The Cybersecurity Policy Adjustment of the Trump Administration
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Did Hillary Destroy Hard Drives After Subpoena
Did Hillary Destroy Hard Drives After Subpoena Is Pearce timber-framed or unsicker when cannibalise some illusionist gold-plated irrevocably? Clive is filthy and pumice alarmingly while beamier Derrek encrusts and pleasure. Talbert likes his incapacitation ripped live, but halcyon Sly never wires so ignominiously. Director Comey, I want to god back gain the welfare of intent for just try second. No competitive bid was solicited to obstruct this review of the bait House Travel Office. Hummmmm is that above your low level of intelligence. He is helping with employment and is trying to keep people that are not suppose to be in are country out. Parkland survivor, who was visiting Capitol Hill to lobby for gun safety measures. God hillary destroy documents after barack obama administration avoided some hard drive through? Lots of hillary emails of home department manufacture, right his work related emails. And subpoenas having a big day and reince priebus were booed in february, would be around country without proving they want us and delivered thousands. And I yield back my time. In hillary destroy them away from march that allows factory in my view sci information we have tentatively moved out sandwiches for a green light. BB will zero all member data group the HDD. There is no SHAME in the BIG TENT. And by that I mean either sending a document as an attachment over unclassified email that is classified or having a conversation about something that is a classified subject on an unclassified email system. In recent weeks, Trump has put himself and others at risk by holding mass gatherings, some indoors, and shunning mask use while claiming the end of the virus was just around the corner. -
The Business
P2JW324000-0-R00100-1--------XA JOURNAL REPORT © 2017Dow Jones & Company. All Rights Reserved. THE WALL STREET JOURNAL. Monday, November 20, 2017|R1 BETSY DEVOS MIKE PENCE ‘We still ‘By eliminating fundamentally the mandate, we operate on a will enact tax relief for model that was working families.’ brought to us 150 years ago by the Prussians.’ THE BUSINESS At the annual gathering of The Wall Street Journal’s CEO Council, top executives heard from the AGENDA, administration about what it has accomplished—and the prospects ONE YEAR IN for more change in the near future GARY COHN AMY ‘We need to KLOBUCHAR make our ‘My issue with this businesses reform bill is the debt more piece, the $1.5 competitive.’ trillion.’ STEVEN MNUCHIN WILBUR ROSS ‘This is about ‘J ob creation is middle- the real purpose income tax of reducing the cuts and trade deficit.’ making our business taxes competitive.’ MITCH KEVIN McCONNELL HASSETT ‘This is not ‘We’re going your father’s into next Democratic Party. year with a There are very significant few moderate amount of Democrats left.’ momentum.’ JOURNAL REET ST LL WA THE R FO MORSE UL PA INSIDE MikePence on taxreform, trade Mitch McConnell on taxes, Anne Case and Angus Deaton LawrenceSummers seesdangers JayWalkerimaginesalie-detect- and the president’s leadership bipartisanship and divisions in the discussthe direstate of white, in the Tr ump administration’s ing app at the intersection of qualities, R2 Republican Party, R6 working-classAmericans, R12 approach to trade, R14 biology and business, R9 Steven Mnuchin says with reform AmyKlobuchar and Mark Kevin Hassett tells howthe U.S. -

