Remote Desktop Server: XDMCP
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Desktop Migration and Administration Guide
Red Hat Enterprise Linux 7 Desktop Migration and Administration Guide GNOME 3 desktop migration planning, deployment, configuration, and administration in RHEL 7 Last Updated: 2021-05-05 Red Hat Enterprise Linux 7 Desktop Migration and Administration Guide GNOME 3 desktop migration planning, deployment, configuration, and administration in RHEL 7 Marie Doleželová Red Hat Customer Content Services [email protected] Petr Kovář Red Hat Customer Content Services [email protected] Jana Heves Red Hat Customer Content Services Legal Notice Copyright © 2018 Red Hat, Inc. This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. -

The GNOME Census: Who Writes GNOME?
The GNOME Census: Who writes GNOME? Dave Neary & Vanessa David, Neary Consulting © Neary Consulting 2010: Some rights reserved Table of Contents Introduction.........................................................................................3 What is GNOME?.............................................................................3 Project governance...........................................................................3 Why survey GNOME?.......................................................................4 Scope and methodology...................................................................5 Tools and Observations on Data Quality..........................................7 Results and analysis...........................................................................10 GNOME Project size.......................................................................10 The Long Tail..................................................................................11 Effects of commercialisation..........................................................14 Who does the work?.......................................................................15 Who maintains GNOME?................................................................17 Conclusions........................................................................................22 References.........................................................................................24 Appendix 1: Modules included in survey...........................................25 2 Introduction What -

Release Notes for Fedora 15
Fedora 15 Release Notes Release Notes for Fedora 15 Edited by The Fedora Docs Team Copyright © 2011 Red Hat, Inc. and others. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/. The original authors of this document, and Red Hat, designate the Fedora Project as the "Attribution Party" for purposes of CC-BY-SA. In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, MetaMatrix, Fedora, the Infinity Logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. For guidelines on the permitted uses of the Fedora trademarks, refer to https:// fedoraproject.org/wiki/Legal:Trademark_guidelines. Linux® is the registered trademark of Linus Torvalds in the United States and other countries. Java® is a registered trademark of Oracle and/or its affiliates. XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL® is a registered trademark of MySQL AB in the United States, the European Union and other countries. All other trademarks are the property of their respective owners. -

SUSE® Linux Enterprise Desktop 12 and the Workstation Extension: What's New ?
SUSE® Linux Enterprise Desktop 12 and the Workstation Extension: What's New ? Frédéric Crozat <[email protected]> Enterprise Desktop Release Manager Scott Reeves <[email protected]> Enterprise Desktop Development Manager Agenda • Design Criteria • Desktop Environment in SUSE Linux Enterprise 12 • GNOME Shell • Desktop Features and Applications 2 Design Criteria SUSE Linux Enterprise Desktop Interoperability Ease of Use Security Ease of Management Lower Costs 4 SUSE Linux Enterprise Desktop 12 • Focus on technical workstation ‒ Developers and System administrators • One tool for the job • Main desktop applications will be shipped: ‒ Mail client, Office Suite, Graphical Editors, ... • SUSE Linux Enterprise Workstation Extension ‒ Extend SUSE Linux Enterprise Server with packages only available on SUSE Linux Enterprise Desktop. (x86-64 only) 5 Desktop in SUSE Linux Enterprise 12 As Part of the Common Code Base SUSE Linux Enterprise 12 Desktop Environment • SUSE Linux Enterprise 12 contains one primary desktop environment • Additional light-weight environment for special use-cases: ‒ Integrated Systems • Desktop environment is shared between the server and desktop products 7 SUSE Linux Enterprise 12 Desktop Environment • GNOME 3 is the main desktop environment ‒ SLE Classic mode by default ‒ GNOME 3 Classic Mode and GNOME 3 Shell Mode also available • SUSE Linux Enterprise 12 ships also lightweight IceWM ‒ Targeted at Integrated Systems • QT fully supported: ‒ QT5 supported for entire SLE12 lifecycle ‒ QT4 supported, will be removed in future -
Post Increment Evaluation Report Increment 11 International Space
SSP 54311 Baseline WWW.NASAWATCH.COM Post Increment Evaluation Report Increment 11 International Space Station Program Baseline June 2006 National Aeronautics and Space Administration International Space Station Program Johnson Space Center Houston, Texas Contract Number: NNJ04AA02C WWW.NASAWATCH.COM SSP 54311 Baseline - WWW.NASAWATCH.COM REVISION AND HISTORY PAGE REV. DESCRIPTION PUB. DATE - Initial Release (Reference per SSCD XXXXXX, EFF. XX-XX-XX) XX-XX-XX WWW.NASAWATCH.COM SSP 54311 Baseline - WWW.NASAWATCH.COM INTERNATIONAL SPACE STATION PROGRAM POST INCREMENT EVALUATION REPORT INCREMENT 11 CHANGE SHEET Month XX, XXXX Baseline Space Station Control Board Directive XXXXXX/(X-X), dated XX-XX-XX. (X) CHANGE INSTRUCTIONS SSP 54311, Post Increment Evaluation Report Increment 11, has been baselined by the authority of SSCD XXXXXX. All future updates to this document will be identified on this change sheet. WWW.NASAWATCH.COM SSP 54311 Baseline - WWW.NASAWATCH.COM INTERNATIONAL SPACE STATION PROGRAM POST INCREMENT EVALUATION REPORT INCREMENT 11 Baseline (Reference SSCD XXXXXX, dated XX-XX-XX) LIST OF EFFECTIVE PAGES Month XX, XXXX The current status of all pages in this document is as shown below: Page Change No. SSCD No. Date i - ix Baseline XXXXXX Month XX, XXXX 1-1 Baseline XXXXXX Month XX, XXXX 2-1 - 2-2 Baseline XXXXXX Month XX, XXXX 3-1 - 3-3 Baseline XXXXXX Month XX, XXXX 4-1 - 4-15 Baseline XXXXXX Month XX, XXXX 5-1 - 5-10 Baseline XXXXXX Month XX, XXXX 6-1 - 6-4 Baseline XXXXXX Month XX, XXXX 7-1 - 7-61 Baseline XXXXXX Month XX, XXXX A-1 - A-9 Baseline XXXXXX Month XX, XXXX B-1 - B-3 Baseline XXXXXX Month XX, XXXX C-1 - C-2 Baseline XXXXXX Month XX, XXXX D-1 - D-92 Baseline XXXXXX Month XX, XXXX WWW.NASAWATCH.COM SSP 54311 Baseline - WWW.NASAWATCH.COM INTERNATIONAL SPACE STATION PROGRAM POST INCREMENT EVALUATION REPORT INCREMENT 11 JUNE 2006 i SSP 54311 Baseline - WWW.NASAWATCH.COM SSCB APPROVAL NOTICE INTERNATIONAL SPACE STATION PROGRAM POST INCREMENT EVALUATION REPORT INCREMENT 11 JUNE 2006 Michael T. -

