G DATA Malware Report H1 2015
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Intro to Google for the Hill
Introduction to A company built on search Our mission Google’s mission is to organize the world’s information and make it universally accessible and useful. As a first step to fulfilling this mission, Google’s founders Larry Page and Sergey Brin developed a new approach to online search that took root in a Stanford University dorm room and quickly spread to information seekers around the globe. The Google search engine is an easy-to-use, free service that consistently returns relevant results in a fraction of a second. What we do Google is more than a search engine. We also offer Gmail, maps, personal blogging, and web-based word processing products to name just a few. YouTube, the popular online video service, is part of Google as well. Most of Google’s services are free, so how do we make money? Much of Google’s revenue comes through our AdWords advertising program, which allows businesses to place small “sponsored links” alongside our search results. Prices for these ads are set by competitive auctions for every search term where advertisers want their ads to appear. We don’t sell placement in the search results themselves, or allow people to pay for a higher ranking there. In addition, website managers and publishers take advantage of our AdSense advertising program to deliver ads on their sites. This program generates billions of dollars in revenue each year for hundreds of thousands of websites, and is a major source of funding for the free content available across the web. Google also offers enterprise versions of our consumer products for businesses, organizations, and government entities. -

1592213370-Monetize.Pdf
Table of Contents 1. Online Monetization: How to Turn Your Following into Cash 1.1 What is monetization? 1.2 How to monetize your website, blog, or social media channel 1.3 Does a monetization formula exist? Chapter 1 Takeaways 2. How to Monetize Your Blog The Right Way 2.1 Why should you start monetizing with your blog? 2.2 How to earn money from blogging 2.3 How to transform your blog visitors into loyal fans 2.4 Blog monetization tools you should know about Chapter 2 Takeaways 3. Facebook Monetization: The What, Why, Where, and How 3.1 How Facebook monetization works 3.2 Facebook monetization strategies Chapter 3 Takeaways 4. How to monetize your Instagram following 4.1 Before you go chasing that Instagram money... 4.2 The four main ways you can earn money on Instagram 4.3 Instagram monetization tools 4.4 Ideas to make money on Instagram Chapter 4 Takeaways 5. Monetizing a YouTube Brand Without Ads 5.1 How to monetize Youtube videos without Adsense 5.2 Essential Youtube monetization tools 5.3 Factors that determine your channel’s long-term success Chapter 5 Takeaways 1. Online Monetization: How to Turn Your Following into Cash 5 Stop me if you’ve heard this one before. Jenn, a customer service agent at a car leasing company, is fed up with her job. Her pay’s lousy, she’s on edge with customers yelling at her over the phone all day (they actually treat her worse in person), and her boss ignores all her suggestions, even though she knows he could make her job a lot less stressful. -

Google Adsense Fuels Growth for Android- Focused Site
Google AdSense Case Study Google AdSense fuels growth for Android- focused site About elandroidelibre • elandoidelibre.com • Based in Madrid • Blog about the Android operating system “We regard AdSense as an essential tool that’s helping us to set up more blogs, take on more staff, and earn more revenue.” — Paolo Álvarez, administrator and editor. elandroidelibre.com (“the free Android”) is a leading Spanish-language blog about the Android operating system, featuring news, reviews, games and other apps for Android smartphone users. Launched in 2009, it now employs six people and attracts 6.5 million visits each month. Since the outset, Google AdSense has accounted for around 40 per cent of its income. Administrator and editor Paolo Álvarez says: “I was attracted to AdSense because it was simple and effective. I began using it right from the start, and even though I wasn’t an expert, I could see that it worked.” He’s highly satisfied with the quality and relevance of the ads appearing on his site, and says the 300 x 250 Medium Rectangle and the 728 x 90 Leaderboard formats work particularly well. Álvarez uses Google AdSense reports and Google Analytics to analyse the return on the site and gain a better understanding of the kind of visitors it attracts: for example 30 per cent of traffic and income comes from mobile devices. He has also begun using Google’s free ad serving solution, DoubleClick for Publishers, allowing him to manage his online advertising more effectively and segment traffic from different countries. He plans to continue improving the quality and quantity of content in the future. -

