Oracle VM Virtualbox User Manual
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Kernel Panic
Kernel Panic Connect, Inc. 1701 Quincy Avenue, Suites 5 & 6, Naperville, IL 60540 Ph: (630) 717-7200 Fax: (630) 717-7243 www.connectrf.com Table of Contents SCO Kernel Patches for Panics on Pentium Systems…………………………………..1 Kernel Panic Debug Methodologies..............................................................................3 SCO Kernel Patches for Panics on Pentium Systems SCO Kernel Patches for Panics on Pentium Systems Web Links http://www.sco.com/cgi-bin/ssl_reference?104530 http://www.sco.com/cgi-bin/ssl_reference?105532 Pentium System Panics with Trap Type 6; no dump is saved to /dev/swap. Keywords panic trap kernel invalid opcode pentium querytlb querytbl 386 mpx unix v4 dump swap double type6 no patch /etc/conf/pack.d/kernel/locore.o image locore Release SCO UNIX System V/386 Release 3.2 Operating System Version 4.0, 4.1 and 4.2 SCO Open Desktop Release 2.0 and 3.0 SCO Open Server System Release 2.0 and 3.0 Problem My system panics with a Trap Type 6, but no memory dump gets written. Cause There is a flaw in the kernel querytlb() routine that allows the Pentium to execute a 386-specific instruction which causes it to panic with an invalid opcode. querytlb() is only called when your system is panicking. The fault causes the system to double- panic and it thus fails to write a panic dump to disk. This means that the panic trap type 6 is concealing another type of panic which will show itself after the following patch has been applied. Solution You can apply the following patch, as root, to: /etc/conf/pack.d/kernel/locore.o Use the procedure that follows. -

Virtual Machine Technologies and Their Application in the Delivery of ICT
Virtual Machine Technologies and Their Application In The Delivery Of ICT William McEwan accq.ac.nz n Christchurch Polytechnic Institute of Technology Christchurch, New Zealand [email protected] ABSTRACT related areas - a virtual machine or network of virtual machines can be specially configured, allowing an Virtual Machine (VM) technology was first ordinary user supervisor rights, and it can be tested implemented and developed by IBM to destruction without any adverse effect on the corporation in the early 1960's as a underlying host system. mechanism for providing multi-user facilities This paper hopes to also illustrate how VM in a secure mainframe computing configurations can greatly reduce our dependency on environment. In recent years the power of special purpose, complex, and expensive laboratory personal computers has resulted in renewed setups. It also suggests the important additional role interest in the technology. This paper begins that VM and VNL is likely to play in offering hands-on by describing the development of VM. It practical experience to students in a distance e- discusses the different approaches by which learning environment. a VM can be implemented, and it briefly considers the advantages and disadvantages Keywords: Virtual Machines, operating systems, of each approach. VM technology has proven networks, e-learning, infrastructure, server hosting. to be extremely useful in facilitating the Annual NACCQ, Hamilton New Zealand July, 2002 www. Annual NACCQ, Hamilton New Zealand July, teaching of multiple operating systems. It th offers an alternative to the traditional 1. INTRODUCTION approaches of using complex combinations Virtual Machine (VM) technology is not new. It was of specially prepared and configured OS implemented on mainframe computing systems by the images installed via the network or installed IBM Corporation in the early 1960’s (Varian 1997 pp permanently on multiple partitions or on 3-25, Gribben 1989 p.2, Thornton 2000 p.3, Sugarman multiple physical hard drives. -

