Marshal8e6 Security Threats: Email and Web Threats by Marshal8e6 Tracelabs July 2009
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A the Hacker
A The Hacker Madame Curie once said “En science, nous devons nous int´eresser aux choses, non aux personnes [In science, we should be interested in things, not in people].” Things, however, have since changed, and today we have to be interested not just in the facts of computer security and crime, but in the people who perpetrate these acts. Hence this discussion of hackers. Over the centuries, the term “hacker” has referred to various activities. We are familiar with usages such as “a carpenter hacking wood with an ax” and “a butcher hacking meat with a cleaver,” but it seems that the modern, computer-related form of this term originated in the many pranks and practi- cal jokes perpetrated by students at MIT in the 1960s. As an example of the many meanings assigned to this term, see [Schneier 04] which, among much other information, explains why Galileo was a hacker but Aristotle wasn’t. A hack is a person lacking talent or ability, as in a “hack writer.” Hack as a verb is used in contexts such as “hack the media,” “hack your brain,” and “hack your reputation.” Recently, it has also come to mean either a kludge, or the opposite of a kludge, as in a clever or elegant solution to a difficult problem. A hack also means a simple but often inelegant solution or technique. The following tentative definitions are quoted from the jargon file ([jargon 04], edited by Eric S. Raymond): 1. A person who enjoys exploring the details of programmable systems and how to stretch their capabilities, as opposed to most users, who prefer to learn only the minimum necessary. -

Fortinet's March Threatscape Report Shows Domination of Ransomware and Troublesome Zero-Day
Fortinet's March Threatscape Report Shows Domination of Ransomware and Troublesome Zero-Day Rise of Ransomware Is Primarily Driven by Bredolab and Pushdo Botnets SUNNYVALE, CA, Apr 01, 2010 (MARKETWIRE via COMTEX News Network) -- Fortinet(R) (NASDAQ: FTNT) -- a leading network security provider and worldwide leader of unified threat management (UTM) solutions -- today announced its March 2010 Threatscape report showed domination of ransomware threats with nine of the detections in the malware top ten list resulting in either scareware or ransomware infesting the victim's PC. Fortinet observed the primary drivers behind these threats to be two of the most notorious botnet "loaders" -- Bredolab and Pushdo. Another important finding is the aggressive entrance of a new zero-day threat in FortiGuard's top ten attack list, MS.IE.Userdata.Behavior.Code.Execution, which accounted for 25 percent of the detected activity last month. Key threat activities for the month of March include: -- SMS-based Ransomware High Activity: A new ransomware threat -- W32/DigiPog.EP -- appeared in Fortinet's top ten malware list. DigiPog is an SMS blocker using Russian language, locking out a system and aggressively killing off popular applications like Internet Explorer and Firefox until an appropriate code is entered into a field provided to the user. To obtain the code, a user must send an SMS message to the provided number, receiving a code in return. Upon execution, DigiPog registers the user's MAC address with its server. It is the first time that SMS-based ransomware enters Fortinet's top ten list, showing that the rise of ransomware is well on its way. -

3/16/2020 Testout Labsim
3/16/2020 TestOut LabSim 8.4 Web Application Attacks As you study this section, answer the following questions: What are two ways that drive-by download attacks occur? Which countermeasures can be used to eliminate buffer overflow attacks? How can cross-site scripting (XSS) be used to breach the security of a web user? What is the best method for preventing SQL injection attacks? What are some types of header manipulation? Which mitigation practices help to protect internet-based activities from web application attacks? In this section, you will learn to: Prevent cross-site scripting Key terms for this section include the following: Term Definition Drive-By Download An attack where software or malware is downloaded and installed without explicit consent from the user. Typosquatting/URL Hijacking An attack that occurs when an attacker registers domain names that correlate to common typographical errors made by users when trying to access a legitimate website. Buffer Overflow An attack that exploits an operating system or an application that does not properly enforce boundaries for how much and what type of data can be inputted. An attack that exploits a computational operation by a running process that results in a numeric value that exceeds the maximum size of the integer type used to store it in Integer Overflow memory. Cross-Site Scripting (XSS) An attack that injects scripts into webpages. Cross-Site Request Forgery A type of malicious exploit whereby unauthorized commands are transmitted from the user to a website that currently trusts the user by way of authentication, cookies, etc. (CSRF/XSRF) LDAP Injection An attack that uses LDAP statements with arbitrary commands to exploit web-based applications with access to a directory service. -

