Mumbai, the Lessons Learned
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Project Division
MAGAL SECURITY SYSTEMS Focused Solutions for the World’s Security Needs Kobi Vinokur, CFO March 2020 1 / SAFE HARBOR/ Statements concerning Magal Security’s business outlook or future economic performance, product introductions and plans and objectives related thereto, and statements concerning assumptions made or expectations as to any future events, conditions, performance or other matters, are "forward-looking statements'' as that term is defined under U.S. federal securities laws. Forward-looking statements are subject to various risks, uncertainties and other factors that could cause actual results to differ materially from those stated in such statements. These risks, uncertainties and factors include, but are not limited to: the effect of global economic conditions in general and conditions affecting Magal Security’s industry and target markets in particular; shifts in supply and demand; market acceptance of new products and continuing products' demand; the impact of competitive products and pricing on Magal Security’s and its customers' products and markets; timely product and technology development/upgrades and the ability to manage changes in market conditions as needed; the integration of acquired companies, their products and operations into Magal Security’s business; and other factors detailed in Magal Security’s filings with the Securities and Exchange Commission. Magal Security assumes no obligation to update the information in this release. Estimated growth rates and other predictive statements represent Magal Security’s assumptions and expectations in light of currently available information. Estimated growth rates and other predictive statements, are based on industry trends, circumstances involving clients and other factors, and they involve risks, variables and uncertainties. -

Water Sector Cybersecurity Brief for States
WATER SECTOR CYBERSECURITY BRIEF FOR STATES Introduction Implementing cybersecurity best practices is critical for water and wastewater utilities. Cyber-attacks are a growing threat to critical infrastructure sectors, including water and wastewater systems. Many critical infrastructure facilities have experienced cybersecurity incidents that led to the disruption of a business process or critical operation. Cyber Threats to Water and Wastewater Systems Cyber-attacks on water or wastewater utility business enterprise or process control systems can cause significant harm, such as: • Upset treatment and conveyance processes by opening and closing valves, overriding alarms or disabling pumps or other equipment; • Deface the utility’s website or compromise the email system; • Steal customers’ personal data or credit card information from the utility’s billing system; and • Install malicious programs like ransomware, which can disable business enterprise or process control operations. These attacks can: compromise the ability of water and wastewater utilities to provide clean and safe water to customers, erode customer confidence, and result in financial and legal liabilities. Benefits of a Cybersecurity Program The good news is that cybersecurity best practices can be very effective in eliminating the vulnerabilities that cyber-attacks exploit. Implementing a basic cybersecurity program can: • Ensure the integrity of process control systems; • Protect sensitive utility and customer information; • Reduce legal liabilities if customer or employee personal information is stolen; and • Maintain customer confidence. Challenges for Utilities in Starting a Cybersecurity Program Many water and wastewater utilities, particularly small systems, lack the resources for information technology (IT) and security specialists to assist them with starting a cybersecurity program. Utility personnel may believe that cyber-attacks do not present a risk to their systems or feel that they lack the technical capability to improve their cybersecurity. -

Security Studies (SCST) 1