SAS Enters the Mainstream Although Adoption of Serial Attached SCSI
SAS enters the mainstream By the InfoStor staff http://www.infostor.com/articles/article_display.cfm?Section=ARTCL&C=Newst&ARTICLE_ID=295373&KEYWORDS=Adaptec&p=23 Although adoption of Serial Attached SCSI (SAS) is still in the infancy stages, the next 12 months bode well for proponents of the relatively new disk drive/array interface. For example, in a recent InfoStor QuickVote reader poll, 27% of the respondents said SAS will account for the majority of their disk drive purchases over the next year, although Serial ATA (SATA) topped the list with 37% of the respondents, followed by Fibre Channel with 32%. Only 4% of the poll respondents cited the aging parallel SCSI interface (see figure). However, surveys of InfoStor’s readers are skewed by the fact that almost half of our readers are in the channel (primarily VARs and systems/storage integrators), and the channel moves faster than end users in terms of adopting (or at least kicking the tires on) new technologies such as serial interfaces. Click here to enlarge image To get a more accurate view of the pace of adoption of serial interfaces such as SAS, consider market research predictions from firms such as Gartner and International Data Corp. (IDC). Yet even in those firms’ predictions, SAS is coming on surprisingly strong, mostly at the expense of its parallel SCSI predecessor. For example, Gartner predicts SAS disk drives will account for 16.4% of all multi-user drive shipments this year and will garner almost 45% of the overall market in 2009 (see figure on p. 18). -

OLD PRETENDER Lovrenc Gasparin, Fotolia
COVER STORY Bochs Emulator Legacy emulator OLD PRETENDER Lovrenc Gasparin, Fotolia Gasparin, Lovrenc Bochs, the granddaddy of all emulators, is alive and kicking; thanks to regular vitamin jabs, the lively old pretender can even handle Windows XP. BY TIM SCHÜRMANN he PC emulator Bochs first saw the 2.2.6 version in the Universe reposi- box). This also applies if you want to the light of day in 1994. Bochs’ tory; you will additionally need to install run Bochs on a pre-Pentium CPU, such Tinventor, Kevin Lawton, distrib- the Bximage program. (Bximage is al- as a 486. uted the emulator under a commercial li- ready part of the Bochs RPM for open- After installation, the program will cense before selling to French Linux ven- SUSE.) If worst comes to worst, you can simulate a complete PC, including CPU, dor Mandriva (which was then known always build your own Bochs from the graphics, sound card, and network inter- as MandrakeSoft). Mandriva freed the source code (see the “Building Bochs” face. The virtual PC in a PC works so emulator from its commercial chains, re- leasing Bochs under the LGPL license. Building Bochs If you prefer to build your own Bochs, or an additional --enable-ne2000 parameter Installation if you have no alternative, you will first to configure. The extremely long list of Bochs has now found a new home at need to install the C++ compiler and de- parameters in the user manual [2] gives SourceForge.net [1] (Figure 1). You can veloper packages for the X11 system. you a list of available options. -

The Seeds of Rural Resilience
NEWS & VIEWS FROM THE SUSTAINABLE SOUTHWEST Growing a Regional Food System THE SEEDS OF RURAL RESILIENCE October 2017 NORTHERN NEW MEXICO’S LARGEST DISTRIBUTION NEWSPAPER Vol. 9 No. 10 2 Green Fire Times • October 2017 www.GreenFireTimes.com Is Your Roof Winter Ready? Whether your roof is currently leaking or you’d like to restore your roof before it fails, Fix My Roof is the right choice. Call today for a free roof assessment! www.GreenFireTimes.com Green Fire Times • October 2017 3 YOU’LL LOVE WHAT YOU SEE! PROGRAM PARTNERS: FRIDAY SATURDAY OCT 27 NOV 14 7:30 PM 7:30 PM Sponsored by The L.A. Grow the Growers Browns Dance Farm Training 5 Project Business Incubation A CULTIVATING BERNALILLO COUNTY INITIATIVE bernalillo Applications for the 2018 Opencounty Space internships now available Lensic.org 505-988-1234 For more information NONPROFIT • COMMUNITY FUNDED SERVICE CHARGES APPLY AT ALL POINTS OF PURCHASE A special thanks to our www.bernco.gov/growthegrowers 2017/2018 sponsor: Find Your Future in ENGINEERING @Northern New Mexico College NORTHERN The most affordable 4-year now offering college in the Southwest classes at Santa Fe HEC! Northern Engineering programs include: n ABET-accredited Bachelor in INFORMATION ENGINEERING Tech (IET) n Ask about our new CYBERSECURITY concentration in IET Schedule your campus visit today! n Bachelor in ELECTROMECHANICAL Engineering/Solar Energy Concentration CALL 505.747.2111 or visit nnmc.edu n Associate of Applied Science degrees in RENEWABLE ENERGY and ELECTRICAL TECH 4 Green Fire Times Oc tober 2017 www.GreenFireTimes.com Vol. 9, No. 10 October 2017 Issue No. -

