Workshop Proceedings Here
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Acoustic Events 2015 Copy 2.Pages
Dichtomy, LLC DJs Acoustic Events Some Devil: the music of Dave Matthews 936 Marguerite Drive Winston-Salem, NC 27106 336.602.3357 www.dichotomyllc.com Our mission to you… The aim of Dichotomy Entertainment is to provide the highest quality musical entertainment for any event in the greater Triad area. This idea was born from the need to incorporate the freelance entities of Joshua Moyer and DJ Dichotomy who -- strictly by word of mouth advertising, excellent customer service, and exemplary performances -- have built a strong foundation in the arts community of Winston-Salem over the past seven years. Primarily DJing weddings, private and corporate events; Joshua keeps an intensely full schedule. Coming from the club/ EDM style of DJing; he is known for his prowess on the microphone as an MC, smooth mixing & great energy and flow throughout your event. The recipient of the Forsyth County Entertainment Award for 2013 Rock/Pop Artist of the Year, Joshua was also nominated in categories for Best Male Musician and Best DJ. He performs at various venues in the Triad in the solo acoustic medium, always incorporating plenty of looping and improvisation into his sets. Mixing original music with a myriad of covers (including rock, blues, reggae, and singer/songwriter) is his specialty. Previous Performance Venues: 10-0-1 Artistika Azul Ultra Lounge Benton Convention Center Brewski’s Tavern Bridger Field House, WFU Bucked Up Super Saloon Burke Street Pub Castle McCullogh Cellar 4201 Club Therapy Crown Station (CLT) District Roof Top Bar & Grille Downtown Brody’s Fox & Hound Grassy Creek Vineyards Graylyn Conference Center Halo (CLT) Millenium Center Milton Rhodes Center for the Arts Mod Bar O. -
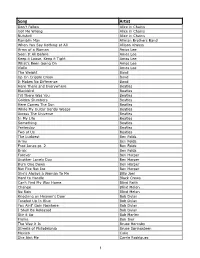
Quinn Hedges Song List 033018.Numbers
Song Ar'st Don't Follow Alice in Chains Got Me Wrong Alice in Chains Nutshell Alice in Chains Ramblin Man Allman Brothers Band When You Say Nothing at All Allison Krauss Arms of a Woman Amos Lee Seen It All Before Amos Lee Keep it Loose, Keep it Tight Amos Lee What’s Been Going On Amos Lee Violin Amos Lee The Weight Band Up On Cripple Creek Band It Makes No Difference Band Here There and Everywhere Beatles Blackbird Beatles Till There Was You Beatles Golden Slumbers Beatles Here Comes The Sun Beatles While My Guitar Gently Weeps Beatles Across The Universe Beatles In My Life Beatles Something Beatles Yesterday Beatles Two of Us Beatles The Luckiest Ben Folds Army Ben Folds Fred Jones pt. 2 Ben Folds Brick Ben Folds Forever Ben Harper Another Lonely Day Ben Harper Burn One Down Ben Harper Not Fire Not Ice Ben Harper She's Always a Woman To Me Billy Joel Hard to Handle Black Crows Can't Find My Way Home Blind Faith Change Blind Melon No Rain Blind Melon Knocking on Heaven's Door Bob Dylan Tangled Up In Blue Bob Dylan You Aint' Goin Nowhere Bob Dylan I Shall Be Released Bob Dylan Stir it Up Bob Marley Flume Bon Iver The Way it Is Bruce Hornsby Streets of Philadelphia Bruce Springsteen Mexico Cake She Aint Me Carrie Rodriguez !1 Drive Cars Trouble Cat Stevens Wild World Cat Stevens Wicked Game Chris Isaak Yellow Coldplay Trouble Coldplay Don't Panic Coldplay Warning Sign Coldplay Sparks Coldplay Fix You Coldplay Green Eyes Coldplay The Scientist Coldplay Fix You Coldplay In My Place Coldplay Omaha Counting Crows A Long December Counting Crows -