Security Studies (SCST) 1 SECURITY STUDIES (SCST) SCST 2363. Intro to Homeland Security. 3 Hours. This introductory course is designed to familiarize students with the field of security studies. Topics include Surveys, threats, and challenges from terrorist attacks, to pandemics to climate change. SCST 2364. Homeland Sec Research Methods. 3 Hours. Students gain knowledge about research design and methodology. Students develop the ability to analyze and critically evaluate data, ideas, arguments, and policy. Students also hone critical thinking skills and enhance their ability to be effective consumers of data. SCST 2365. Intro to Emergency Management. 3 Hours. Students study the evolution of emergency management in the United States from early community-based response practices to the current robust national system focused on risk analysis, communications, risk prevention and mitigation, and social and economic recovery. Students examine benchmark policies, regulations, and directives that form the basis of the emergency management field. Students engage in case study research and gain exposure to current and emerging trends in emergency management domestically and internationally. SCST 2366. Introduction to Cybersecurity. 3 Hours. Students examine the problem of cybersecurity from a homeland security perspective. Students explore the diversity of threats and security measures in cyberspace from a non-technical perspective and with a focus on laws, strategies, and policies. Security issues, from crime to espionage to cyberwar, will be considered on both the micro and macro-level. SCST 2368. Transportation Security. 3 Hours. Students examine a wide range of facets that comprise the field of transportation security. As part of this course students assess the capabilities and vulnerabilities of the transportation network as well as explore the agencies and governance issues impacting transportation security. -

Critical Infrastructure Protection: Concepts and Continuum
Critical Infrastructure Protection: Concepts and Continuum Contents Introduction........................................................................................................ 3 Terms and concepts..................................................................................................................4 Protecting critical infrastructure is a continuum............................................ 5 Trusted collaboration and information sharing ground the CIP continuum......6 Key CIP capabilities ...................................................................................................................6 Sharing threat information leads to improved CIP.......................................................7 Establishing trustworthy policies and plans.................................................... 9 Prepare...........................................................................................................................................9 Review policies and existing programs.........................................................................9 Identify operational responsibilities...............................................................................9 Partner.........................................................................................................................................10 Coordinate.................................................................................................................................10 Plan...............................................................................................................................................12 -

Critical Infrastructure: Security Preparedness and Maturity Sponsored by Unisys Independently Conducted by Ponemon Institute LLC Publication Date: July 2014
Critical Infrastructure: Security Preparedness and Maturity Sponsored by Unisys Independently conducted by Ponemon Institute LLC Publication Date: July 2014 31 Part 1. Introduction Ponemon Institute is pleased to present the results of the “Critical Infrastructure: Security Preparedness and Maturity” study, sponsored by Unisys. The purpose of this research is to learn how utility, oil and gas, alternate energy and manufacturing organizations are addressing cyber security threats. These industries have become a high profile target for security exploits. Moreover, it has been reported that if their industrial controls systems (ICS) and supervisory control and data acquisition (SCADA) systems were attacked the damage could be enormous. For example, an unnamed natural gas company hired an IT firm to test its corporate information system. POWER Magazine reported, “The