PC Anti-Virus Protection 2011
PC Anti-Virus Protection 2011 12 POPULAR ANTI-VIRUS PROGRAMS COMPARED FOR EFFECTIVENESS Dennis Technology Labs, 03/08/2010 www.DennisTechnologyLabs.com This test aims to compare the effectiveness of the most recent releases of popular anti-virus software1. The products include those from Kaspersky, McAfee, Microsoft, Norton (Symantec) and Trend Micro, as well as free versions from Avast, AVG and Avira. Other products include those from BitDefender, ESET, G-Data and K7. The tests were conducted between 07/07/2010 and 22/07/2010 using the most up to date versions of the software available. A total of 12 products were exposed to genuine internet threats that real customers could have encountered during the test period. Crucially, this exposure was carried out in a realistic way, reflecting a customer’s experience as closely as possible. For example, each test system visited real, infected websites that significant numbers of internet users were encountering at the time of the test. These results reflect what would have happened if those users were using one of the seven products tested. EXECUTIVE SUMMARY Q Products that block attacks early tended to protect the system more fully The nature of web-based attacks means that the longer malware has access to a system, the more chances it has of downloading and installing further threats. Products that blocked the malicious and infected websites from the start reduced the risk of compromise by secondary and further downloads. Q 100 per cent protection is rare This test recorded an average protection rate of 87.5 per cent. New threats appear online frequently and it is inevitable that there will be times when specific security products are unable to protect from some of these threats. -

Synthesizing Near-Optimal Malware Specifications from Suspicious
Synthesizing Near-Optimal Malware Specifications from Suspicious Behaviors Somesh Jha∗, Matthew Fredrikson∗, Mihai Christodoresu†, Reiner Sailer‡, Xifeng Yan§ ∗University of Wisconsin–Madison, †Qualcomm Research Silicon Valley, ‡IBM T.J Watson Research Center, §University of California–Santa Barbara Abstract—Behavior-based detection techniques are a promis- and errors. ing solution to the problem of malware proliferation. However, We make the observation that behavioral specifications they require precise specifications of malicious behavior that do not result in an excessive number of false alarms, while still are best viewed as a form of discriminative specification.A remaining general enough to detect new variants before tradi- discriminative specification describes the unique properties tional signatures can be created and distributed. In this paper, of a given class, in contrast to the properties exhibited by we present an automatic technique for extracting optimally discriminative specifications a second mutually-exclusive class. This paper presents an , which uniquely identify a class automated technique that combines program analysis, graph of programs. Such a discriminative specification can be used by a behavior-based malware detector. Our technique, based mining, and stochastic optimization to synthesize malware on graph mining and stochastic optimization, scales to large behavior specifications. We represent program behaviors as classes of programs. When this work was originally published, graphs that are mined for discriminative patterns. As there the technique yielded favorable results on malware targeted are many ways in which malware can accomplish the same towards workstations (~86% detection rates on new malware). goal, we use these patterns as building blocks for construct- We believe that it can be brought to bear on emerging malware- based threats for new platforms, and discuss several promising ing discriminative specifications that are general across vari- avenues for future work in this direction. -

Cyber Warfare a “Nuclear Option”?
CYBER WARFARE A “NUCLEAR OPTION”? ANDREW F. KREPINEVICH CYBER WARFARE: A “NUCLEAR OPTION”? BY ANDREW KREPINEVICH 2012 © 2012 Center for Strategic and Budgetary Assessments. All rights reserved. About the Center for Strategic and Budgetary Assessments The Center for Strategic and Budgetary Assessments (CSBA) is an independent, nonpartisan policy research institute established to promote innovative thinking and debate about national security strategy and investment options. CSBA’s goal is to enable policymakers to make informed decisions on matters of strategy, secu- rity policy and resource allocation. CSBA provides timely, impartial, and insight- ful analyses to senior decision makers in the executive and legislative branches, as well as to the media and the broader national security community. CSBA encour- ages thoughtful participation in the development of national security strategy and policy, and in the allocation of scarce human and capital resources. CSBA’s analysis and outreach focus on key questions related to existing and emerging threats to US national security. Meeting these challenges will require transforming the national security establishment, and we are devoted to helping achieve this end. About the Author Dr. Andrew F. Krepinevich, Jr. is the President of the Center for Strategic and Budgetary Assessments, which he joined following a 21-year career in the U.S. Army. He has served in the Department of Defense’s Office of Net Assessment, on the personal staff of three secretaries of defense, the National Defense Panel, the Defense Science Board Task Force on Joint Experimentation, and the Defense Policy Board. He is the author of 7 Deadly Scenarios: A Military Futurist Explores War in the 21st Century and The Army and Vietnam. -

