International Spy Museum
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

James Bond a 50 The
JAMES BOND: SIGNIFYING CHANGING IDENTITY THROUGH THE COLD WAR AND BEYOND By Christina A. Clopton Submitted to Central European University Department of International Relations and European Studies In partial fulfillment of the requirements for the Masters of Arts Supervisor: Professor Alexander Astrov CEU eTD Collection Budapest, Hungary 2014 Word Count: 12,928 Abstract The Constructivist paradigm of International Relations (IR) theory has provided for an ‘aesthetic turn’ in IR. This turn can be applied to popular culture in order to theorize about the international system. Using the case study of the James Bond film series, this paper investigates the continuing relevancy of the espionage series through the Cold War and beyond in order to reveal new information about the nature of the international political system. Using the concept of the ‘empty signifier,’ this work establishes the shifting identity of James Bond in relation to four thematic icons in the films: the villains, locations, women and technology and their relation to the international political setting over the last 50 years of the films. Bond’s changing identity throughout the series reveals an increasingly globalized society that gives prominence to David Chandler’s theory about ‘empire in denial,’ in which Western states are ever more reluctant to take responsibility for their intervention abroad. CEU eTD Collection i Acknowledgements I would like to extend my deepest gratitude to Professor Alexander Astrov for taking a chance with me on this project and guiding me through this difficult process. I would also like to acknowledge the constant support and encouragement from my IRES colleagues through the last year. -

Scouting Games. 61 Horse and Rider 54 1
The MacScouter's Big Book of Games Volume 2: Games for Older Scouts Compiled by Gary Hendra and Gary Yerkes www.macscouter.com/Games Table of Contents Title Page Title Page Introduction 1 Radio Isotope 11 Introduction to Camp Games for Older Rat Trap Race 12 Scouts 1 Reactor Transporter 12 Tripod Lashing 12 Camp Games for Older Scouts 2 Map Symbol Relay 12 Flying Saucer Kim's 2 Height Measuring 12 Pack Relay 2 Nature Kim's Game 12 Sloppy Camp 2 Bombing The Camp 13 Tent Pitching 2 Invisible Kim's 13 Tent Strik'n Contest 2 Kim's Game 13 Remote Clove Hitch 3 Candle Relay 13 Compass Course 3 Lifeline Relay 13 Compass Facing 3 Spoon Race 14 Map Orienteering 3 Wet T-Shirt Relay 14 Flapjack Flipping 3 Capture The Flag 14 Bow Saw Relay 3 Crossing The Gap 14 Match Lighting 4 Scavenger Hunt Games 15 String Burning Race 4 Scouting Scavenger Hunt 15 Water Boiling Race 4 Demonstrations 15 Bandage Relay 4 Space Age Technology 16 Firemans Drag Relay 4 Machines 16 Stretcher Race 4 Camera 16 Two-Man Carry Race 5 One is One 16 British Bulldog 5 Sensational 16 Catch Ten 5 One Square 16 Caterpillar Race 5 Tape Recorder 17 Crows And Cranes 5 Elephant Roll 6 Water Games 18 Granny's Footsteps 6 A Little Inconvenience 18 Guard The Fort 6 Slash hike 18 Hit The Can 6 Monster Relay 18 Island Hopping 6 Save the Insulin 19 Jack's Alive 7 Marathon Obstacle Race 19 Jump The Shot 7 Punctured Drum 19 Lassoing The Steer 7 Floating Fire Bombardment 19 Luck Relay 7 Mystery Meal 19 Pocket Rope 7 Operation Neptune 19 Ring On A String 8 Pyjama Relay 20 Shoot The Gap 8 Candle -

