Cshrc and Login Files Overview
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Administering Unidata on UNIX Platforms
C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta UniData Administering UniData on UNIX Platforms UDT-720-ADMU-1 C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Notices Edition Publication date: July, 2008 Book number: UDT-720-ADMU-1 Product version: UniData 7.2 Copyright © Rocket Software, Inc. 1988-2010. All Rights Reserved. Trademarks The following trademarks appear in this publication: Trademark Trademark Owner Rocket Software™ Rocket Software, Inc. Dynamic Connect® Rocket Software, Inc. RedBack® Rocket Software, Inc. SystemBuilder™ Rocket Software, Inc. UniData® Rocket Software, Inc. UniVerse™ Rocket Software, Inc. U2™ Rocket Software, Inc. U2.NET™ Rocket Software, Inc. U2 Web Development Environment™ Rocket Software, Inc. wIntegrate® Rocket Software, Inc. Microsoft® .NET Microsoft Corporation Microsoft® Office Excel®, Outlook®, Word Microsoft Corporation Windows® Microsoft Corporation Windows® 7 Microsoft Corporation Windows Vista® Microsoft Corporation Java™ and all Java-based trademarks and logos Sun Microsystems, Inc. UNIX® X/Open Company Limited ii SB/XA Getting Started The above trademarks are property of the specified companies in the United States, other countries, or both. All other products or services mentioned in this document may be covered by the trademarks, service marks, or product names as designated by the companies who own or market them. License agreement This software and the associated documentation are proprietary and confidential to Rocket Software, Inc., are furnished under license, and may be used and copied only in accordance with the terms of such license and with the inclusion of the copyright notice. -

Autocad Command Aliases
AutoCAD and Its Applications Advanced Appendix D AutoCAD Command Aliases Command Alias 3DALIGN 3AL 3DFACE 3F 3DMOVE 3M 3DORBIT 3DO, ORBIT, 3DVIEW, ISOMETRICVIEW 3DPOLY 3P 3DPRINT 3DP, 3DPLOT, RAPIDPROTOTYPE 3DROTATE 3R 3DSCALE 3S 3DWALK 3DNAVIGATE, 3DW ACTRECORD ARR ACTSTOP ARS -ACTSTOP -ARS ACTUSERINPUT ARU ACTUSERMESSAGE ARM -ACTUSERMESSAGE -ARM ADCENTER ADC, DC, DCENTER ALIGN AL ALLPLAY APLAY ANALYSISCURVATURE CURVATUREANALYSIS ANALYSISZEBRA ZEBRA APPLOAD AP ARC A AREA AA ARRAY AR -ARRAY -AR ATTDEF ATT -ATTDEF -ATT Copyright Goodheart-Willcox Co., Inc. Appendix D — AutoCAD Command Aliases 1 May not be reproduced or posted to a publicly accessible website. Command Alias ATTEDIT ATE -ATTEDIT -ATE, ATTE ATTIPEDIT ATI BACTION AC BCLOSE BC BCPARAMETER CPARAM BEDIT BE BLOCK B -BLOCK -B BOUNDARY BO -BOUNDARY -BO BPARAMETER PARAM BREAK BR BSAVE BS BVSTATE BVS CAMERA CAM CHAMFER CHA CHANGE -CH CHECKSTANDARDS CHK CIRCLE C COLOR COL, COLOUR COMMANDLINE CLI CONSTRAINTBAR CBAR CONSTRAINTSETTINGS CSETTINGS COPY CO, CP CTABLESTYLE CT CVADD INSERTCONTROLPOINT CVHIDE POINTOFF CVREBUILD REBUILD CVREMOVE REMOVECONTROLPOINT CVSHOW POINTON Copyright Goodheart-Willcox Co., Inc. Appendix D — AutoCAD Command Aliases 2 May not be reproduced or posted to a publicly accessible website. Command Alias CYLINDER CYL DATAEXTRACTION DX DATALINK DL DATALINKUPDATE DLU DBCONNECT DBC, DATABASE, DATASOURCE DDGRIPS GR DELCONSTRAINT DELCON DIMALIGNED DAL, DIMALI DIMANGULAR DAN, DIMANG DIMARC DAR DIMBASELINE DBA, DIMBASE DIMCENTER DCE DIMCONSTRAINT DCON DIMCONTINUE DCO, DIMCONT DIMDIAMETER DDI, DIMDIA DIMDISASSOCIATE DDA DIMEDIT DED, DIMED DIMJOGGED DJO, JOG DIMJOGLINE DJL DIMLINEAR DIMLIN, DLI DIMORDINATE DOR, DIMORD DIMOVERRIDE DOV, DIMOVER DIMRADIUS DIMRAD, DRA DIMREASSOCIATE DRE DIMSTYLE D, DIMSTY, DST DIMTEDIT DIMTED DIST DI, LENGTH DIVIDE DIV DONUT DO DRAWINGRECOVERY DRM DRAWORDER DR Copyright Goodheart-Willcox Co., Inc. -