Collabkit – a Multi-User Multicast Collaboration System Based on VNC
Humboldt-Universität zu Berlin Institut für Informatik Lehrstuhl für Rechnerorganisation und Kommunikation Diplomarbeit CollabKit – A Multi-User Multicast Collaboration System based on VNC Christian Beier 19. April 2011 Gutachter Prof. Dr. Miroslaw Malek Prof. Dr. Jens-Peter Redlich Betreuer Peter Ibach <[email protected]> Abstract Computer-supported real-time collaboration systems offer functionality to let two or more users work together at the same time, allowing them to jointly create, modify and exchange electronic documents, use applications, and share information location-independently and in real-time. For these reasons, such collaboration systems are often used in professional and academic contexts by teams of knowledge workers located in different places. But also when used as computer-supported learning environments – electronic classrooms – these systems prove useful by offering interactive multi-media teaching possibilities and allowing for location-independent collaborative learning. Commonly, computer-supported real-time collaboration systems are realised using remote desktop technology or are implemented as web applications. However, none of the examined existing commercial and academic solutions were found to support concurrent multi-user interaction in an application-independent manner. When used in low-throughput shared-medium computer networks such as WLANs or cellular networks, most of the investigated systems furthermore do not scale well with an increasing number of users, making them unsuitable for multi-user collaboration of a high number of participants in such environments. For these reasons this work focuses on the design of a collaboration system that supports concurrent multi-user interaction with standard desktop applications and is able to serve a high number of users on low-throughput shared-medium computer networks by making use of multicast data transmission. -

Linux Networking Cookbook.Pdf
Linux Networking Cookbook ™ Carla Schroder Beijing • Cambridge • Farnham • Köln • Paris • Sebastopol • Taipei • Tokyo Linux Networking Cookbook™ by Carla Schroder Copyright © 2008 O’Reilly Media, Inc. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (safari.oreilly.com). For more information, contact our corporate/institutional sales department: (800) 998-9938 or [email protected]. Editor: Mike Loukides Indexer: John Bickelhaupt Production Editor: Sumita Mukherji Cover Designer: Karen Montgomery Copyeditor: Derek Di Matteo Interior Designer: David Futato Proofreader: Sumita Mukherji Illustrator: Jessamyn Read Printing History: November 2007: First Edition. Nutshell Handbook, the Nutshell Handbook logo, and the O’Reilly logo are registered trademarks of O’Reilly Media, Inc. The Cookbook series designations, Linux Networking Cookbook, the image of a female blacksmith, and related trade dress are trademarks of O’Reilly Media, Inc. Java™ is a trademark of Sun Microsystems, Inc. .NET is a registered trademark of Microsoft Corporation. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and O’Reilly Media, Inc. was aware of a trademark claim, the designations have been printed in caps or initial caps. While every precaution has been taken in the preparation of this book, the publisher and author assume no responsibility for errors or omissions, or for damages resulting from the use of the information contained herein. -