Lakeridge Health Uses Trend Micro™ Messaging and Web Security for Comprehensive Gateway Web Threat Protection
Securing Your Web World Lakeridge Health Uses Trend Micro™ Messaging and Web Security for Comprehensive Gateway Web Threat Protection Lakeridge Health (LH) serves a community of more than 500,000 residents within an area of 19,000 square kilometers in Ontario. IT must build in security to protect the mission-critical infrastructure that spans the 25 hospitals, clinics, and administrative sites. A recent escalation in web threats, including web-based phishing and malware as well as the spam emails that deliver links to these threats, called for a combination of Trend Micro messaging and web solutions supported by the Trend Micro Smart Protection Network. ESCALATING WEB THREATS “ Trend Micro messaging and Over the years, LH has tried many web security builds up our alternatives in its search for the best possible security. When web threats began defenses where they can to increase, LH’s user help desk was flooded do the most good—right at with complaints about spyware and other the edge of our network. infections. Unsatisfied with its previously These solutions have proven deployed products and lack of support from the vendor, LH evaluated four other security invaluable for fighting the vendors including Trend Micro. constantly evolving web After identifying Trend Micro as the winner of its security “bake off,” LH deployed multiple threats.” layers of Trend Micro protection. Trend Micro gateway protection blocks web-based threats by introducing messaging and web defense right at the network perimeter: — Peter Hastie, IT Systems Consultant • Trend Micro InterScan™ Messaging Security blocks emails threats, including spam, Lakeridge Health (LH), phishing, and malware, and offers content filtering to enforce compliance and prevent Ontario, Canada data leaks. -

Large-Scale Malware Experiments
LARGE-SCALE MALWARE EXPERIMENTS ... CALVET ET AL. LARGE-SCALE MALWARE • Unlike with in-the-wild experiments [1], there are fewer ethical or legal issues to deal with than when performing EXPERIMENTS: WHY, HOW, AND arbitrary attacks against infected computers. SO WHAT? • Having an in vitro environment provides us with a way to Joan Calvet, Jose M. Fernandez conduct computer security research in a scientifi c way: we École Polytechnique de Montréal, Montréal, Canada can reproduce experiments and test the effect of various independent variables. Email {joan.calvet, jose.fernandez}@polymtl.ca We decided to use the Waledac botnet as a fi rst experiment for the following reasons: Pierre-Marc Bureau ESET, Montréal, Canada • Thanks to prior reverse engineering [2], we had in-depth knowledge of this threat family. Email [email protected] • This malware does not replicate, thus limiting the risk of running an experiment that might get out of control. Jean-Yves Marion LORIA, Nancy, France • There exists a set of vulnerabilities in Waledac’s peer-to- peer protocol that were worth investigating. We wanted to Email [email protected] evaluate the impact of a mitigation scheme against the botnet. ABSTRACT 1.1 The Waledac case study One of the most popular research areas in the anti-malware The architecture of the Waledac botnet is split into four layers. industry (second only to detection) is to document malware The fi rst layer contains infected hosts with private IP addresses characteristics and understand their operations. Most initiatives that are referred to as spammers. They are essentially the are based on reverse engineering of malicious binaries so as to ‘worker’ bots and constitute approximately 80% of the botnet. -

