Pre-Built JOP Chains with the JOP ROCKET: Bypassing DEP Without ROP
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Die Meilensteine Der Computer-, Elek
Das Poster der digitalen Evolution – Die Meilensteine der Computer-, Elektronik- und Telekommunikations-Geschichte bis 1977 1977 1978 1979 1980 1981 1982 1983 1984 1985 1986 1987 1988 1989 1990 1991 1992 1993 1994 1995 1996 1997 1998 1999 2000 2001 2002 2003 2004 2005 2006 2007 2008 2009 2010 2011 2012 2013 2014 2015 2016 2017 2018 2019 2020 und ... Von den Anfängen bis zu den Geburtswehen des PCs PC-Geburt Evolution einer neuen Industrie Business-Start PC-Etablierungsphase Benutzerfreundlichkeit wird gross geschrieben Durchbruch in der Geschäftswelt Das Zeitalter der Fensterdarstellung Online-Zeitalter Internet-Hype Wireless-Zeitalter Web 2.0/Start Cloud Computing Start des Tablet-Zeitalters AI (CC, Deep- und Machine-Learning), Internet der Dinge (IoT) und Augmented Reality (AR) Zukunftsvisionen Phasen aber A. Bowyer Cloud Wichtig Zählhilfsmittel der Frühzeit Logarithmische Rechenhilfsmittel Einzelanfertigungen von Rechenmaschinen Start der EDV Die 2. Computergeneration setzte ab 1955 auf die revolutionäre Transistor-Technik Der PC kommt Jobs mel- All-in-One- NAS-Konzept OLPC-Projekt: Dass Computer und Bausteine immer kleiner, det sich Konzepte Start der entwickelt Computing für die AI- schneller, billiger und energieoptimierter werden, Hardware Hände und Finger sind die ersten Wichtige "PC-Vorläufer" finden wir mit dem werden Massenpro- den ersten Akzeptanz: ist bekannt. Bei diesen Visionen geht es um die Symbole für die Mengendarstel- schon sehr früh bei Lernsystemen. iMac und inter- duktion des Open Source Unterstüt- möglichen zukünftigen Anwendungen, die mit 3D-Drucker zung und lung. Ägyptische Illustration des Beispiele sind: Berkley Enterprice mit neuem essant: XO-1-Laptops: neuen Technologien und Konzepte ermöglicht Veriton RepRap nicht Ersatz werden. -

AMD EPYC™ 7003 Series Cpus Set New Standard As Highest Performance Server Processor
March 15, 2021 AMD EPYC™ 7003 Series CPUs Set New Standard as Highest Performance Server Processor New AMD EPYC processor extends per socket performance leadership and best per core performance1** with new “Zen 3” cores and modern security features Partners including AWS, Cisco, Dell Technologies, Google Cloud, HPE, Lenovo, Microsoft Azure, Oracle Cloud Infrastructure, Supermicro, Tencent Cloud and others grow EPYC processor ecosystem to an expected 400 cloud instances and 100 new OEM platforms by end of 2021 SANTA CLARA, Calif., March 15, 2021 (GLOBE NEWSWIRE) -- At a digital event, AMD (NASDAQ: AMD) announced the new AMD EPYC™ 7003 Series CPUs, which includes the AMD EPYC 7763, the world’s highest-performing server processor2*. The new EPYC 7003 series processors help HPC, cloud and enterprise customers do more, faster, by delivering the best performance of any server CPU with up to 19% more instructions per clock3. “With the launch of our 3rd Gen AMD EPYC processors, we are incredibly excited to deliver the fastest server CPU in the world. These processors extend our data center leadership and help customers solve today’s most complex IT challenges, while substantially growing our ecosystem,” said Forrest Norrod, senior vice president and general manager, Data Center and Embedded Solutions Business Group. “We not only double the performance over the competition in HPC, cloud and enterprise workloads with our newest server CPUs, but together with the AMD Instinct GPUs, we are breaking the exascale barrier in supercomputing and helping to tackle problems that have previously been beyond humanity’s reach.” AMD EPYC Processors, Powering the Modern Data Center Available immediately, AMD EPYC 7003 Series Processors have up to 64 “Zen 3” cores per processor and introduce new levels of per-core cache memory, while continuing to offer the PCIe® 4 connectivity and class-leading memory bandwidth4 that defined the EPYC 7002 series CPUs. -