Broadband Video Advertising 101
BROADBAND VIDEO ADVERTISING 101 The web audience’s eyes are already on broadband THE ADVERTISING CHALLENGES OF video, making the player and the surrounding areas the ONLINE PUBLISHERS perfect real estate for advertising. This paper focuses on what publishers need to know about online advertising in Why put advertising on your broadband video? When order to meet their business goals and adapt as the online video plays on a site, the user’s attention is largely drawn advertising environment shifts. away from other content areas on the page and is focused on the video. The player, therefore, is a premium spot for advertising, and this inventory space commands a premium price. But adding advertising to your online video involves a lot of moving parts and many decisions. You need to consider the following: • What types and placements of ads do you want? • How do you count the ads that are viewed? • How do you ensure that the right ad gets shown to the right viewer? Luckily, there are many vendors that can help publishers fill up inventory, manage their campaigns, and get as much revenue from their real estate as possible. This paper focuses on the online advertising needs of the publisher and the services that can help them meet their advertising goals. THE VIDEO PLATFORM COMCASTTECHNOLOGYSOLUTIONS.COM | 800.844.1776 | © 2017 COMCAST TECHNOLOGY SOLUTIONS ONLINE VIDEO ADS: THE BASICS AD TYPES You have many choices in how you combine ads with your content. The best ads are whatever engages your consumers, keeps them on your site, and makes them click. -
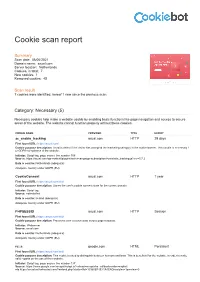
Cookie Scan Report
Cookie scan report Summary Scan date: 08/06/2021 Domain name: axual.com Server location: Netherlands Cookies, in total: 7 New cookies: 1 Removed cookies: 45 Scan result 7 cookies were identified, hereof 1 new since the previous scan. Category: Necessary (5) Necessary cookies help make a website usable by enabling basic functions like page navigation and access to secure areas of the website. The website cannot function properly without these cookies. COOKIE NAME PROVIDER TYPE EXPIRY ac_enable_tracking axual.com HTTP 29 days First found URL: https://axual.com/ Cookie purpose description: Used to detect if the visitor has accepted the marketing category in the cookie banner. This cookie is necessary f or GDPR-compliance of the website. Initiator: Script tag, page source line number 508 Source: https://axual.com/wp-content/plugins/activecampaign-subscription-forms/site_tracking.js?ver=5.7.2 Data is sent to: Netherlands (adequate) Adequate country under GDPR (EU) CookieConsent axual.com HTTP 1 year First found URL: https://axual.com/trial/ Cookie purpose description: Stores the user's cookie consent state for the current domain Initiator: Script tag Source: notinstalled Data is sent to: Ireland (adequate) Adequate country under GDPR (EU) PHPSESSID axual.com HTTP Session First found URL: https://axual.com/trial/ Cookie purpose description: Preserves user session state across page requests. Initiator: Webserver Source: axual.com Data is sent to: Netherlands (adequate) Adequate country under GDPR (EU) rc::a google.com HTML Persistent First found URL: https://axual.com/trial/ Cookie purpose description: This cookie is used to distinguish between humans and bots. -

Ei-Report-2013.Pdf
Economic Impact United States 2013 Stavroulla Kokkinis, Athina Kohilas, Stella Koukides, Andrea Ploutis, Co-owners The Lucky Knot Alexandria,1 Virginia The web is working for American businesses. And Google is helping. Google’s mission is to organize the world’s information and make it universally accessible and useful. Making it easy for businesses to find potential customers and for those customers to find what they’re looking for is an important part of that mission. Our tools help to connect business owners and customers, whether they’re around the corner or across the world from each other. Through our search and advertising programs, businesses find customers, publishers earn money from their online content and non-profits get donations and volunteers. These tools are how we make money, and they’re how millions of businesses do, too. This report details Google’s economic impact in the U.S., including state-by-state numbers of advertisers, publishers, and non-profits who use Google every day. It also includes stories of the real business owners behind those numbers. They are examples of businesses across the country that are using the web, and Google, to succeed online. Google was a small business when our mission was created. We are proud to share the tools that led to our success with other businesses that want to grow and thrive in this digital age. Sincerely, Jim Lecinski Vice President, Customer Solutions 2 Economic Impact | United States 2013 Nationwide Report Randy Gayner, Founder & Owner Glacier Guides West Glacier, Montana The web is working for American The Internet is where business is done businesses. -

