Global Security, the Number One Dilemma of the World Community: the Case of the United States
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Les Archives Du Sombre Et De L'expérimental
Guts Of Darkness Les archives du sombre et de l'expérimental avril 2006 Vous pouvez retrouvez nos chroniques et nos articles sur www.gutsofdarkness.com © 2000 - 2008 Un sommaire de ce document est disponible à la fin. Page 2/249 Les chroniques Page 3/249 ENSLAVED : Frost Chronique réalisée par Iormungand Thrazar Premier album du groupe norvégien chz le label français Osmose Productions, ce "Frost" fait suite au début du groupe avec "Vikingligr Veldi". Il s'agit de mon album favori d'Enslaved suivi de près par "Eld", on ressent une envie et une virulence incroyables dans cette oeuvre. Enslaved pratique un black metal rageur et inspiré, globalement plus violent et ténébreux que sur "Eld". Il n'y a rien à jeter sur cet album, aucune piste de remplissage. On commence après une intro aux claviers avec un "Loke" ravageur et un "Fenris" magnifique avec son riff à la Satyricon et son break ultra mélodique. Enslaved impose sa patte dès 1994, avec la très bonne performance de Trym Torson à la batterie sur cet album, qui s'en ira rejoindre Emperor par la suite. "Svarte vidder" est un grand morceau doté d'une intro symphonique, le développement est excellent, 9 minutes de bonheur musical et auditif. "Yggdrasill" se pose en interlude de ce disque, un titre calme avec voix grave, guimbarde, choeurs et l'utilisation d'une basse fretless jouée par Eirik "Pytten", le producteur de l'album: un intemrède magnifique et judicieux car l'album gagne en aération. Le disque enchaîne sur un "Jotu249lod" destructeur et un Gylfaginning" accrocheur. -

The Guardian, July 22, 1992
Wright State University CORE Scholar The Guardian Student Newspaper Student Activities 7-22-1992 The Guardian, July 22, 1992 Wright State University Student Body Follow this and additional works at: https://corescholar.libraries.wright.edu/guardian Part of the Mass Communication Commons Repository Citation Wright State University Student Body (1992). The Guardian, July 22, 1992. : Wright State University. This Newspaper is brought to you for free and open access by the Student Activities at CORE Scholar. It has been accepted for inclusion in The Guardian Student Newspaper by an authorized administrator of CORE Scholar. For more information, please contact [email protected]. The Guardian ISSUE NO. 2. VOL. 28 WRIGHT STATE UNIVERSITY WEDNESDAY, JULY 22, 1992 O RECYCLED PAP!!* Oops, watch that turn Students to pay more in the fall By THOMAS J. LUCENTE News Editor Wright State University, for the third time in the last four quarters, has raised tuition. Full-time, undergraduate stu- dents will begin paying $979 per quarter this fall. On July 13, the state Con- trolling Board voted to allow universities to raise their tu- ition as much as 9 percent. The previous cap was 7 percent. Am The cap increase came af- ter Gov. George Voinovich, a graduate of Ohio University and The Ohio State Univer- sity. cut $170.2 million from the budget for higher educa- Paige E. Mulhollan The Falrbom fire department had trouble maneuvering their truck earlier this month, tion. damaging the quad and a trash can. Voinovich, who ran for election as the "education gover- education could be facing an- nor," has now cut the higher educa- other 5 percent in cuts at the end tion budget three times since tak- of the calendar year if no im- INSIDE ing office in January 1991. -
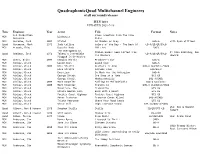
Quadraphonicquad Multichannel Engineers of All Surround Releases
QuadraphonicQuad Multichannel Engineers of all surround releases JULY 2021 UPDATED 2021-7-16 Type Engineer Year Artist Title Format Notes 5.1 Production Live… Greetins From The Flow MCH Dishwalla Services, State MCH Abraham, Josh 2003 Staind 14 Shades of Grey DVD-A with Ryan Williams Quad Abramson, Mark 1973 Judy Collins Colors of the Day - The Best Of CD-4/Q8/QR/SACD MCH Acquah, Ebby Depeche Mode 101 Live SACD The Outrageous Dr. Stolen Goods: Gems Lifted from P: Alan Blaikley, Ken Quad Adelman, Jack 1972 Teleny's Incredible CD-4/Q8/QR/SACD the Masters Howard Plugged-In Orchestra MCH Ahern, Brian 2003 Emmylou Harris Producer’s Cut DVD-A MCH Ainlay, Chuck David Alan David Alan DVD-A MCH Ainlay, Chuck 2005 Dire Straits Brothers In Arms DVD-A DualDisc/SACD MCH Ainlay, Chuck Dire Straits Alchemy Live DVD/BD-V MCH Ainlay, Chuck Everclear So Much for the Afterglow DVD-A MCH Ainlay, Chuck George Strait One Step at a Time DTS CD MCH Ainlay, Chuck George Strait Honkytonkville DVD-A/SACD MCH Ainlay, Chuck 2005 Mark Knopfler Sailing To Philadelphia DVD-A DualDisc MCH Ainlay, Chuck 2005 Mark Knopfler Shangri La DVD-A DualDisc/SACD MCH Ainlay, Chuck Mavericks, The Trampoline DTS CD MCH Ainlay, Chuck Olivia Newton John Back With a Heart DTS CD MCH Ainlay, Chuck Pacific Coast Highway Pacific Coast Highway DTS CD MCH Ainlay, Chuck Peter Frampton Frampton Comes Alive! DVD-A/SACD MCH Ainlay, Chuck Trisha Yearwood Where Your Road Leads DTS CD MCH Ainlay, Chuck Vince Gill High Lonesome Sound DTS CD/DVD-A/SACD QSS: Ron & Howard Quad Albert, Ron & Howard 1975 -