The Botnet Chronicles a Journey to Infamy
The Botnet Chronicles A Journey to Infamy Trend Micro, Incorporated Rik Ferguson Senior Security Advisor A Trend Micro White Paper I November 2010 The Botnet Chronicles A Journey to Infamy CONTENTS A Prelude to Evolution ....................................................................................................................4 The Botnet Saga Begins .................................................................................................................5 The Birth of Organized Crime .........................................................................................................7 The Security War Rages On ........................................................................................................... 8 Lost in the White Noise................................................................................................................. 10 Where Do We Go from Here? .......................................................................................................... 11 References ...................................................................................................................................... 12 2 WHITE PAPER I THE BOTNET CHRONICLES: A JOURNEY TO INFAMY The Botnet Chronicles A Journey to Infamy The botnet time line below shows a rundown of the botnets discussed in this white paper. Clicking each botnet’s name in blue will bring you to the page where it is described in more detail. To go back to the time line below from each page, click the ~ at the end of the section. 3 WHITE -
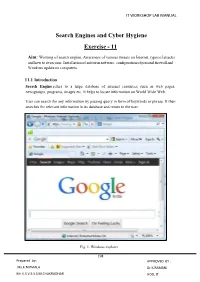
Search Engines and Cyber Hygiene Exercise - 11
IT WORKSHOP LAB MANUAL Search Engines and Cyber Hygiene Exercise - 11 Aim: Working of search engine, Awareness of various threats on Internet, types of attacks and how to overcome. Installation of antivirus software, configuration of personal firewall and Windows update on computers. 11.1 Introduction Search Engine refers to a huge database of internet resources such as web pages, newsgroups, programs, images etc. It helps to locate information on World Wide Web. User can search for any information by passing query in form of keywords or phrase. It then searches for relevant information in its database and return to the user. Fig. 1. Windows explorer 198 Prepared by: APPROVED BY : Ms.K.NIRMALA Dr.K.RAMANI Mr.V.S.V.S.S.S.M.CHAKRADHAR HOD, IT IT WORKSHOP LAB MANUAL Search Engine Components Generally there are three basic components of a search engine as listed below: 1. Web Crawler 2. Database 3. Search Interfaces Web crawler It is also known as spider or bots. It is a software component that traverses the web to gather information. Database All the information on the web is stored in database. It consists of huge web resources. Search Interfaces This component is an interface between user and the database. It helps the user to search through the database. Search Engine Working Web crawler, database and the search interface are the major component of a search engine that actually makes search engine to work. Search engines make use of Boolean expression AND, OR, NOT to restrict and widen the results of a search. Following are the steps that are performed by the search engine: The search engine looks for the keyword in the index for predefined database instead of going directly to the web to search for the keyword. -

MODELING the PROPAGATION of WORMS in NETWORKS: a SURVEY 943 in Section 2, Which Set the Stage for Later Sections
942 IEEE COMMUNICATIONS SURVEYS & TUTORIALS, VOL. 16, NO. 2, SECOND QUARTER 2014 Modeling the Propagation of Worms in Networks: ASurvey Yini Wang, Sheng Wen, Yang Xiang, Senior Member, IEEE, and Wanlei Zhou, Senior Member, IEEE, Abstract—There are the two common means for propagating attacks account for 1/4 of the total threats in 2009 and nearly worms: scanning vulnerable computers in the network and 1/5 of the total threats in 2010. In order to prevent worms from spreading through topological neighbors. Modeling the propa- spreading into a large scale, researchers focus on modeling gation of worms can help us understand how worms spread and devise effective defense strategies. However, most previous their propagation and then, on the basis of it, investigate the researches either focus on their proposed work or pay attention optimized countermeasures. Similar to the research of some to exploring detection and defense system. Few of them gives a nature disasters, like earthquake and tsunami, the modeling comprehensive analysis in modeling the propagation of worms can help us understand and characterize the key properties of which is helpful for developing defense mechanism against their spreading. In this field, it is mandatory to guarantee the worms’ spreading. This paper presents a survey and comparison of worms’ propagation models according to two different spread- accuracy of the modeling before the derived countermeasures ing methods of worms. We first identify worms characteristics can be considered credible. In recent years, although a variety through their spreading behavior, and then classify various of models and algorithms have been proposed for modeling target discover techniques employed by them. -

An Introduction to Malware
Downloaded from orbit.dtu.dk on: Sep 24, 2021 An Introduction to Malware Sharp, Robin Publication date: 2017 Document Version Publisher's PDF, also known as Version of record Link back to DTU Orbit Citation (APA): Sharp, R. (2017). An Introduction to Malware. General rights Copyright and moral rights for the publications made accessible in the public portal are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognise and abide by the legal requirements associated with these rights. Users may download and print one copy of any publication from the public portal for the purpose of private study or research. You may not further distribute the material or use it for any profit-making activity or commercial gain You may freely distribute the URL identifying the publication in the public portal If you believe that this document breaches copyright please contact us providing details, and we will remove access to the work immediately and investigate your claim. An Introduction to Malware Robin Sharp DTU Compute Spring 2017 Abstract These notes, written for use in DTU course 02233 on Network Security, give a short introduction to the topic of malware. The most important types of malware are described, together with their basic principles of operation and dissemination, and defenses against malware are discussed. Contents 1 Some Definitions............................2 2 Classification of Malware........................2 3 Vira..................................3 4 Worms................................