Cooperative Border Security for Jordan: Assessment and Options
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
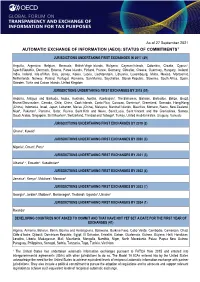
Automatic Exchange of Information: Status of Commitments
As of 27 September 2021 AUTOMATIC EXCHANGE OF INFORMATION (AEOI): STATUS OF COMMITMENTS1 JURISDICTIONS UNDERTAKING FIRST EXCHANGES IN 2017 (49) Anguilla, Argentina, Belgium, Bermuda, British Virgin Islands, Bulgaria, Cayman Islands, Colombia, Croatia, Cyprus2, Czech Republic, Denmark, Estonia, Faroe Islands, Finland, France, Germany, Gibraltar, Greece, Guernsey, Hungary, Iceland, India, Ireland, Isle of Man, Italy, Jersey, Korea, Latvia, Liechtenstein, Lithuania, Luxembourg, Malta, Mexico, Montserrat, Netherlands, Norway, Poland, Portugal, Romania, San Marino, Seychelles, Slovak Republic, Slovenia, South Africa, Spain, Sweden, Turks and Caicos Islands, United Kingdom JURISDICTIONS UNDERTAKING FIRST EXCHANGES BY 2018 (51) Andorra, Antigua and Barbuda, Aruba, Australia, Austria, Azerbaijan3, The Bahamas, Bahrain, Barbados, Belize, Brazil, Brunei Darussalam, Canada, Chile, China, Cook Islands, Costa Rica, Curacao, Dominica4, Greenland, Grenada, Hong Kong (China), Indonesia, Israel, Japan, Lebanon, Macau (China), Malaysia, Marshall Islands, Mauritius, Monaco, Nauru, New Zealand, Niue4, Pakistan3, Panama, Qatar, Russia, Saint Kitts and Nevis, Saint Lucia, Saint Vincent and the Grenadines, Samoa, Saudi Arabia, Singapore, Sint Maarten4, Switzerland, Trinidad and Tobago4, Turkey, United Arab Emirates, Uruguay, Vanuatu JURISDICTIONS UNDERTAKING FIRST EXCHANGES BY 2019 (2) Ghana3, Kuwait5 JURISDICTIONS UNDERTAKING FIRST EXCHANGES BY 2020 (3) Nigeria3, Oman5, Peru3 JURISDICTIONS UNDERTAKING FIRST EXCHANGES BY 2021 (3) Albania3, 7, Ecuador3, Kazakhstan6 -

The Egypt-Palestine/Israel Boundary: 1841-1992
University of Northern Iowa UNI ScholarWorks Dissertations and Theses @ UNI Student Work 1992 The Egypt-Palestine/Israel boundary: 1841-1992 Thabit Abu-Rass University of Northern Iowa Let us know how access to this document benefits ouy Copyright ©1992 Thabit Abu-Rass Follow this and additional works at: https://scholarworks.uni.edu/etd Part of the Human Geography Commons Recommended Citation Abu-Rass, Thabit, "The Egypt-Palestine/Israel boundary: 1841-1992" (1992). Dissertations and Theses @ UNI. 695. https://scholarworks.uni.edu/etd/695 This Open Access Thesis is brought to you for free and open access by the Student Work at UNI ScholarWorks. It has been accepted for inclusion in Dissertations and Theses @ UNI by an authorized administrator of UNI ScholarWorks. For more information, please contact [email protected]. THE EGYPT-PALESTINE/ISRAEL BOUNDARY: 1841-1992 An Abstract of a Thesis .Submitted In Partial Fulfillment of the Requirements for the ~egree Master of Arts Thabit Abu-Rass University of Northern Iowa July 1992 ABSTRACT In 1841, with the involvement of European powers, the Ottoman Empire distinguished by Firman territory subject to a Khedive of Egypt from that subject more directly to Istanbul. With British pressure in 1906, a more formal boundary was established between Egypt and Ottoman Palestine. This study focuses on these events and on the history from 1841 to the present. The study area includes the Sinai peninsula and extends from the Suez Canal in the west to what is today southern Israel from Ashqelon on the Mediterranean to the southern shore of the Dead Sea in the east. -