Metal Machine Music: Technology, Noise, and Modernism in Industrial Music 1975-1996
SSStttooonnnyyy BBBrrrooooookkk UUUnnniiivvveeerrrsssiiitttyyy The official electronic file of this thesis or dissertation is maintained by the University Libraries on behalf of The Graduate School at Stony Brook University. ©©© AAAllllll RRRiiiggghhhtttsss RRReeessseeerrrvvveeeddd bbbyyy AAAuuuttthhhooorrr... Metal Machine Music: Technology, Noise, and Modernism in Industrial Music 1975-1996 A Dissertation Presented by Jason James Hanley to The Graduate School in Partial Fulfillment of the Requirements for the Degree of Doctor of Philsophy in Music (Music History) Stony Brook University August 2011 Copyright by Jason James Hanley 2011 Stony Brook University The Graduate School Jason James Hanley We, the dissertation committee for the above candidate for the Doctor of Philosophy degree, hereby recommend acceptance of this dissertation. Judith Lochhead – Dissertation Advisor Professor, Department of Music Peter Winkler - Chairperson of Defense Professor, Department of Music Joseph Auner Professor, Department of Music David Brackett Professor, Department of Music McGill University This dissertation is accepted by the Graduate School Lawrence Martin Dean of the Graduate School ii Abstract of the Dissertation Metal Machine Music: Technology, Noise, and Modernism in Industrial Music 1975-1996 by Jason James Hanley Doctor of Philosophy in Music (Music History) Stony Brook University 2011 The British band Throbbing Gristle first used the term Industrial in the mid-1970s to describe the intense noise of their music while simultaneously tapping into a related set of aesthetics and ideas connected to early twentieth century modernist movements including a strong sense of history and an intense self-consciousness. This model was expanded upon by musicians in England and Germany during the late-1970s who developed the popular music style called Industrial as a fusion of experimental popular music sounds, performance art theatricality, and avant-garde composition. -

Current, June 14, 1999
University of Missouri, St. Louis IRL @ UMSL Current (1990s) Student Newspapers 6-14-1999 Current, June 14, 1999 University of Missouri-St. Louis Follow this and additional works at: https://irl.umsl.edu/current1990s Recommended Citation University of Missouri-St. Louis, "Current, June 14, 1999" (1999). Current (1990s). 310. https://irl.umsl.edu/current1990s/310 This Newspaper is brought to you for free and open access by the Student Newspapers at IRL @ UMSL. It has been accepted for inclusion in Current (1990s) by an authorized administrator of IRL @ UMSL. For more information, please contact [email protected]. YOUl' SOU1'ce jOl' campus news PROFILE and information Toya Like graduated cum laude after four years of working through college, being a single mom, and remembering a tragedy. .... See page 4 '\ UNiVERSITY OF MISSOURI - ,ST. L OUIS VOLUME 33 • ISSUE gsa University adds two new Here come the grads ... endowed professorships BY CORY BLACKWOOD filling UM-St. Louis maxirnunl num and new challenges to the global econ staff assistant ber. omy, Each professorship is made possi The professorship in corporate Endowed Professorships in ble when a plivate investor such as E. learning will hold appointment in the Corporate Learning and Economic Desmond Lee donates $550,000 School of Business Administration. History were recently instituted at which is matched by the State of The professor will work with regional UM-St. Louis. Chancellor. Blanche Missouri, After the private investor business organizations to give stu Touhill announced on May 18 that the commits money, a national search dents a better leatlllng opportunity and two endowed professorships would be committee is fOlmed to find a candi make UM-St Louis a more competi instituted, date eligible to be a professor in that tive business school. -