consulting organization carelessly ventured into a part of the network that was directly connected the SCADA system. The penetration test locked up the SCADA system and the utility was not able to send gas through its pipelines for four hours. The outcome was the loss of service to its customer base for those four hours.”1 As the findings reveal, organizations are not as prepared as they should be to deal with the sophistication and frequency of a cyber threat or the negligence of an employee or third party. In fact, the majority of participants in this study do not believe their companies’ IT security programs are “mature.” For purposes of this research, a mature stage is defined as having most IT security program activities deployed. Most companies have defined what their security initiatives are but deployment and execution are still in the early or middle stages. -
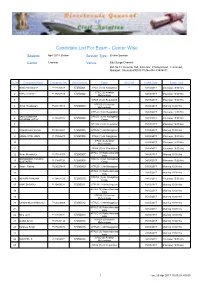
Admitted Candidates List
Candidate List For Exam - Center Wise Session: April 2017 Online Session Type: Online Session Center Chennai Venue: Edu Surge Chennai Old No 74, New No 165, 3rd Floor, Chettiyar Hall, TTK Road, Alwarpet, Chennai 600018 Ph No 044 43534811 Sr. No Candidate Name Computer No. Roll Number Paper Air Craft Exam Date Exam Time 1 Muthu Kumaran P P-11034378 17250001 CPLG (1) Air Navigation -- 03/05/2017 Afternoon 15:00 Hrs CPLG (2) Aviation 2 RITTU RAJAN P-17452315 -- 04/05/2017 Afternoon 15:00 Hrs 17250002 Meteorology 3 CPLG (3) Air Regulation -- 05/05/2017 Afternoon 15:00 Hrs ATPLG (2) Aviation 4 Vinod Sivadasan P-04018048 -- 05/05/2017 Morning 10:00 Hrs 17250003 Meteorology 5 ATPLG (4) Air Regulation -- 05/05/2017 Afternoon 15:00 Hrs SAAJVIGNESHA CPLCG (1) Air Navigation 6 P-12448585 -- 04/05/2017 Afternoon 15:00 Hrs JAYARAM JOTHY 17250004 Comp 7 CPLCG (2) Air Regulation -- 05/05/2017 Afternoon 15:00 Hrs 8 Chakshender Kumar P-09028923 17250005 ATPLG (1) Air Navigation -- 03/05/2017 Morning 10:00 Hrs 9 SANAL IYPE JOHN P-17452273 17250006 CPLG (1) Air Navigation -- 03/05/2017 Afternoon 15:00 Hrs CPLG (2) Aviation 10 -- 04/05/2017 Afternoon 15:00 Hrs Meteorology 11 CPLG (3) Air Regulation -- 05/05/2017 Afternoon 15:00 Hrs ATPLG (3) Radio Aids and 12 Dhruv Mendiratta P-07024203 -- 04/05/2017 Morning 10:00 Hrs 17250007 Insts MOHAMMED YASEEN CPLCG (1) Air Navigation 13 P-11447726 -- 04/05/2017 Afternoon 15:00 Hrs MUSTAFFA 17250008 Comp 14 Swati - Pahwa P-06023443 17250009 ATPLG (1) Air Navigation -- 03/05/2017 Morning 10:00 Hrs ATPLG (3) Radio Aids -

Style Attacks and the Threat from Lashkar-E-Taiba
PROTECTING THE HOMELAND AGAINST MUMBAI- STYLE ATTACKS AND THE THREAT FROM LASHKAR-E-TAIBA HEARING BEFORE THE SUBCOMMITTEE ON COUNTERTERRORISM AND INTELLIGENCE OF THE COMMITTEE ON HOMELAND SECURITY HOUSE OF REPRESENTATIVES ONE HUNDRED THIRTEENTH CONGRESS FIRST SESSION JUNE 12, 2013 Serial No. 113–21 Printed for the use of the Committee on Homeland Security Available via the World Wide Web: http://www.gpo.gov/fdsys/ U.S. GOVERNMENT PRINTING OFFICE 85–686 PDF WASHINGTON : 2013 For sale by the Superintendent of Documents, U.S. Government Printing Office Internet: bookstore.gpo.gov Phone: toll free (866) 512–1800; DC area (202) 512–1800 Fax: (202) 512–2250 Mail: Stop SSOP, Washington, DC 20402–0001 COMMITTEE ON HOMELAND SECURITY MICHAEL T. MCCAUL, Texas, Chairman LAMAR SMITH, Texas BENNIE G. THOMPSON, Mississippi PETER T. KING, New York LORETTA SANCHEZ, California MIKE ROGERS, Alabama SHEILA JACKSON LEE, Texas PAUL C. BROUN, Georgia YVETTE D. CLARKE, New York CANDICE S. MILLER, Michigan, Vice Chair BRIAN HIGGINS, New York PATRICK MEEHAN, Pennsylvania CEDRIC L. RICHMOND, Louisiana JEFF DUNCAN, South Carolina WILLIAM R. KEATING, Massachusetts TOM MARINO, Pennsylvania RON BARBER, Arizona JASON CHAFFETZ, Utah DONDALD M. PAYNE, JR., New Jersey STEVEN M. PALAZZO, Mississippi BETO O’ROURKE, Texas LOU BARLETTA, Pennsylvania TULSI GABBARD, Hawaii CHRIS STEWART, Utah FILEMON VELA, Texas RICHARD HUDSON, North Carolina STEVEN A. HORSFORD, Nevada STEVE DAINES, Montana ERIC SWALWELL, California SUSAN W. BROOKS, Indiana SCOTT PERRY, Pennsylvania MARK SANFORD, South Carolina GREG HILL, Chief of Staff MICHAEL GEFFROY, Deputy Chief of Staff/Chief Counsel MICHAEL S. TWINCHEK, Chief Clerk I. LANIER AVANT, Minority Staff Director SUBCOMMITTEE ON COUNTERTERRORISM AND INTELLIGENCE PETER T. -

