Flex Edition 2.6.0, 10 November 2015
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lexical Analysis with Flex Edition 2.5.35, 8 February 2013
Lexical Analysis with Flex Edition 2.5.35, 8 February 2013 Vern Paxson, Will Estes and John Millaway The flex manual is placed under the same licensing conditions as the rest of flex: Copyright c 2001, 2002, 2003, 2004, 2005, 2006, 2007, 2012 The Flex Project. Copyright c 1990, 1997 The Regents of the University of California. All rights reserved. This code is derived from software contributed to Berkeley by Vern Paxson. The United States Government has rights in this work pursuant to contract no. DE- AC03-76SF00098 between the United States Department of Energy and the University of California. Redistribution and use in source and binary forms, with or without modification, are per- mitted provided that the following conditions are met: 1. Redistributions of source code must retain the above copyright notice, this list of con- ditions and the following disclaimer. 2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution. Neither the name of the University nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission. THIS SOFTWARE IS PROVIDED “AS IS” AND WITHOUT ANY EXPRESS OR IM- PLIED WARRANTIES, INCLUDING, WITHOUT LIMITATION, THE IMPLIED WAR- RANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. i Table of Contents 1 Copyright ................................. 1 2 Reporting Bugs............................ 2 3 Introduction ............................... 3 4 Some Simple Examples..................... 4 5 Format of the Input File ................... 6 5.1 Format of the Definitions Section ............................ -

CALI Round 03.Pdf
California Academic Learning Initiative 2015 - 2016 Round 3 Written by Ankit Aggarwal, Hidehiro Anto, P.C. Chauhan, Jason Cheng, Boyang Jiao, Aseem Keyal, Eddie Kim, Bruce Lou, Charlie Mann, Kevin Wang, Corry Wang, Kion You TOSSUPS 1. T he Supreme Court has decided that tailored use of this practice is permissible for achieving so-called "critical mass," although Sandra Day O'Connor wrote that this practice would no longer be necessary in 25 years. In 2003 the Supreme Court ruled against a point-based version of this practice in G ratz v. Bollinger. In June 2015 the court agreed to rehear the case (*) Fisher v. Texas challenging this practice. In 1978 quota-based versions of this practice were ruled unconstitutional in B akke v. Regents of the University of California . For 10 points, name this practice of giving preference to historically disadvantaged racial minorities. ANSWER: affirmative action in the college admissions process [accept positive discrimination; prompt on "reverse discrimination" or "discrimination"] 2. A leader criticized this religion's contradictions in his essay Against the Galileans during the 4th century. According to legend, one of this religion's major holidays was specifically scheduled to upstage a festival led by the Sol Invictus cult. Julian the Apostate attempted to roll back the spread of this religion, whose members were systematically persecuted by (*) D iocletian ( "DIE"-oh-klee-shun). It was granted toleration in the Edict of Milan by Constantine the Great, who became the first Roman emperor to convert to it. For 10 points, Pontius Pilate crucified the founder of what religion? ANSWER: Christianity [accept specific forms of Christianity] 3. -

C Programming and Data Structures May/June 2007
C Programming and Data Structures May/June 2007 SET-2 1. (a) What is a string constant? How do string constants differ from character constants? Do string constants represent numerical values? A string constant is a sequence of characters enclosed in double quotes. The characters may be letters, numbers, special characters and blank spaces. Example: hai , 1982, etc; A character constant is not equivalent to the single character constant. A single character string constant does not have an equivalent integer whereas a character constant has an integer value (ASCII value). String constants do not represent equivalent numerical values. (b) Summarize the standard escape sequences in C. Describe them. Black slash characters are also called escape sequences. Constant Meaning \a Audible alert(bell) \b Back space \f Form feed \n New line \r Carriage return \t Tab space \v Vertical tab \ Single quote \ Double quote \? Question mark \\ Back slash \0 Null (c) What is a variable? How can variables be characterized? Give the rules for variable declaration. A variable is a data name that may be used to store a data value. A variable may take different values at different times during execution. Variables are characterized based on the value they hold. Depending on that they are classified into int, float, char, double, and so on. Rules for variable declaration: · They must begin with a letter. Some compilers permit underscore as the first character. · ANSI standard recognizes a length of 31 characters. However, the length should not be normally more than eight characters. Appendix-C.p65 12 7/29/08, 5:21 PM Solved Question Papers C.13 · Uppercase and lowercase are significant. -