The Hero with Mad Skills James Bond and the World of Extreme Sports
The Hero with Mad Skills James Bond and the World of Extreme Sports DAVID M. PEGRAM In the 2007 Matchstick Productions film, Seven Sunny Days, professional skier and BASE jumper Shane McConke created a near shot!" -shot remake of the #ames Bond ski chase from The Spy Who Loved Me $%&77'( )he original featured stuntman +ick S l,ester $as #ames Bond' skiin* off the top of Mount Asgard, in Canada, to -hat appears to "e certain death( But, in the midst of freefall, S l,ester kicks off his skis and then opens a .nion #ack parachute, in -hat has become one of the /most iconic” scenes in the cinematic histor of #ames Bond $Aja Cho-dhur 1td( in Murph 20%2'( In Seven Sunny Days, McConke 3s jump is more darin*( As he flies off the ed*e of the cliff $shot in 4or-a , rather than Canada', he completes three full somersaults in midair before deplo in* his chute, in a demonstration of ho- far e5treme sports had come in the thirt ears since the S l,ester3s jump( )he recreation of S l,ester3s stunt -as McConke 3s homage to the cinematic moment that inspired him the most6 /)hat -as the coolest stunt I3d e,er seen,0 he recalled, creditin* S l,ester3s jump for *i,in* him the idea to sk di,e and BASE jump in the first place $McConkey 20%2'( )hat a #ames Bond film should ha,e such an influence on a skiin* /legend0 $Ble,ins 200&' su**ests, perhaps, a si*nificant connection "et-een the Bond franchise and the -orld of extreme sports. -

Completeandleft
MEN WOMEN 1. Adam Ant=English musician who gained popularity as the Amy Adams=Actress, singer=134,576=68 AA lead singer of New Wave/post-punk group Adam and the Amy Acuff=Athletics (sport) competitor=34,965=270 Ants=70,455=40 Allison Adler=Television producer=151,413=58 Aljur Abrenica=Actor, singer, guitarist=65,045=46 Anouk Aimée=Actress=36,527=261 Atif Aslam=Pakistani pop singer and film actor=35,066=80 Azra Akin=Model and actress=67,136=143 Andre Agassi=American tennis player=26,880=103 Asa Akira=Pornographic act ress=66,356=144 Anthony Andrews=Actor=10,472=233 Aleisha Allen=American actress=55,110=171 Aaron Ashmore=Actor=10,483=232 Absolutely Amber=American, Model=32,149=287 Armand Assante=Actor=14,175=170 Alessandra Ambrosio=Brazilian model=447,340=15 Alan Autry=American, Actor=26,187=104 Alexis Amore=American pornographic actress=42,795=228 Andrea Anders=American, Actress=61,421=155 Alison Angel=American, Pornstar=642,060=6 COMPLETEandLEFT Aracely Arámbula=Mexican, Actress=73,760=136 Anne Archer=Film, television actress=50,785=182 AA,Abigail Adams AA,Adam Arkin Asia Argento=Actress, film director=85,193=110 AA,Alan Alda Alison Armitage=English, Swimming=31,118=299 AA,Alan Arkin Ariadne Artiles=Spanish, Model=31,652=291 AA,Alan Autry Anara Atanes=English, Model=55,112=170 AA,Alvin Ailey ……………. AA,Amedeo Avogadro ACTION ACTION AA,Amy Adams AA,Andre Agasi ALY & AJ AA,Andre Agassi ANDREW ALLEN AA,Anouk Aimée ANGELA AMMONS AA,Ansel Adams ASAF AVIDAN AA,Army Archerd ASKING ALEXANDRIA AA,Art Alexakis AA,Arthur Ashe ATTACK ATTACK! AA,Ashley -