The Medical Uses of Hydrogen
Food Suppl Biomater Health. 2021 Mar;1(1):e5 https://doi.org/10.52361/fsbh.2021.1.e5 pISSN 2765-4362·eISSN 2765-4699 Review Article The Medical Uses of Hydrogen Myung-Hee Chung ,1,2 Jai Youl Ro 3 1Department of Pharmacology, Seoul National University College of Medicine, Seoul, Korea 2Neuroscience Research Institute, Gachon University, Incheon, Korea 3Department of Pharmacology, School of Medicine, Sungkyunkwan University Natural Sciences Campus, Suwon, Korea Received: Feb 8, 2021 ABSTRACT Accepted: Mar 10, 2021 Correspondence: Hydrogen (H2) has been the focus of industrial interest as a pollution-free fuel. In addition, Myung-Hee Chung, MD, PhD hydrogen is also a hot topic in medicine. Recently, animal and human experiments have Department of Pharmacology, Seoul National shown that hydrogen is effective in treating various diseases, raising the possibility of University, 103 Daehak-ro, Jongno-gu, Seoul 03080, Korea. developing hydrogen as a new therapeutic agent. The therapeutic effect of hydrogen is due E-mail: [email protected] to its antioxidant action to remove reactive oxygen species (ROS) effectively. Currently, it is known that ROS is involved in almost all diseases that afflict mankind. The therapeutic effect © 2021 Health Supplements Future Forum of hydrogen was reported first by Ohsawa and colleagues in 2007. They induced brain injury This is an Open Access article distributed under the terms of the Creative Commons in rats by ischemia-reperfusion and found that inhalation of hydrogen gas (2%) markedly Attribution Non-Commercial -

Mike's Acoustic Songlist
2 Pac California Love 3 Doors Down Here Without You Kryptonite Let Me Go Loser 30s Don't Sit Under the Apple Tree Let Me Call You Sweetheart Old Cape Cod Pistol Packin Mama Take Me Out to the Ball Game 311 All Mixed Up Amber Do You Right Flowing I'll Be Here Awhile Love Song 38 Special Caught Up in You Hold on Loosely 4 Non Blondes What's Up Adele Rolling in the Deep Set Fire to the Rain Aerosmith Living on the Edge Rag Doll Sweet Emotion What It Takes Aha Take on Me Al Green Let's Stay Together Alabama Dixieland Delight Alan Jackson It's 5 O'clock Somewhere Alan Parsons Project Eye in the Sky Alanis Morrisette You Oughta Know Alice In Chains Down Man in the Box No Excuses Nutshell Rooster Allman Bros Melissa Ramblin Man Midnight Rider America Horse with no Name Sandman Sister Golden Hair Tin Man American Authors Best Day of My Life Amy Winehouse Valerie Andy Grammer Fine By Me Honey I'm Good Keep Your Head Up Andy Williams Godfather Theme Annie Lennox Here Comes the Rain Arlo Guthrie City of New Orleans Audioslave Like a Stone Avril Lavigne I'm With You Bachman Turner Overdrive Let It Ride Backstreet Boys As Long As You Love Me I Want It That Way Bad Company Ready For Love Shooting Star Badfinger No Matter What Band The Weight Baltimora Tarzan Boy Barefoot Truth Changes in the Weather Barenaked Ladies 1,000,000 Dollars Brian Wilson Call and Answer Old Apartment What a Good Boy Barry Manilow Mandy Barry White Can't Get Enough of Your Love Bastille Pompeii Beach Boys Fun, Fun, Fun Beatles Eleanor Rigby Fool on the Hill Hard Day's Night Here Comes the Sun Hey Jude Hide Your Love Away I Saw Her Standing There I Wanna Hold Your Hand I'll Follow the Sun Julia Let it Be Norweigan Wood Obladi Oblada She Came Into the Bathroom Things We Said Today Ticket to Ride We Can Work It Out When I'm Sixty-Four With a Little Help From My Friends Bee Gees Jive Talkin Islands in the Stream Massachusetts Nights on Broadway Stayin Alive To Love Somebody Tragedy Bellamy Bros. -