En Klubb, Ett Band, En Livsstil
Groove 8 • 2005 Amusement Parks on Fire sidan 5 Idoler finns överallt Tre frågor till Christian Kellvander s. 5 När löpsedlarna dagligen basunerar av dessa är de riktiga idolerna, de som Panikångest bakom skivspelarna s. 5 Omslags- ut att folk kollapsat i Idol-tävlan är inte riktigt har talangen men som foto Suburban Kids with Biblical names s. 6 förra årets egentlige vinnare redan på ändå vågar upp framför den obarm- Anton Är vi boskap? sidan 6 gång med nytt album. Småtjejernas härtiga juryn. Det skulle jag aldrig Corbijn vrål hörs återigen i alla Sveriges köp- våga själv! Hoppas bara de inser att Groove är en oberoende musiktidning, Bronco Busters sidan 7 center när killen som gett tandställ- just de kanske inte är menade att bli och ges ut av Musiktidning i Göteborg AB. Favvoplattan sidan 7 ningen ett ansikte gjort en uppföljare popidoler, men att de inte är värde- till vårvinterns The Anthem. Det gäl- lösa för det. Groove Yob sidan 8 ler att smida medan järnet är varmt. Men vissa ska ändå använda detta Box 112 91 CocoRosie sidan 8 Men Darin är nu ingen flopp, var- nederlag som tändvätska. De udda 404 26 Göteborg Thomas Denver Jonsson sidan 10 ken kommersiellt eller annars, fast och oslipade artisterna behövs mer Telefon 031–833 855 plattan gör honom inte heller till Sve- än nånsin när sångare i Darins klass Elpost [email protected] They Live by Night sidan 10 riges Justin – så bra är den inte. Även dessutom får uppbackning av dyra http://www.groove.se Cat5 sidan 11 om spåren Step up och framförallt producenter och stora skivbolag. -

Lanthorn, Vol. 23, No. 08, October 19, 1988 Grand Valley State University
Grand Valley State University ScholarWorks@GVSU Volume 23 Lanthorn, 1968-2001 10-19-1988 Lanthorn, vol. 23, no. 08, October 19, 1988 Grand Valley State University Follow this and additional works at: http://scholarworks.gvsu.edu/lanthorn_vol23 Part of the Archival Science Commons, Education Commons, and the History Commons Recommended Citation Grand Valley State University, "Lanthorn, vol. 23, no. 08, October 19, 1988" (1988). Volume 23. 8. http://scholarworks.gvsu.edu/lanthorn_vol23/8 This Issue is brought to you for free and open access by the Lanthorn, 1968-2001 at ScholarWorks@GVSU. It has been accepted for inclusion in Volume 23 by an authorized administrator of ScholarWorks@GVSU. For more information, please contact [email protected]. Inside: Opinion Campus Life Concerts Sports Professionalism Classified Ads Crackdowns Legalizing Volume 22; Issue Number 8 Read M y Turn, page 4 Grand Valley State University j T H E L A N T Downtown Center Move Draws Mixed Reactions Let There be Light By Gina Fernandez Proposal was sponsored by Kelly Student Senate, Tim Hondorp. By Michael Newell pus, or in this case, campuses. News Writer J. Israels and ratified by the According to Hondorp, the Guest News Writer Ben Danenberg, a senior in the business school was sympathetic Student Senate on October 29th, illumination of the walkway 1987. Downtown may be where the to transportation problems whicii The lights have finally been from Parking Lot J to the Grand put up on the path. Last week This proposal was fun is but it’s not usually where the will undoubtedly surface with the Valley State University Water the contractor that the Physical recommended by the Student classes are. -