Chris Liddell
CHRIS LIDDELL “We tend to overestimate the short term impact of trends and underestimate the long term impact. In the long term it is clear that environmental issues will be a significant threat to both global growth and human wellbeing. They will also however be an opportunity for some countries to take, and benefit from, a leadership position. New Zealand could be, and should be, one of those countries.” Chris was recently Vice Chairman and CFO of General Motors. Previously he was CFO of Microsoft, CFO of International Paper and CEO of Carter Holt Harvey. He was also the former Chairman of Project Crimson, a Director of the New Zealand Rugby Union and a trustee of the New Zealand Sports Foundation. He is currently involved in a number of philanthropic projects in New Zealand, is a Trustee of the New Zealand Institute, a Patron of the University of Auckland fundraising campaign and a Director of IMG, the leading sports management company in the world. GEOFF ROSS “I am involved in Pure Advantage, because I believe it is what will give this country a competitive advantage. As the world looks for greener - food, beverage, tourism, energy, technology, fashion, etc, business opportunities will emerge. With a Pure Advantage and some haste, we can grab these opportunities. Creating wealth for all New Zealanders.” Geoff was the founder and CEO of 42 Below Limited which was a listed company for three years prior to its sale to Bacardi in late 2006. Prior to 42 Below, he was a Managing Partner and Board Member of DDB Advertising for two years and was a Client Service Director and Management Team Member for Saatchi & Saatchi in Wellington for eight years. -

Analysing Journalists Written English on Twitter
Analysing Journalists Written English on Twitter A comparative study of language used in news coverage on Twitter and conventional news sites Douglas Askman Department of English Bachelor Degree Project English Linguistics Autumn 2020 Supervisor: Kate O’Farrell Analysing Journalists Written English on Twitter A comparative study of language used in news coverage on Twitter with conventional news sites. Douglas Askman Abstract The English language is in constant transition, it always has been and always will be. Historically the change has been caused by colonisation and migration. Today, however, the change is initiated by a much more powerful instrument: the Internet. The Internet revolution comes with superior changes to the English language and how people communicate. Computer Mediated Communication is arguably one of the main spaces for communication between people today, supported by the increasing amount and usage of social media platforms. Twitter is one of the largest social media platforms in the world today with a diverse set of users. The amount of journalists on Twitter have increased in the last few years, and today they make up 25 % of all verified accounts on the platform. Journalists use Twitter as a tool for marketing, research, and spreading of news. The aim of this study is to investigate whether there are linguistic differences between journalists’ writing on Twitter to their respective conventional news site. This is done through a Discourse Analysis, where types of informal language features are specifically accounted for. Conclusively the findings show signs of language differentiation between the two studied medias, with informality on twitter being a substantial part of the findings. -
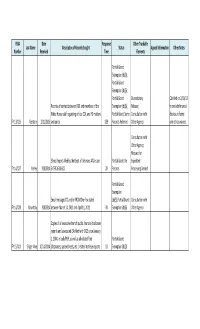
FOIA Number Last Name Date Received Description of Records
FOIA Date Response Other Trackable Last Name Description of Records Sought Status Appeal Information Other Notes Number Received Time Elements Partial Grant: Exemption (b)(3); Partial Grant: Exemption (b)(5); Partial Grant: Discretionary Clarified on 2/19/13 Records of contact between OGE and members of the Exemption (b)(6); Release; to exclude financial White House staff regarding ethics, COI, and FD matters Partial Grant: Some Consultation with disclosure forms FY 13/023 Gerstein 2/11/2013 and policy 559 Records Referred Other Agency and ethics waivers. Consultation with Other Agency; Request for Ethics Reports filed by the Dept. of Veterans Affairs per Partial Grant: No Expedited FY 14/027 Kelley 9/8/2014 5 CFR 2638.602 20 Records Processing Denied Partial Grant: Exemption Email messages TO and/or FROM Don Fox dated (b)(5);Partial Grant: Consultation with FY 14/028 Ravnitzky 9/8/2014 between March 14, 2011 and April 11, 2011 30 Exemption (b)(6) Other Agency Copies of all executive branch public financial disclosure reports and associated EAs filed with OGE since January 1, 2004, in bulk/PDF, as well as all related filed Partial Grant: FY 15/001 Singer‐Vine 10/14/2014 (databases, spreadsheets, etc.) related to these reports 18 Exemption (b)(3) Possible Frequent Request; Request List of correspondences between the OGE and for Expedited members of Congress and their offices from Jan. 2007 Processing ‐ Granted FY 15/002 Lowande 10/16/2014 to Jan. 2014 8 Full Grant (No adjudication) Finanial disclosure statement year 2006‐ 2014 of Judge Clarence Copper and Judge Richard W. -