Virtual Routing in the Cloud
I I I I I I I I I CISCO ~ ptg17123584 Virtual Routing in the Cloud Arvind Durai Stephen Lynn ciscopress.com Amit Srivastava Exclusive Offer - 40% OFF Cisco Press Video Training live lessons·® ciscopress.com/video Use coupon code CPVIDE040 during checkout. Video Instruction from Technology Experts livelessons·® ptg17123584 Advance Your Skills Train Anywhere Learn Get started with fundamentals, Train anywhere, at your Learn from trusted author become an expert, or get certified. own pace, on any device. trainers published by Cisco Press. Try Our Popular Video Training for FREE! ciscopress.com/video Explore hundreds of FREE video lessons from our growing library of Complete Video Courses, Livelessons, networking talks, and workshops. 9781587144943_Durai_Virtual_Routing_Cloud_CVR.indd 2 4/8/16 1:25 PM Virtual Routing in the Cloud Arvind Durai, CCIE No. 7016 Stephen Lynn, CCIE No. 5507 & CCDE No. 20130056 Amit Srivastava ptg17123584 Cisco Press 800 East 96th Street Indianapolis, IN 46240 USA ii Virtual Routing in the Cloud Virtual Routing in the Cloud Arvind Durai, CCIE No. 7016 Stephen Lynn, CCIE No. 5507 & CCDE No. 20130056 Amit Srivastava Copyright© 2016 Cisco Systems, Inc. Published by: Cisco Press 800 East 96th Street Indianapolis, IN 46240 USA All rights reserved. No part of this book may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage and retrieval system, without written permission from the publisher, except for the inclusion of brief quotations in a review. Printed in the United States of America First Printing April 2016 Library of Congress Control Number: 2016934921 ISBN-13: 978-1-58714-494-3 ISBN-10: 1-58714-494-8 Warning and Disclaimer ptg17123584 This book is designed to provide information about CSR 1000V router and adoption of NFV technology in the cloud environment. -