Egypt & Jordan
G E O T O U R S EGYPT & JORDAN JANUARY 24 – FEBRUARY 10, 2021 PALAWAN EGYPT & JORDAN = $2890 (16 days/15 nights in Egypt & Jordan) Included – Hotels, breakfasts, 3 lunches, 4 dinners, entries, flight from Cairo to Amman, transportation, guides, Matt and/or Suzan Ebiner as group leader Not Included – Airfare from USA (about $800); meals not listed above, tips to guides and drivers Highlights: Pyramids & Sphinx of Giza, Cairo (Citadel, Khan el Khalili bazaar, Egyptian Museum with King Tut’s treasures), Camel Ride to an old desert monastery, Nubian village and dinner, Luxor (Valley of the Kings and Hatshepsut Temple), Felucca (traditional sailboat) ride on the Nile River from Aswan to Kom Ombo (1 night sleeping on deck on the Nile riverbank); Jordan: Wadi Rum (desert safari and camp, Bedouin culture); Petra (ancient city carved into stone cliffs; one of the greatest archeological sites in the world); Madaba (Byzantine mosaics), Dead Sea (float in the saltiest, lowest body of water on earth), Amman (Jordan’s capital); Jerash (great ancient Roman city) Sun 1/24/21 Depart USA to Egypt Depart the USA for Cairo, Egypt Mon 1/25/21 Arrive Cairo, Egypt Welcome to Egypt! Two nights in Cairo at Pyramisa Suites Hotel (5*) or equivalent. Tue 1/26/21 Cairo Spend a full day in Cairo to enjoy some of Egypt’s highlights. Start at the Pyramids and Sphinx, and marvel at the most famous ancient site on the planet. For extra cost you can ride a camel or go inside the interior of one of the pyramids. -

The Disi Aquifer: a Silenced Conflict Between Jordan and Saudi Arabia
TheThe securitizationsecuritization ofof thethe DisiDisi Aquifer:Aquifer: aa silentsilent conflictconflict betweenbetween JordanJordan andand SaudiSaudi ArabiaArabia DisiDisi isis ¾ AA sharedshared groundwatergroundwater basinbasin ¾ AA nonnon renewablerenewable aquiferaquifer ¾ AA projectproject withwith aa heavyheavy environmentalenvironmental impactimpact ¾ FarFar fromfrom AmmanAmman andand consequentlyconsequently costlycostly OurOur theoreticaltheoretical toolstools ¾¾ TheThe securitizationsecuritization continuumcontinuum Non- Politicised Securitized Violised politicised ¾¾TheThe SanctionedSanctioned discoursediscourse ¾¾TheThe hydraulichydraulic missionmission conceptconcept ¾¾TheThe conceptconcept ofof “non“non violentviolent conflict”conflict” ¾¾SilenceSilence asas aa methodmethod ofof controlcontrol && powerpower ¾¾PriorPrior useuse conceptconcept WhyWhy DisiDisi?? ¾¾JordanJordan isis oneone ofof thethe countriescountries locatedlocated withinwithin Israel’sIsrael’s hegemonichegemonic areaarea ¾¾AsAs aa consequenceconsequence ofof thisthis ,Jordan,Jordan chosechose thethe optionoption toto embarkembark onon aa conflictconflict withwith SaudiSaudi ArabiaArabia thanthan openingopening aa newnew bargainingbargaining processprocess withwith IsraelIsrael ¾¾DisiDisi isis thereforetherefore anan effecteffect ofof dominancedominance dependingdepending onon thethe IsraeliIsraeli “hydro“hydro--HegemonHegemon status”status” TheThe politicizationpoliticization phasephase ¾ Disi was discovered in 1984 and until the 1990s geological and hydro-chemical -

Solomon's Navy in the Context of Maritime Trade Relations in Iron Age South Levant
Eva Katarina Glazer, Danijel Štruklec - Solomon’s navy in... (161-168) Histria Antiqua, 21/2012 Eva Katarina GLAZER, Danijel ŠTRUKLEC SOLOMON’S NAVY IN THE CONTEXT OF MARITIME TRADE RELATIONS IN IRON AGE SOUTH LEVANT UDK 903:339.165.4>(262.2)”638” dr. sc. Eva Katarina Glazer Original scientific paper Hrvatski studiji, Odjel za povijest Received: 14.06.2012. Sveučilište u Zagrebu, Approved: 23.08.2012. Borongajska cesta 83 D, 10 000 Zagreb, Hrvatska [email protected] Danijel Štruklec, M. Hist. Hrvatski studiji Sveučilište u Zagrebu, Borongajska cesta 83 D, 10 000 Zagreb, Hrvatska [email protected] evant can be seen as an important link between the two great centers of social and historical events of the Near East, Mesopotamia and Egypt. In Early Iron Age, this area was marked by many social changes, such as the weakening of LEgypts supremacy in the Levant area and the emergence of new ethnic groups like the Philistines and Israelites. The problem of Israel’s monarchy and Solomon, David’s successor is an important topic in the scientific world for a long time now. What does the Old Testament tell and what is the archaeological evidence? How strong was the monarchy of Solomon and what was its relation to neighboring nations? With the help of archaeological and literary sources this paper attempts to present as faithfully as possible the social relations between Israel and some of the people in the southern Levant. Solomon’s navy is the key to understanding these relationships, in both political and economic aspects. The importance of maritime trade, maritime routes and harbors suggest a great social activity, and according to the Old Testament the foundation of Solomon’s wealth. -