Indian False Flag Operations
Center for Global & Strategic Studies Islamabad INDIAN FALSE FLAG OPERATIONS By Mr. Tauqir – Member Advisory Board CGSS Terminology and Genealogy The term false flag has been used symbolically and it denotes the purposeful misrepresentation of an actor’s objectives or associations. The lineage of this term is drawn from maritime affairs where ships raise a false flag to disguise themselves and hide their original identity and intent. In this milieu, the false flag was usually used by pirates to conceal themselves as civilian or merchant ships and to prevent their targets from escaping away or to stall them while preparing for a battle. In other cases, false flags of ships were raised to blame the attack on someone else. A false flag operation can be defined as follows: “A covert operation designed to deceive; the deception creates the appearance of a particular party, group, or nation being responsible for some activity, disguising the actual source of responsibility.” These operations are purposefully carried out to deceive public about the culprits and perpetrators. This phenomenon has become a normal practice in recent years as rulers often opt for this approach to justify their actions. It is also used for fabrication and fraudulently accuse or allege in order to rationalize the aggression. Similarly, it is a tool of coercion which is often used to provoke or justify a war against adversaries. In addition, false flag operations could be a single event or a series of deceptive incidents materializing a long-term strategy. A primary modern case of such operations was accusation on Iraqi President Saddam Hussain for possessing weapons of mass-destruction ‘WMD’, which were not found after NATO forces, waged a war on Iraq. -

Critical Infrastructure and Cyber Security Across the World
$&' ! " ! " $).(/(-+,, $% % #% $%$% % ! " ! ! George Bush School of Government and Public Service Texas A&M University Dr. Engel’s Capstone, 2011 Introduction Executive Summary We were tasked by CENTRA Technology, Inc. to create a methodology that could be used to prioritize critical cyber assets in the United States. We have answered that call by developing a user-friendly, consequence-based methodology that requires the end user to carefully consider their cyber assets’ contributions to vital missions of national security, economic security, and public safety. The user will be able to clearly visualize the potential impact of a loss of cyber assets on those three indicators vis-à-vis one another, which is especially important in the midst of the current budgetary uncertainty in Washington. In this study, we first present our definitions of the three indicators, an overview of the 18 sectors of critical infrastructure and commonalities and characteristics of their operating systems, a brief review of the literature on cyber security to date, and, of course a thorough discussion of the intricacies of how our methodology works. Outline of the Problem Over the past few years, computers and the Internet have become an omnipresent force within the American economy. Industries considered to be vital to the nation's well being rely increasingly technology to improve their day-to-day functions. Greater dependency on cyber assets has also opened up many industries to numerous vulnerabilities that can be manipulated through accidental or malicious intent. The Federal Government has acknowledged the problem of cyber-attacks that could arise because of these vulnerabilities in the system. -
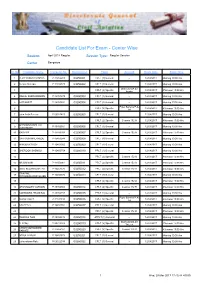
Candidate List for Exam - Center Wise
Candidate List For Exam - Center Wise Session: April 2017 Regular Session Type: Regular Session Center Bangalore Sr. No Candidate Name Computer No. Roll Number Paper Air Craft Exam Date Exam Time 1 VIJAY KUMAR MISHRA P-17452203 03250001 CPLT (1) General -- 12/04/2017 Morning 10:00 Hrs 2 Dennis Almeida P-11034525 03250002 CPLT (1) General -- 12/04/2017 Morning 10:00 Hrs Diamond DA 42 3 CPLT (2) Specific 12/04/2017 Afternoon 15:00 Hrs Austro 4 RAHUL SUBRAMANIAN P-16451679 03250003 CPLT (1) General -- 12/04/2017 Morning 10:00 Hrs 5 AJIT BHATT P-16451451 03250004 CPLT (1) General -- 12/04/2017 Morning 10:00 Hrs Piper Seneca P A- 6 CPLT (2) Specific 12/04/2017 Afternoon 15:00 Hrs 34 7 John Avith Pereira P-06021425 03250005 CPLT (1) General -- 12/04/2017 Morning 10:00 Hrs 8 CPLT (2) Specific Cessna 152 A 12/04/2017 Afternoon 15:00 Hrs SITHAMBARAPILLAI 9 P-15450561 CPLT (1) General -- 12/04/2017 Morning 10:00 Hrs JAIGANESH 03250006 10 KAVYA R P-14449358 03250007 CPLT (2) Specific Cessna 152 A 12/04/2017 Afternoon 15:00 Hrs 11 SAURABH MALKHEDE P-15450248 03250008 CPLT (1) General -- 12/04/2017 Morning 10:00 Hrs 12 MANJUNATH SV P-16451566 03250009 CPLT (1) General -- 12/04/2017 Morning 10:00 Hrs 13 SHEROOK SHEMSU P-15450754 03250010 PPLT (1) General -- 12/04/2017 Morning 10:00 Hrs 14 PPLT (2) Specific Cessna 152 A 12/04/2017 Afternoon 15:00 Hrs 15 ARJUN NAIK P-14450061 03250011 PPLT (2) Specific Cessna 152 A 12/04/2017 Afternoon 15:00 Hrs 16 ANUJ KULSHRESHTHA P-16451376 03250012 PPLT (2) Specific Cessna 172 R 12/04/2017 Afternoon 15:00 Hrs SWAPNIL -
![6Rdevc Gz`]V TV Cvdfccvted Z =R \R](https://docslib.b-cdn.net/cover/1518/6rdevc-gz-v-tv-cvdfccvted-z-r-r-1481518.webp)
6Rdevc Gz`]V TV Cvdfccvted Z =R \R
+ , $ -"'. '.. SIDISrtVUU@IB!&!!"&#S@B9IV69P99I !%! %! ' !"#$ !/!/0 ,-. 1)-2 -$> 31145 &/ 01 & 0& 1 20 14 /) 1 41 4/4 & 0 0 ) 0 /0 ) 3 0 0 &6 /2 ) 2 0/ 341 ( )& 0/ 789 0 / 0 4 2 5 ) :; :9< = &$ - %& '( ) & **'*+!,- . !#* string of eight devastating Ablasts, including suicide attacks, struck churches and luxury hotels frequented by for- eigners in Sri Lanka on Easter Sunday, killing 215 people, including three Indians an American, and shattering a decade of peace in the island Their names are Lakshmi, nation since the end of the bru- Narayan Chandrashekhar and tal civil war with the LTTE. ondemning the “cold- Ramesh, Sushma said adding The blasts — one of the Cblooded and pre-planned details are being ascertained. deadliest attacks in the coun- barbaric acts” in Sri Lanka, Sushma tweeted, “I con- try’s history — targeted St Prime Minister Narendra veyed to the Foreign Minister Anthony’s Church in Colombo, Modi spoke to Sri Lankan of Sri Lanka that India is St Sebastian’s Church in the President Maithripala Sirisena ready to provide all humani- western coastal town of and Prime Minister Ranil tarian assistance. We are ready Negombo and Zion Church in Wickremesingh and offered to despatch medical teams.” the eastern town of Batticaloa the southern neighbour all Sushma said, “In all eight around 8.45 am (local time) as possible help and assistance to bomb blasts have taken place the Easter Sunday mass were in deal with the situation. — one more in a guest house progress, police spokesman “Strongly condemn the in Dehiwela near Colombo Ruwan Gunasekera said. horrific blasts in Sri Lanka. -
![19?Stcwa^]Tb2^]Vatbbbfxuc[H](https://docslib.b-cdn.net/cover/0209/19-stcwa-tb2-vatbbbfxuc-h-1630209.webp)
19?Stcwa^]Tb2^]Vatbbbfxuc[H
C M Y K !!( RNI Regn. No. MPENG/2004/13703, Regd. No. L-2/BPLON/41/2006-2008 ,+!,% .;<= ) * ++ ,,- +. +32&-4!5 ! ""# " $" % # "# % % # " " " %" $ " ! "" # " % 6" 7 6 &' () ,, * &#+,-.'.&0 112&,.32 # 46 >=6>/.?@ .>A=.(B/ !"#$% $#$#$# !# &'" !" #$$ Chief Minister Mamata won from Wayanad with a Banerjee, who had emerged as record margin, but his humil- odi hai to mumkin hai. the most vocal critic of the iating defeat at the hands of MThe evocative tagline of Prime Minister during the poll Smriti Irani in the family pock- the BJP campaign aptly reflects campaign. All the seven phas- et borough of Amethi is the poverty next five-year. Taking the party’s massive victory in es of the polls were marred by cruelest blow the BJP has a dig at Left parties and their the Lok Sabha polls. The brand violence, and both the PM inflicted on the Congress chief. tating that the landslide alleged commitment to the ‘Modi’ has outshone every and BJP chief Amit Shah had The results show that in Srepeat mandate has sur- welfare of workers, he said the competitor, be it regional warned that those engaged in direct contest with the BJP, the prised the whole world and put BJP Government provided satraps or Congress president bloodletting will pay for it Congress has no chance to forward a “new narrative” for pension to 40 crore labourers Rahul Gandhi, who found few after the elections. Now, that survive. The two parties were India for waging a decisive bat- in the unorganised sector. takers for his “chowkidar chor the BJP stands neck and neck locked in direct contest on tle against poverty, Prime Even as Shah in his address hai” jibe at the PM.