Introduction to Programming with C-19CSE23 Module 1
Introduction to programming with C-19CSE23 Module 1 Hardware Components Processor, memoryand Input/Output devices, are the important components of adigital computer. Processor will have ALU (Arithmetic Logic Unit) and Control Unit(CU) as its components. Memory can be subdivided into primary and secondary memory. Input devices accept data and control signals from the user. Examples of input devices are keyboard, mouse, pen based systems, data scanners, game controllers, voice recognition systems etc. Output devices communicate the processed data to the user. Examples of output devices are Monitor, Printer, Plotter, sound system etc. Processor Central Processing Unit (CPU) -It is the brain of the computer. It performs the bulk ofthe data processing operations. The function of the processor is to fetch the instructionfrom memory, examine (decode) the instruction and execute the instructions. It consists of Control unit, Arithmetic Logic Unit (ALU) and registers. Control unit is responsible for fetching the instructions from memory and interpreting them. ALU performs arithmetic and logical operations. Registers are very high speed memory unitsfor storing very small amount of data. Program counter, Instruction register, Memoryaddress register, memory buffer register and accumulator are some examples of registers.Bus is a collection of wires. They may be unidirectional or bidirectional. Bus is usedto connect different parts of a computer. Bus may be serial or parallel. USB is anexample of a serial bus. Bus connecting computer and a dot matrix printer is normallya parallel bus. Parallel bus carries several bits at a time. These bits may indicateinstruction, data, address or commands. Bus width and Bus speed are the two major components for performance measure of a computer. -

How To: Use Basic C++, Syntax and Operators A
June 7, 1999 10:10 owltex Sheet number 22 Page number 705 magenta black How to: Use Basic C++, Syntax and Operators A In this How to we summarize the basic syntax of C++ and the rules and operators that are used in C++ expressions. This is a brief language reference for C++ as used in this book, not the entire language. We don’t cover the use of dynamic memory in this How to. A.1 Syntax A.1.1 The Function main C++ programs begin execution with a function main. The smallest C++ program is shown below. It doesn’t do anything, but it’s syntactically legal C++. int main() { return 0; } The return value is passed back to the “system,” a nonzero value indicates some kind of failure. Although not used in this book, the function main can have parameters, these are so-called command-line parameters, passed to the program when the function is run. A brief synopsis of command-line parameters is given in Section A.2.6. A.1.2 Built-in and OtherTypes The built-in types in C++ used in this book are int, double, bool, and char.A type void is used as a built-in “empty-type,” but we don’t treat void as an explicit type. A function declared as void does not return a value of type void, but returns no value. In addition to double, the type float can be used to represent floating point values; but float is less precise and we do not use it. -

Rsyslog Doc Documentation Release 8.26.0
Rsyslog Doc Documentation Release 8.26.0 foo bar Aug 24, 2017 Contents 1 Manual 3 2 Reference 301 3 Sponsors and Community 343 4 Related Links 345 i ii Rsyslog Doc Documentation, Release 8.26.0 Rsyslog is a rocket-fast system for log processing. It offers high-performance, great security features and a modular design. While it started as a regular syslogd, rsyslog has evolved into a kind of swiss army knife of logging, being able to • accept inputs from a wide variety of sources, • transform them, • and output the results to diverse destinations. Rsyslog has a strong enterprise focus but also scales down to small systems. It supports, among others, MySQL, Post- greSQL, failover log destinations, ElasticSearch, syslog/tcp transport, fine grain output format control, high precision timestamps, queued operations and the ability to filter on any message part. Contents 1 Rsyslog Doc Documentation, Release 8.26.0 2 Contents CHAPTER 1 Manual Configuration Rsyslogd is configured via the rsyslog.conf file, typically found in /etc. By default, rsyslogd reads the file /etc/ rsyslog.conf. This can be changed by a command line option. Note that configurations can be built interactively via the online rsyslog configuration builder tool. Basic Structure This section describes how rsyslog configuration basically works. Think of rsyslog as a big logging and event pro- cessing toolset. It can be considered a framework with some basic processing that is fixed in the way data flows, but is highly customizable in the details of this message flow. During configuration, this customization is done by defining and customizing the rsyslog objects. -
Digraphs and Trigraphs
Digraphs and trigraphs In computer programming, digraphs and trigraphs are sequences of two and three characters, respectively, that appear in source code and, according to a programming language's specification, should be treated as if they were single characters. Various reasons exist for using digraphs and trigraphs: keyboards may not have keys to cover the entire character set of the language, input of special characters may be difficult, text editors may reserve some characters for special use and so on. Trigraphs might also be used for some EBCDIC code pages that lack characters such as { and }. Contents History Implementations Language support ALGOL Pascal J C C++ RPL Application support Vim GNU Screen Lotus See also References External links History The basic character set of the C programming language is a subset of the ASCII character set that includes nine characters which lie outside the ISO 646 invariant character set. The ANSI C committee invented trigraphs as a way of entering source code using keyboards that support any version of the ISO 646 character set. Implementations Trigraphs are not commonly encountered outside compiler test suites.[1] Some compilers support an option to turn recognition of trigraphs off, or disable trigraphs by default and require an option to turn them on. Some can issue warnings when they encounter trigraphs in source files. Borland supplied a separate program, the trigraph preprocessor (TRIGRAPH.EXE), to be used only when trigraph processing is desired (the rationale was to maximise speed of compilation). Language support Different systems define different sets of digraphs and trigraphs, as described below. -