System Analysis and Tuning Guide System Analysis and Tuning Guide SUSE Linux Enterprise Server 15 SP1
SUSE Linux Enterprise Server 15 SP1 System Analysis and Tuning Guide System Analysis and Tuning Guide SUSE Linux Enterprise Server 15 SP1 An administrator's guide for problem detection, resolution and optimization. Find how to inspect and optimize your system by means of monitoring tools and how to eciently manage resources. Also contains an overview of common problems and solutions and of additional help and documentation resources. Publication Date: September 24, 2021 SUSE LLC 1800 South Novell Place Provo, UT 84606 USA https://documentation.suse.com Copyright © 2006– 2021 SUSE LLC and contributors. All rights reserved. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”. For SUSE trademarks, see https://www.suse.com/company/legal/ . All other third-party trademarks are the property of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its aliates. Asterisks (*) denote third-party trademarks. All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its aliates, the authors nor the translators shall be held liable for possible errors or the consequences thereof. Contents About This Guide xii 1 Available Documentation xiii -

Foot Prints Feel the Freedom of Fedora!
The Fedora Project: Foot Prints Feel The Freedom of Fedora! RRaahhuull SSuunnddaarraamm SSuunnddaarraamm@@ffeeddoorraapprroojjeecctt..oorrgg FFrreeee ((aass iinn ssppeeeecchh aanndd bbeeeerr)) AAddvviiccee 101011:: KKeeeepp iitt iinntteerraaccttiivvee!! Credit: Based on previous Fedora presentations from Red Hat and various community members. Using the age old wisdom and Indian, Free software tradition of standing on the shoulders of giants. Who the heck is Rahul? ( my favorite part of this presentation) ✔ Self elected Fedora project monkey and noisemaker ✔ Fedora Project Board Member ✔ Fedora Ambassadors steering committee member. ✔ Fedora Ambassador for India.. ✔ Editor for Fedora weekly reports. ✔ Fedora Websites, Documentation and Bug Triaging projects volunteer and miscellaneous few grunt work. Agenda ● Red Hat Linux to Fedora & RHEL - Why? ● What is Fedora ? ● What is the Fedora Project ? ● Who is behind the Fedora Project ? ● Primary Principles. ● What are the Fedora projects? ● Features, Future – Fedora Core 5 ... The beginning: Red Hat Linux 1994-2003 ● Released about every 6 months ● More stable “ .2” releases about every 18 months ● Rapid innovation ● Problems with retail channel sales model ● Impossible to support long-term ● Community Participation: ● Upstream Projects ● Beta Team / Bug Reporting The big split: Fedora and RHEL Red Hat had two separate, irreconcilable goals: ● To innovate rapidly. To provide stability for the long-term ● Red Hat Enterprise Linux (RHEL) ● Stable and supported for 7 years plus. A platform for 3rd party standardization ● Free as in speech ● Fedora Project / Fedora Core ● Rapid releases of Fedora Core, every 6 months ● Space to innovate. Fedora Core in the tradition of Red Hat Linux (“ FC1 == RHL10” ) Free as in speech, free as in beer, free as in community support ● Built and sponsored by Red Hat ● ...with increased community contributions. -

Indicators for Missing Maintainership in Collaborative Open Source Projects
TECHNISCHE UNIVERSITÄT CAROLO-WILHELMINA ZU BRAUNSCHWEIG Studienarbeit Indicators for Missing Maintainership in Collaborative Open Source Projects Andre Klapper February 04, 2013 Institute of Software Engineering and Automotive Informatics Prof. Dr.-Ing. Ina Schaefer Supervisor: Michael Dukaczewski Affidavit Hereby I, Andre Klapper, declare that I wrote the present thesis without any assis- tance from third parties and without any sources than those indicated in the thesis itself. Braunschweig / Prague, February 04, 2013 Abstract The thesis provides an attempt to use freely accessible metadata in order to identify missing maintainership in free and open source software projects by querying various data sources and rating the gathered information. GNOME and Apache are used as case studies. License This work is licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported (CC BY-SA 3.0) license. Keywords Maintenance, Activity, Open Source, Free Software, Metrics, Metadata, DOAP Contents List of Tablesx 1 Introduction1 1.1 Problem and Motivation.........................1 1.2 Objective.................................2 1.3 Outline...................................3 2 Theoretical Background4 2.1 Reasons for Inactivity..........................4 2.2 Problems Caused by Inactivity......................4 2.3 Ways to Pass Maintainership.......................5 3 Data Sources in Projects7 3.1 Identification and Accessibility......................7 3.2 Potential Sources and their Exploitability................7 3.2.1 Code Repositories.........................8 3.2.2 Mailing Lists...........................9 3.2.3 IRC Chat.............................9 3.2.4 Wikis............................... 10 3.2.5 Issue Tracking Systems...................... 11 3.2.6 Forums............................... 12 3.2.7 Releases.............................. 12 3.2.8 Patch Review........................... 13 3.2.9 Social Media............................ 13 3.2.10 Other Sources.......................... -