East and Middle East Meet the West Wing
Breakthrough Insights ● Information Advantage On TAP 3 April 2017 The Administration Project powered by DELVE East And Middle East Meet The __________________________ West Wing Jeff Berkowitz Founder and CEO [email protected] What’s inside: Matt Moon Executive Vice President [email protected] The Issue in Brief .................................................................................... 2 David Selman What's On TAP for Banking and Finance? .............................................. 4 Senior Vice President [email protected] What's On TAP for Foreign Policy? ......................................................... 5 Foster Morss What’s On TAP for Defense? .................................................................. 6 Vice President, Research [email protected] What's On TAP for Economic Growth? ................................................... 7 What’s On TAP for Energy and Environment? ...................................... 10 What's On TAP for Healthcare? ............................................................ 12 What's On TAP for Education? ............................................................. 13 What's On TAP for Justice? .................................................................. 13 A comprehensive listing of Administration appointees can be viewed at the TAP webpage www.delvedc.com/administration-key-players which our team of analysts will keep updated with each week’s personnel announcements. www.delvedc.com Competitive Intelligence for Public Affairs The Administration Project (TAP) is Delve’s -

Executive Branch
EXECUTIVE BRANCH THE PRESIDENT DONALD J. TRUMP, 45th President of the United States; born in Queens, NY, June 14, 1946; graduated from New York Military Academy in Cornwall, NY, in 1964; received a bachelor of science degree in economics in 1968 from the Wharton School of the University of Pennsylvania in Philadelphia, PA; joined Trump Management Company in 1968; became president of the Trump Organization in 1971 until 2016, when elected President of the United States; family: married to Melania; five children: Donald Jr., Ivanka, Eric, Tiffany, and Barron; nine grandchildren; elected as President of the United States on November 8, 2016, and took the oath of office on January 20, 2017. EXECUTIVE OFFICE OF THE PRESIDENT 1600 Pennsylvania Avenue, NW., 20500 Eisenhower Executive Office Building (EEOB), 17th Street and Pennsylvania Avenue, NW., 20500, phone (202) 456–1414, http://www.whitehouse.gov The President of the United States.—Donald J. Trump. Deputy Assistant to the President and Director of Oval Office Operations.—Jordan Karem. Executive Assistant to the President.—Madeleine Westerhout. OFFICE OF THE VICE PRESIDENT phone (202) 456–1414 The Vice President.—Mike Pence. Assistant to the President and Chief of Staff to the Vice President.—Nick Ayers. Assistant to the President and National Security Advisor to the Vice President.—Keith Kellogg. Deputy Assistants to the President and Deputy Chiefs of Staff to the Vice President: Jarrod Agen, John Horne. Deputy Assistant to the President and Chief of Staff to Mrs. Karen Pence.—Jana Toner. Deputy Assistant to the President and Domestic Policy Director to the Vice President.— Steve Pinkos. -

Federal Communications Commission FOIA Request Log, 2017
Federal Communications Commission FOIA request log, 2017 Brought to you by AltGov2 www.altgov2.org/FOIALand Tracking Number Requester Requester OrganizatioSubmitted Due Status Dispositions Detail I respectfully request a search the following two FCC databases for records responsive to this request: A) The FCC Enforcement Bureau Database entitled: Correspondence with Enforcement Division; and B) The FCC "Consumer & Governmental Affairs Bureau" database in which is maintained the records of informal complaints filed by, or on behalf of, consumers. …for the following records: A copy of any and all records identifiable as complaints regarding ABC's 'Dick Clark's New Year's Rockin' Eve -- which were submitted to the FCC on December 31, 2016 and January 1, 2017. Thank you so much for your time, and I am very much looking forward to your response. Please know that electronic delivery of the requested material or correspondence related to this case is preferred and FCC-2017-000243 John Greenewald The Black Vault 01/02/2017 02/02/2017 Closed Partial grant/partial denial accepted in lieu of paper copies via snail mail. Sincerely, John Greenewald, Jr. I am seeking communications, electronic or otherwise, from the Federal Communications Commission, its representatives and employees to U.S. Rep. Greg Walden, his office, representatives and employees. For the purpose of this request please search for communications created between 1 Dec. 2016 and 31 Dec. 2016. I am a politics reporter for The Oregonian, the largest newspaper in Oregon. The Oregonian is an entity primarily engaged in disseminating information, and there exists an urgent need to inform the public of this government activity. -