Mmt-001 Programming and Data Structures
Indira Gandhi National Open University MMT-001 School of Sciences PROGRAMMING AND DATA STRUCTURES 1Block INTRODUCTION TO THE C PROGRAMMING LANGUAGE UNIT 1 Getting Started 7 UNIT 2 Data Types in C 21 UNIT 3 Operators and Expressions in C 49 UNIT 4 Decision Structures in C 75 UNIT 5 Control Structures-I 101 Curriculum Design Committee Dr. B.D. Acharya Prof. O.P. Gupta Prof. C. Musili Dept. of Science & Technology Dept. of Financial Studies Dept. of Mathematics and Statistics New Delhi University of Delhi University of Hyderabad Prof. Adimurthi Prof. S.D. Joshi Prof. Sankar Pal School of Mathematics Dept. of Electrical Engineering ISI, Kolkata TIFR, Bangalore IIT, Delhi Prof. A.P. Singh Prof. Archana Aggarwal Dr. R. K. Khanna PG Dept. of Mathematics CESP, School of Social Sciences Scientific Analysis Group University of Jammu JNU, New Delhi DRDO, Delhi Faculty Members Prof. R. B. Bapat Prof. Susheel Kumar School of Sciences, IGNOU Indian Statistical Institute, New Delhi Dept. of Management Studies Dr. Deepika Prof. M.C. Bhandari IIT, Delhi Prof. Poornima Mital Dept. of Mathematics Prof. Veni Madhavan Dr. Atul Razdan IIT, Kanpur Scientific Analysis Group Prof. Parvin Sinclair Prof. Sujatha Varma Prof. R. Bhatia DRDO, Delhi Dr. S. Venkataraman Indian Statistical Institute, New Delhi Prof. J.C. Mishra Prof. A. D. Dharmadhikari Dept. of Mathematics Dept. of Statistics IIT, Kharagpur University of Pune Course Design Committee Prof. C.A. Murthy Faculty Members ISI, Kolkata School of Sciences, IGNOU Prof. S.B. Pal Dr. Deepika IIT, Kharagpur Prof. Poornima Mital Dr. Atul Razdan Dr. B.S. Panda Prof. -
Block Introduction
UNIT 1: Introductory Structure 1.0 Introduction 1.1 Objectives 1.2 An Overview 1.3 A C Program 1.4 Escape Sequences 1.5 Getting a "feel" for C 1.6 Summary 1.0 INTRODUCTION This Unit presents the basic features common to all C programs. Quite inevitably, use is made of operators and functions that are discussed at greater length in subsequent Units: for example, operator priorities and associativities, expressions, pointers and input/output form the subject of the following Unit; but they are implicitly used in the present Unit. You will find that it is possible, in fact easy, to write simple programs that make use of the many facilities that C provides, the more intricate features of which you may not perhaps fully comprehend right away. This shouldn't worry you. That knowledge will come with further reading, and practice. We would like you to create and execute the programs listed anyway, and experiment with different values for program variables. Try to see why you get the results that you do, and before you know it you'll have mastered the language! 1.1 OBJECTIVES After working through this Unit you should be able to -declare, define and compute the values of program variables via simple arithmetic operation -create and execute simple C programs -recognise examples of C strings, escape sequences, and program comments -use the simplest functions for input and output. 1.2 AN OVERVIEW C is a general purpose computer programming language. It was originally created by Dennis M. Ritchie (circa 1971) for the specific purpose of rewriting much of the Unix operating system. -
Portable Paper
Vol. 4, No. 6 The HP Portable/Portable Plus/Portable Vectra Users Newsletter November / December 1989 (; ~) PortableTHE Paper Publisher's Message .................. 3 Always Select Backlight Powerdown . .. 14 Letters Generate a Bullet ..................... 14 The Mac Portable And The HP Portables ....... 4 More LS/12 and Vectra Products On The Horizon 15 More On "tjctrl" . .. 4 News From Personalized Software The Editor Makes PAM and Time Manager easier .. 4 What we're working on . .. 15 Short note of appreciation . .. 4 Upgrade 256K Portable Plus into a 512K Plus. .. 16 Getting The 110 and a PC to Read the Same Disks 4 1 Meg RAMjROM and 2 Meg RAM Drawers Need Scientific Word Processor ............. 5 Shipping Again For Portable Plus ........... 16 A few useful hints... ..................... 5 VI Editor For HP An IBM-Compatible Computers 16 Likes Empowerer ....................... 5 World's Smallest MNP Modem ............. 17 Using Squish Plus With The Plus And Vectra Together 5 Subscribers Disks Only Available With Subscription 17 Squish Plus Extends Life Of Portable Plus . .. 5 1986-1989 Index Soon Available ............ 17 Suggestions To Improve Time Manager ........ 5 First Issue Of The UltraLite Connection Ships . .. 17 Likes MS-Word over WordPerfect ............ 39 Profiles 110% Portable Computing With The Plus ......... 22 LS/12 Still On HP Price List ... But not for Long .. 6 Frustrations - And Resolutions . .. 24 The 1990 Subscribers Disk . .. 6 The Savvy User Attention HP3000 Users: MPE On HP Portables! .. 6 Time Manager Solution . .. 27 Infocom Games ........................ 6 Using 1JCTRL With Memomaker . .. 28 What is ASCII.... .. .. .. .. .. .. .. .. .. ... 8 PAM Menu Overflows ................... 30 HPIL Switch Box ....................... 9 Webster's Pop Up Spelling Checker. -
Sample C++ Programs
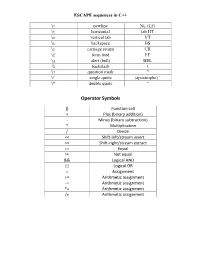
ESCAPE sequences in C++ \n newline NL (LF) \t horizontal tab HT \v vertical tab VT \b backspace BS \r carriage return CR \f form feed FF \a alert (bell) BEL \\ backslash \ \? question mark ? \’ single quote (apostrophe) ’ \" double quote " Operator Symbols () Function call + Plus (binary addition) - Minus (binary subtraction) * Multiplication / Divide << Shift-left/stream insert >> Shift-right/stream extract == Equal != Not equal && Logical AND || Logical OR = Assignment += Arithmetic assignment -= Arithmetic assignment *= Arithmetic assignment /= Arithmetic assignment Program 1 // A simple C++ program #include <iostream> using namespace std; int main() { cout << "Programming is great fun!"; return 0; } Program 2 // A simple C++ program #include <iostream> using namespace std; int main() { cout << "Programming is " << "great fun!"; return 0; } Program 3 // A simple C++ program #include <iostream> using namespace std; int main() { cout << "Programming is "; cout << "great fun!"; return 0; } Program 4 // This program has a variable. #include <iostream> using namespace std; int main() { int number; number = 5; cout << "The value in number is " << number << endl; return 0; } Program 5 // This program shows three variables defined on the same line. #include <iostream> using namespace std; int main() { int floors, rooms, suites; floors = 15; rooms = 300; suites = 30; cout << "The Grande Hotel has " << floors << " floors\n"; cout << "with " << rooms << " rooms and " << suites; cout << " suites.\n"; return 0; } If Statement #include <iomanip> using namespace std; int main() { int score1, score2, score3; // To hold three test scores double average; // TO hold the average score // Get the three test scores. cout << "Enter 3 test scores and I will average them: "; cin >> score1 >> score2 >> score3; // Calculate and display the average score. -

