IBM I Security Sockets Layer Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cipher Support on a Citrix MPX/SDX (N3) Appliance
Cipher support on a Citrix MPX/SDX (N3) appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, frontend, backend, and internal services. On an SDX appliance, if an SSL chip is assigned to a VPX instance, the cipher support of an MPX appliance applies. Otherwise, the normal cipher support of a VPX instance applies. From release 10.5 build 56.22, NetScaler MPX appliances support full hardware optimization for all ciphers. In earlier releases, part of ECDHE/DHE cipher optimization was done in software. Use the 'show hardware' command to identify whether your appliance has N3 chips. > sh hardware Platform: NSMPX-22000 16*CPU+24*IX+12*E1K+2*E1K+4*CVM N3 2200100 Manufactured on: 8/19/2013 CPU: 2900MHZ Host Id: 1006665862 Serial no: ENUK6298FT Encoded serial no: ENUK6298FT Done How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0, releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Ciphersuite Name Hex Wireshark Ciphersuite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CB 10.5, 11.0, 10.5, 11.0, C_SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f -

Implementation and Analysis of Key Reinstallation Attack
International Journal of Innovations in Engineering and Technology (IJIET) http://dx.doi.org/10.21172/ijiet.133.21 Implementation and Analysis of Key Reinstallation Attack Saba Khanum1, Ishita kalra2 1Department of Information Technology, MSIT, Janakpuri, New Delhi, India 2Department of Computer Science and Engineering, MSIT, Janakpuri, New Delhi, India Abstract- The objective of the paper is to implement and analyzed the impact of Key Reinstallation Attack (popularly dubbed as KRACK) on debian based machines. The paper elucidates on the capture of packets through the attack without being a part of the network and affecting the target machines with the help of an attack machine placed inside the network. It basically exploits the nonce of the network which ultimately paves way to the execution of the attack. The issue tends to gather more eyeballs as it affects all devices using Wi-Fi through WPA2 protocol. Hence, the catastrophe complimented along the attack is severe. The analysis of the impact is carried on by analyzing the type of packets visible as well as captured during the course of the implementation. Here, we have created a python script which identifies whether the targeted machine is vulnerable to KRACK or not and corresponding to that the packet capture starts and ultimately, the impact is measured. Keywords – KRACK, weakness, WPA2, attack, security I. INTRODUCTION The presence of the bug has been detected in the cryptographic nonce of the WPA2 and can be used to clone a connected party to reinstall a used key. The presence of the nonce is specifically intended to prevent reuse, but in this particular case, it gives malicious users the opportunity to replay, decrypt, or forge packets, ultimately enabling them to access all previously considered encrypted information without actually being part of the network. -
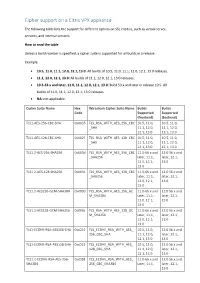
Cipher Support on a Citrix ADC VPX Appliance
Cipher support on a Citrix VPX appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, services, and internal services. How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0 releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Cipher Suite Name Hex Wireshark Cipher Suite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f TLS_RSA_WITH_AES_128_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1.2-AES-256-SHA256 0x003d TLS_RSA_WITH_AES_256_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES-128-SHA256 0x003c TLS_RSA_WITH_AES_128_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES256-GCM-SHA384 0x009d TLS_RSA_WITH_AES_256_GC 11.0-66.x and 12.0 56.x and M_SHA384 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES128-GCM-SHA256 0x009c TLS_RSA_WITH_AES_128_GC 11.0-66.x and 12.0 56.x and M_SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1-ECDHE-RSA-AES256-SHA -

Analysis of DTLS Implementations Using Protocol State Fuzzing
Analysis of DTLS Implementations Using Protocol State Fuzzing Paul Fiterau-Brostean and Bengt Jonsson, Uppsala University; Robert Merget, Ruhr-University Bochum; Joeri de Ruiter, SIDN Labs; Konstantinos Sagonas, Uppsala University; Juraj Somorovsky, Paderborn University https://www.usenix.org/conference/usenixsecurity20/presentation/fiterau-brostean This paper is included in the Proceedings of the 29th USENIX Security Symposium. August 12–14, 2020 978-1-939133-17-5 Open access to the Proceedings of the 29th USENIX Security Symposium is sponsored by USENIX. Analysis of DTLS Implementations Using Protocol State Fuzzing Paul Fiterau-Bro¸stean˘ Bengt Jonsson Robert Merget Joeri de Ruiter Uppsala University Uppsala University Ruhr University Bochum SIDN Labs Konstantinos Sagonas Juraj Somorovsky Uppsala University Paderborn University Abstract reach 11.6 billion by 2021 [26]. This will constitute half of all devices connected to the Internet, with the percentage set to Recent years have witnessed an increasing number of proto- grow in subsequent years. Such trends also increase the need cols relying on UDP. Compared to TCP, UDP offers perfor- to ensure that software designed for these devices is properly mance advantages such as simplicity and lower latency. This scrutinized, particularly with regards to its security. has motivated its adoption in Voice over IP, tunneling techno- DTLS is also used as one of the two security protocols in logies, IoT, and novel Web protocols. To protect sensitive data WebRTC, a framework enabling real-time communication. exchange in these scenarios, the DTLS protocol has been de- WebRTC can be used, for example, to implement video con- veloped as a cryptographic variation of TLS. -