Things Are Not Enough Bond, Stiegler, and Technics
Things Are Not Enough Bond, Stiegler, and Technics CLAUS-ULRICH VIOL Discussions of Bond’s relationship with technology frequently centre around the objects he uses, the things he has at his disposal: what make is the car, what products have been placed in the flm, are the flm’s technical inventions realistic, visionary even !his can be observed in cinema foyers, fan circles, the media, as well as academia. #$en these discussions take an admiring turn, with commentators daz%led by the technological foresight of the flmic ideas; ' quite ofen too, especially in academic circles, views tend to be critical, connecting Bond’s technological overkill to some compensatory need in the character, seeing the technological objects as (props) that would and should not have to be ' *ee, for instance, publications like The Science of James Bond by Gresh and ,einberg -.//01, who set out to provide an “informative look at the real2world achievements and brilliant imaginations) behind the Bond gadgets, asking how realistic or “fant2 astic) the adventures and the equipment are and promising to thus probe into (the limits of science, the laws of nature and the future of technology” -back cover1" 3arker’s similar Death Rays, Jet Packs, Stunts and Supercars -.//41 includes discussions of the physics behind the action scenes -like stunts and chases1, but there remains a heavy preponderance of (ama%ing devices), (gadgets and gi%mos), “incredible cars), (reactors) and (guns) -v2vi1" ,eb pages and articles about (Bond Gadgets that 5ave Become 6eal), “Bond Gadgets 7ou 8an 9ctually Buy”, “Bond Gadgets that 8ould ,ork in 6eal :ife) and the like are legion. -

Military History Anniversaries 0101 Thru 0131
Military History Anniversaries 1 thru 31 January Events in History over the next 30 day period that had U.S. military involvement or impacted in some way on U.S military operations or American interests Jan 00 1944 – WW2: USS Scorpion (SS–278). Date of sinking unknown. Most likely a Japanese mine in Yellow or East China Sea. 77 killed. Jan 00 1945 – WW2: USS Swordfish (SS–193) missing. Possibly sunk by Japanese Coast Defense Vessel No. 4 on 5 January or sunk by a mine off Okinawa on 9 January. 89 killed. Jan 01 1942 – WW2: The War Production Board (WPB) ordered the temporary end of all civilian automobile sales leaving dealers with one half million unsold cars. Jan 01 1945 – WW2: In Operation Bodenplatte, German planes attack American forward air bases in Europe. This is the last major offensive of the Luftwaffe. Jan 02 1777 – American Revolution: American forces under the command of George Washington repulsed a British attack at the Battle of the Assunpink Creek near Trenton, New Jersey. Casualties and losses: US 7 to 100 - GB 55 to 365. Jan 02 1791 – Big Bottom massacre (11 killed) in the Ohio Country, marking the beginning of the Northwest Indian War. Jan 02 1904 – Latin America Interventions: U.S. Marines are sent to Santo Domingo to aid the government against rebel forces. Jan 02 1942 – The Federal Bureau of Investigation (FBI) convicts 33 members of a German spy ring headed by Fritz Joubert Duquesne in the largest espionage case in United States history-the Duquesne Spy Ring. Jan 02 1942 – WW2: In the Philippines, the city of Manila and the U.S. -

The Diplomatic Battle for the United States, 1914-1917
ACQUIRING AMERICA: THE DIPLOMATIC BATTLE FOR THE UNITED STATES, 1914-1917 Presented to The Division of History The University of Sheffield Fulfilment of the requirements for PhD by Justin Quinn Olmstead January 2013 Table of Contents Introduction 1: Pre-War Diplomacy 29 A Latent Animosity: German-American Relations 33 Britain and the U.S.: The Intimacy of Attraction and Repulsion 38 Rapprochement a la Kaiser Wilhelm 11 45 The Set Up 52 Advancing British Interests 55 Conclusion 59 2: The United States and Britain's Blockade 63 Neutrality and the Declaration of London 65 The Order in Council of 20 August 1914 73 Freedom of the Seas 83 Conclusion 92 3: The Diplomacy of U-Boat Warfare 94 The Chancellor's Challenge 96 The Chancellor's Decision 99 The President's Protest 111 The Belligerent's Responses 116 First Contact: The Impact of U-Boat Warfare 119 Conclusion 134 4: Diplomatic Acquisition via Mexico 137 Entering the Fray 140 Punitive Measures 145 Zimmerman's Gamble 155 Conclusion 159 5: The Peace Option 163 Posturing for Peace: 1914-1915 169 The House-Grey Memorandum 183 The German Peace Offer of 1916 193 Conclusion 197 6: Conclusion 200 Bibliography 227 Introduction Shortly after war was declared in August 1914 the undisputed leaders of each alliance, Great Britain and Gennany, found they were unable to win the war outright and began searching for further means to secure victory; the fonnation of a blockade, the use of submarines, attacking the flanks (Allied attacks in the Balkans and Baltic), Gennan Zeppelin bombardment of British coastal towns, and the diplomatic search for additional allies in an attempt to break the stalemate that had ensued soon after fighting had commenced. -

