Electronic signatures in German, French and Polish law perspective DR CHRISTIANE BIEREKOVEN, PHILIP BAZIN AND TOMASZ KOZLOWSKI This article presents some significant apply to the German legislation on electronic issues on the recognition of signatures. electronic signatures with regard to It may be stressed that Germany was the first foreign certificates from the country in the European Union that issued a law perspective of German, French and on electronic, respectively digital, signatures prior to the Electronic Signature Directive. The Act on Polish law. The European Union Digital Signatures came into force on 1 August legislation applies to Germany and 1997 and was restricted to the use of digital France, and has served as a guide signatures only. It had to be amended after the for Polish legislation in the course of Electronic Signature Directive was published, preparations of the accession of because the Directive provides for electronic Poland to the European Union. signatures in general and is not restricted to the There are therefore strong use of digital signatures only. similarities between the legislation I of these countries, but as the French The German legislation example shows, the results may also The Electronic Signature Directive was differ with regard to the material implemented into German law by the “Act on law applicable to a contract. The outlining Conditions for Electronic Signatures and difference between simple and for the Amendment of further Regulations” advanced electronic signature is (Gesetz über Rahmenbedingungen für discussed within the context of elektronische Signaturen und zur Änderung weiterer Vorschriften), hereinafter referred to as French law. “SigG” - of 21 May 2001. -

The Anonymity Heuristic: How Surnames Stop Identifying People When They Become Trademarks
Volume 124 Issue 2 Winter 2019 The Anonymity Heuristic: How Surnames Stop Identifying People When They Become Trademarks Russell W. Jacobs Follow this and additional works at: https://ideas.dickinsonlaw.psu.edu/dlr Part of the Behavioral Economics Commons, Civil Law Commons, Comparative and Foreign Law Commons, Economic Theory Commons, Intellectual Property Law Commons, Law and Economics Commons, Law and Psychology Commons, Legal Writing and Research Commons, Legislation Commons, Other Law Commons, Phonetics and Phonology Commons, Psychiatry and Psychology Commons, Psycholinguistics and Neurolinguistics Commons, and the Semantics and Pragmatics Commons Recommended Citation Russell W. Jacobs, The Anonymity Heuristic: How Surnames Stop Identifying People When They Become Trademarks, 124 DICK. L. REV. 319 (2020). Available at: https://ideas.dickinsonlaw.psu.edu/dlr/vol124/iss2/3 This Article is brought to you for free and open access by the Law Reviews at Dickinson Law IDEAS. It has been accepted for inclusion in Dickinson Law Review by an authorized editor of Dickinson Law IDEAS. For more information, please contact [email protected]. \\jciprod01\productn\D\DIK\124-2\DIK202.txt unknown Seq: 1 28-JAN-20 14:56 The Anonymity Heuristic: How Surnames Stop Identifying People When They Become Trademarks Russell Jacobs ABSTRACT This Article explores the following question central to trade- mark law: if a homograph has both a surname and a trademark interpretation will consumers consider those interpretations as intrinsically overlapping or the surname and trademark as com- pletely separate and unrelated words? While trademark jurispru- dence typically has approached this question from a legal perspective or with assumptions about consumer behavior, this Article builds on the Law and Behavioral Science approach to legal scholarship by drawing from the fields of psychology, lin- guistics, economics, anthropology, sociology, and marketing. -