Google-Doubleclick Case
Statement of FEDERAL TRADE COMMISSION Concerning Google/DoubleClick FTC File No. 071-0170 The Federal Trade Commission has voted 4-11 to close its investigation of Google’s proposed acquisition of DoubleClick after a thorough examination of the evidence bearing on the transaction. The Commission dedicated extensive resources to this investigation because of the importance of the Internet and the role advertising has come to play in the development and maintenance of this rapidly evolving medium of communication.2 Online advertising fuels the diversity and wealth of free information available on the Internet today. Our investigation focused on the impact of this transaction on competition in the online advertising marketplace. The investigation was conducted pursuant to the Commission’s statutory authority under the Clayton Act to review mergers and acquisitions. If this investigation had given the Commission reason to believe that the transaction was likely to harm competition and injure consumers, the Commission could have filed a federal court action seeking to enjoin the transaction under Section13(b) of the Federal Trade Commission Act (“FTC Act”) and Section 15 of the Clayton Act. The standard used by the Commission to review mergers and acquisitions is set forth in Section 7 of the Clayton Act. That statute prohibits acquisitions or mergers, the effect of which “may be substantially to lessen competition, or to tend to create a monopoly.” The Commission can apply Section 7 (as well as Section 1 of the Sherman Act and Section 5 of the FTC Act) to challenge transactions that threaten to create, enhance, or facilitate the exercise of market power. -

Google Adsense •Doubleclick •MSN.Com •Yahoo Publisher •Valueclick Network •AOL.Com •Aquantive •Quigo •Ask.Com •24/7 Real Media
DefiningDefining thethe RelevantRelevant ProductProduct MarketMarket forfor GoogleGoogle-- DoubleClickDoubleClick MergerMerger Robert W. Hahn, Reg-Markets Hal J. Singer, Criterion Economics IndustryIndustry BackgroundBackground InIn 2007,2007, U.S.U.S. advertisersadvertisers werewere expectedexpected forfor thethe firstfirst timetime toto spendspend moremore onon onlineonline advertisingadvertising thanthan onon radioradio advertisingadvertising • Source: eMarketer U.S.U.S. onlineonline advertisingadvertising revenuesrevenues inin 20072007 werewere roughlyroughly $17$17 billion,billion, anan increaseincrease ofof 3535 percentpercent overover 20052005 revenuesrevenues • Source: Interactive Advertising Bureau 2 TheThe InputsInputs toto anan OnlineOnline AdAd Suppliers of online advertising provide three primary inputs: (1) ad tools, (2) intermediation, and (3) publisher tools Ad tools: software packages that allow advertisers to manage inventory and produce ads Intermediation: matching advertisers (buyers) to publishers (sellers) in an advertising marketplace • publishers’ direct sales forces • “ad networks” (resell publisher ad space) • “ad exchanges” (match advertisers and publishers) 3 ResearchResearch AgendaAgenda OurOur analysisanalysis focusesfocuses onon whetherwhether differentdifferent channelschannels ofof onlineonline advertisingadvertising representrepresent aa singlesingle productproduct marketmarket Limitation:Limitation: WeWe dodo notnot analyzeanalyze whetherwhether otherother formsforms ofof advertisingadvertising -

Why Google Dominates Advertising Markets Competition Policy Should Lean on the Principles of Financial Market Regulation
Why Google Dominates Advertising Markets Competition Policy Should Lean on the Principles of Financial Market Regulation Dina Srinivasan* * Since leaving the industry, and authoring The Antitrust Case Against Face- book, I continue to research and write about the high-tech industry and competition, now as a fellow with Yale University’s antitrust initiative, the Thurman Arnold Pro- ject. Separately, I have advised and consulted on antitrust matters, including for news publishers whose interests are in conflict with Google’s. This Article is not squarely about antitrust, though it is about Google’s conduct in advertising markets, and the idea for writing a piece like this first germinated in 2014. At that time, Wall Street was up in arms about a book called FLASH BOYS by Wall Street chronicler Michael Lewis about speed, data, and alleged manipulation in financial markets. The controversy put high speed trading in the news, giving many of us in advertising pause to appre- ciate the parallels between our market and trading in financial markets. Since then, I have noted how problems related to speed and data can distort competition in other electronic trading markets, how lawmakers have monitored these markets for con- duct they frown upon in equities trading, but how advertising has largely remained off the same radar. This Article elaborates on these observations and curiosities. I am indebted to and thank the many journalists that painstakingly reported on industry conduct, the researchers and scholars whose work I cite, Fiona Scott Morton and Aus- tin Frerick at the Thurman Arnold Project for academic support, as well as Tom Fer- guson and the Institute for New Economic Thinking for helping to fund the research this project entailed. -