Download File
Eastern European Modernism: Works on Paper at the Columbia University Libraries and The Cornell University Library Compiled by Robert H. Davis Columbia University Libraries and Cornell University Library With a Foreword by Steven Mansbach University of Maryland, College Park With an Introduction by Irina Denischenko Georgetown University New York 2021 Cover Illustration: No. 266. Dvacáté století co dalo lidstvu. Výsledky práce lidstva XX. Věku. (Praha, 1931-1934). Part 5: Prokroky průmyslu. Photomontage wrappers by Vojtěch Tittelbach. To John and Katya, for their love and ever-patient indulgence of their quirky old Dad. Foreword ©Steven A. Mansbach Compiler’s Introduction ©Robert H. Davis Introduction ©Irina Denischenko Checklist ©Robert H. Davis Published in Academic Commons, January 2021 Photography credits: Avery Classics Library: p. vi (no. 900), p. xxxvi (no. 1031). Columbia University Libraries, Preservation Reformatting: Cover (No. 266), p.xiii (no. 430), p. xiv (no. 299, 711), p. xvi (no. 1020), p. xxvi (no. 1047), p. xxvii (no. 1060), p. xxix (no. 679), p. xxxiv (no. 605), p. xxxvi (no. 118), p. xxxix (nos. 600, 616). Cornell Division of Rare Books & Manuscripts: p. xv (no. 1069), p. xxvii (no. 718), p. xxxii (no. 619), p. xxxvii (nos. 803, 721), p. xl (nos. 210, 221), p. xli (no. 203). Compiler: p. vi (nos. 1009, 975), p. x, p. xiii (nos. 573, 773, 829, 985), p. xiv (nos. 103, 392, 470, 911), p. xv (nos. 1021, 1087), p. xvi (nos. 960, 964), p. xix (no. 615), p. xx (no. 733), p. xxviii (no. 108, 1060). F.A. Bernett Rare Books: p. xii (nos. 5, 28, 82), p. -
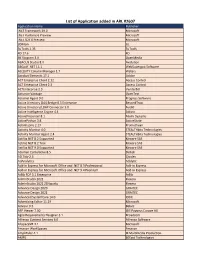
List of Application Added in ARL #2607
List of Application added in ARL #2607 Application Name Publisher .NET Framework 19.0 Microsoft .NET Runtime 6 Preview Microsoft .NET SDK 6 Preview Microsoft 3DMark UL 3uTools 2.35 3uTools 4D 17.6 4D 4K Stogram 3.0 OpenMedia ABACUS Studio 8.0 Avolution ABCpdf .NET 11.1 WebSupergoo Software ACQUITY Column Manager 1.7 Waters Acrobat Elements 17.1 Adobe ACT Enterprise Client 2.12 Access Control ACT Enterprise Client 2.3 Access Control ACTEnterprise 2.3 Vanderbilt Actiance Vantage OpenText Actional Agent 9.0 Progress Software Active Directory (AD) Bridge 8.5 Enterprise BeyondTrust Active Directory/LDAP Connector 5.0 Auth0 Active Intelligence Engine 4.4 Attivio ActivePresenter 8.1 Atomi Systems ActivePython 3.8 ActiveState ActivInspire 2.17 Promethean Activity Monitor 4.0 STEALTHbits Technologies Activity Monitor Agent 2.4 STEALTHbits Technologies ActiViz.NET 8.2 Supported Kitware SAS ActiViz.NET 8.2 Trial Kitware SAS ActiViz.NET 9.0 Supported Kitware SAS Acumen Cumulative 8.5 Deltek AD Tidy 2.6 Cjwdev AdAnalytics Adslytic Add-in Express for Microsoft Office and .NET 8.3 Professional Add-in Express Add-in Express for Microsoft Office and .NET 9.4 Premium Add-in Express Adlib PDF 5.1 Enterprise Adlib AdminStudio 2021 Flexera AdminStudio 2021 ZENworks Flexera Advance Design 2020 GRAITEC Advance Design 2021 GRAITEC Advanced SystemCare 14.0 IObit Advertising Editor 11.29 Microsoft Advisor 9.5 Belarc AFP Viewer 7.50 ISIS Papyrus Europe AG Agile Requirements Designer 3.1 Broadcom Alfresco Content Services 6.0 Alfresco Software AltspaceVR 4.1 Microsoft