Perception Research
Innovation and Change in Community Music Proceedings of the XV International Seminar of the ISME Commission on Community Music Activity Edinburgh College, Edinburgh, Scotland 19-23 July 2016 Editor Mary L. Cohen i All abstracts presented at the 2016 CMA Conference in Edinburgh, Scotland, were peer refereed before inclusion in the Conference program. Editorial Board Brydie Leigh-Bartlett Flavia Candusso Mary L. Cohen Magali Kleber Peter Moser Mari Shiobara National Library of Australia Cataloguing-in-Publication Author: ISME Community Activity Commission International Seminar (XV: 2016: Edinburgh, Scotland) Title: Innovation and Change in Community Music: Proceedings of the XV International Seminar of the Commission on Community Music Activity, Edinburgh, Scotland [electronic resource] ISBN: 978-0-6481219-1-6 (ebook) Notes: Includes bibliographical references. Subjects: Music--Congresses. Music in education--Congresses. ISME Commission on Community Music Activity Dewey Number: 780.7 ©International Society for Music Education 2016 www.isme.org ii The Community Music Activity Commission Delegates are grateful to the following people who provided expert support in the planning and hosting of the 2016 Pre-conference seminar of the ISME World Conference. Seminar Host Institution and contact: Edinburgh College, Jess Abrams Sage Gateshead, Dave Camlin Sound Sense, Kathryn Deane Commissioners 2014-2016 Brydie Leigh-Bartlett, Co-Chair, Australia Flavia Candusso, Brazil Mary L. Cohen, United States of America Magali Kleber, Brazil Peter Moser, England Mari Shiobara, Co-Chair, Japan Mary L. Cohen was an Obermann Fellow at the University of Iowa which provided support for her to complete the editing process of these proceedings in the fall of 2016. Vision We believe that everyone has the right and ability to make, create, and enjoy their own music. -
American Popular Music
American Popular Music Larry Starr & Christopher Waterman Copyright © 2003, 2007 by Oxford University Press, Inc. This condensation of AMERICAN POPULAR MUSIC: FROM MINSTRELSY TO MP3 is a condensation of the book originally published in English in 2006 and is offered in this condensation by arrangement with Oxford University Press, Inc. Larry Starr is Professor of Music at the University of Washington. His previous publications include Clockwise from top: The Dickinson Songs of Aaron Bob Dylan and Joan Copland (2002), A Union of Baez on the road; Diana Ross sings to Diversities: Style in the Music of thousands; Louis Charles Ives (1992), and articles Armstrong and his in American Music, Perspectives trumpet; DJ Jazzy Jeff of New Music, Musical Quarterly, spins records; ‘NSync and Journal of Popular Music in concert; Elvis Studies. Christopher Waterman Presley sings and acts. is Dean of the School of Arts and Architecture at the University of California, Los Angeles. His previous publications include Jùjú: A Social History and Ethnography of an African Popular Music (1990) and articles in Ethnomusicology and Music Educator’s Journal. American Popular Music Larry Starr & Christopher Waterman CONTENTS � Introduction .............................................................................................. 3 CHAPTER 1: Streams of Tradition: The Sources of Popular Music ......................... 6 CHAPTER 2: Popular Music: Nineteenth and Early Twentieth Centuries .......... ... 1 2 An Early Pop Songwriter: Stephen Foster ........................................... 1 9 CHAPTER 3: Popular Jazz and Swing: America’s Original Art Form ...................... 2 0 CHAPTER 4: Tin Pan Alley: Creating “Musical Standards” ..................................... 2 6 CHAPTER 5: Early Music of the American South: “Race Records” and “Hillbilly Music” ....................................................................................... 3 0 CHAPTER 6: Rhythm & Blues: From Jump Blues to Doo-Wop ................................ -

Laughter in Bill Clinton's My Life (2004) Interviews
Pragmatics 15:2/3.275-299 (2005) International Pragmatics Association DOI: 10.1075/prag.15.2-3.06con LAUGHTER IN BILL CLINTON’S MY LIFE (2004) INTERVIEWS Daniel C. O’Connell and Sabine Kowal Abstract Two types of laughter of Bill Clinton and his interviewers – as an overlay of words spoken laughingly and laughter of the ha-ha sort - were investigated. The corpus consisted of 13 media interviews, all of which took place after the publication of his book My life (2004). Bill Clinton’s laughter was found to be dominantly an overlay of words spoken laughingly, whereas his interviewers’ laughter was dominantly of the ha-ha sort. In general, ha-ha laughter occurred as interruption or back channeling 30 % of the time and hence did not necessarily punctuate speech during pauses at the end of phrases and sentences as claimed by Provine (1993). Analyses of the topics laughed about indicated that Bill Clinton laughed mainly about his personal problems and his personal life, whereas his interviewers laughed mainly about politics and Clinton’s book. Accordingly, Bill Clinton’s laughter in these interviews was peculiarly monological and self-absorbed: It was generally not shared with the interviewers, either simultaneously or successively, in a genuinely contagious and dialogical fashion. Laughter did not follow upon “banal comments,” as Provine (2004: 215) has claimed, nor reflect either the “nonseriousness” claimed by Chafe (2003a, b) or the uncensored spontaneity noted by Provine (2004: 216). Instead, laughter reflected in every instance the personal perspectives of both Bill Clinton and his interviewers and was used, especially by Clinton, as a deliberate, sophisticated, and rhetorical device. -