Environmental Assessment, Documentation and Spatial Modeling of Heavy Metal Pollution Along the Jordan Gulf of Aqaba Using Coral Reefs As Environmental Indicator
Environmental Assessment, Documentation and Spatial Modeling of Heavy Metal Pollution along the Jordan Gulf of Aqaba Using Coral Reefs as Environmental Indicator Doctorate Thesis Submitted to Department of Hydrogeology and Environment Julius-Maximilians-University of Würzburg By Nedal Al Ouran from At Tafileh/Jordan Würzburg, 2005 Umweltbewertung, Dokumentation und räumliche Modellierung der Schwermetallverschmutzung entlang der Küste von Aqaba (Jordanien) unter Verwendung von Korallenriffen als Umweltindikator Dissertation zur Erlangung des naturwissenschaftlichen Doktorgrades der Bayerischen Julius-Maximilians-Universität Würzburg vorgelegt von Nedal Al Ouran aus At Tafileh/Jordanien Würzburg, 2005 Eingereicht am: 1. Gutachter der Dissertation: Prof. Dr. P. Udluft 2. Gutachter der Dissertation: Prof. Dr. E. Salameh 1. Prüfer: Prof. Dr. P. Udluft 2. Prüfer: Prof. Dr. D. Busche Tag der mündlichen Prüfung: Doktorurkunde ausgehändigt am: Nedal M. Al Ouran i Acknowledgment I am deeply indebted to my supervisor, Professor Peter Udluft for his constant support. Through the facilities offered to me during this work, all things went very smooth, and I should acknowledge his assistance in supplying invaluable literature which was not available at the university of Würzburg or not accessible online. Without his help, this work would not have actually been possible. Deep thanks and appreciation are due to my Co-supervisor Prof Elias Salameh; University of Jordan. I will never forget the extreme confidence he has offered me pertaining the research, as I was confused at the very early stages to go ahead with such pilot work in Aqaba. I am also much indebted to Mr. Peter Zolda, University of Vienna, for the help he has offered in selecting the sampling sites, and providing one of the three cores used in this research, (to avoid further damage to the reef) in addition to the determination of the core geochronology. -

Religion & Faith Biblical
Ahlan Wa Sahlan Welcome to the Hashemite Kingdom of Jordan, founded by carved from rock over 2000 years ago, it also offers much more King Abdullah I, and currently ruled by King Abdullah II son of for the modern traveller, from the Jordan Valley, fertile and ever the late King Hussein. Over the years, Jordan has grown into a changing, to the remote desert canyons, immense and still. stable, peaceful and modern country. Whether you are a thrill seeker, a historian, or you just want to relax, Jordan is the place for you. While Jordan is known for the ancient Nabataean city of Petra, Content Biblical Jordan 2 Bethany Beyond the Jordan 4 Madaba 6 Mount Nebo 8 Mukawir 10 Tall Mar Elias 11 Anjara 11 Pella 12 As-Salt 12 Umm Qays 13 Umm Ar-Rasas 14 Jerash 15 Petra 16 Umm Ar-Rasas Hisban 17 The Dead Sea & Lot’s Cave 18 Amman 20 Aqaba 21 MAP LEGEND The King’s Highway 22 Historical Site Letters of Acknowledgement 23 Castle Itineraries 24 Religious Site Hotel Accommodation Camping Facilities Showkak Airport Road Highway Railway Bridge Nature / Wildlife Reserve Jordan Tourism Board: Is open Sunday to Thursday (08:00-17:00). Petra, the new world wonder UNESCO, world heritage site 1 BIBLICAL JORDAN The Hashemite Kingdom of Jordan has proven home to some of the most influential Biblical leaders of the past; Abraham, Job, Moses, Ruth, Elijah, John the Baptist, Jesus Christ and Paul, to name a few. As the only area within the Holy Land visited by all of these great individuals, Jordan breathes with the histories recorded in the Holy Bible. -