Authenticated Encryption Mode IAPM Using SHA-3'S Public Random
Authenticated Encryption Mode IAPM using SHA-3’s Public Random Permutation Charanjit Jutla IBM T. J. Watson Research Center New York 10598 Abstract. We study instantiating the random permutation of the block- cipher mode of operation IAPM (Integrity-Aware Parallelizable Mode) with the public random permutation of Keccak, on which the draft stan- dard SHA-3 is built. IAPM and the related mode OCB are single-pass highly parallelizable authenticated-encryption modes, and while they were originally proven secure in the private random permutation model, Kurosawa has shown that they are also secure in the public random per- mutation model assuming the whitening keys are uniformly chosen with double the usual entropy. In this paper, we show a general composabil- ity result that shows that the whitening key can be obtained from the usual entropy source by a key-derivation function which is itself built on Keccak. We stress that this does not follow directly from the usual indifferentiability of key-derivation function constructions from Random Oracles. We also show that a simple and general construction, again employing Keccak, can also be used to make the IAPM scheme key- dependent-message secure. Finally, implementations on modern AMD-64 architecture supporting 128-bit SIMD instructions, and not supporting the native AES instructions, show that IAPM with Keccak runs three times faster than IAPM with AES. 1 Introduction Symmetric key encryption of bulk data is usually performed using either a stream cipher or a block cipher. A long message is divided into small fixed-size blocks and encryption is performed by either a stream-cipher mode or a block-cipher mode employing a cryptographic primitive that operates on blocks. -

Prying Open Pandora's Box: KCI Attacks Against
Prying open Pandora’s box: KCI attacks against TLS Clemens Hlauschek, Markus Gruber, Florian Fankhauser, Christian Schanes RISE – Research Industrial Systems Engineering GmbH {clemens.hlauschek, markus.gruber, florian.fankhauser, christian.schanes}@rise-world.com Abstract and implementations of the protocol: their utility is ex- tremely limited, their raison d’ˆetre is practically nil, and Protection of Internet communication is becoming more the existence of these insecure key agreement options common in many products, as the demand for privacy only adds to the arsenal of attack vectors against cryp- in an age of state-level adversaries and crime syndi- tographically secured communication on the Internet. cates is steadily increasing. The industry standard for doing this is TLS. The TLS protocol supports a multi- 1 Introduction tude of key agreement and authentication options which provide various different security guarantees. Recent at- The TLS protocol [1, 2, 3] is probably the most tacks showed that this plethora of cryptographic options widely used cryptographic protocol on the Internet. in TLS (including long forgotten government backdoors, It is designed to secure the communication between which have been cunningly inserted via export restric- client/server applications against eavesdropping, tamper- tion laws) is a Pandora’s box, waiting to be pried open by ing, and message forgery, and it also provides additional, heinous computer whizzes. Novel attacks lay hidden in optional security properties such as client authentica- plainsight. Parts of TLS areso oldthat theirfoul smell of tion. TLS is an historically grown giant: its predecessor, rot cannot be easily distinguished from the flowery smell SSL [4,5], was developed more than 20 years ago. -