Oracle Berkeley DB Installation and Build Guide Release 18.1
Oracle Berkeley DB Installation and Build Guide Release 18.1 Library Version 18.1.32 Legal Notice Copyright © 2002 - 2019 Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. Berkeley DB, and Sleepycat are trademarks or registered trademarks of Oracle. All rights to these marks are reserved. No third- party use is permitted without the express prior written consent of Oracle. Other names may be trademarks of their respective owners. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. -
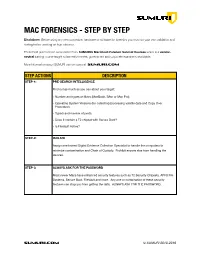
SUMURI Macintosh Forensics Best Practices
! MAC FORENSICS - STEP BY STEP Disclaimer: Before using any new procedure, hardware or software for forensics you must do your own validation and testing before working on true evidence. These best practices are summarized from SUMURI’s Macintosh Forensic Survival Courses which is a vendor- neutral training course taught to law enforcement, government and corporate examiners worldwide. More information about SUMURI can be found at SUMURI.com STEP ACTIONS DESCRIPTION STEP-1: PRE-SEARCH INTELLIGENCE Find out as much as you can about your target: • Number and types of Macs (MacBook, iMac or Mac Pro). • Operating System Versions (for collecting/processing volatile data and Copy Over Procedure). • Type/s and number of ports. • Does it contain a T2 chipset with Secure Boot? • Is FileVault Active? STEP-2: ISOLATE Assign one trained Digital Evidence Collection Specialist to handle the computers to minimize contamination and Chain of Custody. Prohibit anyone else from handling the devices. STEP-3: ALWAYS ASK FOR THE PASSWORD Most newer Macs have enhanced security features such as T2 Security Chipsets, APFS File Systems, Secure Boot, FileVault and more. Any one or combination of these security features can stop you from getting the data. ALWAYS ASK FOR THE PASSWORD. SUMURI.com © SUMURI 2010-2019 ! STEP ACTIONS DESCRIPTION STEP-4: IF COMPUTER IS ON - SCREEN SAVER PASSWORD ACTIVE Options are: • Ask for the Password - Confirm password and proceed to Step-6. • Restart to Image RAM - Connect a RAM Imaging Utility to the Mac such as RECON IMAGER. Conduct a soft-restart (do not power off if possible and image the RAM). -

Oracle VM Virtualbox User Manual
Oracle VM VirtualBox R User Manual Version 5.1.0 c 2004-2016 Oracle Corporation http://www.virtualbox.org Contents 1 First steps 11 1.1 Why is virtualization useful?............................. 12 1.2 Some terminology................................... 12 1.3 Features overview................................... 13 1.4 Supported host operating systems.......................... 15 1.5 Installing VirtualBox and extension packs...................... 16 1.6 Starting VirtualBox.................................. 17 1.7 Creating your first virtual machine......................... 18 1.8 Running your virtual machine............................ 21 1.8.1 Starting a new VM for the first time.................... 21 1.8.2 Capturing and releasing keyboard and mouse.............. 22 1.8.3 Typing special characters.......................... 23 1.8.4 Changing removable media......................... 24 1.8.5 Resizing the machine’s window...................... 24 1.8.6 Saving the state of the machine...................... 25 1.9 Using VM groups................................... 26 1.10 Snapshots....................................... 26 1.10.1 Taking, restoring and deleting snapshots................. 27 1.10.2 Snapshot contents.............................. 28 1.11 Virtual machine configuration............................ 29 1.12 Removing virtual machines.............................. 30 1.13 Cloning virtual machines............................... 30 1.14 Importing and exporting virtual machines..................... 31 1.15 Global Settings................................... -

AD Bridge User Guide
AD Bridge User Guide May 2019 Legal Notice © Copyright 2019 Micro Focus or one of its affiliates. The only warranties for products and services of Micro Focus and its affiliates and licensors (“Micro Focus”) are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. Micro Focus shall not be liable for technical or editorial errors or omissions contained herein. The information contained herein is subject to change without notice. For additional information, such as certification-related notices and trademarks, see http://www.microfocus.com/about/legal/. Contents About This Guide 5 1 Getting Started 7 2 Installing AD Bridge 9 Linux Requirements and Supported Platforms . 9 Linux Requirements . 9 Supported Linux Platforms. 10 Installing the AD Bridge Linux Agent. 11 Licensing the Linux Agent . 12 Joining Active Directory - Post Installation . 13 Installing the AD Bridge GPEdit Extension . 13 3 Managing Linux GPO Settings 15 Accessing or Creating Group Policy Objects . 15 Configuring Linux GPO Settings . 16 Managing Linux Agent Services with GPOs . 17 Importing Custom Configuration File Settings. 18 Managing Linux Applications with GPOs . 18 Managing User Logins with GPOs . 19 Viewing Policy Injection on a Linux Agent. 20 A Appendix 21 Linux Agent GPO Settings . 21 Linux Agent Commands and Lookups . 22 GPO Best Practices . 23 Contents 3 4 About This Guide The AD Bridge User Guide provides information to help you understand, install, configure, and employ the Micro Focus AD Bridge product to help manage your enterprise environment. Audience This guide is written for administrators and users who will use Micro Focus AD Bridge to more effectively manage Active Directory and group policies in a cross-platform environment. -