History and Culture.Indd
History & Culture Table of Contents Map of Jordan 1 L.Tiberius Umm Qays Welcome 2 Irbid Jaber Amman 4 Pella Hemmeh Ramtha er As-Salt HISTORY & CULTURE12 ITINERARIES Ajlun Mafraq Madaba 14 dan Riv Jerash Deir 'Alla Umm al-Jimal 1 Day Tour Options: Jor Umm Ar-Rasas1. Jerash, Ajlun 16 ey Salt Qasr Al Hallabat Mount Nebo2. Amman (City Tour) 17 all Zarqa Marka 3. Madaba, Mount Nebo, Bethany Beyond the Jordan V dan Jordan Valley & The Dead Sea 18 Jor Amman Iraq al-Amir Qusayr Amra Azraq Karak 20 Bethany Beyond The Jordan Mt. Nebo Qasr Al Mushatta 3 Day Itinerary: Dead Sea Spas Queen Alia Qasr Al Kharrana Petra 22 Madaba International Day 1. Amman, Jerash, Madaba and Dead Sea - Overnight in Ammana Airport e Hammamat Ma’in Aqaba Day 2. Petra - Overnight in26 Little Petra S d Dhiban a Umm Ar-Rasas Jerash Day 3. Karak, Madaba and30 Mount Nebo - Overnight in Ammane D Ajlun 36 5 Day Itinerary: Umm Al-Jimal 38 Qatraneh Day 1. Amman, Jerash, Ajlun - Overnight in Amman Karak Pella 39 Mu'ta Day 2. Madaba, Mount Nebo, Karak - Overnight at PetraAl Mazar aj-Janubi Umm QaysDay 3. Petra - Overnight at40 Petra Shawbak Day 4. Wadi Rum - Overnight42 Dead Sea Tafileh Day 5. Bethany Beyond The Jordan MAP LEGEND Desert Umayyad Castles 44 History & Culture Itineraries 49 Historical Site Shawbak Highway Castle Desert Wadi Musa Petra Religious Site Ma'an Airport Ras an-Naqab Road For further information please contact: Highway Jordan Tourism Board: Tel: +962 6 5678444. It is open daily (08:00- Railway 16:00) except Fridays. -

Trade Logistics in Egypt and Jordan (Work in Progress
Trade Logistics in Egypt and Jordan Prepared by Peter H. J. Yee (Work in progress - Please do not quote) The findings, interpretations and conclusions expressed in this paper are entirely those of the authors and do not necessarily represent the views of the World Bank, its Executive Directors, or the countries they represent. 1. Introduction The purpose of this paper is twofold: firstly, to review the trade logistics systems of Egypt and Jordan with respect to the level of performance and the degree of friction in the logistics chain; and, secondly, to prescribe policy measures for removing or alleviating the impediments to efficient trade. Two export products, garments and vegetables, for each country are investigated from a supply chain perspective, as measured by logistics costs and processing times. Trade logistics cost is quantified in terms of transport charges and non-transport related logistics costs (capital carrying costs, cost of safety stock, etc.), the latter reflecting the impact of poor service levels in the freight logistics system.1 An efficient trade logistics system has many requisites, such as good transport infrastructure, competitive carriers, competent transport intermediaries, fast cross-border procedures, customer oriented banking and insurance sectors, modern information and communication technology, and a sound legal framework. Above all, good trade logistics needs proficient exporters and importers who are knowledgeable and skilled in international commercial terms, documentary credits, document handling, and multimodal transport arrangements to name a few, so that transaction costs are kept to a minimum through proper handling. Conversely, an inefficient trade logistics system will manifest many sources of friction, notably the areas mentioned previously, slowing down the flow of trade by lengthening the order-to-delivery cycle time with concomitant high deadweight costs. -