Amd's Commitment To
This presentation contains forward-looking statements concerning Advanced Micro Devices, Inc. (AMD) such as AMD’s journey; the proposed transaction with Xilinx, Inc. including expectations, benefits and plans of the proposed transaction; total addressable markets; AMD’s technology roadmaps; the features, functionality, performance, availability, timing and expected benefits of future AMD products; AMD’s path forward in data center, PCs and gaming; and AMD’s 2021 financial outlook, long-term financial model and ability to drive shareholder returns, which are made pursuant to the Safe Harbor provisions of the Private Securities Litigation Reform Act of 1995. Forward looking statements are commonly identified by words such as "would," "may," "expects," "believes," "plans," "intends," "projects" and other terms with similar meaning. Investors are cautioned that the forward- looking statements in this presentation are based on current beliefs, assumptions and expectations, speak only as of the date of this presentation and involve risks and uncertainties that could cause actual results to differ materially from current expectations. Such statements are subject to certain known and unknown risks and uncertainties, many of which are difficult to predict and generally beyond AMD's control, that could cause actual results and other future events to differ materially from those expressed in, or implied or projected by, the forward-looking information and statements. Investors are urged to review in detail the risks and uncertainties in AMD’s Securities and Exchange Commission filings, including but not limited to AMD’s most recent reports on Forms 10-K and 10-Q. AMD does not assume, and hereby disclaims, any obligation to update forward-looking statements made in this presentation, except as may be required by law. -

AMD Announces World's Best Mobile Processors¹ in CES 2021 Keynote
January 12, 2021 AMD Announces World’s Best Mobile Processors¹ In CES 2021 Keynote AMD Ryzen Threadripper PRO Processors, designed for the most demanding professional workloads, coming to retail channel SANTA CLARA, Calif., Jan. 12, 2021 (GLOBE NEWSWIRE) -- CES 2021 -- Today, AMD (NASDAQ: AMD) announced the full portfolio of AMD Ryzen™ 5000 Series Mobile Processors, bringing the highly-efficient and extremely powerful “Zen 3” core architecture to the laptop market. New AMD Ryzen 5000 Series Mobile Processors provide unprecedented levels of performance and incredible battery life for gamers, creators, and professionals. New laptops powered by Ryzen 5000 Series Mobile processors will be available from major PC manufacturers including ASUS, HP and Lenovo, starting in Q1 2021. Expanding its leadership client computing product portfolio featuring the “Zen 3” core, AMD also announced the AMD Ryzen PRO 5000 Series Mobile Processors, delivering enterprise- grade security and seamless manageability to commercial users. Throughout the course of 2021, AMD expects a broad portfolio of more than 150 consumer and commercial notebooks based on the Ryzen 5000 Series Mobile Processors. “As the PC becomes an even more essential part of how we work, play and connect, users demand more performance, security and connectivity,” said Saeid Moshkelani, senior vice president and general manager, Client business unit, AMD. “The new AMD Ryzen 5000 Series Desktop and Mobile Processors bring the best innovation AMD has to offer to consumers and professionals as we continue our commitment to delivering best-in-class experiences with instant responsiveness, incredible battery life and fantastic designs. With our PC partners, we are delivering top-quality performance and no-compromise solutions alongside our record-breaking growth in the notebook and desktop space in the previous year.” AMD Ryzen 5000 Series Mobile Processors Building upon the previous generation of leadership mobile processors, the Ryzen 5000 Series includes high-performance H- and ultra-mobile U-Series processors. -

PAP Advanced Computer Architectures 1 ISA Development History
Advanced Computer Architectures History and Future Czech Technical University in Prague, Faculty of Electrical Engineering Slides authors: Michal Štepanovský, update Pavel Píša B4M35PAP Advanced Computer Architectures 1 ISA development history 1936 Alan Turing: On computable numbers, with an application to 1939 Bombe: the Entscheidungsproblem designed to crack 1937: Howard Aiken: Concept of Enigma Automatic Sequence Controlled 1941 Konrad Zuse: Calculator – ASCC. Z3 – the world first 1945 John von Neumann: First functional Turing Draft of a Report on the EDVAC. complete computer, New idea: Stored-program program controlled computer. Previous computers 1944 Harvard Mark I required to physically modified to 1944 Colossus for given task. Remark: stored- 1946 ENIAC program idea appeared even 1947 Transistor earlier in 1943 year – ENIAC 1948 Manchester development: J. P. Eckert a J. Baby – the first stored- Mauchly program computer 1949 EDSAC – Computers of that era are single accumulator equipped by accumulator (one 1953 EDSAC, register) for arithmetic and logic Manchester Mark I, operations which is fixed IBM 700 series: single accumulator destination and one of source + index register operands. 2 B4M35PAP Advanced Computer Architectures 2 ISA development history 1954 John Backus: FORTRAN (FOrmula TRANslator) language There is a significant separation of the programming model from 1958: JohnMcCarthy: LSP (LISt implementation !!! Processing) language 1961 B5000: Computer designed and 1960 ALGOL (ALGOrithmic Language) optimized for ALGOL 60 -