Solaris 10 807 Release Notes
Solaris 10 8/07 Release Notes Oracle Corporation 500 Oracle Parkway Redwood City, CA 94065 U.S.A. Part No: 820–1259–13 August 2007 Copyright © 2008, 2011, Oracle and/or its affiliates. All rights reserved. License Restrictions Warranty/Consequential Damages Disclaimer This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. Warranty Disclaimer The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. Restricted Rights Notice If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT RIGHTS Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are "commercial computer software" or "commercial technical data" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, duplication, disclosure, modification, and adaptation shall be subject to the restrictions and license terms set forth in the applicable Government contract,and, to the extent applicable by the terms of the Government contract, the additional rights set forth in FAR 52.227-19, Commercial Computer Software License (December 2007). -

CS101 Lecture 9
How do you copy/move/rename/remove files? How do you create a directory ? What is redirection and piping? Readings: See CCSO’s Unix pages and 9-2 cp option file1 file2 First Version cp file1 file2 file3 … dirname Second Version This is one version of the cp command. file2 is created and the contents of file1 are copied into file2. If file2 already exits, it This version copies the files file1, file2, file3,… into the directory will be replaced with a new one. dirname. where option is -i Protects you from overwriting an existing file by asking you for a yes or no before it copies a file with an existing name. -r Can be used to copy directories and all their contents into a new directory 9-3 9-4 cs101 jsmith cs101 jsmith pwd data data mp1 pwd mp1 {FILES: mp1_data.m, mp1.m } {FILES: mp1_data.m, mp1.m } Copy the file named mp1_data.m from the cs101/data Copy the file named mp1_data.m from the cs101/data directory into the pwd. directory into the mp1 directory. > cp ~cs101/data/mp1_data.m . > cp ~cs101/data/mp1_data.m mp1 The (.) dot means “here”, that is, your pwd. 9-5 The (.) dot means “here”, that is, your pwd. 9-6 Example: To create a new directory named “temp” and to copy mv option file1 file2 First Version the contents of an existing directory named mp1 into temp, This is one version of the mv command. file1 is renamed file2. where option is -i Protects you from overwriting an existing file by asking you > cp -r mp1 temp for a yes or no before it copies a file with an existing name. -

An Introduction to the X Window System Introduction to X's Anatomy
An Introduction to the X Window System Robert Lupton This is a limited and partisan introduction to ‘The X Window System’, which is widely but improperly known as X-windows, specifically to version 11 (‘X11’). The intention of the X-project has been to provide ‘tools not rules’, which allows their basic system to appear in a very large number of confusing guises. This document assumes that you are using the configuration that I set up at Peyton Hall † There are helpful manual entries under X and Xserver, as well as for individual utilities such as xterm. You may need to add /usr/princeton/X11/man to your MANPATH to read the X manpages. This is the first draft of this document, so I’d be very grateful for any comments or criticisms. Introduction to X’s Anatomy X consists of three parts: The server The part that knows about the hardware and how to draw lines and write characters. The Clients Such things as terminal emulators, dvi previewers, and clocks and The Window Manager A programme which handles negotiations between the different clients as they fight for screen space, colours, and sunlight. Another fundamental X-concept is that of resources, which is how X describes any- thing that a client might want to specify; common examples would be fonts, colours (both foreground and background), and position on the screen. Keys X can, and usually does, use a number of special keys. You are familiar with the way that <shift>a and <ctrl>a are different from a; in X this sensitivity extends to things like mouse buttons that you might not normally think of as case-sensitive. -

Release Notes (100 001420)
VERITAS File System™ 3.3.3 Release Notes Solaris January 2000 100-001420 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software Corporation makes no warranty of any kind with regard to this manual, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. VERITAS Software Corporation shall not be liable for errors contained herein or for incidental or consequential damages in connection with the furnishing, performance, or use of this manual. Copyright Copyright © 2000 VERITAS Software Corporation. All rights reserved. VERITAS is a registered trademark of VERITAS Software Corporation in the US and other countries. The VERITAS logo and VERITAS File System are trademarks of VERITAS Software Corporation. All other trademarks or registered trademarks are the property of their respective owners. Printed in the USA, January 2000. VERITAS Software Corporation 1600 Plymouth St. Mountain View, CA 94043 Phone 650–335–8000 Fax 650–335–8050 www.veritas.com VERITAS File System Release Notes This guide provides information on VERITAS File System™ (VxFS) Release 3.3.3 for Solaris 2.5.1, Solaris 2.6, Solaris 7 (32-bit and 64-bit), and Solaris 8 (32-bit and 64-bit) operating systems. References in this document to VxFS 3.3 regarding new features, end of product support, compatibility, and software limitations apply to VxFS 3.3.3. Review this entire document before installing VxFS. The VERITAS File System packages include VxFS software, documentation, -