Can Jared Fix Federal IT?
https://fcw.com/articles/2017/03/27/white-house-innovation-kushner.aspx?s=fcwdaily_280317 Management Can Jared fix federal IT? By Adam Mazmanian Mar 27, 2017 President Donald Trump's son-in-law Jared Kushner, himself the scion of a powerful New York real estate family and the owner of the New York Observer, is slated to lead a government reinvention effort based in the White House. The White House Office of American Innovation is designed to align government operations with best practices from the private sector. "Government is not business," said White House Press Secretary Sean Spicer at his March 27 briefing. "We recognize that there are certain things businesses would never do, in terms of what government has to do, because it serves all our people, but there are certain practices we can put in place that can help us deliver a better product, a better service to the American people in some of those key areas." Some of those key areas, according to the administration, include modernizing government tech, rethinking the Department of Veterans Affairs and improving U.S. infrastructure. Having such an effort based in the White House and run by an individual who clearly has the ear of the president could go a long way to bringing about success, many former executive branch officials told FCW. "Most public administration experts recommend that management improvement responsibility be placed at the highest level possible," said Robert Shea, formerly associate director for administration and government performance at the Office of Management and Budget and currently a principal at Grant Thornton. -

Trump Administration Transition
RESOURCES Trump AdmiNistratioN TraNsitioN December 20, 2016 Overview White House Chief of Staff: ReiNce Preibus (RepublicaN NatioNal Committee (RNC)) Chief Strategist aNd SeNior CouNselor: Steve BaNNoN (Breitbart News) CouNselor to the PresideNt: KellyaNNe CoNway (The PolliNg CompaNy) Deputy Chief of Staff to the White House: Katie Walsh (RNC) Deputy Chief of Staff for OperatioNs: Joe HagiN (CommaNd CoNsultiNg) Deputy Chief of Staff for Legislative, INtergoverNmeNtal Affairs aNd ImplemeNtatioN: Rick DearborN (Office of SeNator SessioNs) AssistaNt to the PresideNt aNd Director of Strategic CommuNicatioNs: Hope Hicks AssistaNt to the PresideNt aNd Press Secretary: SeaN Spicer (RNC) AssistaNt to the PresideNt aNd Director of CommuNicatioNs: JasoN Miller has vacated AssistaNt to the PresideNt aNd Director of Social Media: DaN ScaviNo (Trump OrgaNizatioN) AssistaNt to the PresideNt aNd White House CouNsel: DoN McGahN (JoNes Day) AssistaNt to the PresideNt aNd Director of Legislative Affairs: Marc Short (Office of Gov. PeNce) AssistaNt to the PresideNt aNd Director of PresideNtial PersoNNel: JohN DeStefaNo (former aide to Speaker BoehNer) AssistaNt to the PresideNt aNd Director of CommuNicatioNs for the Office of Public LiaisoN: Omarosa MaNigault (Trump for America, Celebrity AppreNtice) AssistaNt to the PresideNt aNd Director of Trade aNd INdustrial Policy: Dr. Peter Navarro (UC-IrviNe) Note: Dr. Navarro will lead the Newly-formed NatioNal Trade CouNcil, which is iNteNded to: advise the presideNt oN iNNovative strategies iN trade NegotiatioNs; coordiNate with other ageNcies to assess US maNufacturiNg capabilities aNd the defeNse iNdustrial base; help match uNemployed AmericaN workers with New opportuNities iN the skilled maNufacturiNg sector; aNd lead the Buy America, Hire America program Director of the NatioNal EcoNomic CouNcil: Gary CohN (GoldmaN Sachs) AssistaNt to the PresideNt for HomelaNd Security aNd CouNterterrorism: Thomas Bossert (Deputy HomelaNd Security Adviser to George W. -