The Ethics of Intelligence Collection Ross W. Bellaby
What’s the Harm? The Ethics of Intelligence Collection Ross W. Bellaby Thesis submitted in fulfilment of the requirements for the degree of PhD Department of International Politics Aberystwyth University June 13th, 2011 DECLARATION This work has not previously been accepted in substance for any degree and is not being concurrently submitted in candidature for any degree. Signed ...................................................................... (Ross W. Bellaby) Date ........................................................................ STATEMENT 1 This thesis is the result of my own investigations, except where otherwise stated. Where *correction services have been used, the extent and nature of the correction is clearly marked in a footnote(s). Other sources are acknowledged by footnotes giving explicit references. A bibliography is appended. Signed ..................................................................... (Ross W. Bellaby) Date ........................................................................ [*this refers to the extent to which the text has been corrected by others] STATEMENT 2 I hereby give consent for my thesis, if accepted, to be available for photocopying and for inter- library loan, and for the title and summary to be made available to outside organisations. Signed ..................................................................... (Ross W. Bellaby) Date ........................................................................ I hereby give consent for my thesis, if accepted, to be available for photocopying -

A Younger Perspective Seniors Share Their Thoughts on the Presidential Election, Pg
october 26, 2012 Volume 76, Issue 3 1650 Ridgeview rd., uA, oH 43221 upper ArlIngton HIgH scHool a younger perspective seniors share their thoughts on the presidential election, pg. 17 differing districts student shares experience transferring from columbus to ua schools, pg. 6 Marching in the spotlight ua alum slated to take her bow in script ohio during final game of the OSU season, pg. 27 Media picks survey reveals students’ favorite aspects of social networking, pg. 25 www.arlingtonian.com advertisements Thanks to President Obama and Senator Sherrod Brown, • Pell Grant funding was doubled and a college tax credit was established, putting higher education within reach for millions more Americans. • The President successfully fought to prevent federal student loan interest rates from doubling for over 7 million students, and he capped federal student loan repayments. Mitt Romney’s plan to cut middle-class investments could slash Pell Grants for nearly 9.6 million students and would eliminate the President’s college tax credit. Romney would also roll back the President’s student loan reform - reforms that have saved over $60 billion and allowed investments in Pell Grants, community colleges and deficit reduction. He said that students who were unable to afford college or to start a business on their own should just “borrow money from your parents.” Thanks to President Obama and Senator Sherrod Brown, • Employers cannot deny you or your family members health care coverage due to pre-existing health conditions. • You will enjoy health coverage on your parents’ policy until age 26. • Your family will not be denied health coverage because you’ve reached a lifetime limit due to a family member’s chronic disease. -