OCB: a Bock-Cipher Mode of Operation for Efficient Authenticated Encryption
OCB: A Bock-Cipher Mode of Operation for Efficient Authenticated Encryption Phillip Rogaway UC Davis This work done at Chiang Mai University [email protected] http://www.cs.ucdavis.edu/~rogaway Mihir Bellare John Black Ted Krovetz UC San Diego University of Nevada UC Davis CCS-8 — Philadelphia, USA — November 8, 2001 Slide 1 Principal Goals of Symmetric Cryptography Privacy What the Adversary sees tells her nothing of significance about the underlying message M that the Sender sent Authenticity The Receiver is sure that the string he receives was sent (in exactly this form) by the Sender Authenticated Encryption Achieves both privacy and authenticity C C* Nonce M M K Adversary K or invalid K K Sender Receiver Slide 2 Why Authenticated Encryption? • Efficiency By merging privacy and authenticity one can achieve efficiency difficult to achieve if handling them separately. • Easier-to-correctly-use abstraction By delivering strong security properties one may minimize encryption-scheme misuse. Slide 3 Easier to correctly use because stronger security properties Idealized encryption OCB Authenticated encryption [Bellare, Rogaway] IND-CPA + auth of ciphertexts [Katz,Yung] [Bellare, Namprempre] IND-CCA = NM-CCA CTR, CBC$ [Goldwasser, Micali] IND-CPA [Bellare, Desai, Jokipii, Rogaway] ECB Slide 4 Right or Wrong? It depends on what definition E satisfies K A . R K A A B EK (A . B . RA . RB .sk) EK (RB) Slide 5 Folklore approach. See Generic Composition [Bellare, Namprempre] and [Krawczyk] Traditional approach to authenticated encryption for -

Global Journal of Engineering Science And
[Arslan, 6(3): March 2019] ISSN 2348 – 8034 DOI- 10.5281/zenodo.2599921 Impact Factor- 5.070 GLOBAL JOURNAL OF ENGINEERING SCIENCE AND RESEARCHES PRIVACY PRESERVING SECURITY MECHANISM FOR IOT BASED DISTRIBUTED SMART HEALTHCARE SYSTEM Farrukh Arslan School of Electrical and Computer Engineering, Purdue University, USA ABSTRACT Data security and privacy are one of the key concerns in the Internet of Things (IoT). Usage of IOT is increasing in the society day-by-day, and security challenges are becoming more and more severe. From a data perspective, IOT data security plays a major role. Some of the sensitive data such as criminal record, military information, the medical record of the patients, etc. Due to the size and other features of IOT, it is almost impossible to create an efficient centralized authentication system. The proposed system focused on IoT security for distributed medical record to provide perimeter security to the patient. Building trust in distributed environments without the need for authorities is a technological advance that has the potential to change many industries, the IOT is one among them. Furthermore, it protects data integrity and availability. It improves the accessibility of data by using the indexing method along with the blockchain. Moreover, it facilitate the utility of tracking the previous history of the patient record using the hyper ledger with authorization. Keywords: security, Internet of Things, Health-care, Block chain, Hyper ledger. I. INTRODUCTION Amount of information grows day by day but the security of the data is not maintained properly. Nowadays blockchain technology is very useful in IOT field such as smart cities, smart home system as well as it provides security [1]. -

CMU-CS-17-118 July 2017
Secure Large-Scale Outsourced Services Founded on Trustworthy Code Executions Bruno Vavala CMU-CS-17-118 July 2017 School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 Faculty of Sciences University of Lisbon 1749-16 Lisbon, Portugal Thesis Committee: Peter Steenkiste, Co-Chair Nuno Neves, University of Lisbon, Co-Chair Anupam Datta Vyas Sekar Antonia Lopes, University of Lisbon Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Computer Science Copyright c 2017 Bruno Vavala This research was sponsored by Fundac¸ao˜ para a Cienciaˆ e Tecnologia (Portuguese Foundation for Science and Technology) through the Carnegie Mellon Portugal Program under grant SFRH/BD/51562/2011 (until August 2016) and the Information and Communication Technology Institute at Carnegie Mellon University, by FCT through project UID/CEC/00408/2013 (LaSIGE), by the EC through project FP7-607109 (SEGRID) and project H2020-643964 (SUPERCLOUD). The views and conclusions contained in this document are those of the author and should not be interpreted as representing the official policies, either expressed or implied, of any sponsoring institution, the Portuguese government, the U.S. government or any other entity. Keywords: Trusted Computing, Cloud Security, Trusted Execution Abstraction, Execution Integrity, Code Identity, Large-scale Data, TPM, Intel SGX, Efficient Execution Verification, Passive Replication, Service Availability This work was partially supported by the Fundac¸ao˜ para a Cienciaˆ e Tecnologia (FCT) through research grant SFRH/BD/51562/2011 (until August 2016) and through project UID/CEC/00408/2013 (LaSIGE), by the Informa- tion and Communication Technology Institute at Carnegie Mellon University, by the EC through project FP7-607109 (SEGRID) and project H2020-643964 (SUPERCLOUD). -