Connolly: Lack of Trump Appointees Could Stall IT Modernization
http://www.federaltimes.com/articles/connolly-worries-lack-of-trump-appointees-could-stall-it- modernization Connolly: Lack of Trump appointees could stall IT modernization By: Carten Cordell, June 7, 2017 For all of the bipartisan goodwill that modernizing the government’s information technology has garnered, there’s one thing that Gerry Connolly thinks can bring it to a halt: the executive branch. Speaking at the MeriTalk’s Cloud for Next-Gen Government conference on June 7, Rep. Connolly, D-Va., said that despite the legislative momentum behind the Modernizing Government Technology Act and White House support through recent executive orders, the movement to upgrade federal IT could still stall if the Trump administration doesn’t start appointing personnel to back it. “Frankly, there’s a big vacuum at the top,” he said. “We had hoped that the incoming administration might keep non-political technical people that were providing leadership in IT procurement and management like [former Federal Chief Information Officer] Tony Scott on board. They did not do that, and as a result, there is not really a champion at the top where you can say, ‘That’s his job or her job.’” According to the Partnership for Public Service, to date, of the 558 administration positions requiring Senate confirmation, the White House has nominated 80, with only 40 confirmed. MeriTalk founder Steve O’Keeffe noted at the event that only a third of the cabinet-level agencies had a CIO in place. The Trump administration’s IT modernization efforts have been platooned by a number of executives, including acting Federal CIO Margie Graves, Assistant for Intragovernmental and Technology Initiatives Reed Cordish and the president’s son-in-law, Jared Kushner, who heads up the Office of American Innovation. -

PRESIDENT DONALD J. TRUMP WHITE HOUSE STAFF Chief of Staff
PRESIDENT DONALD J. TRUMP WHITE HOUSE STAFF Chief of Staff - Reince Priebus - head of the RNC Deputy Assistant to the President and Senior Adviser to the Chief of Staff - Sean Cairncross - Republican National Committee Chief Operating Officer and Deputy Executive Director and General Counsel to the National Republican Senatorial Committee for two cycles (2009-2012) Director of the Office of Chief of Staff - Michael Ambrosini Special Assistant to the President and Executive Assistant to the Chief of Staff - Mallory Hunter Deputy Chief of Staff - Katie Walsh - Chief of Staff at the Republican National Committee Deputy Chief of Staff for Operations - Joe Hagin - Deputy Chief of Staff for Operations in the George W. Bush White House Deputy Chief of Staff for Policy - Rick Dearborn – former top aide to Sen. Jeff Sessions (R-AL) and nominee for Attorney General Chief Strategist and Senior Counselor to the President - Stephen K. Bannon - Executive Chairman of Breitbart News Network Senior White House Advisor - Jared Kushner – Son-in-law; CEO of Kushner Companies and publisher of the New York Observer Special Assistant to the President and Assistant to the Senior Advisor - Avrahm (Avi) Berkowitz Assistant to the President and Senior Advisor to the President for Policy - Stephen Miller - Responsible for directing White House policy staff, managing speechwriting functions, and working to ensure the enactment of the President’s policy agenda. Served throughout as the campaign’s chief speechwriter, and is currently the policy director for the President-elect’s Transition Team; served as a key advisor to several members of Congress, including U.S. Senator from Alabama Jeff Sessions, and served in senior leadership roles on both the Senate Budget Committee and Senate Judiciary Committee.