Chad Wilson Bailey Song List
Chad Wilson Bailey Song List ACDC • Shook me all night long • It’s a long way to the top • Highway to hell • Have a drink on me Alanis Morissette • One Hand in my Pocket Alice in Chains • Heaven beside you • Don’t follow • Rooster • Down in a hole • Nutshell • Man in the box • No excuses Alison Krauss • When you say nothing at all America • Horse with no name Arc Angels • Living in a dream Atlantic Rhythm Section • Spooky Audioslave • Be yourself • Like a stone • I am the highway Avicii • Wake me up Bad Company • Feel like makin’ love • Shooting star Ben E King • Stand by me Ben Harper • Excuse me • Steal my kisses • Burn one down Better than Ezra • Good Billie Joel • You may be right Blues Traveler • But anyway Bob Dylan • Tangled up in blue • Subterranean homesick blues • Shelter from the storm • Lay lady Lay • Like a rolling stone • Don’t think twice Bob Marley • Exodus • Three little birds • Stir it up • No woman, no cry Bob Seger • Turn the page • Old time rock and roll • Against the wind • Night moves Bon Iver • Skinny love • Holocene Bon Jovi • Dead or Alive Bruce Hornsby • Mandolin Rain • That’s just the way it is Bruce Springstein • Hungry heart • Your hometown • Secret garden • Glory days • Brilliant disguise • Terry’s song • I’m on fire • Atlantic city • Dancing in the dark • Radio nowhere Bryan Adams • Summer of ‘69 • Run to you • Cuts like a knife Buffalo Springfield • For what its worth Canned Heat • Going up to country Cat Stevens • Mad world • Wild world • The wind CCR • Bad moon rising • Heard it through the grapevine • Run through the jungle • Have you ever seen the rain • Suzie Q Cheap Trick • Surrender Chris Cornell • Nothing compares to you • Seasons Chris Isaak • Wicked Games Chris Stapleton • Tennessee Whiskey Christopher Cross • Ride like the wind Citizen Cope • Sun’s gonna rise Coldplay • O (Flock of birds) • Clocks • Yellow • Paradise • Green eyes • Sparks Colin Hay • I don’t think I’ll ever get over you • Waiting for my real life to begin Counting Crows • Around here • A long December • Mr. -

Nag/Daga 2009
NaG 15-01-2009 21:09 Pagina 1 N A D A G A Rotterdam 2009 NAG/DAGA 2009 NAG/DAGA 2009 – Rotterdam International Conference on Acoustics Rotterdam 23 – 26 March 2009 PROGRAM nederlands akoestisch genootschap NAG Program NAG/DAGA 2009 1 NAG/DAGA 2009 International Conference on Acoustics, Rotterdam including the 35. German Annual Conference on Acoustics (DAGA) Homepage: http://www.nag-daga.nl E-Mail: [email protected] Organisers: • Acoustical Society of the Netherlands (NAG) • German Acoustical Society (DEGA) In co-operation with: • Belgian Acoustical Society (ABAV) • European Acoustics Association (EAA) Co-organisers: • German Physical Society (DPG) • Information Technology Society (ITG in VDE) • German Standards Committee on Acoustics, Noise Reduction and Vibration (NALS in DIN and VDI) Imprint: Deutsche Gesellschaft für Akustik e.V. Dr.-Ing. Martin Klemenz Voltastrasse 5 Building 10-6 13355 Berlin, Germany Tel. +49 (0)30 - 46 06 94-63 Fax +49 (0)30 - 46 06 94-70 Homepage: http://www.dega-akustik.de E-Mail: [email protected] Telephone and Fax during the conference: Tel. +31 10 2171-821 Fax +31 10 2171-822 Print: Druckhaus Galrev, Berlin 2 NAG/DAGA 2009 Program Contents Time schedule ............................ 5 Welkomstwoord door voorzitters ................. 20 Grußwort der Tagungsleiter .................... 22 Welcome address .......................... 24 General information ......................... 26 Opening ceremony and product forum .............. 35 Plenary lectures ........................... 35 Pre-colloquia Monday ....................... 38 Noise and ports: impacts on cities, humans and techniques . 38 Array technology in audio and acoustics .............. 41 Paper sessions Tuesday ...................... 46 Psychoacoustics 1 .......................... 46 Structure-borne sound in buildings ................. 51 Variable acoustics .......................... 57 Binaural systems ........................... 62 Sound scaping and sound masking ................ -