Matrixssl Elliptic Curve Cipher Suites
MatrixSSL Elliptic Curve Cipher Suites Electronic versions are uncontrolled unless directly accessed from the QA Document Control system. Printed version are uncontrolled except when stamped with ‘VALID COPY’ in red. External release of this document may require a NDA. © INSIDE Secure - 2016 - All rights reserved TABLE OF CONTENTS 1 ELLIPTIC CURVE CRYPTOGRAPHY ....................................................................... 3 2 ECC CIPHER SUITES ......................................................................................... 4 2.1 Variations .......................................................................................................... 4 2.1.1 ECDHE_ECDSA ............................................................................................... 4 2.1.2 ECDHE_RSA ................................................................................................... 4 2.1.3 ECDH_ECDSA ................................................................................................. 4 2.1.4 ECDH_RSA ...................................................................................................... 4 2.2 Support in MatrixSSL ........................................................................................ 4 3 WHEN ECC CIPHER SUITES ARE A GOOD ALTERNATIVE ...................................... 5 4 API .................................................................................................................. 6 2 © INSIDE Secure – 2016 - All rights reserved 1 ELLIPTIC CURVE CRYPTOGRAPHY This document -

TLS Cipher Suites Recommendations: a Combinatorial Coverage Measurement Approach
TLS Cipher Suites Recommendations: A Combinatorial Coverage Measurement Approach Dimitris E. Simos∗, Kristoffer Kleine∗, Artemios G. Voyiatzis∗, Rick Kuhnx, Raghu Kackerx ∗ SBA Research, Vienna, Austria Email: fdsimos,kkleine,[email protected] x NIST, Information Technology Laboratory, Gaithersburg, MD, USA Email: fd.kuhn.nist.gov,[email protected] Abstract—We present a coverage measurement for TLS ci- channel and, at the same time, also conform to a desired pher suites recommendations provided by various regulatory level of security. It not enough for a TLS implementation and intelligence organizations such as the IETF, ENISA, the to support a set cryptographic algorithms for various tasks German BSI, Mozilla and the USA NSA. These cipher suites are measured and analyzed using a combinatorial approach, (e.g., encryption or authentication) but also to ensure that only which was made feasible via developing the necessary input “secure” combinations of them are accepted and used. models. Besides, shedding light on the coverage achieved by In this paper, we perform a study of the combinatorial the proposed recommendations we discuss implications towards coverage of the TLS cipher suites. The aim of the study is aspects of test quality. One of them relates to the testing of a TLS implementation, where a system designer or tester should expand to provide insights on the coverage achieved by the proposed the TLS cipher suite registry and integrate the information back recommendations and guide, if possible, the selection of ap- to the TLS implementation itself such that the (overall) testing propriate test suites that minimize the number of combinations effort is reduced. -

The Evolution of Authenticated Encryption
The Evolution of Authenticated Encryption Phillip Rogaway University of California, Davis, USA Those who’ve worked with me on AE: Mihir Bellare Workshop on Real-World Cryptography John Black Thursday, 10 January 2013 Ted Krovetz Stanford, California, USA Chanathip Namprempre Tom Shrimpton David Wagner 1/40 Traditional View (~2000) Of Symmetric Goals K K Sender Receiver Privacy Authenticity (confidentiality) (data-origin authentication) Encryption Authenticated Encryption Message scheme Achieve both of these aims Authentication Code (MAC) IND-CPA [Goldwasser, Micali 1982] Existential-unforgeability under ACMA [Bellare, Desai, Jokipii, R 1997] [Goldwasser, Micali, Rivest 1984, 1988], [Bellare, Kilian, R 1994], [Bellare, Guerin, R 1995] 2/40 Needham-Schroeder Protocol (1978) Attacked by Denning-Saco (1981) Practioners never saw a b IND-CPA as S encryption’s goal A . B . NA {N . B . s . {s . A} } 1 A b a 2 a b {s . A} A 3 b B 4 {NB}s 5 {NB -1 }s 3/40 Add redundancy No authenticity for any S = f (P) CBC ~ 1980 Doesn’t work Beyond CBC MAC: regardless of how you compute unkeyed checksums don’t work even the (unkeyed) checksum S = R(P1, …, Pn) with IND-CCA or NM-CPA schemes (Wagner) [An, Bellare 2001] 4/40 Add more arrows PCBC 1982 Doesn’t work See [Yu, Hartman, Raeburn 2004] The Perils of Unauthenticated Encryption: Kerberos Version 4 for real-world attacks 5/40 Add yet more stuff iaPCBC [Gligor, Donescu 1999] Doesn’t work Promptly broken by Jutla (1999) & Ferguson, Whiting, Kelsey, Wagner (1999) 6/40 Emerging understanding that: - We’d like