Amd Ryzen™ 5000 Series Processors the Fastest in the Game1
QUICK REFERENCE GUIDE AMD RYZEN™ 5000 SERIES PROCESSORS THE FASTEST IN THE GAME1 THE FASTEST IN THE GAME1 THE LATEST TECHNOLOGIES BUILD WITH CONFIDENCE AMD Ryzen™ 5000 Series processors power the next generation of All AMD RyzenTM 5000 Series processors come with the full suite With AMD RyzenTM 5000 Series desktop processors, you can demanding games, providing one of a kind immersive experiences of Ryzen™ processor technologies designed to elevate your PC’s easily configure and customize your rig for the ultimate gaming and dominate any multithreaded task like 3D and video rendering, processing power including Precision Boost 2 and Precision Boost build. These processors drop-in ready with a BIOS update on and software compiling. With up to 16 cores, 32 threads, boost Overdrive3. Also get maximum graphics and storage bandwidth AMD 500 and 400 Series motherboards. You can easily tweak 2 clocks of up to 4.9GHz and up to 72MB of cache in select models, with these PCIe® 4.0 ready processors. That's not all, AMD and tune your processor with Ryzen™ Master and jump in the TM AMD Ryzen 5000 Series processors deliver the ultimate gaming RyzenTM 5000 Series features the exceptional 7nm architecture game faster with AMD StoreMI technology. performance. performance-per-watt. CORES/ UP TOMAX/BASE TOTAL PCIE® 4.0 LANES UNLOCKED FOR IN BOX THREADS TYPICAL TDP FREQUENCY2,4 CACHE WITH X570 CHIPSET OVERCLOCKING5 ARCHITECTURE COOLER (USABLE / TOTAL) AMD Ryzen™ 9 5950X 16/32 105W 4.9/3.4 72MB 36/44 Yes "Zen 3" - AMD Ryzen™ 9 3950X 16/32 105W 4.7/3.5 72MB -
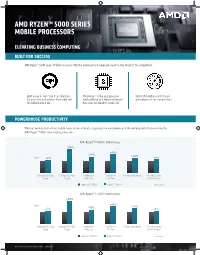
Amd Ryzentm 5000 Series Mobile Processors
AMD RYZENTM 5000 SERIES MOBILE PROCESSORS ELEVATING BUSINESS COMPUTING BUILT FOR SUCCESS AMD Ryzen™ 5000 Series Mobile Processors offer the advanced technology you need to stay ahead of the competition. Built on up to 7nm “Zen 3” architecture AMD Ryzen™ is the only processor Up to 90% higher multi-thread for processor performance leadership and family with up to 8 high performance performance vs the competition.2 incredible battery life. X86 cores for ultrathin notebooks.1 POWERHOUSE PRODUCTIVITY Whether working from office, huddle room, home or hotel, stay productive everywhere with the winning performance offered by AMD Ryzen™ 5000 series mobile processors. AMD RyzenTM 7 5800U Performance +90% +49% +30% +23% Up to +2% +9% .......................................................................................................................................................................................................... Cinebench R20 Single Cinebench R20 Multi- GeekBench v5 PassMark 10 PCMark 10 Benchmark MS Office Overall Thread Thread Multi-Core CPU Mark PCMark 10 Apps Intel Core i7-1165G7 RyzenTM 7 5800U See endnote 2 AMD RyzenTM 5 5600U Performance +90% +43% Up to +29% +5% +19% +8% .......................................................................................................................................................................................................... Cinebench R20 Single Cinebench R20 Multi- GeekBench v5 PassMark 10 PCMark 10 Benchmark MS Office Overall Thread Thread Multi-Core CPU Mark PCMark 10 Apps -

