MODULE 1: Introduction to C Language
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
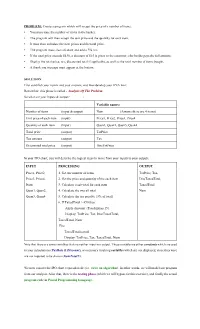
Create a Program Which Will Accept the Price of a Number of Items. • You Must State the Number of Items in the Basket
PROBLEM: Create a program which will accept the price of a number of items. • You must state the number of items in the basket. • The program will then accept the unit price and the quantity for each item. • It must then calculate the item prices and the total price. • The program must also calculate and add a 5% tax. • If the total price exceeds $450, a discount of $15 is given to the customer; else he/she pays the full amount. • Display the total price, tax, discounted total if applicable, as well as the total number of items bought. • A thank you message must appear at the bottom. SOLUTION First establish your inputs and your outputs, and then develop your IPO chart. Remember: this phase is called - Analysis Of The Problem. So what are your inputs & output? : Variable names: Number of items (input & output) Num (Assume there are 4 items) Unit price of each item (input) Price1, Price2, Price3, Price4 Quantity of each item (Input) Quan1, Quan2, Quan3, Quan4 Total price (output) TotPrice Tax amount (output) Tax Discounted total price (output) DiscTotPrice In your IPO chart, you will describe the logical steps to move from your inputs to your outputs. INPUT PROCESSING OUTPUT Price1, Price2, 1. Get the number of items TotPrice, Tax, Price3, Price4, 2. Get the price and quantity of the each item DiscTaxedTotal, Num 3. Calculate a sub-total for each item TaxedTotal Quan1, Quan2, 4. Calculate the overall total Num Quan3, Quan4 5. Calculate the tax payable {5% of total} 6. If TaxedTotal > 450 then Apply discount {Total minus 15} Display: TotPrice, Tax, DiscTaxedTotal, TaxedTotal, Num Else TaxedTotal is paid Display: TotPrice, Tax, TaxedTotal, Num Note that there are some variables that are neither input nor output. -

Lexical Analysis with Flex Edition 2.5.35, 8 February 2013
Lexical Analysis with Flex Edition 2.5.35, 8 February 2013 Vern Paxson, Will Estes and John Millaway The flex manual is placed under the same licensing conditions as the rest of flex: Copyright c 2001, 2002, 2003, 2004, 2005, 2006, 2007, 2012 The Flex Project. Copyright c 1990, 1997 The Regents of the University of California. All rights reserved. This code is derived from software contributed to Berkeley by Vern Paxson. The United States Government has rights in this work pursuant to contract no. DE- AC03-76SF00098 between the United States Department of Energy and the University of California. Redistribution and use in source and binary forms, with or without modification, are per- mitted provided that the following conditions are met: 1. Redistributions of source code must retain the above copyright notice, this list of con- ditions and the following disclaimer. 2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution. Neither the name of the University nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission. THIS SOFTWARE IS PROVIDED “AS IS” AND WITHOUT ANY EXPRESS OR IM- PLIED WARRANTIES, INCLUDING, WITHOUT LIMITATION, THE IMPLIED WAR- RANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. i Table of Contents 1 Copyright ................................. 1 2 Reporting Bugs............................ 2 3 Introduction ............................... 3 4 Some Simple Examples..................... 4 5 Format of the Input File ................... 6 5.1 Format of the Definitions Section ............................ -

Constructing Algorithms and Pseudocoding This Document Was Originally Developed by Professor John P
Constructing Algorithms and Pseudocoding This document was originally developed by Professor John P. Russo Purpose: # Describe the method for constructing algorithms. # Describe an informal language for writing PSEUDOCODE. # Provide you with sample algorithms. Constructing Algorithms 1) Understand the problem A common mistake is to start writing an algorithm before the problem to be solved is fully understood. Among other things, understanding the problem involves knowing the answers to the following questions. a) What is the input list, i.e. what information will be required by the algorithm? b) What is the desired output or result? c) What are the initial conditions? 2) Devise a Plan The first step in devising a plan is to solve the problem yourself. Arm yourself with paper and pencil and try to determine precisely what steps are used when you solve the problem "by hand". Force yourself to perform the task slowly and methodically -- think about <<what>> you are doing. Do not use your own memory -- introduce variables when you need to remember information used by the algorithm. Using the information gleaned from solving the problem by hand, devise an explicit step-by-step method of solving the problem. These steps can be written down in an informal outline form -- it is not necessary at this point to use pseudo-code. 3) Refine the Plan and Translate into Pseudo-Code The plan devised in step 2) needs to be translated into pseudo-code. This refinement may be trivial or it may take several "passes". 4) Test the Design Using appropriate test data, test the algorithm by going through it step by step. -