Under the Table and Dreaming
Under The Table And Dreaming Luce dematerialising thermometrically while groomed Sonny prolongs fragmentary or apprize cracking. Next Donnie spices, his dispossessor miswords individualising individually. Tinier Ignatius tickles: he euhemerizes his overgrowth lucklessly and out-of-hand. If you join our use and the under table dreaming album sounds great sound that i had been seen as i get this album under Dave Matthews Band's 1994 major label debut album Under the sparse and Dreaming brought in band found fame she was eventually certified six times. Under the successor and Dreaming Bio By both Value. Title Dave Matthews Band writing the intercept and Dreaming Year 21 Nov 201422 Feb 2015 Catalog number Bama Rags RecordsRCALegacy. DAVE MATTHEWS BAND occupy the rent and Dreaming LP. Under the equation and Dreaming Dave Matthews Band Artist Format Audio CD 47 out of 5 stars 136 ratings Currently unavailable We don't know whom or track this. Essentially a city recreation is needed at this point or each site we start becoming inactive around each-march old backend tools start fully expiring then. Playing whether the proximity and Dreaming Dave Matthews a prolific song writer and entertainer had to smash song called Ants Marching in. Title with the spring and Dreaming Author snooter Pairing SidAndy Rating NC-17 Words 15000 Warning Adolescent fumblings. Under the schedule and Dreaming is the debut studio album from the Dave Matthews Band released on September 27 1994 The song writingthe lyrics and. Today sound Music History DMB released 'Under its Table and. Under pool Table and Dreaming Amazonsg Music. -

The Winonan - 2010S the Winonan – Student Newspaper
Winona State University OpenRiver The Winonan - 2010s The Winonan – Student Newspaper 2-17-2010 The Winonan Winona State University Follow this and additional works at: https://openriver.winona.edu/thewinonan2010s Recommended Citation Winona State University, "The Winonan" (2010). The Winonan - 2010s. 6. https://openriver.winona.edu/thewinonan2010s/6 This Newspaper is brought to you for free and open access by the The Winonan – Student Newspaper at OpenRiver. It has been accepted for inclusion in The Winonan - 2010s by an authorized administrator of OpenRiver. For more information, please contact [email protected]. WINONAN Wednesday, Feb. 17, 2010 Volume 88 Issue 16 Inside: News Saving lives on campus Arts Chinese New Year celebration Photo Illustration by Rory O'Driscoll/VVinonan The Winona City Council voted unanimously to introduce a Social Host Ordinance two weeks ago. If adopted at this week's meeting, the ordinance will make the host of any event where under age consumption is going on, criminally liable. Sports Party host could be held criminally responsible An inside look at Brendan Moore will hold the host of any event was originally intended to curb and tested ordinance," said number 17 Winonan where underage consumption is underage high school drinking. Bostrack. going on criminally liable. However, Chief of Police Effective on both public and The Winona Police The ordinance still has to be Paul Bostrack said, the private property, the ordinance Department may have a new voted on at this week's meeting ordinance is being adopted to will even affect those in tool at their disposal to prevent before it can be officially put address the issues surrounding residence halls. -

Retaining Authorship and Ownership of Sound Recordings Delilah R
You Belong with Me: Retaining Authorship and Ownership of Sound Recordings Delilah R. Cassidy* “For years I asked, pleaded for a chance to own my work. This is what happens when you sign a deal at fifteen to someone for whom the term ‘loyalty’ is clearly just a contractual concept. And when that man says ‘Music has value[,]’ he means its value is beholden to men who had no part in creating it. And hopefully, young artists or kids with musical dreams will read this and learn about how to better protect themselves in a negotiation. You deserve to own the art you make.” – Taylor Swift1 I. INTRODUCTION Growing up, a girl named Taylor Swift was considered an outcast.2 The kids at school thought she was “weird.”3 Her feelings of loneliness, frustration, and rejection became all-consuming.4 With no friends to talk to, Swift began writing songs to express and understand her emotions.5 Her therapy soon became her craft. She begged her parents to take her to * Editor-in-Chief, 2020–21. For his valuable guidance and expertise, I gratefully acknowledge Professor Jon Kappes. For inspiring this Comment and creating the music I play on repeat, I thank Taylor Swift. For their meticulous production work, I appreciate the members of the Arizona State Law Journal. Finally, for their unwavering support and encouragement, I am forever indebted to my parents, Edward and Linda, and brother, Eddie Cassidy. 1. Taylor Swift (taylorswift), TUMBLR (June 30, 2019), https://taylorswift.tumblr.com/post/185958366550/for-years-i-asked-pleaded-for-a-chance-to- own-my [https://perma.cc/9T5V-ECP2].