B1756153x the Project Gutenberg Ebook of Searchlights on Health by B
b1756153x The Project Gutenberg EBook of Searchlights on Health by B. G. Jefferis and J. L. Nichols This eBook is for the use of anyone anywhere at no cost and with almost no restrictions whatsoever. You may copy it, give it away or re-use it under the terms of the Project Gutenberg License included with this eBook or online at www.gutenberg.net Title: Searchlights on Health The Science of Eugenics Author: B. G. Jefferis and J. L. Nichols Release Date: September 12, 2004 [EBook #13444] Language: English Character set encoding: ASCII *** START OF THIS PROJECT GUTENBERG EBOOK SEARCHLIGHTS ON HEALTH *** Produced by Juliet Sutherland, Alicia Williams, and the Online Distributed Proofreading Team. SEARCHLIGHTS ON HEALTH THE SCIENCE OF EUGENICS * * * * * A Guide to Purity and Physical Manhood Advice to Maiden, Wife and Mother Love, Courtship, and Marriage * * * * * By PROF. B.G. JEFFERIS, M.D., PH. D. and J.L. NICOLS, A.M. _With Excerpts from Well-Known Authorities_ REV. LEONARD DAWSON DR. M.J. SAVAGE REV. H.R. HAWEIS DR. PANCOAST DR. STALL DR. J.F. SCOTT DR. GEORGE NAPHEYS DR. STOCKHAM Page 1 b1756153x DR. T.D. NICHOLLS DR. R.L. DUGDALE DR. JOHN COWAN DR. M.L. HOLBROOK * * * * * Published by J.L. NICHOLS & COMPANY Naperville, Illinois, U.S.A. 1920 AGENTS WANTED "Vice has no friend like the prejudice which claims to be virtue."--_Lord Lytton._ "When the judgment's weak, the prejudice is strong."--_Kate O'Hare._ "It is the first right of every child to be well born." * * * * * COPYRIGHTED 1919, BY J.L. -

Download Tracklist (Pdf)
switchbLack tracklist #001-#300 by DJ Wildhoney & DJ Stellarator 0Kontrol Nebenwirkung [digital single] 1000 Homo DJ's Supernaut (DIE KRUPPS Remix) [Occult Box - sampler] 1000 Homo DJ's Supernaut [Supernaut] 1000 Ohm A.G.N.E.S. [A.G.N.E.S. 7"] 101 Rock To The Beat [Rock To The Beat 12"] 13th Chime Coffin Maker [The Singles: 1981-1983] 16volt Alkali [American Porn Songs] 16volt Somebody To Hate (Hate Hegel Remix) [American Porn Songs Remixed] 16volt Suffering You [Fullblackhabit] 16volt The Carrion [Beating Dead Horses] 16volt The Man Comes Around [The Negative Space] 16volt The Perfect One [The Negative Space] 16volt With Fire And Burning [American Porn Songs] 16volt vs Cyanotic The Defect People (Glitch Mode Mix) [Cyanotic Presents: Gears Gone Wild] 1919 Dream [2015: "The Madness Continues" Sessions] 1919 Man, Myth, And The Curse Of The Immortal [Futurecide] 2 Times Terror Maailman Tuomari (feat. Puijon Perkele) [Equals One Sudden Death] 22 HERTZ Detonate [Detonate] 22 HERTZ Is This Real [Detonate] 2nd face Prophecy [1st Of His Name] 32CRASH Anger (Tim Schuldt Remix) [Weird News From An Uncertain Future] 32CRASH Plutonian Breeders [Weird News From An Uncertain Future] 3rd Machine Ditch The Hollow [The Egotiator] 3TEETH Affluenza [Metawar] 3TEETH Altær [Metawar] 3TEETH Bornless [Metawar] 3TEETH Dust [3TEETH] 3TEETH Nihil [3TEETH] 3TEETH Pearls 2 Swine [3TEETH] 3TEETH Sell Your Face 2.0 [Metawar] 3TEETH Too Far Gone [3TEETH] 3TEETH X-Day [3TEETH] 400 Blows Fundamental Islam [The New Lords On The Block] 5 Star Grave Terminal Bedroom [Drugstore -