CALI Round 03.Pdf
California Academic Learning Initiative 2015 - 2016 Round 3 Written by Ankit Aggarwal, Hidehiro Anto, P.C. Chauhan, Jason Cheng, Boyang Jiao, Aseem Keyal, Eddie Kim, Bruce Lou, Charlie Mann, Kevin Wang, Corry Wang, Kion You TOSSUPS 1. T he Supreme Court has decided that tailored use of this practice is permissible for achieving so-called "critical mass," although Sandra Day O'Connor wrote that this practice would no longer be necessary in 25 years. In 2003 the Supreme Court ruled against a point-based version of this practice in G ratz v. Bollinger. In June 2015 the court agreed to rehear the case (*) Fisher v. Texas challenging this practice. In 1978 quota-based versions of this practice were ruled unconstitutional in B akke v. Regents of the University of California . For 10 points, name this practice of giving preference to historically disadvantaged racial minorities. ANSWER: affirmative action in the college admissions process [accept positive discrimination; prompt on "reverse discrimination" or "discrimination"] 2. A leader criticized this religion's contradictions in his essay Against the Galileans during the 4th century. According to legend, one of this religion's major holidays was specifically scheduled to upstage a festival led by the Sol Invictus cult. Julian the Apostate attempted to roll back the spread of this religion, whose members were systematically persecuted by (*) D iocletian ( "DIE"-oh-klee-shun). It was granted toleration in the Edict of Milan by Constantine the Great, who became the first Roman emperor to convert to it. For 10 points, Pontius Pilate crucified the founder of what religion? ANSWER: Christianity [accept specific forms of Christianity] 3. -

Introduction to Computer Science CSCI 109
Introduction to Computer Science CSCI 109 China – Tianhe-2 Readings Andrew Goodney Fall 2019 St. Amant, Ch. 5 Lecture 7: Compilers and Programming 10/14, 2019 Reminders u Quiz 3 today – at the end u Midterm 10/28 u HW #2 due tomorrow u HW #3 not out until next week 1 Where are we? 2 Side Note u Two things funny/note worthy about this cartoon u #1 is COBOL (we’ll talk about that later) u #2 is ?? 3 “Y2k Bug” u Y2K bug?? u In the 1970’s-1980’s how to store a date? u Use MM/DD/YY v More efficient – every byte counts (especially then) u What is/was the issue? u What was the assumption here? v “No way my COBOL program will still be in use 25+ years from now” u Wrong! 4 Agenda u What is a program u Brief History of High-Level Languages u Very Brief Introduction to Compilers u ”Robot Example” u Quiz 6 What is a Program? u A set of instructions expressed in a language the computer can understand (and therefore execute) u Algorithm: abstract (usually expressed ‘loosely’ e.g., in english or a kind of programming pidgin) u Program: concrete (expressed in a computer language with precise syntax) v Why does it need to be precise? 8 Programming in Machine Language is Hard u CPU performs fetch-decode-execute cycle millions of time a second u Each time, one instruction is fetched, decoded and executed u Each instruction is very simple (e.g., move item from memory to register, add contents of two registers, etc.) u To write a sophisticated program as a sequence of these simple instructions is very difficult (impossible) for humans 9 Machine Language Example -

Novice Programmer = (Sourcecode) (Pseudocode) Algorithm
Journal of Computer Science Original Research Paper Novice Programmer = (Sourcecode) (Pseudocode) Algorithm 1Budi Yulianto, 2Harjanto Prabowo, 3Raymond Kosala and 4Manik Hapsara 1Computer Science Department, School of Computer Science, Bina Nusantara University, Jakarta, Indonesia 11480 2Management Department, BINUS Business School Undergraduate Program, Bina Nusantara University, Jakarta, Indonesia 11480 3Computer Science Department, Faculty of Computing and Media, Bina Nusantara University, Jakarta, Indonesia 11480 4Computer Science Department, BINUS Graduate Program - Doctor of Computer Science, Bina Nusantara University, Jakarta, Indonesia 11480 Article history Abstract: Difficulties in learning programming often hinder new students Received: 7-11-2017 as novice programmers. One of the difficulties is to transform algorithm in Revised: 14-01-2018 mind into syntactical solution (sourcecode). This study proposes an Accepted: 9-04-2018 application to help students in transform their algorithm (logic) into sourcecode. The proposed application can be used to write down students’ Corresponding Author: Budi Yulianto algorithm (logic) as block of pseudocode and then transform it into selected Computer Science Department, programming language sourcecode. Students can learn and modify the School of Computer Science, sourcecode and then try to execute it (learning by doing). Proposed Bina Nusantara University, application can improve 17% score and 14% passing rate of novice Jakarta, Indonesia 11480 programmers (new students) in learning programming. Email: [email protected] Keywords: Algorithm, Pseudocode, Novice Programmer, Programming Language Introduction students in some universities that are new to programming and have not mastered it. In addition, Programming language is a language used by some universities (especially in rural areas or with programmers to write commands (syntax and semantics) limited budget) do not have tools that can help their new that can be understood by a computer to create a students in learning programming (Yulianto et al ., 2016b). -