Military History Anniversaries 1 Thru 15 January
Military History Anniversaries 1 thru 15 January Events in History over the next 15 day period that had U.S. military involvement or impacted in some way on U.S military operations or American interests Jan 00 1944 – WW2: USS Scorpion (SS–278). Date of sinking unknown. Most likely a Japanese mine in Yellow or East China Sea. 77 killed. Jan 00 1945 – WW2: USS Swordfish (SS–193) missing. Possibly sunk by Japanese Coast Defense Vessel No. 4 on 5 January or sunk by a mine off Okinawa on 9 January. 89 killed. Jan 01 1781 – American Revolution: Mutiny of the Pennsylvania Line – 1,500 soldiers from the Pennsylvania Line (all 11 regiments under General Anthony Wayne’s command) insist that their three-year enlistments are expired, kill three officers in a drunken rage and abandon the Continental Army’s winter camp at Morristown, New Jersey. Jan 01 1883 – Civil War: President Abraham Lincoln signs the final Emancipation Proclamation, which ends slavery in the rebelling states. The proclamation freed all slaves in states that were still in rebellion as of 1 JAN. Jan 01 1915 – WWI: The 15,000-ton British HMS class battleship Formidable is torpedoed by the German submarine U-24 and sinks in the English Channel, killing 547 men. The Formidable was part of the 5th Battle Squadron unit serving with the Channel Fleet. Jan 01 1942 – WW2: The War Production Board (WPB) ordered the temporary end of all civilian automobile sales leaving dealers with one half million unsold cars. Jan 01 1942 – WW2: United Nations – President Franklin D. -

Emergency Operations Center How-To Quick Reference Guide August 2021
National Incident Management System Emergency Operations Center How-To Quick Reference Guide August 2021 This page intentionally left blank Table of Contents Introduction .................................................................................................................................. 9 1. Purpose ...................................................................................................................................... 9 1.1. NIMS Compliance and Integration ................................................................................. 9 What Is an EOC? ........................................................................................................................ 10 1. Hallmarks of an EOC ............................................................................................................... 10 Preliminary Assessments .......................................................................................................... 12 1. Hazard and Vulnerability Assessment .................................................................................... 12 2. Resilience Analysis and Planning Tool ................................................................................... 12 3. Capability Assessment ............................................................................................................ 13 3.1. Interagency Coordination ............................................................................................. 13 3.2. Multiagency Coordination Groups .............................................................................. -
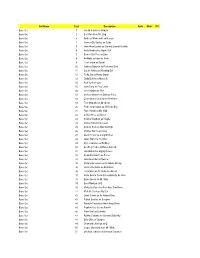
Set Name Card Description Auto Mem #'D Base Set 1 Harold Sakata As Oddjob Base Set 2 Bert Kwouk As Mr
Set Name Card Description Auto Mem #'d Base Set 1 Harold Sakata as Oddjob Base Set 2 Bert Kwouk as Mr. Ling Base Set 3 Andreas Wisniewski as Necros Base Set 4 Carmen Du Sautoy as Saida Base Set 5 John Rhys-Davies as General Leonid Pushkin Base Set 6 Andy Bradford as Agent 009 Base Set 7 Benicio Del Toro as Dario Base Set 8 Art Malik as Kamran Shah Base Set 9 Lola Larson as Bambi Base Set 10 Anthony Dawson as Professor Dent Base Set 11 Carole Ashby as Whistling Girl Base Set 12 Ricky Jay as Henry Gupta Base Set 13 Emily Bolton as Manuela Base Set 14 Rick Yune as Zao Base Set 15 John Terry as Felix Leiter Base Set 16 Joie Vejjajiva as Cha Base Set 17 Michael Madsen as Damian Falco Base Set 18 Colin Salmon as Charles Robinson Base Set 19 Teru Shimada as Mr. Osato Base Set 20 Pedro Armendariz as Ali Kerim Bey Base Set 21 Putter Smith as Mr. Kidd Base Set 22 Clifford Price as Bullion Base Set 23 Kristina Wayborn as Magda Base Set 24 Marne Maitland as Lazar Base Set 25 Andrew Scott as Max Denbigh Base Set 26 Charles Dance as Claus Base Set 27 Glenn Foster as Craig Mitchell Base Set 28 Julius Harris as Tee Hee Base Set 29 Marc Lawrence as Rodney Base Set 30 Geoffrey Holder as Baron Samedi Base Set 31 Lisa Guiraut as Gypsy Dancer Base Set 32 Alejandro Bracho as Perez Base Set 33 John Kitzmiller as Quarrel Base Set 34 Marguerite Lewars as Annabele Chung Base Set 35 Herve Villechaize as Nick Nack Base Set 36 Lois Chiles as Dr.