Pdf External()
The CImg Library 2.9.9 Generated by Doxygen 1.8.17 i 1 Main Page 1 2 CImg Library Overview 3 2.1 Library structure............................................. 3 2.2 CImg version of "Hello world"....................................... 4 2.3 How to compile ? ............................................ 4 2.4 What's next ? .............................................. 5 3 FAQ 7 3.1 FAQ Summary.............................................. 7 3.2 1. General information and availability ................................. 7 3.2.1 1.1. What is the CImg Library ?................................. 7 3.2.2 1.2. What platforms are supported ? .............................. 8 3.2.3 1.3. How is CImg distributed ? ................................. 8 3.2.4 1.4. What kind of people are concerned by CImg ?....................... 8 3.2.5 1.5. What are the specificities of the CeCILL license ?..................... 8 3.2.6 1.6. Who is behind CImg ? ................................... 9 3.3 2. C++ related questions ........................................ 9 3.3.1 2.1 What is the level of C++ knowledge needed to use CImg ?................. 9 3.3.2 2.2 How to use CImg in my own C++ program ?........................ 9 3.3.3 2.3 Why is CImg entirely contained in a single header file ? .................. 9 3.4 3. Other resources ........................................... 10 3.4.1 3.1 Translations......................................... 10 4 Setting Environment Variables 11 5 How to use CImg library with Visual C++ 2005 Express Edition ? 13 5.1 How to use CImg library with Visual C++ 2005 Express Edition ? ................... 13 6 Tutorial : Getting Started. 15 7 Image Loops. 17 7.1 Loops over the pixel buffer........................................ 17 7.2 Loops over image dimensions...................................... 18 7.3 Loops over interior regions and borders.