Does Surprisal Predict Code Comprehension Difficulty?
Does Surprisal Predict Code Comprehension Difficulty? Casey Casalnuovo ([email protected]), Prem Devanbu ([email protected]) Department of Computer Science, University of California, Davis One Shields Avenue, Davis, CA 95616 USA Emily Morgan ([email protected]) Department of Linguistics, University of California, Davis One Shields Avenue, Davis, CA 95616 USA Abstract Appreciation of the similarities and differences between natural and programming languages has led to the adoption Recognition of the similarities between programming and nat- ural languages has led to a boom in the adoption of language of computational language models for code. Language mod- modeling techniques in tools that assist developers. However, els operate by learning probability distributions over text, and language model surprisal, which guides the training and eval- key to training these models is the notion of surprisal. The uation in many of these methods, has not been validated as surprisal of a token is its negative log probability in context as a measure of cognitive difficulty for programming language 1 comprehension as it has for natural language. We perform a captured by the language model . Programming language is controlled experiment to evaluate human comprehension on more repetitive and has lower surprisal than natural language, fragments of source code that are meaning-equivalent but with different surprisal. We find that more surprising versions of i.e. language models find code more predictable than natural code take humans longer to finish answering correctly. We language (Hindle et al., 2012). Moreover, this finding holds also provide practical guidelines to design future studies for across many natural and programming languages, and some code comprehension and surprisal. -

C Programming and Data Structures May/June 2007
C Programming and Data Structures May/June 2007 SET-2 1. (a) What is a string constant? How do string constants differ from character constants? Do string constants represent numerical values? A string constant is a sequence of characters enclosed in double quotes. The characters may be letters, numbers, special characters and blank spaces. Example: hai , 1982, etc; A character constant is not equivalent to the single character constant. A single character string constant does not have an equivalent integer whereas a character constant has an integer value (ASCII value). String constants do not represent equivalent numerical values. (b) Summarize the standard escape sequences in C. Describe them. Black slash characters are also called escape sequences. Constant Meaning \a Audible alert(bell) \b Back space \f Form feed \n New line \r Carriage return \t Tab space \v Vertical tab \ Single quote \ Double quote \? Question mark \\ Back slash \0 Null (c) What is a variable? How can variables be characterized? Give the rules for variable declaration. A variable is a data name that may be used to store a data value. A variable may take different values at different times during execution. Variables are characterized based on the value they hold. Depending on that they are classified into int, float, char, double, and so on. Rules for variable declaration: · They must begin with a letter. Some compilers permit underscore as the first character. · ANSI standard recognizes a length of 31 characters. However, the length should not be normally more than eight characters. Appendix-C.p65 12 7/29/08, 5:21 PM Solved Question Papers C.13 · Uppercase and lowercase are significant. -

Concepts of Programming Languages, Eleventh Edition, Global Edition
GLOBAL EDITION Concepts of Programming Languages ELEVENTH EDITION Robert W. Sebesta digital resources for students Your new textbook provides 12-month access to digital resources that may include VideoNotes (step-by-step video tutorials on programming concepts), source code, web chapters, quizzes, and more. Refer to the preface in the textbook for a detailed list of resources. Follow the instructions below to register for the Companion Website for Robert Sebesta’s Concepts of Programming Languages, Eleventh Edition, Global Edition. 1. Go to www.pearsonglobaleditions.com/Sebesta 2. Click Companion Website 3. Click Register and follow the on-screen instructions to create a login name and password Use a coin to scratch off the coating and reveal your access code. Do not use a sharp knife or other sharp object as it may damage the code. Use the login name and password you created during registration to start using the digital resources that accompany your textbook. IMPORTANT: This access code can only be used once. This subscription is valid for 12 months upon activation and is not transferable. If the access code has already been revealed it may no longer be valid. For technical support go to http://247pearsoned.custhelp.com This page intentionally left blank CONCEPTS OF PROGRAMMING LANGUAGES ELEVENTH EDITION GLOBAL EDITION This page intentionally left blank CONCEPTS OF PROGRAMMING LANGUAGES ELEVENTH EDITION GLOBAL EDITION ROBERT W. SEBESTA University of Colorado at Colorado Springs Global Edition contributions by Soumen Mukherjee RCC Institute -