Ryzen 3 3200G Overclock Settings
Ryzen 3 3200g Overclock Settings So performance wise thing look great for the 3900X CPU, however there are some specifics that are not. also having the overclock ability. The ryzen 3 3200g is a cracking entry-level cpu from amd with integrated graphics processing. These options give you a bit of an overclocking boost at safe levels, but the results usually are nothing special. According to the leaker, the Ryzen 3 3200G can be overclocked to 4. The AMD Ryzen 3 3300X wasn't an obvious overclocking chip when I reviewed it. AMD 2nd Gen Ryzen processors including the Ryzen 3200G processor are not compatible with Precision Boost Overdrive. Talking about the overclock, 3200g seem to have larger overclock headroom for the igpu than 3400g, and a overclocked 3200g could have similar FPS as a overclocked 3400g. In dem erreiche ich auf niedrigen Settings nur 40fps durchschnittlich. 0, Lightning Gen 4 x4 M. 6GHz as opposed to 3. recently i build a Pc with ryzen 3 3200G on B450M S2H GIGABYTE MOBO Corsair 500watt Smps 8gb 1 stick 3200mhz ram and 256GB SSD + 1TB HDD (7200RPM) my processor is not turbo boosting upto 4Ghz as said on box when i tried overclocking using ryzen master and used freq 4000 @1. 7 GHz maximum clock and an integrated Vega 8 GPU, which is part of the most recent family of graphic chips from AMD. 0 GHz Max Boost) Socket AM4 65W YD3200C5FHBOX Desktop Processor with fast shipping and top-rated customer service. This is where to find the settings to overclock the CPU. -

Linux Hwmon Documentation
Linux Hwmon Documentation The kernel development community Jul 14, 2020 CONTENTS i ii CHAPTER ONE THE LINUX HARDWARE MONITORING KERNEL API Guenter Roeck 1.1 Introduction This document describes the API that can be used by hardware monitoring drivers that want to use the hardware monitoring framework. This document does not describe what a hardware monitoring (hwmon) Driver or Device is. It also does not describe the API which can be used by user space to communicate with a hardware monitoring device. If you want to know this then please read the following file: Documentation/hwmon/sysfs-interface.rst. For additional guidelines on how to write and improve hwmon drivers, please also read Documentation/hwmon/submitting-patches.rst. 1.2 The API Each hardware monitoring driver must #include <linux/hwmon.h> and, in most cases, <linux/hwmon-sysfs.h>. linux/hwmon.h declares the following regis- ter/unregister functions: struct device * hwmon_device_register_with_groups(struct device *dev, const char *name, void *drvdata, const struct attribute_group **groups); struct device * devm_hwmon_device_register_with_groups(struct device *dev, const char *name, void *drvdata, const struct attribute_group␣ ,!**groups); struct device * hwmon_device_register_with_info(struct device *dev, const char *name, void *drvdata, const struct hwmon_chip_info *info, const struct attribute_group **extra_ ,!groups); (continues on next page) 1 Linux Hwmon Documentation (continued from previous page) struct device * devm_hwmon_device_register_with_info(struct device *dev, const char *name, void *drvdata, const struct hwmon_chip_info *info, const struct attribute_group **extra_ ,!groups); void hwmon_device_unregister(struct device *dev); void devm_hwmon_device_unregister(struct device *dev); hwmon_device_register_with_groups registers a hardware monitoring device. The first parameter of this function is a pointer to the parent device. -

AMD Ryzen™ 5000 Series Mobile Processors with Radeon™ Graphics
QUICK REFERENCE GUIDE: JAN 2021 AMD Ryzen™ 5000 Series Mobile Processors with Radeon™ Graphics SUPREME PERFORMANCE. INFINITE POSSIBILITIES. AMD Ryzen™ 5000 Series Mobile Processors power game-changing notebooks with superb performance, outstanding battery life, and thin-and-light style. REWRITE THE RULES ULTIMATE UNCOMPROMISED PERFORMANCE Take on anything in the latest BATTERY LIFE thin and light notebook designs. AMD Ryzen™ 5000 Series mobile Intelligent, power-efficient Load robust apps at lightning processors feature the latest and performance means speeds, stream 4K Video greatest AMD processor technology you won’t run out of juice with HDR, and run immersive for users who need the when you need it most. multimedia and gaming ultimate performance. experiences, faster than ever. AMD RYZEN™ 5000 SERIES MOBILE PROCESSORS: SURPREME PERFORMANCE OVERALL PERFORMANCE PRODUCTIVITY ENTERTAINMENT CONTENT CREATION GAMING CHECK Up to 8 advanced processor CHECK Blaze through office work up to CHECK Be immersed in every detail of video CHECK Up to 24% faster video encoding2 CHECK A top tier AMD Ryzen™ 5000 series cores deliver powerful processing, 24% faster than previous gen1 chats or movies in up to 4K, HDR and 27% faster 3D rendering3 than gaming laptop can offer up to 70% incredible efficiency, and cool & with AMD Ryzen™ 7 5800U previous gen with AMD Ryzen™ 7 faster game performance than a top quiet performance mobile processor 5800U mobile processor tier previous gen laptop4 QUICK REFERENCE GUIDE | AMD RYZEN™ 5000 SERIES MOBILE PROCESSORS WITH -