Google Data Collection —NEW—
Digital Content Next January 2018 / DCN Distributed Content Revenue Benchmark Google Data Collection —NEW— August 2018 digitalcontentnext.org CONFIDENTIAL - DCN Participating Members Only 1 This research was conducted by Professor Douglas C. Schmidt, Professor of Computer Science at Vanderbilt University, and his team. DCN is grateful to support Professor Schmidt in distributing it. We offer it to the public with the permission of Professor Schmidt. Google Data Collection Professor Douglas C. Schmidt, Vanderbilt University August 15, 2018 I. EXECUTIVE SUMMARY 1. Google is the world’s largest digital advertising company.1 It also provides the #1 web browser,2 the #1 mobile platform,3 and the #1 search engine4 worldwide. Google’s video platform, email service, and map application have over 1 billion monthly active users each.5 Google utilizes the tremendous reach of its products to collect detailed information about people’s online and real-world behaviors, which it then uses to target them with paid advertising. Google’s revenues increase significantly as the targeting technology and data are refined. 2. Google collects user data in a variety of ways. The most obvious are “active,” with the user directly and consciously communicating information to Google, as for example by signing in to any of its widely used applications such as YouTube, Gmail, Search etc. Less obvious ways for Google to collect data are “passive” means, whereby an application is instrumented to gather information while it’s running, possibly without the user’s knowledge. Google’s passive data gathering methods arise from platforms (e.g. Android and Chrome), applications (e.g. -

How to Monetize Web 2.0
$129 ISBN: 978-1-932353-78-5 Subscription Marketers: How to Monetize Web 2.0 A MarketingSherpa Toolkit MarketingSherpa ToolKit: Subscription Marketers - How to Monetize Web 2.0 MarketingSherpa ToolKit: Subscription Marketers: How to Monetize Web 2.0 ISBN: 978-1-932353-78-5 Copyright © 2008 by MarketingSherpa Inc. All rights reserved. No part of this kit may be reproduced (except for private use) or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, faxing, emailing, posting online or by any information storage and retrieval system, without written permission from the Publisher. To purchase additional copies of this report, please visit http://www.SherpaStore.com Yes, bulk discounts are available for multiple copies. Contact: Customer Service MarketingSherpa Inc. +1 (877) 895-1717 (outside US call +401-247-7655) [email protected] 499 Main St. Warren, RI 02885 USA MarketingSherpa ToolKit: Subscription Marketers - How to Monetize Web 2.0 TABLE OF CONTENTS GLOssary .........................................................4 5 Tips for Starting a Web 2.0 Site ............................... 25 Case Study: How ESPN Added Web 2.0 to Boost SECTION 1: WHY CONTENT PUBLISHErs Paid Subscriber Rates ................................................ 26 NEED WEB 2.0 ...................................................5 Types of Web 2.0 ......................................................... 5 SECTION 4: SOCIAL NETWORKING – Social networking .................................................. 5 THE -

Marketing and Advertising Using Google™ Targeting Your Advertising to the Right Audience
Marketing and Advertising Using Google™ Targeting Your Advertising to the Right Audience Marketing and Advertising Using Google™ Copyright © 2007 Google Inc. All rights reserved To order additional copies call (800) 355-9983 (Thomson Custom Customer Service) or go to: adwords.thomsoncustom.com ISBN: -426-62737-8 We want to hear your feedback about this book. Please email [email protected]. Marketing and Advertising Using Google™ Lesson 1 – Google Search Marketing: AdWords Topic – Online Advertising: A Brief History of a Young Medium 5 Topic 2 – Online Advertising Joins the Marketing Mix 8 Topic 3 – Behind the Scenes: How Google Search Works 11 Topic 4 – AdWords Ads Fundamentals 15 Topic 5 – AdWords Ads Appear Across Many Websites 18 Lesson 2 – Overview of Google AdWords Accounts Topic – Getting Started: AdWords Starter Edition 29 Topic 2 – How Ads Are Shown: The AdWords Auction 37 Topic 3 – Ad Rank, AdWords’ Discounter, and Basic Tenets of Optimization 39 Topic 4 – Introduction to Site-Targeted Campaigns 40 Topic 5 – Ad Formats 45 Lesson 3 – Successful Keyword-Targeted Advertising Topic – Choosing the Right Keywords 53 Topic 2 – Writing Successful Ad Text 56 Topic 3 – Choosing Relevant Landing Pages 58 Topic 4 – Monitoring Performance and Analyzing an Ad’s Quality Score 60 Topic 5 – How Do Advertisers Know Their Quality Score? 6 Topic 6 – Optimize Ads to Boost Performance and Quality Score 62 Lesson 4 – Image and Video Ads Topic – Overview of Image Ads 69 Topic 2 – Video Ads 72 Topic 3 – Tips on Creating Successful Video