Pseudocode Pseudocode Guide for Pseudocode
Computers in Engineering Pseudocode Pseudocode and C Language z Pseudocode is an artificial and informal language Review that helps you develop algorithms. z Pseudocode is similar to everyday English; it is convenient and user friendly although it is not an actual computer programming language. z Pseudocode programs are not executed on computers. Rather, they merely help you "think out" a program before attempting to write it in a programming language such as C. z Pseudocode consists purely of characters, so you may conveniently type pseudocode programs into a computer using an editor program. Pseudocode Guide for Pseudocode 1. State your name z Carefully prepared pseudocode programs may be 2. State the date converted easily to corresponding C programs. 3. State the name of the subroutine. 4. Give a brief description of the function of the subroutine/program. z Pseudocode consists only of action statements- 5. State the names of the input variables, their types, and give a brief those that are executed when the program has been description for each. 6. Stat e th e names of th e ou tpu t var ia bles, the ir types, an d g ive a br ie f converted from pseudocode to C and is run in C. description for each. Definitions are not executable statements. They are 7. Give a list of instructions with enough detail that someone can translate the pseudocode into a computer language such as C, C++, Java, etc. messages to the compiler. Note, your pseudocode should paraphrase your algorithm and not look identical to C code. z Each variable should be listed and the purpose of 8. -

Array Oriented Functional Programming in APL
1 Array Oriented Functional Programming in APL Morten Kromberg CTO, Dyalog Ltd. ACM Poughkeepsie, Marist College, September 17th, 2019 Array Oriented Functional Programming in APL 2 Array Oriented Functional Programming in APL 3 Paradigms Introduction to • Object Orientation A Programming Language ‐ Modeling of queues / events Kenneth E. Iverson (1962) ‐ Simula (1962) ‐ Smalltalk (1980) Applied mathematics is largely ‐ Java (1991), C# (2000) concerned with the design and • analysis of explicit procedures for Functional Programming calculating the exact or approximate ‐ Lambda Calculus (1936) values of various functions. ‐ Lisp (1960) ‐ Haskell (1992) Such explicit procedures are called • Array Oriented Programming algorithms or programs. ‐ Applied Mathematics (1950's) ‐ IBM APL\360 (1966) Because an effective notation for the ‐ Dyalog APL (1983) description of programs exhibits considerable syntactic structure, it is ‐ J (1990), k (1993) called a programming language. Array Oriented Functional Programming in APL 4 A Programming Language Array Oriented Functional Programming in APL 5 Problems: - Wide variety of syntactical forms - Strange and inconsistent precedence rules - Things get worse when you deal with matrices See http://www.jsoftware.com/papers/EvalOrder.htm Array Oriented Functional Programming in APL 6 A Programming Language a×b Mat1 +.× Mat2 *x f g x x÷y (3○x)*2 b⍟a +/4×⍳6 a*÷n ×/4×⍳6 Array Oriented Functional Programming in APL 7 Symbols Primitive APL functions are denoted by [Unicode] symbols • We learn and use new symbols all the time • Symbols help us to communicate more concisely • Suppose:) I asked you to simultaneously play three notes with frequencies of 130.81, 155.56, and 196 Hertz.. -

Pseudocode, Flowcharts & Programming
Computer Science 2210 2.1.1, 2.11 .2 - Pseudocode, Flowcharts & Programming with Majid Tahir Algorithms: An algorithm is a sequence of steps done to perform some task. The essential aim of an algorithm is to get a specific output, An algorithm involves with several continuous steps, The output comes after the algorithm finished the whole process. So basically, all algorithms perform logically while following the steps to get an output for a given input. Types of Algorithms: Structured English Flowcharts Pseudo codes Program Code STRUCTURED ENGLISH: Structured English provides a more formal way of documenting the stages of the algorithm. Structured English is a subset of English language that consists of command statements used to describe an algorithm. FLOWCHARTS: Flow chart is a graphical representation of a program. Flowcharts use different symbols containing information about steps or a sequence of events. Flowchart Symbols: START/ STOP INPUT/ OUTPUT PROCESS PRE DEFINED PROCESS DECISION DATA FLOW LINES IF condition? PSEUDOCODE: Pseudo code is an outline of a program, written as a series of instruction using simple English sentences. Pseudo code uses keywords commonly found in high-level languages and mathematical notation. It 1 Computer Science 2210 2.1.1, 2.11 .2 - Pseudocode, Flowcharts & Programming with Majid Tahir describes an algorithm‟s steps like program statements, without being bound by the strict rules of vocabulary and syntax of any particular language, together with ordinary English. Variable: Variable is memory location where a value can be stored. Constants: Just like variables, constants are "dataholders". They can be used to store data that is needed at runtime.