Oracle Webcenter Portal 11G R1 PS7 Virtual Machine
Oracle WebCenter Portal 11g R1 PS7 Virtual Machine CONFIGURING AND RUNNING THE VIRTUAL MACHINE Announcing the availability of Oracle WebCenter Portal 11g R1 PS7 Virtual Machine based on Linux x86-64-bit platform. It includes everything you need to learn about the R1 PS7 release and try it out. System Requirements Component Requirement ORACLE WEBCENTER POR TAL VIRTUAL MACHINE Includes fully configured: Operating System Microsoft Windows 7 64 bit or Linux 64 bit • Oracle WebCenter Portal Memory At least 12GB RAM • Oracle WebCenter Content with Hard disk 50GB free disk space + Framework Folders 30GB temporary space during Virtual Machine (VM) import • Oracle JDeveloper Virtual Machine Server Oracle VirtualBox 4.3.26 or higher • Getting Started Portal VirtualBox extensions are already installed on the VM Downloading the Virtual Machine The virtual machine is available as an appliance (.OVA file). Import the .OVA file into Oracle VirtualBox. 1. Download the files— Appliance OVA file: OracleWebCenterPortal11gR1PS7.ova MD5 Checksum: OracleWebCenterPortal11gR1PS7.ova.md5 2. Download the checksum tool that is built for your platform. 3. Verify that files are valid by checking their checksum md5sum –c OracleWebCenterPortal11gR1PS7.ova.md5. Importing and Starting the Virtual Machine Import the appliance into Oracle VirtualBox (File Import Appliance…). This takes around 40 minutes. The VM has one virtual hard drive. Ensure that the drive/mount point specified by the Virtual Disk Image (see Figure 1) has at least 60GB free disk space. CONFIGURING AND RUNN ING THE VIRTUAL MACH INE Figure 1 - Importing the virtual machine For more information on importing an appliance into VirtualBox, refer its online help. -
Engineering Specifications
DOC NO : Rev. Issued Date : 2020/10/08 V1.0 SOLID STATE STORAGE TECHNOLOGY CORPORATION 司 Revised Date : ENGINEERING SPECIFICATIONS Product Name: CVB-CDXXX (WT) Model CVB-CD128 CVB-CD256 CVB-CD512 CVB-CD1024 Author: Ken Liao DOC NO : Rev. Issued Date : 2020/10/08 V1.0 SOLID STATE STORAGE TECHNOLOGY CORPORATION 司 Revised Date : Version History Date 0.1 Draft 2020/07/20 1.0 First release 2020/10/08 DOC NO : Rev. Issued Date : 2020/10/08 V1.0 SOLID STATE STORAGE TECHNOLOGY CORPORATION 司 Revised Date : Copyright 2020 SOLID STATE STORAGE TECHNOLOGY CORPORATION Disclaimer The information in this document is subject to change without prior notice in order to improve reliability, design, and function and does not represent a commitment on the part of the manufacturer. In no event will the manufacturer be liable for direct, indirect, special, incidental, or consequential damages arising out of the use or inability to use the product or documentation, even if advised of the possibility of such damages. This document contains proprietary information protected by copyright. All rights are reserved. No part of this datasheet may be reproduced by any mechanical, electronic, or other means in any form without prior written permission of SOLID STATE STORAGE Technology Corporation. DOC NO : Rev. Issued Date : 2020/10/08 V1.0 SOLID STATE STORAGE TECHNOLOGY CORPORATION 司 Revised Date : Table of Contents 1 Introduction ....................................................................... 5 1.1 Overview .............................................................................................