Shell Variables
Shell Using the command line Orna Agmon ladypine at vipe.technion.ac.il Haifux Shell – p. 1/55 TOC Various shells Customizing the shell getting help and information Combining simple and useful commands output redirection lists of commands job control environment variables Remote shell textual editors textual clients references Shell – p. 2/55 What is the shell? The shell is the wrapper around the system: a communication means between the user and the system The shell is the manner in which the user can interact with the system through the terminal. The shell is also a script interpreter. The simplest script is a bunch of shell commands. Shell scripts are used in order to boot the system. The user can also write and execute shell scripts. Shell – p. 3/55 Shell - which shell? There are several kinds of shells. For example, bash (Bourne Again Shell), csh, tcsh, zsh, ksh (Korn Shell). The most important shell is bash, since it is available on almost every free Unix system. The Linux system scripts use bash. The default shell for the user is set in the /etc/passwd file. Here is a line out of this file for example: dana:x:500:500:Dana,,,:/home/dana:/bin/bash This line means that user dana uses bash (located on the system at /bin/bash) as her default shell. Shell – p. 4/55 Starting to work in another shell If Dana wishes to temporarily use another shell, she can simply call this shell from the command line: [dana@granada ˜]$ bash dana@granada:˜$ #In bash now dana@granada:˜$ exit [dana@granada ˜]$ bash dana@granada:˜$ #In bash now, going to hit ctrl D dana@granada:˜$ exit [dana@granada ˜]$ #In original shell now Shell – p. -
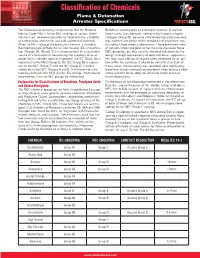
Classification of Chemicals
Classification of Chemicals Flame & Detonation Arrester Specifications PROTECTOSEAL ® The Protectoseal Company recommends that the National Butadiene would qualify as a Group D material. In each of Electric Code (NEC) Article 500, rankings of various chemi - these cases, the chemicals were primarly listed in a higher cals be used, whenever possible, to determine the suitability category (Group B), because of relatively high pressure read - of a detonation arrester for use with a particular chemical. ings noted in one phase of the standard test procedure con - When no NEC rating of the particular chemical is available, ducted by Underwriters Laboratories. These pressures were the International Electrotechnical Commission (IEC) classifica - of concern when categorizing the chemicals because these tion (Groups IIA, IIB and IIC) is recommended as a secondary NEC groupings are also used as standard indicators for the source of information for determining the suitability of an ar - design strength requirements of electrical boxes, apparatus, rester for its intended service. In general, the IEC Group IIA is etc. that must withstand the pressures generated by an igni - equivalent to the NEC Group D; the IEC Group IIB is equiva - tion within the container. It should be noted that, in each of lent to the NEC Group C; and the IEC Group IIC includes these cases, the test pressures recorded were significantly chemicals in the NEC Groups A and B. In the event of a dis - lower than those commonly encountered when testing a deto - crepancy between the NEC and the IEC ratings, Protectoseal nation arrester for its ability to withstand stable and over - recommends that the NEC groups be referenced. -

README for X11R7.5 on Netbsd Rich Murphey David Dawes Marc Wandschneider Mark Weaver Matthieu Herrb Table of Contents What and Where Is X11R7.5?
README for X11R7.5 on NetBSD Rich Murphey David Dawes Marc Wandschneider Mark Weaver Matthieu Herrb Table of Contents What and Where is X11R7.5?..............................................................................................3 New OS dependent features...............................................................................................3 Configuring X for Your Hardware.....................................................................................4 Running X..............................................................................................................................5 Kernel Support for X............................................................................................................5 Rebuilding the X Distribution...........................................................................................7 Building New X Clients.......................................................................................................8 Thanks.....................................................................................................................................8 What and Where is X11R7.5? X11R7.5 is an Open Source version of the X Window System that supports several UNIX(R) and UNIX-like operating systems (such as Linux, the BSDs and Solaris x86) on Intel and other platforms. This version is compatible with X11R6.6, and is based on the XFree86 4.4.0RC2 code base, which, in turn was based on the X consortium sample implementation. See the Copyright Notice1. The sources for X11R7.5 -