Instructions for Filling up the Passport Application Form (Diplomatic/ Official)
INSTRUCTIONS FOR FILLING UP THE PASSPORT APPLICATION FORM (DIPLOMATIC/ OFFICIAL) A. GENERAL INSTRUCTIONS This Diplomatic/ Official Passport Application Form, issued by the Government of India, is machine-readable. It will be scanned by the Intelligent Character Recognition (ICR) enabled scanners. Incomplete or inappropriately-filled application form will not be accepted. Please follow the instructions given below while filling the form. Use CAPITAL LETTERS only, throughout the application form, as shown in the image below – Applicant's Given Name Applicant's Given Name s h a s h i S H A S H I Incorrect Correct Use standard fonts and avoid stylized writing. Use black or blue ball point pen only. Do NOT fill the application form with ink-pen or pencil. Write as clearly as possible. Use a pen with a thinnest possible tip. Put a cross ( ) in the boxes where you have to choose one or more options as your answer and leave the other option(s) blank. For example, if your gender is male, put a cross in the box against male as shown in the image below – Do NOT put dots ( ), tick marks ( ), etc, in the boxes, to choose the appropriate option as your answer. Write clearly within the boxes without touching the boundaries. Try and write in the centre of the box, as shown in the image below – Incorrect Correct Leave one box blank after each complete word, while filling up the boxes. Father's Given Name Father's Given Name D E V A N G J I G N E S H D E V A N G J I G N E S H Incorrect Correct Do NOT write anything outside the given boxes. -

Presenting Your Research: NLP Conference Submissions
Anonymity Overview Review forms Author responses Venues My assessment Titles Abstracts Style sheets Camera-ready Presenting your research: NLP conference submissions Christopher Potts Stanford Linguistics CS224u: Natural language understanding 1 / 11 Anonymity Overview Review forms Author responses Venues My assessment Titles Abstracts Style sheets Camera-ready The ACL anonymity period 1. The ACL conferences have adopted a uniform policy that submitted papers cannot be uploaded to repositories like arXiv (or made public in any way) starting one month from the submission deadline and extending through the time when decisions go out. 2. For specific conferences, check their sites for the precise date when this embargo goes into effect. 3. The policy is an attempt to balance the benefits of free and fast distribution of new ideas against the benefits of double-blind peer review. 4. For more on the policy and its rationale, see this ACL policy page. 2 / 11 Anonymity Overview Review forms Author responses Venues My assessment Titles Abstracts Style sheets Camera-ready Typical NLP conference set-up 1. You submit your paper, along with area keywords that help determine which committee gets your paper. 2. Reviewers scan a long list of titles and abstracts and then bid on which ones they want to do. The title is probably the primary factor in bidding decisions. 3. The program chairs assign reviewers their papers, presumably based in large part on their bids. 4. Reviewers read the papers, write comments, supply ratings. 5. Authors are allowed to respond briefly to the reviews. 6. The program/area chair might stimulate discussion among the reviewers about conflicts, the author response, etc. -
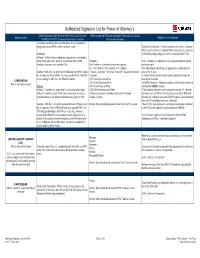
Authorized Signature List for Poas.Xlsx
Authorized Signature List for Power of Attorney’s List the following on the first line of the POA, as well as in the Who may sign the POA and Acceptable Titles to list on Capacity Business Entity Additional Forms Required WITNESS WHEREOF line near the bottom of the form line (last line on form) The legal corporation name and DBA name if the corporation is doing business as (DBA) another company name Corporate Certification – Should someone other than a Corporate Officer sign the POA, a Corporate Officer must sign the Corporate Subsidiary Certification giving said power to the person signing the POA Defined - A wholly owned subsidiary corporation is considered a stand-alone legal entity. As such, a corporate officer of the President 5106 - Additions or updates may be required and should not be subsidiary company must sign the POA. Vice President - authorized to bind the company performed until: I.E. - V.P. Finance, V.P. Customs, V.P. Logistics, • An initial importer bond query is generated to review importer Example - ABC Inc. is a wholly owned subsidiary of Whole Foods Treasurer, Secretary - Secretary Treasurer - Assistant Secretary data on file in ACE Inc. A corporate officer of ABC Inc. must sign the POA. The POA Treasurer • Letter of authorization from the client to update their importer is only binding for ABC Inc., not Whole Foods Inc. CEO Chief Executive Officer record with Customs CORPORATION COO Chief Operation Officer • EIN/IRS Numbers – Obtain acceptable proof from the importer to POA is valid until revoked Division CFO Chief Financial Officer validate their EIN/IRS number.