The Eighth Day : a Novel with Critical Commentary
University of Lethbridge Research Repository OPUS http://opus.uleth.ca Theses Arts and Science, Faculty of 1994 The eighth day : a novel with critical commentary Galbraith, Evelyn Van Lethbridge, Alta : University of Lethbridge, Faculty of Arts and Science, 1994 http://hdl.handle.net/10133/25 Downloaded from University of Lethbridge Research Repository, OPUS THE EIGHTH DAY: A NOVEL WITH CRITICAL COMMENTARY Evelyn Van Galbraith Master of Arts Degree in English University of Lethbridge, 1994 A Thesis Submitted to the Council on Graduate Studies of the University of Lethbridge in Partial Fulfillment of the Requirements for the Degree MASTER OF ARTS LETHBRIDGE, ALBERTA April, 1994 © Evelyn Van Galbraith, 1994 THE EIGHTH DAY: A NOVEL WITH CRITICAL COMMENTARY ABSTRACT This thesis contains two parts: a novel, The Eighth Day and its critical commentary. The novel sets the story of Olivia, a contemporary protagonist, into the Sumerian myth of Inanna: Queen of Heaven and Earth. Like Inanna, Olivia descends, removing her mortal vestments or metaphors of belief, in seven stages or gates that lead to the underworld where she will arrive naked and bowing low before her sister-self, Rahab. Because Olivia's ideology is rigidly bound by ethics framed in the Old Testament, both of these myths play a large part in the unfolding of her story. Livia's beliefs must be closely identified before she can dicard or amend them. The Inanna myth illuminates the spiral nature of life's journey from the blind innocence of a child descending down to a conscious innocence bom of choice. The critical commentary that precedes the novel discusses the art and technique that plays part in all fiction and in the novel, The Eighth Day. -

RECORD SHOP Gesamtkatalog Gültig Bis 30.06.2021 Record Shop Holger Schneider Flurstr
RECORD SHOP GESamtkatalOG gültig bis 30.06.2021 Record Shop Holger Schneider Flurstr. 7, 66989 Höheinöd, Germany Tel.: (0049) 06333-993214 Fax: (0049) 06333-993215 @Mail: [email protected] Homepage: www.recordshop-online.de Gruppe / Titel Artikelbeschreibung B.-Nr.Preis Gruppe / Titel Artikelbeschreibung B.-Nr. Preis 10 CC AC/DC - VARIOUS ARTITS GREATEST HITS 1972 - 1978CD M-/M 90675 4,99 € BACK IN BLACKCD A TRIBUTE TO AC/DC M/M 85519 5,99 € 12 STONES THE MANY FACES OFCD 3 CD BOX Lim. Edition im Digipack !!! EX-/EX/EX/EX 96776 6,99 € 12 STONESCD M-/M 97005 6,99 € ACCEPT POTTERS FIELDCD M/M 97004 6,99 € ACCEPTCD D/2005/Steamhammer M/M 99871 19,99 € 18 SUMMERS ACCEPTLP Spain/79/Victoria Lady Lou.... M/M 20437 14,99 € VIRGIN MARYCD EX-/M- 93108 4,99 € BALLS TO THE WALLCD D/2002/BMG 12 TRACKS 98714 6,99 € BEST OFCD M/M- 77627 4,99 € 23RD GRADE OF EVIL BLOOD OF NATIONSCD M-/M 95090 7,99 € WHAT WILL REMAIN WHEN WE ARE GCD M-/M 98249 9,99 € HUNGRY YEARSCD DIGITAL REMIX M-/M- 50773 6,99 € 24 K LIVE IN JAPANLP D/85RCA EX/EX -Co- 10371 6,99 € BULLETPROOFCD EX-/M 82303 4,99 € LIVE IN JAPANLP D/85RCA M-/EX 20482 7,99 € PURECD EX-/M- 72083 4,99 € LIVE IN JAPANLP D/85RCA M-/M 20431 9,99 € 3 DOORS DOWN METAL MASTERSCD EX-/M- 63277 4,99 € THE BETTER LIFECD M/M 84233 2,99 € PREDATORCD EX-/M 81397 9,99 € RUSSIAN ROULETTECD Remastered Edition mit 2 Bonus Livetracks OVP 87910 6,99 € 30.000 Kollegen THE ACCEPT COLLECTIONCD BOX 3 CD SET EU/2010/UNIVERSAL EX/EX-/EX/EX+ 91760 6,99 € Allein auf weiter flurLP M/M 20841 5,99 € 36 CRYZYFISTS ACCEPT / VA A TRIBUTE TO ACCEPT ICD Lim.