AMD Brings Power of “Zen 3” to World's Best Mobile Processors for Business(1)
March 16, 2021 AMD Brings Power of “Zen 3” to World’s Best Mobile Processors for Business(1) -- AMD Ryzen PRO 5000 Series Mobile Processors – Business notebooks from HP and Lenovo powered by AMD Ryzen™ PRO 5000 Series Mobile Processors provide leadership performance and enterprise-class security solutions to meet the evolving demands of the modern workforce - SANTA CLARA, Calif., March 16, 2021 (GLOBE NEWSWIRE) -- Today, AMD (NASDAQ: AMD) announced the AMD Ryzen™ PRO 5000 Series Mobile Processors, bringing the uncompromising performance and efficiency of the “Zen 3” core architecture to premium business laptops. Paired with AMD PRO technologies that offer strengthened multi-layer enterprise-class security features and powerhouse productivity, the new AMD Ryzen PRO 5000 Series Mobile Processors are built to meet the demands of the modern workforce. With broad availability from HP and Lenovo expected starting in Q2, the number of AMD- powered enterprise notebooks is expected to triple by the end of 2021. “Navigating an increasingly distributed work environment requires more performance and security from our professional laptops. Businesses need to be confident they are investing in technology that will meet the needs of their employees, whether they are working remotely or from the office,” said Saeid Moshkelani, senior vice president and general manager, Client Business Unit, AMD. “The new AMD Ryzen PRO 5000 Series Mobile Processors significantly increase the capabilities of ultrathin enterprise notebooks and deliver best-in- class user experiences with leadership performance, exceptional battery life and robust security features for every work environment.” AMD Ryzen PRO 5000 Series Mobile Processors AMD Ryzen PRO 5000 Series Mobile Processors are built to provide a powerful computing experience with security features for today’s demanding business environments. -

Amd Ryzen™ 5000 Series Processors the World's Best Gaming Processors
QUICK REFERENCE GUIDE AMD RYZEN™ 5000 SERIES PROCESSORS THE WORLD'S BEST GAMING PROCESSORS THE FASTEST IN THE GAME1 THE LATEST TECHNOLOGIES BUILD WITH CONFIDENCE AMD Ryzen™ 5000 Series processors power the next generation of All AMD RyzenTM 5000 Series processors come with the full suite With AMD RyzenTM 5000 Series desktop processors, you can demanding games, providing one of a kind immersive experiences of Ryzen™ processor technologies designed to elevate your PC’s easily configure and customize your rig for the ultimate gaming and dominate any multithreaded task like 3D and video rendering, processing power including Precision Boost 2 and Precision Boost build. These processors drop-in ready with a BIOS update on and software compiling. With up to 16 cores, 32 threads, boost Overdrive3. Also get maximum graphics and storage bandwidth AMD 500 and 400 Series motherboards. You can easily tweak 2 clocks of up to 4.9GHz and up to 72MB of cache in select models, with these PCIe® 4.0 ready processors. That's not all, AMD and tune your processor with Ryzen™ Master and jump in the TM AMD Ryzen 5000 Series processors deliver the ultimate gaming RyzenTM 5000 Series features the exceptional 7nm architecture game faster with AMD StoreMI technology. performance. performance-per-watt. CORES/ UP TOMAX/BASE TOTAL PCIE® 4.0 LANES UNLOCKED FOR IN BOX COMPETITIVE THREADS TYPICAL TDP FREQUENCY2,4 CACHE WITH X570 CHIPSET OVERCLOCKING5 ARCHITECTURE COOLER PROCESSOR (USABLE / TOTAL) AMD Ryzen™ 9 5950X 16/32 105W 4.9/3.4 72MB 36/44 Yes "Zen 3" - - AMD Ryzen™