JORDAN, PALESTINE and ISRAEL Giulia Giordano and Lukas Rüttinger
MIDDLE EAST CLIMATE-FRAGILITY RISK BRIEF JORDAN, PALESTINE AND ISRAEL Giulia Giordano and Lukas Rüttinger This is a knowledge product provided by: CLIMATE-FRAGILITY RISK BRIEF: JORDAN, PALESTINE AND ISRAEL AUTHORED BY Dr. Giulia Giordano is an Italian researcher and practitioner with extensive experience in the Middle East. She is now the Director of International Programs at EcoPeace Middle East, a trilateral organization based in Israel, Jordan and Palestine. Her research interests are Middle Eastern studies, the Israeli-Palestinian conflict, and environmental diplomacy. Lukas Rüttinger is a Senior Advisor at adelphi, working at the intersection of environment, development, foreign and security policy. He has published widely on these topics and was the lead author of the 2015 report “A New Climate for Peace”. PROVIDED BY The Climate Security Expert Network, which comprises some 30 international experts, supports the Group of Friends on Climate and Security and the Climate Security Mechanism of the UN system. It does so by synthesising scientific knowledge and expertise, by advising on entry points for building resilience to climate-security risks, and by helping to strengthen a shared understanding of the challenges and opportunities of addressing climate-related security risks. www.climate-security-expert-network.org The climate diplomacy initiative is a collaborative effort of the German Federal Foreign Office in partnership with adelphi. The initiative and this publication are supported by a grant from the German Federal Foreign Office. www.climate-diplomacy.org SUPPORTED BY LEGAL NOTICE Contact: [email protected] Published by: adelphi research gGmbH, Alt-Moabit 91, 10559 Berlin, Germany www.adelphi.de CORPORATE DESIGN MANUAL The analysis, results, recommendations and graphics in this paper represent the opinion of STAND VOM 08.12.2010 the authors and are not necessarily representative of the position of any of the organisations listed above. -

CONGRESSIONAL RECORD— Extensions Of
July 20, 2010 CONGRESSIONAL RECORD — Extensions of Remarks E1377 I share Troop 463’s pride in being nomi- Had I been present, I would have voted in United States, and I believe all involved par- nated as a ‘‘Super Troop’’ for four years, three favor of H. Res. 1472, H. Con. Res. 126, and ties to ensure that the goal is a reunified Cy- of which have been consecutive. The Super H. Res. 1219. prus where Greek Cypriots and Turkish Cyp- Troop honor is bestowed upon the Troop f riots live together in peace and security. A which exemplifies the best in Scout Spirit, successful settlement effort must build on the RECOGNIZING THE 36TH ANNIVER- competitive edge, good attitude and dem- work towards a bizonal, bicommunal federa- SARY OF TURKEY’S ILLEGAL IN- onstrates a positive example to others. tion with political equality that represents U.N. VASION OF CYPRUS Madam Speaker, the young men of Boy Security Council resolutions. In the end, Cy- Scout Troop 463 have shown dedication to prus must have a single sovereignty and sin- their peers, their community, and their cause. HON. FRANK PALLONE, JR. gle citizenship which all Cypriots can enjoy. The Troop’s accomplishments reflect the best OF NEW JERSEY Now is the time for Turkey to show that they values of Scouting and should not go unno- IN THE HOUSE OF REPRESENTATIVES are willing to take a sincere approach to allow- ticed. Tuesday, July 20, 2010 ing a peaceful resolution to the dispute. The f Mr. PALLONE. Madam Speaker, tonight I leadership in Ankara must show that the will join my colleagues on the House floor to re- and support behind a peaceful settlement is in TRIBUTE TO LIEUTENANT the best interest of Turkey and that it is fully GENERAL R. -

What Kind of Future for the Port of Beirut?
What kind of future for the Port of Beirut? by Leila J. Sawaya Bachelor of Engineering, Civil and Environmental Engineering, American University of Beirut, 2000 Submitted to the Department of Civil and Environmental Engineering in Partial Fulfillment of the Requirements for the Degree of Master of Science in Civil and Environmental Engineering at the Massachusetts Institute of Technology September 2002 @ Massachusetts Institute of Technology 2002. All rights reserved. Signature of Author- Department of CiUji and Environmental Engineering August 16, 2002 Certified by: Professor Fred Moavenzadeh Departmen of Civil and Environmental Engineering / Thesis Co-Supervisor Accepted by_ K Oral Buyukozturk Chairman, Departmental Committee on Graduate Studies What kind of future for the Port of Beirut? by Leila J. Sawaya Submitted to the Department of Civil and Environmental Engineering on August 23, 2002, in partial fulfillment of the requirements for the degree of Master of Science in Civil and Environmental Engineering ABSTRACT The purpose of my thesis is to try to determine whether the port of Beirut can take advantage of his geographical position and redefine its role as either a transshipment hub or a transit gateway. It is obvious that in the present there are various new players that were able to take advantage of their location and of the technological changes to improve the performance of their ports while Lebanon was still trying to recover from its destroying war. The advance in technologies and the move to containerized traffic have rendered old port structures completely obsolete in favor of new ports that were able to cater for the new needs of this century.