Introduction to Tivoli Enterprise Data Warehouse
Front cover Introduction to Tivoli Enterprise Data Warehouse Insider’s guide to Tivoli Enterpise Data Warehouse Best practices for creating data marts Integration with all major OLAP tools Vasfi Gucer William Crane Chris Molloy Sven Schubert Roger Walker ibm.com/redbooks International Technical Support Organization Introduction to Tivoli Enterprise Data Warehouse May 2002 SG24-6607-00 Take Note! Before using this information and the product it supports, be sure to read the general information in “Notices” on page xvii. First Edition (May 2002) This edition applies to Tivoli Enterprise Data Warehouse Version 1.1. Comments may be addressed to: IBM Corporation, International Technical Support Organization Dept. JN9B Building 003 Internal Zip 2834 11400 Burnet Road Austin, Texas 78758-3493 When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. © Copyright International Business Machines Corporation 2002. All rights reserved. Note to U.S Government Users – Documentation related to restricted rights – Use, duplication or disclosure is subject to restrictions set forth in GSA ADP Schedule Contract with IBM Corp. Contents Figures . .ix Tables . xv Notices . xvii Trademarks . xviii Preface . xix The team that wrote this redbook. xx Notice . xxi Comments welcome. xxii Chapter 1. Introducing building blocks. 1 1.1 Business Intelligence. 2 1.2 Business driving forces . 2 1.3 Main Business Intelligence terms . 3 1.3.1 Operational databases . 4 1.3.2 Online transaction processing (OLTP) . 4 1.3.3 Data warehouse . 5 1.3.4 Data mart . -

Linux Cheat Sheet
1 of 4 ########################################### # 1.1. File Commands. # Name: Bash CheatSheet # # # # A little overlook of the Bash basics # ls # lists your files # # ls -l # lists your files in 'long format' # Usage: A Helpful Guide # ls -a # lists all files, including hidden files # # ln -s <filename> <link> # creates symbolic link to file # Author: J. Le Coupanec # touch <filename> # creates or updates your file # Date: 2014/11/04 # cat > <filename> # places standard input into file # Edited: 2015/8/18 – Michael Stobb # more <filename> # shows the first part of a file (q to quit) ########################################### head <filename> # outputs the first 10 lines of file tail <filename> # outputs the last 10 lines of file (-f too) # 0. Shortcuts. emacs <filename> # lets you create and edit a file mv <filename1> <filename2> # moves a file cp <filename1> <filename2> # copies a file CTRL+A # move to beginning of line rm <filename> # removes a file CTRL+B # moves backward one character diff <filename1> <filename2> # compares files, and shows where differ CTRL+C # halts the current command wc <filename> # tells you how many lines, words there are CTRL+D # deletes one character backward or logs out of current session chmod -options <filename> # lets you change the permissions on files CTRL+E # moves to end of line gzip <filename> # compresses files CTRL+F # moves forward one character gunzip <filename> # uncompresses files compressed by gzip CTRL+G # aborts the current editing command and ring the terminal bell gzcat <filename> # -

UNIX (Solaris/Linux) Quick Reference Card Logging in Directory Commands at the Login: Prompt, Enter Your Username
UNIX (Solaris/Linux) QUICK REFERENCE CARD Logging In Directory Commands At the Login: prompt, enter your username. At the Password: prompt, enter ls Lists files in current directory your system password. Linux is case-sensitive, so enter upper and lower case ls -l Long listing of files letters as required for your username, password and commands. ls -a List all files, including hidden files ls -lat Long listing of all files sorted by last Exiting or Logging Out modification time. ls wcp List all files matching the wildcard Enter logout and press <Enter> or type <Ctrl>-D. pattern Changing your Password ls dn List files in the directory dn tree List files in tree format Type passwd at the command prompt. Type in your old password, then your new cd dn Change current directory to dn password, then re-enter your new password for verification. If the new password cd pub Changes to subdirectory “pub” is verified, your password will be changed. Many systems age passwords; this cd .. Changes to next higher level directory forces users to change their passwords at predetermined intervals. (previous directory) cd / Changes to the root directory Changing your MS Network Password cd Changes to the users home directory cd /usr/xx Changes to the subdirectory “xx” in the Some servers maintain a second password exclusively for use with Microsoft windows directory “usr” networking, allowing you to mount your home directory as a Network Drive. mkdir dn Makes a new directory named dn Type smbpasswd at the command prompt. Type in your old SMB passwword, rmdir dn Removes the directory dn (the then your new password, then re-enter your new password for verification.